Xplico action
Having found suspicious traffic I wanted to see what was going on an started a full tcpdump on the default GW to capture everything destined for the "interesting" host.
tcpdump -s 0 -i eth0 host [ip-address]
- Get the xplico OVA file from http://www.xplico.org/download
- Install it into your VirtualBox and configure the VM to fit your needs.
-
Connect to your new Xlpico instance with [http://[ip-of-VM]:9876 [admin/xplico]
-
Create a new user for your action. - Only "Users" can create new cases.
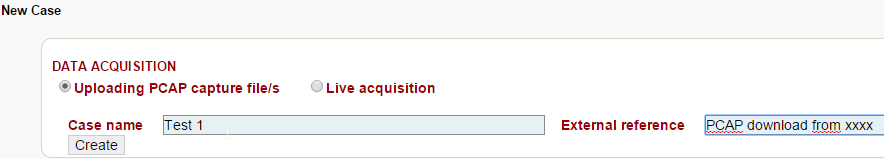
Create a new case:
Within that case, create a new session:
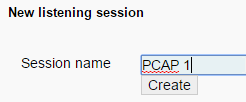
Enter that session and upload your pcap file:
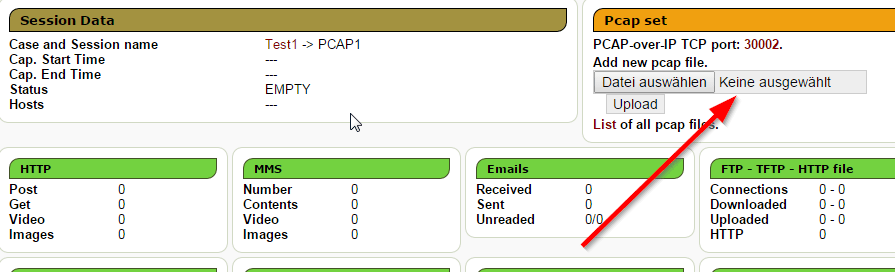
Upload and wait until the decoding has finished:

Now the menu fields have values to be examined:
Also check the "undecoded" section within the menu.
If clickin on one of the lines, this communication snipet can be downloaded and directly opened in other applications (i.E. wireshark)
To use a remote tcpdump to directly send the data into your Xplico, use below command. But please note, this is not a live decoding of the data.
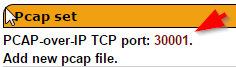
tcpdump -s 65535 -i eth1 not port [port #] -w - | nc [IP of xplico] [port #]
The port number can be found in the sessions tab where up upload your PCAP files.