Analyzing IPhone backups
Well, let's start an easy way first. - Although I'm quite sure not to be able to catch all the relevant data, it's still a good way to get used to the "IOS world".
Create a backup of the device via iTunes.
Find the backupfile at: C:\...\AppData\Roaming\Apple Computer\MobileSync\Backup
Start the JAR file of "IPhone Analyzer" (find the DL link in the tools section)
You basically start with a "Bookmarks" mode and a more raw aproach in the "File System" mode.
While first examining a backup file, wait until all media files have been detected.
From IR of Windows and Linux machines, I try to do it with a zero-change approach of the original devices.
So creating a backup should not change anything on the device (not veified yet) and all the examination can be done on the analyst machine.
So first of all I use the "Export All" from within the file menu to create a browseable copy of the devices content.
Don't worry that the tool has frozen after starting the export. It does not give you any progress while exporting and does not accept further inputs while exporting.
That gives a lot of pfiles, sqlite, and others that are not directly usabe without a view tools. But it already gives you access to pictures.
To get a rough idea where the owner has surfed or talked with the outside world, check the cokkies (also check the deleted fragments):
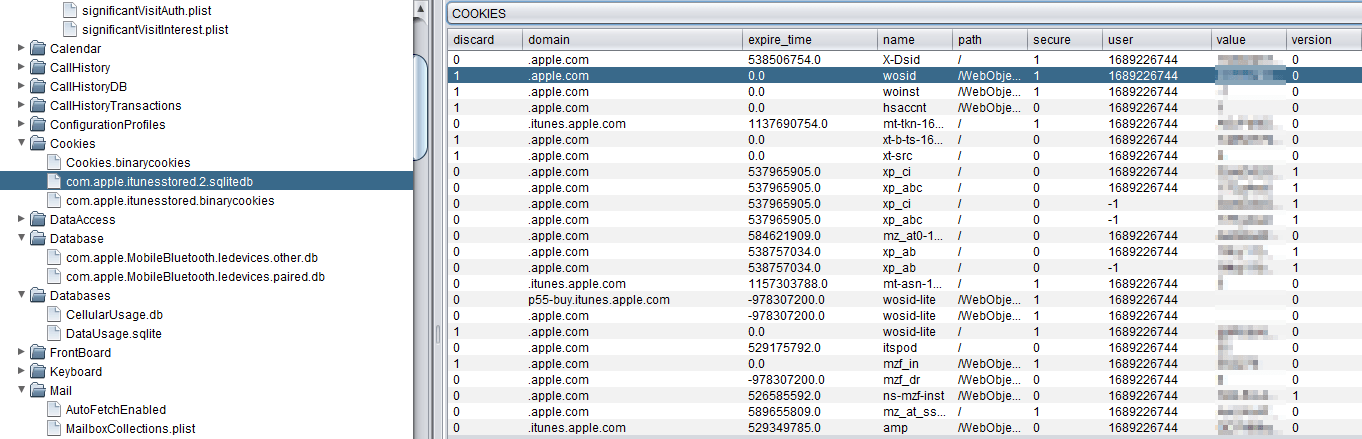
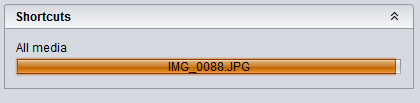
Using the "IPhone research tool"
... to extract some username/password: