APT 001
Also known as: Unit 61398, Comment Crew
Suspected attribution: China’s People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department (总参三部二局), which is most commonly known by its Military Unit Cover Designator (MUCD) as Unit 61398 (61398部队).
Target sectors: Information Technology, Aerospace, Public Administration, Satellites and Telecommunications, Scientific Research and Consulting, Energy, Transportation, Construction and Manufacturing, Engineering Services, High-tech Electronics, International Organizations, Legal Services Media, Advertising and Entertainment, Navigation, Chemicals, Financial Services, Food and Agriculture, Healthcare, Metals and Mining, Education
Overview: APT1 has systematically stolen hundreds of terabytes of data from at least 141 organizations, and has demonstrated the capability and intent to steal from dozens of organizations simultaneously. The group focuses on compromising organizations across a broad range of industries in English-speaking countries. The size of APT1’s infrastructure implies a large organization with at least dozens, but potentially hundreds of human operators.
Associated malware: TROJAN.ECLTYS, BACKDOOR.BARKIOFORK, BACKDOOR.WAKEMINAP, TROJAN.DOWNBOT, BACKDOOR.DALBOT, BACKDOOR.REVIRD, TROJAN.BADNAME, BACKDOOR.WUALESS
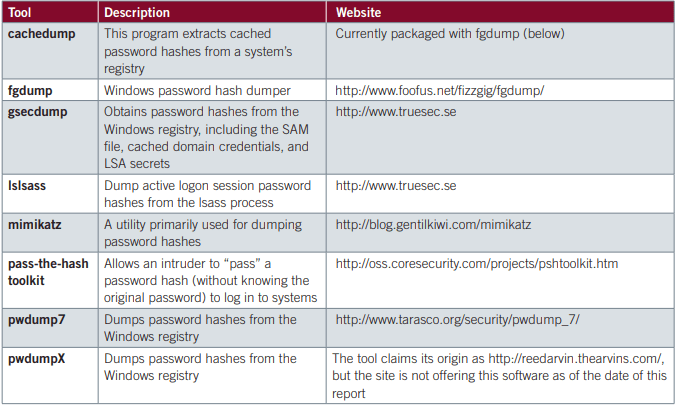
Tools used: BISCUIT, CALENDAR, GLOOXMAIL. WEBC2. gsecdump, Cachedump, Lslsass, Mimikatz, Pass-The-Hash Toolkit, pwdump, PoisonIvy, xCmd, ipconfig, Net, Tasklist
Attack vectors: The most commonly observed method of initial compromise is spear phishing. The spear phishing emails contain either a malicious attachment or a hyperlink to a malicious file. The subject line and the text in the email body are usually relevant to the recipient. APT1 also creates webmail accounts using real peoples’ names. While APT1 intruders occasionally use publicly available backdoors such as Poison Ivy and Gh0st RAT, the vast majority of the time they use what appear to be their own custom backdoors. Throughout their stay in the network (which could be years), APT1 usually installs new backdoors as they claim more systems in the environment. Then, if one backdoor is discovered and deleted, they still have other backdoors they can use. We usually detect multiple families of APT1 backdoors scattered around a victim network when APT1 has been present for more than a few weeks.
Targets
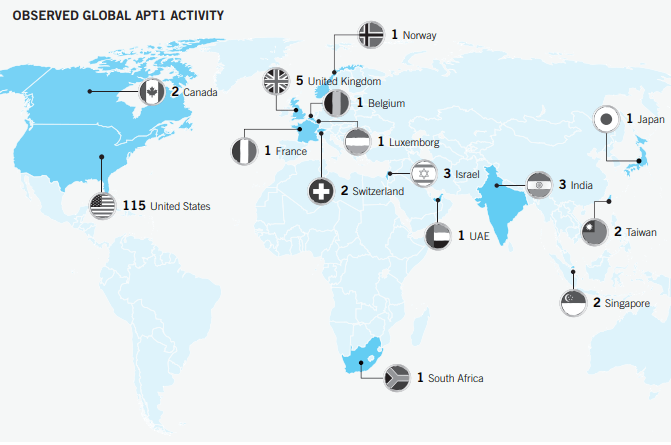
Geographic location of APT1’s victims. In the case of victims with a multinational presence, the location shown reflects either the branch of the organization that APT1 compromised (when known), or else is the location of the organization’s headquarters.
APT1’s Geographic & Industry Focus
APT1 steals a broad range of information from its victims. The types of information the group has stolen relate to: » product development and use, including information on test results, system designs, product manuals, parts lists, and simulation technologies; » manufacturing procedures, such as descriptions of proprietary processes, standards, and waste management processes; » business plans, such as information on contract negotiation positions and product pricing, legal events, mergers, joint ventures, and acquisitions; » policy positions and analysis, such as white papers, and agendas and minutes from meetings involving highranking personnel; » emails of high-ranking employees; and » user credentials and network architecture information. It is often difficult for us to estimate how much data APT1 has stolen during their intrusions for several reasons: » APT1 deletes the compressed archives after they pilfer them, leaving solely trace evidence that is usually overwritten during normal business activities. » Pre-existing network security monitoring rarely records or identifies the data theft. » The duration of time between the data theft and Mandiant’s investigation is often too great, and the trace evidence of data theft is overwritten during the normal course of business. » Some victims are more intent on assigning resources to restore the security of their network in lieu of investigating and understanding the impact of the security breach. Even with these challenges, we have observed APT1 steal as much as 6.5 terabytes of compressed data from a single organization over a ten-month time period. Given the scope of APT1’s operations, including the number of organizations and industries we have seen them target, along with the volume of data they are clearly capable of stealing from any single organization, APT1 has likely stolen hundreds of terabytes from its victims.
Publicly available privilege escalation tools that APT1 has used