APT 015
Also known as: Vixen Panda, Ke3chang, Royal APT, and Playful Dragon
Suspected attribution: Chinese government
Target sectors: Defense, high tech, energy, government, aerospace, manufacturing and other sectors.
Overview: APT15 is known for committing cyberespionage against companies and organizations located in many different countries, targeting different sectors such as the oil industry, government contractors, military, and more. They are known for “living off the land,” meaning they use already available tools and software installed on the computer to operate, and once inside a target network, they will tailor their malware specifically to the target. Other names for the group are Vixen Panda, Ke3chang, Royal APT, and Playful Dragon.
Associated malware: RoyalDNS, RoyalCli, BS2005, spwebmember, Mimikatz, idePool, BMW and MyWeb
Attack vectors: not yet fully disclosed
Further reading
https://www.intezer.com/miragefox-apt15-resurfaces-with-new-tools-based-on-old-ones/
https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2018/march/apt15-is-alive-and-strong-an-analysis-of-royalcli-and-royaldns/
https://securityaffairs.co/wordpress/73636/apt/apt15-miragefox-malware.html
https://www.bleepingcomputer.com/news/security/cyber-espionage-group-steals-data-from-uk-government-contractor/
IOC’s: Download from GitHub here.
Royal DNS: bc937f6e958b339f6925023bc2af375d669084e9551fd3753e501ef26e36b39d>
BS2005: 750d9eecd533f89b8aa13aeab173a1cf813b021b6824bc30e60f5db6fa7b950b
BS2005: 6ea9cc475d41ca07fa206eb84b10cf2bbd2392366890de5ae67241afa2f4269f
RoyalCli: 6df9b712ff56009810c4000a0ad47e41b7a6183b69416251e060b5c80cd05785
MS Exchange Tool: 16b868d1bef6be39f69b4e976595e7bd46b6c0595cf6bc482229dbb9e64f1bce
The RoyalCli backdoor was attempting to communicate to the following domains:
- News.memozilla[.]org
- video.memozilla[.]org
The BS2005 backdoor utilised the following domains for C2:
- Run.linodepower[.]com
- Singa.linodepower[.]com
- log.autocount[.]org
RoyalDNS backdoor was seen communicating to the domain:
- andspurs[.]com
Possible linked APT15 domains include:
- Micakiz.wikaba[.]org
- cavanic9[.]net
- ridingduck[.]com
- zipcodeterm[.]com
- dnsapp[.]info
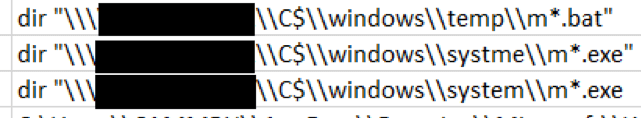
During our analysis of the decoded attacker commands we noticed a typographical mistake, shown below in the folder name 'systme'. This indicates that a human operative was executing commands on a command line style interface, rather than an automated or GUI process.