APT 028
Also known as: Tsar Team, Sofacy, Fancy bear, Pawn Storm, Sednit, Strontium
Suspected attribution: Russian government
Target sectors: The Caucasus, particularly Georgia, eastern European countries and militaries, North Atlantic Treaty Organization (NATO) and other European security organizations and defense firms
Overview: APT28 is a skilled team of developers and operators collecting intelligence on defense and geopolitical issues—intelligence that would be useful only to a government. This APT group compiles malware samples with Russian language settings during working hours (8 a.m. to 6 p.m.), consistent with the time zone of Russia’s major cities, including Moscow and St. Petersburg. This suggests that APT28 receives direct ongoing financial and other resources from a well-established organization, most likely the Russian government.
Associated malware: CHOPSTICK, SOURFACE ADVSTORESHELL, JHUHUGIT, XTunnel
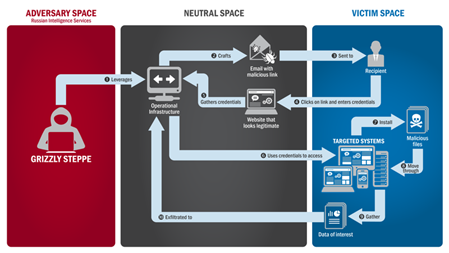
Attack vectors: Tools commonly used by APT28 include the SOURFACE downloader, its second-stage backdoor EVILTOSS and a modular family of implants dubbed CHOPSTICK. APT28 has employed RSA encryption to protect files and stolen information moved from the victim’s network to the controller. It has also made incremental and systematic changes to the SOURFACE downloader and its surrounding ecosystem since 2007, indicating a long-standing and dedicated development effort.
Characteristics and techniquesFancy Bear employs advanced methods consistent with the capabilities of nation-state actors. They use spear phishing emails, malware drop websites disguised as news sources, and zero-day vulnerabilities. One cybersecurity research group noted their use of no less than six different zero-day exploits in 2015, a considerable technical feat that would require large numbers of programmers seeking out previously unknown vulnerabilities in top of the line commercial software. This is a sign that Fancy Bear is a state-run program and not a gang or a lone hacker.
One of Fancy Bear's preferred targets is web-based email services. A typical compromise will consist of web-based email users receiving an email urgently requesting that they change their passwords to avoid being hacked. The email will contain a link to a spoof website that is designed to mimic a real webmail interface, users will attempt to login and their credentials will be stolen. The URL is often obscured as a shortened bit.ly link in order to get past spam filters. Fancy Bear sends these phishing emails primarily on Mondays and Fridays. They also send emails purportedly containing links to news items, but instead linking to malware drop sites that install toolkits onto the target's computer. Fancy Bear also registers domains that resemble legitimate websites, then create a spoof of the site to steal credentials from their victims. Fancy Bear has been known to relay its command traffic through proxy networks of victims that it has previously compromised.
Software that Fancy Bear has used includes ADVSTORESHELL, CHOPSTICK, JHUHUGIT, and XTunnel. Fancy Bear utilises a number of implants, including Foozer, WinIDS, X-Agent, X-Tunnel, Sofacy, and DownRange droppers. Based on compile times, FireEye concluded that Fancy Bear has consistently updated their malware since 2007. To avert detection, Fancy Bear returns to the environment to switch their implants, changes its command and control channels, and modifies its persistent methods. The threat group implements counter-analysis techniques to obfuscate their code. They add junk data to encoded strings, making decoding difficult without the junk removal algorithm. Fancy Bear takes measures to prevent forensic analysis of its hacks, resetting the timestamps on files and periodically clearing the event logs.
Fancy Bear has been known to tailor implants for target environments, for instance reconfiguring them to use local email servers. In August 2015, Kaspersky Lab detected and blocked a version of the ADVSTORESHELL implant that had been used to target defense contractors. An hour and a half following the block, Fancy Bear actors had compiled and delivered a new backdoor for the implant.
APT28 Attacks (Wikipedia)
Fancy Bear's targets have included Eastern European governments and militaries, the country of Georgia and the Caucasus, Ukraine,[17] security-related organizations such as NATO, as well as US defense contractors Academi (formerly known as Blackwater), Science Applications International Corporation (SAIC),[18] Boeing, Lockheed Martin, and Raytheon.[17] Fancy Bear has also attacked citizens of the Russian Federation that are political enemies of the Kremlin, including former oil tycoon Mikhail Khodorkovsky, and Maria Alekhinaof the band Pussy Riot.[17] SecureWorks, a cybersecurity firm headquartered in the United States, concluded that from March 2015 to May 2016, the "Fancy Bear" target list included not merely the United States Democratic National Committee, but tens of thousands of foes of Putin and the Kremlin in the United States, Ukraine, Russia, Georgia, and Syria. Only a handful of Republicans were targeted, however.[19] An AP analysis of 4,700 email accounts that had been attacked by Fancy Bear concluded that no country other than Russia would be interested in hacking so many very different targets that seemed to have nothing else in common other than their being of interest to the Russian government.[17]
Fancy Bear also seems to try to influence political events in order for friends or allies of the Russian government to gain power.
In 2011-2012, Fancy Bear's first-stage malware was the "Sofacy" or SOURFACE implant. During 2013, Fancy Bear added more tools and backdoors, including CHOPSTICK, CORESHELL, JHUHUGIT, and ADVSTORESHELL.
Attacks on prominent journalists in Russia, United States, Ukraine, Moldova, the Baltics, and elsewhereFrom mid-2014 until the fall of 2017, Fancy Bear targeted numerous journalists in the United States, Ukraine, Russia, Moldova, the Baltics, and other countries that had provided articles discrediting Putin and the Kremlin. According to the AP and SecureWorks, this group of journalists is the third largest group targeted by Fancy Bear after diplomatic personnel and U.S. Democrats. Fancy Bear's targeted list includes Adrian Chen, the Armenian journalist Maria Titizian, Eliot Higgins at Bellingcat, Ellen Barry and at least 50 other New York Times reporters, at least 50 foreign correspondents based in Moscow who worked for independent news outlets, Josh Rogin, a Washington Post columnist, Shane Harris, a Daily Beast writer who in 2015 covered intelligence issues, Michael Weiss, a CNN security analyst, Jamie Kirchick with the Brookings Institution, 30 media targets in Ukraine, many at the Kyiv Post, reporters who covered the Russian-backed war in eastern Ukraine, as well as in Russia where the majority of journalists targeted by the hackers worked for independent news (e.g. Novaya Gazeta or Vedomosti) such as Ekaterina Vinokurova at Znak.com and mainstream Russian journalists Tina Kandelaki, Ksenia Sobchak, and the Russian television anchor Pavel Lobkov, all of which worked for Dozhd.[21]
German attack (2014)Fancy Bear is thought to have been responsible for a six-month-long cyber-attack on the German parliament that began in December 2014.[22]
The group is also suspected to be behind a spear phishing attack in August 2016 on members of the Bundestag and multiple political parties such as Linken-faction leader Sahra Wagenknecht, Junge Union and the CDU of Saarland.[23][24][25][26] Authorities fear that sensitive information could be gathered by hackers to later manipulate the public ahead of elections such as Germany's next federal election due in September 2017.[23]
French television hack (April 2015)On April 8, 2015, French television network TV5Monde was the victim of a cyber-attack by a hacker group calling itself "CyberCaliphate" and claiming to have ties to the terrorist organization Islamic State of Iraq and the Levant (ISIL). French investigators later discounted the theory that militant Islamists were behind the cyber-attack, instead suspecting the involvement of Fancy Bear.[27]
Hackers breached the network's internal systems, possibly aided by passwords openly broadcast by TV5,[28] overriding the broadcast programming of the company's 12 channels for over three hours.[29] Service was only partially restored in the early hours of the following morning and normal broadcasting services were disrupted late into April 9.[29] Various computerised internal administrative and support systems including e-mail were also still shut down or otherwise inaccessible due to the attack.[30][29] The hackers also hijacked TV5Monde's Facebook and Twitter pages to post the personal information of relatives of French soldiers participating in actions against ISIS, along with messages critical of President François Hollande, arguing that the January 2015 terrorist attacks were "gifts" for his "unforgivable mistake" of partaking in conflicts that "[serve] no purpose".[31][29]
The director-general of TV5Monde, Yves Bigot, later said that the attack nearly destroyed the company; if it had taken longer to restore broadcasting, satellite distribution channels would have been likely to cancel their contracts. The attack was designed to be destructive, both of equipment and of the company itself, rather than for propaganda or espionage, as had been the case for most other cyber-attacks. The attack was carefully planned; the first known penetration of the network was on January 23, 2015.[32] The attackers then carried out reconnaissance of TV5Monde to understand the way in which it broadcast its signals, and constructed bespoke malicious software to corrupt and destroy the Internet-connected hardware that controlled the TV station's operations, such as the encoder systems. They used seven different points of entry, not all part of TV5Monde or even in France—one was a company based in the Netherlands that supplied the remote controlled cameras used in TV5's studios.[32] Between February 16 and March 25 the attackers collected data on TV5 internal platforms, including its IT Internal Wiki, and verified that login credentials were still valid.[32] During the attack, the hackers ran a series of commands extracted from TACACS logs to erase the firmware from switches and routers.[32]
Although the attack purported to be from IS, France's cyber-agency told Bigot to say only that the messages claimed to be from IS. He was later told that evidence had been found that the attackers were the APT 28 group of Russian hackers. No reason was found for the targeting of TV5Monde, and the source of the order to attack, and funding for it, is not known. It has been speculated that it was probably an attempt to test forms of cyber-weaponry. The cost was estimated at €5m ($5.6m; £4.5m) in the first year, followed by recurring annual cost of over €3m (£3.4m; £2.7m) for new protection. The company's way of working had to change, with authentication of email, checking of flash drives before insertion, and so on, at significant detriment to efficiency for a news media company that must move information.[33]
Root9B report (May 2015)Security firm Root9B released a report on Fancy Bear in May 2015 announcing its discovery of a targeted spear phishing attack aimed at financial institutions. The report listed international banking institutions that were targeted, including the United Bank for Africa, Bank of America, TD Bank, and UAE Bank. According to the Root9B, preparations for the attacks started in June 2014 and the malware used "bore specific signatures that have historically been unique to only one organization, Sofacy."[34] Security journalist Brian Krebsquestioned the accuracy of Root9B's claims, postulating that the attacks had actually originated from Nigerian phishers.[35] In June of 2015 well respected security researcher Claudio Guarnieri published a report based on his own investigation of a concurrent SOFACY attributed exploit against the German Bundestag [36] and credited root9B with having reported, "the same IP address used as Command & Control server in the attack against Bundestag (176.31.112.10)", and went on to say that based on his examination of the Bundestag attack, "at least some" indicators contained within root9B's report appeared accurate, including a comparison of the hash of the malware sample from both incidents. Root9B later published a technical report comparing Claudio's analysis of SOFACY attributed malware to their own sample, adding to the veracity of their original report.[37]
EFF spoof, White House and NATO attack (August 2015)In August 2015, Fancy Bear used a zero-day exploit of Java, spoofing the Electronic Frontier Foundation and launching attacks on the White House and NATO. The hackers used a spear phishing attack, directing emails to the false url electronicfrontierfoundation.org.[38][39]
World Anti-Doping Agency (August 2016In August 2016, the World Anti-Doping Agency reported the receipt of phishing emails sent to users of its database claiming to be official WADA communications requesting their login details. After reviewing the two domains provided by WADA, it was found that the websites' registration and hosting information were consistent with the Russian hacking group Fancy Bear.[40][41] According to WADA, some of the data the hackers released had been forged.[42]
Due to evidence of widespread doping by Russian athletes, WADA recommended that Russian athletes be barred from participating in the 2016 Rio Olympics and Paralympics. Analysts said they believed the hack was in part an act of retaliation against whistleblowing Russian athlete Yuliya Stepanova, whose personal information was released in the breach.[43] In August 2016, WADA revealed that their systems had been breached, explaining that hackers from Fancy Bear had used an International Olympic Committee (IOC)-created account to gain access to their Anti-doping Administration and Management System (ADAMS) database.[44] The hackers then used the website fancybear.net to leak what they said were the Olympic drug testing files of several athletes who had received therapeutic use exemptions, including gymnast Simone Biles, tennis players Venus and Serena Williams and basketball player Elena Delle Donne.[45] The hackers honed in on athletes who had been granted exemptions by WADA for various reasons. Subsequent leaks included athletes from many other countries.[44]
Dutch Safety Board and BellingcatEliot Higgins and other journalists associated with Bellingcat, a group researching the shoot down of Malaysia Airlines Flight 17 over Ukraine, were targeted by numerous spearphishing emails. The messages were fake Gmail security notices with Bit.ly and TinyCC shortened URLs. According to ThreatConnect, some of the phishing emails had originated from servers that Fancy Bear had used in previous attacks elsewhere. Bellingcat is best known for having accused Russia of being culpable for the shoot down of MH17, and is frequently derided in the Russian media.[46][47]
The group targeted the Dutch Safety Board, the body conducting the official investigation into the crash, before and after the release of the board's final report. They set up fake SFTP and VPN servers to mimic the board's own servers, likely for the purpose of spearphishing usernames and passwords.[48] A spokeswoman for the DSB said the attacks were not successful.[49]
Democratic National Committee (2016)Fancy Bear carried out spear phishing attacks on email addresses associated with the Democratic National Committee in the first quarter of 2016.[50] On March 10, phishing emails that were mainly directed at old email addresses of 2008 Democratic campaign staffers began to arrive. One of these accounts may have yielded up to date contact lists. The next day, phishing attacks expanded to the non-public email addresses of high level Democratic Party officials. Hillaryclinton.com addresses were attacked, but required two factor authentication for access. The attack redirected towards Gmail accounts on March 19th. Podesta's Gmail account was breached the same day, with 50,000 emails stolen. The phishing attacks intensified in April,[51] although the hackers seemed to become suddenly inactive for the day on April 15, which in Russia was a holiday in honor of the military's electronic warfare services.[52]The malware used in the attack sent stolen data to the same servers that were used for the group's 2015 attack on the German parliament.[1]
On June 14, CrowdStrike released a report publicizing the DNC hack and identifying Fancy Bear as the culprits. An online persona, Guccifer 2.0, then appeared, claiming sole credit for the breach.[53]
Another sophisticated hacking group attributed to the Russian Federation, nicknamed Cozy Bear, was also present in the DNC's servers at the same time. However the two groups each appeared to be unaware of the other, as each independently stole the same passwords and otherwise duplicated their efforts. Cozy Bear appears to be a different agency, one more interested in traditional long-term espionage.[52] A CrowdStrike forensic team determined that while Cozy Bear had been on the DNC's network for over a year, Fancy Bear had only been there a few weeks.[1]
Ukrainian artilleryAn infected version of an app to control the D-30 Howitzer was allegedly distributed to the Ukrainian artillery
According to CrowdStrike from 2014 to 2016, the group used Android malware to target the Ukrainian Army's Rocket Forces and Artillery. They distributed an infected version of an Android app whose original purpose was to control targeting data for the D-30 Howitzer artillery. The app, used by Ukrainian officers, was loaded with the X-Agent spyware and posted online on military forums. CrowdStrike initially claimed that more than 80% of Ukrainian D-30 Howitzers were destroyed in the war, the highest percentage loss of any artillery pieces in the army (a percentage that had never been previously reported and would mean the loss of nearly the entire arsenal of the biggest artillery piece of the Ukrainian Armed Forces[54]).[55] According to the Ukrainian army CrowdStrike's numbers were incorrect and that losses in artillery weapons "were way below those reported" and that these losses "have nothing to do with the stated cause".[56] CrowdStrike has since revised this report after the International Institute for Strategic Studies (IISS) disavowed its original report, claiming that the malware hacks resulted in losses of 15–20% rather than their original figure of 80%.[57]
Windows zero-day (October 2016On October 31, 2016, Google's Threat Analysis Group revealed a zero-day vulnerability in most Microsoft Windows versions that is the subject of active malware attacks. On November 1, 2016, Microsoft Executive Vice President of the Windows and Devices Group Terry Myerson posted to Microsoft's Threat Research & Response Blog, acknowledging the vulnerability and explaining that a "low-volume spear-phishing campaign" targeting specific users had utilized "two zero-day vulnerabilities in Adobe Flash and the down-level Windows kernel." Microsoft pointed to Fancy Bear as the threat actor, referring to the group by their in-house code name STRONTIUM.[58]
Dutch ministries (February 2017)In February 2017, the General Intelligence and Security Service (AIVD) of the Netherlands revealed that Fancy Bear and Cozy Bear had made several attempts to hack into Dutch ministries, including the Ministry of General Affairs, over the previous six months. Rob Bertholee, head of the AIVD, said on EenVandaag that the hackers were Russian and had tried to gain access to secret government documents.[59]
In a briefing to parliament, Dutch Minister of the Interior and Kingdom Relations Ronald Plasterk announced that votes for the Dutch general election in March 2017 would be counted by hand.[60]
IAAF hack (February 2017)The officials of International Association of Athletics Federations (IAAF) stated in April 2017 that its servers had been hacked by the "Fancy Bear" group. The attack was detected by cybersecurity firm Context Information Security which identified that an unauthorised remote access to IAAF's servers had taken place on February 21. IAAF stated that the hackers had accessed the Therapeutic Use Exemption applications, needed to use medications prohibited by WADA.[61][62]
German and French elections (2016–2017)See also: French presidential election, 2017; German federal election, 2017; and 2017 Macron e-mail leaks
Researchers from Trend Micro in 2017 released a report outlining attempts by Fancy Bear to target groups related to the election campaigns of Emmanuel Macron and Angela Merkel. According to the report, they targeted the Macron campaign with phishing and attempting to install malware on their site. French government cybersecurity agency ANSSI confirmed these attacks took place, but could not confirm APT28's responsibility.[63] The APT group did not target Marine Le Pen, further showing Russia's involvement in the French Elections, since Putin has expressed his interest and hopes in Marine Le Pen's victory for both political and financial gains.[64]
The report says they then targeted the German Konrad Adenauer Foundation and Friedrich Ebert Foundation, groups that are associated with Angela Merkel's Christian Democratic Union and opposition Social Democratic Party, respectively. Fancy Bear set up fake email servers in late 2016 to send phishing emails with links to malware.[65]
International Olympic Committee (2018)On January 10, 2018, the "Fancy Bears Hack Team" online persona leaked what appeared to be stolen International Olympic Committee (IOC) and U.S. Olympic Committee emails, dated from late 2016 to early 2017, were leaked in apparent retaliation for the IOC's banning of Russian athletes from the 2018 Winter Olympics as a sanction for Russia's systematic doping program. The attack resembles the earlier World Anti-Doping Agency (WADA) leaks. It is not known whether the emails are fully authentic, because of Fancy Bear's history of salting stolen emails with disinformation. The mode of attack was also not known, but was probably phishing.[66][67]
Cyber Security experts have also claimed that attacks also appear to have been targeting the professional sports drug test bottling company known as the Berlinger Group. [68]