APT 030
Suspected attribution: China
Target sectors: Members of the Association of Southeast Asian Nations (ASEAN)
Overview: APT30 is noted not only for sustained activity over a long period of time but also for successfully modifying and adapting source code to maintain the same tools, tactics and infrastructure since at least 2005. Evidence shows that the group prioritizes targets, most likely works in shifts in a collaborative environment and builds malware from a coherent development plan. The group has had the capability to infect air-gapped networks since 2005.
Associated malware: SHIPSHAPE, SPACESHIP, FLASHFLOOD
Attack vectors: APT30 uses a suite of tools that includes downloaders, backdoors, a central controller and several components designed to infect removable drives and cross air-gapped networks to steal data. APT30 frequently registers its own DNS domains for malware CnC activities.
Further reading
APT30 and Lessons for ASEAN
https://www.us-cert.gov/HIDDEN-COBRA-North-Korean-Malicious-Cyber-Activity
http://www.intezer.com/lazarus-group-targets-more-cryptocurrency-exchanges-and-fintech-companies/
https://www.us-cert.gov/sites/default/files/publications/MAR-10135536.11.WHITE.pdf
TeleRAT_ Another Android Trojan Leveraging Telegram’s Bot API to Target Iranian Users.pdf
https://infosec.cert-pa.it/analyze/a76e9730dd08c15ef57919ac62a5d435.html
https://infosec.cert-pa.it/analyze/32afb5d9d3ed93fdaf0cae35063dd53e.html
Drive-by as a service_ BlackTDS _ Proofpoint.pdfAPT30’s development and refinement of a set of integrated tools, as well as their re-use of infrastructure over a period of 10 years, suggests a consistent long-term mission. This suite of tools includes downloaders, backdoors, a central controller, and several components designed to infect removable drives and cross air-gapped networks to steal data. APT30 frequently registers their own DNS domains for use with malware command and control (C2). Based on their presence in malware samples, some of the domains have been in use for many years. APT30 has a structured and organized workflow, illustrative of a collaborative team environment, and their malware reflects a coherent development approach. The group (or the developers supporting them) systematically labels and keeps track of their malware versioning. The malware uses mutexes and events to ensure only a single copy is running at any given time, and the malware version information is embedded within the binary. Malware C2 communications include a version check that allows the malware to update itself to the latest copy, providing a continuous update management capability. The controller software for APT30’s BACKSPACe backdoor (also known as “Lecna”) suggests the threat actors prioritize targets and may work on shifts. APT30 backdoors commonly use a twostage C2 process, where victim hosts contact an initial C2 server to determine whether they should connect to the attackers’ main controller. The controller itself uses a GUI that allows operators to prioritize hosts, add notes to victims, and set alerts for when certain hosts come online. Finally, an unused dialog box in the controller provides a login prompt for the current “attendant.” The group’s primary goal appears to be sensitive information theft for government espionage. APT30 malware includes the ability to steal information (such as specific file types), including, in some cases, the ability to infect removable drives with the potential to jump air gaps. Some malware includes commands to allow it to be placed in “hide” mode and to remain stealthy on the victim host, presumably for long-term persistence. APT30 predominantly targets entities that may satisfy governmental intelligence collection requirements. The vast majority of APT30’s victims are in Southeast Asia. Much of their social engineering efforts suggest the group is particularly interested in regional political, military, and economic issues, disputed territories, and media organizations and journalists who report on topics pertaining to China and the government’s legitimacy.
Targets: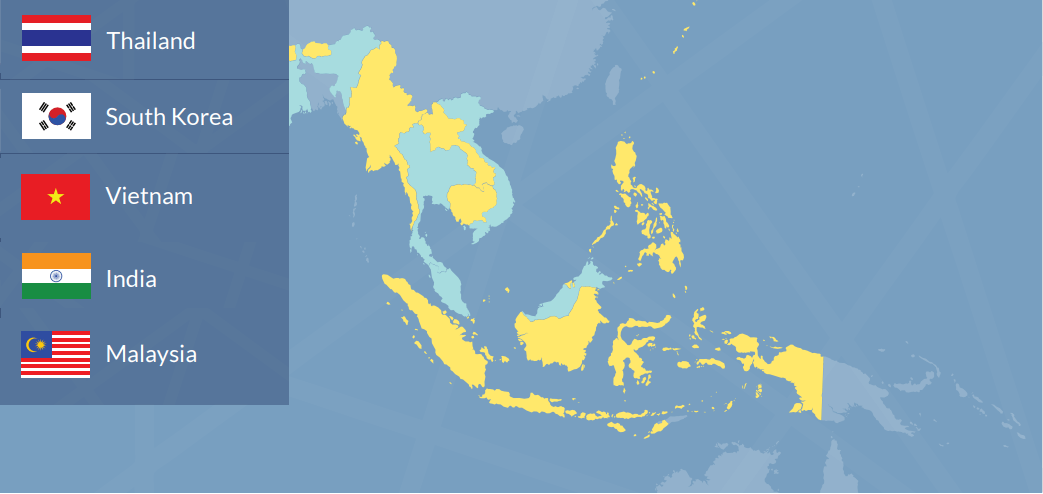
Based on our knowledge of APT30's targeting activity and tools, their objective appears to be data theft as opposed to financial gain. APT30 has not been observed to target victims or data that can be readily monetized (for example, credit card data, personally identifiable information, or bank transfer credentials). Instead, their tools include functionality that allows them to identify and steal documents, including what appears to be an interest in documents that may be stored on air-gapped networks.