APT 032
Also known as: OceanLotus Group
Suspected attribution: Vietnam
Target sectors: Foreign companies investing in Vietnam’s manufacturing, consumer products, consulting and hospitality sectors
Overview: Recent activity targeting private interests in Vietnam suggests that APT32 poses a threat to companies doing business, manufacturing or preparing to invest in the country. While the specific motivation for this activity remains opaque, it could ultimately erode the competitive advantage of targeted organizations.
Associated malware: SOUNDBITE, WINDSHIELD, PHOREAL, BEACON, KOMPROGO, OSX_OCEANLOTUS.D
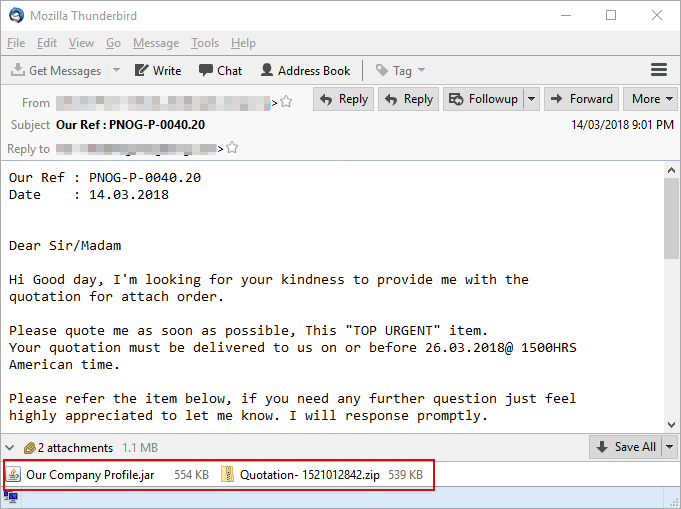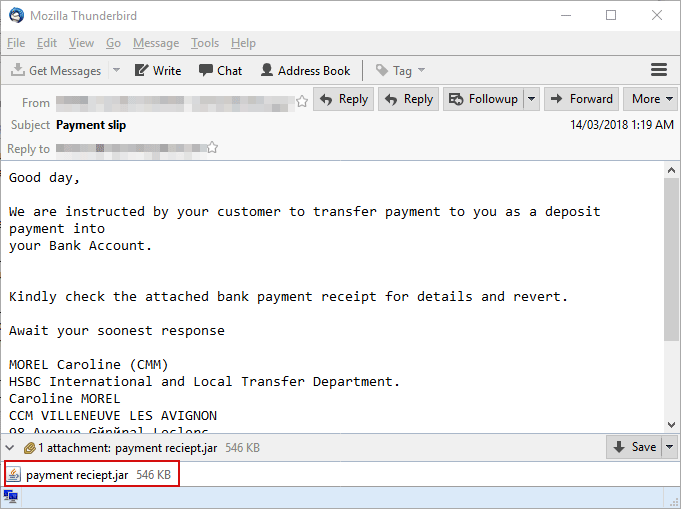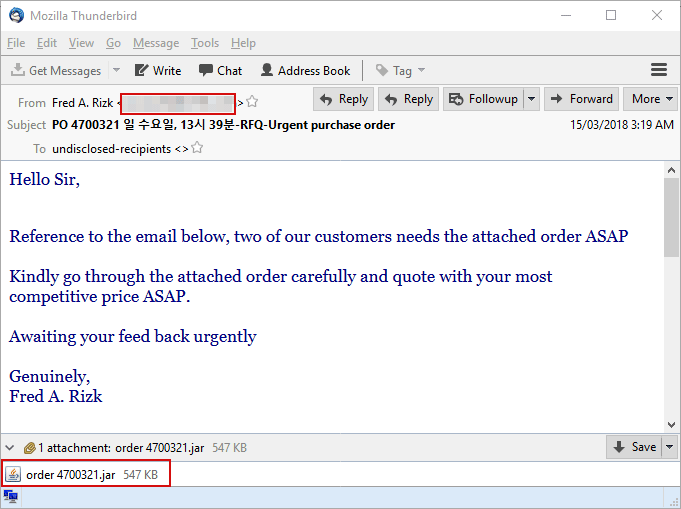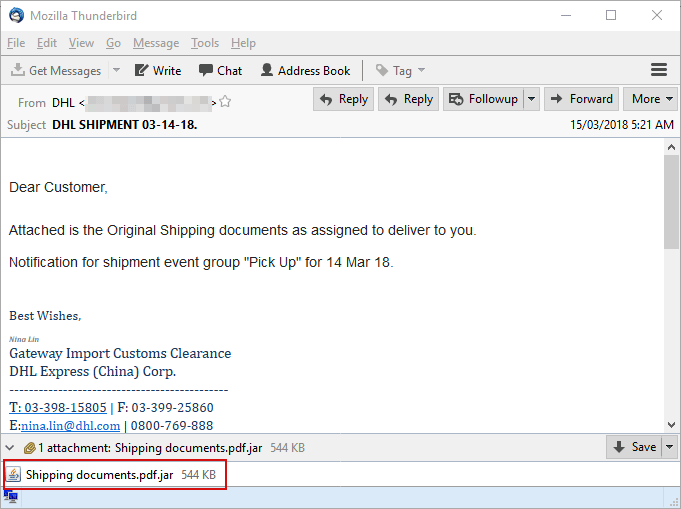
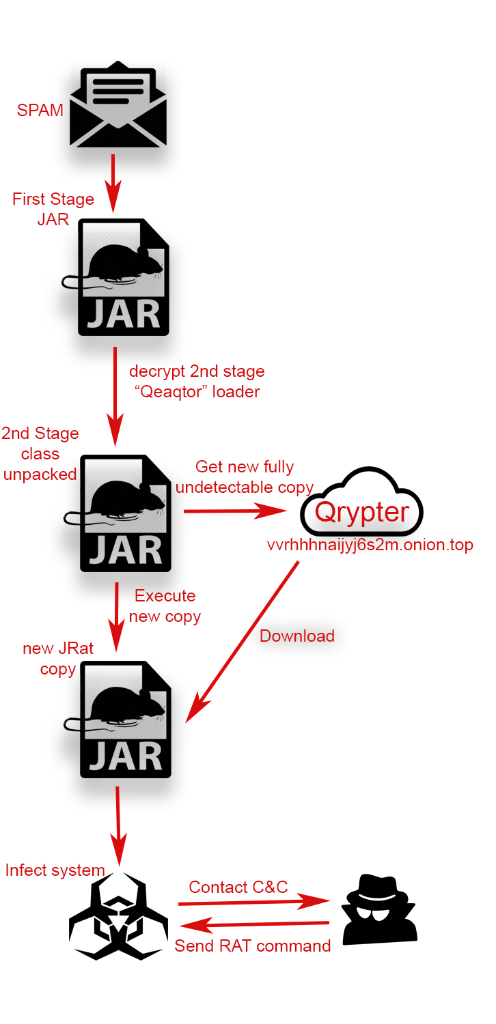
Attack vectors: APT32 actors leverage ActiveMime files that employ social engineering methods to entice the victim into enabling macros. Upon execution, the initialized file typically downloads multiple malicious payloads from a remote server. APT32 actors delivers the malicious attachments via spear phishing emails. Evidence has shown that some may have been sent via Gmail.
Latest findings (04th Apr 2018) show one of the quite rare OSX-malware being used by this group:
The MacOS backdoor was found in a malicious Word document presumably distributed via email. The document bears the filename “2018-PHIẾU GHI DANH THAM DỰ TĨNH HỘI HMDC 2018.doc,” which translates to “2018-REGISTRATION FORM OF HMDC ASSEMBLY 2018.doc.” The document claims to be a registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.
Further reading
- APT32 Blog
- APT32 Webinar
- https://www.us-cert.gov/HIDDEN-COBRA-North-Korean-Malicious-Cyber-Activity
- https://blog.checkpoint.com/2017/09/14/expensivewall-dangerous-packed-malware-google-play-will-hit-wallet/
- TeleRAT_ Another Android Trojan Leveraging Telegram’s Bot API to Target Iranian Users.pdf
- https://blog.avast.com/greedy-cybercriminals-host-malware-on-github
- https://researchcenter.paloaltonetworks.com/2018/03/unit42-sofacy-uses-dealerschoice-target-european-government-agency/
-
https://marcusedmondson.com/2019/02/02/apt-32-oceanlotus-sampled592b06f9d112c8650091166c19ea05a/
Download IOC’s from:
- https://pastebin.com/raw/PvKLJAWP
- https://www.us-cert.gov/sites/default/files/publications/MAR-10135536.11.WHITE.stix.xml
- https://www.us-cert.gov/sites/default/files/publications/TA18-074A_WHITE.csv
| C&C servers |
| Ssl[.]arkouthrie[.]com |
| s3[.]hiahornber[.]com |
| widget[.]shoreoa[.]com |
| SHA256 |
| Delivery document (W2KM_OCEANLOTUS.A):
2bb855dc5d845eb5f2466d7186f150c172da737bfd9c7f6bc1804e0b8d20f22a |
| Dropper (OSX_OCEANLOTUS.D): 4da8365241c6b028a13b82d852c4f0155eb3d902782c6a538ac007a44a7d61b4 |
| Backdoor (OSX_OCEANLOTUS.D): 673ee7a57ba3c5a2384aeb17a66058e59f0a4d0cddc4f01fe32f369f6a845c8f |