APT 039
Suspected attribution: Iran
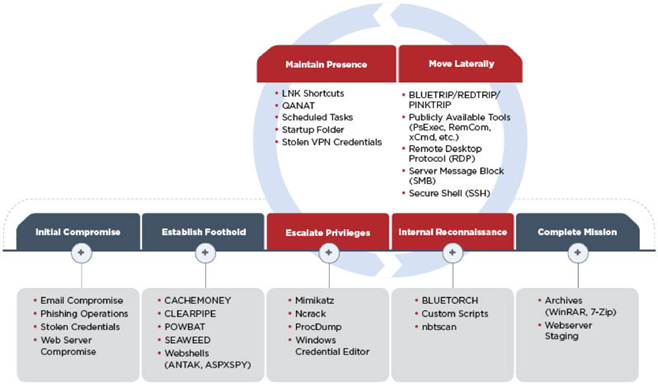
Target sectors: While APT39's targeting scope is global, its activities are concentrated in the Middle East. APT39 has prioritized the telecommunications sector, with additional targeting of the travel industry and IT firms that support it and the high-tech industry.
Associated malware: The group primarily leverages the SEAWEED and CACHEMONEY backdoors along with a specific variant of the POWBAT backdoor.
Overview: We believe APT38’s financial motivation, unique toolset, and tactics, techniques and procedures (TTPs) observed during their carefully executed operations are distinct enough to be tracked separately from other North Korean cyber activity. There are many overlapping characteristics with other operations, known as “Lazarus” and the actor we call TEMP.Hermit; however, we believe separating this group will provide defenders with a more focused understanding of the adversary and allow them to prioritize resources and enable defense. The following are some of the ways APT38 is different from other North Korean actors, and some of the ways they are similar:
Associated malware: A diverse suite of malware for initial intrusion and exfiltration. Along with custom malware used for espionage purposes, APT37 also has access to destructive malware.
Attack vectors: For initial compromise FireEye Intelligence has observed APT39 leverage spearphishing with malicious attachments and/or hyperlinks typically resulting in a POWBAT infection. In some cases previously compromised email accounts have also been leveraged, likely to abuse inherent trusts and increase the chances of a successful attack. APT39 frequently registers and leverages domains that masquerade as legitimate web services and organizations that are relevant to the intended target. Furthermore, this group has routinely identified and exploited vulnerable web servers of targeted organizations to install web shells, such as ANTAK and ASPXSPY, and used stolen legitimate credentials to compromise externally facing Outlook Web Access (OWA) resources. We have not observed APT39 exploit vulnerabilities.
Used Malware/Tools
Software
References
Techniques Used
| Domain | ID | Name | Use |
|---|---|---|---|
| Enterprise | T1090 | Connection Proxy | APT39 used custom tools to create SOCK5 proxies between infected hosts.[1] |
| Enterprise | T1003 | Credential Dumping | APT39 has used Mimikatz, Ncrack, Windows Credential Editor and ProcDump to dump credentials.[1] |
| Enterprise | T1002 | Data Compressed | APT39 has used WinRAR and 7-Zip to compress an archive stolen data.[1] |
| Enterprise | T1046 | Network Service Scanning | APT39 used a custom port scanner known as BLUETORCH[1] |
| Enterprise | T1060 | Registry Run Keys / Startup Folder | APT39 has maintained persistence using the startup folder.[1] |
| Enterprise | T1076 | Remote Desktop Protocol | APT39 has been seen using RDP for lateral movement and persistence.[1] |
| Enterprise | T1021 | Remote Services | APT39 used secure shell (SSH) to move laterally among their targets.[1] |
| Enterprise | T1053 | Scheduled Task | APT39 has created scheduled tasks.[1] |
| Enterprise | T1064 | Scripting | APT39 utilized custom scripts to perform internal reconnaissance.[1] |
| Enterprise | T1023 | Shortcut Modification | APT39 has modified LNK shortcuts.[1] |
| Enterprise | T1045 | Software Packing | APT39 has repacked a modified version of Mimikatz to thwart anti-virus detection.[1] |
| Enterprise | T1193 | Spearphishing Attachment | APT39 leveraged spearphishing emails with malicious attachments to initially compromise victims.[1] |
| Enterprise | T1192 | Spearphishing Link | APT39 leveraged spearphishing emails with malicious links to initially compromise victims.[1] |
| Enterprise | T1016 | System Network Configuration Discovery | APT39 has used nbtscan to discover vulnerable systems.[1] |
| Enterprise | T1033 | System Owner/User Discovery | APT39 used Remexi to collect usernames from the system.[2] |
| Enterprise | T1204 | User Execution | APT39 has sent spearphishing emails in an attempt to lure users to click on a malicious attachment or link.[1] |
| Enterprise | T1078 | Valid Accounts | APT39 has used stolen credentials to compromise Outlook Web Access (OWA).[1] |
| Enterprise | T1100 | Web Shell | APT39 has installed ANTAK and ASPXSPY web shells.[1] |