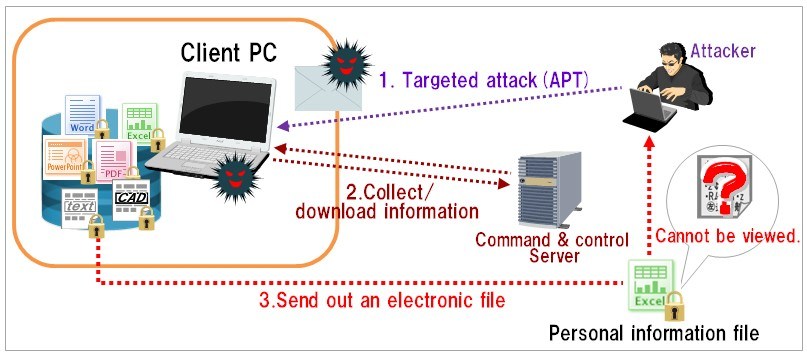
What we should know in Cyber about APT's
Definition of "APT" as per Wiki:
An advanced persistent threat is a set of stealthy and continuous computer hacking processes, often orchestrated by a person or persons targeting a specific entity. An APT usually targets either private organizations, states or both for business or political motives. APT processes require a high degree of covertness over a long period of time. The "advanced" process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The "persistent" process suggests that an external command and control system is continuously monitoring and extracting data from a specific target. The "threat" process indicates human involvement in orchestrating the attack.
Characteristics
- Objectives – The end goal of the threat, your adversary
- Timeliness – The time spent probing and accessing your system
- Resources – The level of knowledge and tools used in the event (skills and methods will weigh on this point)
- Risk tolerance – The extent the threat will go to in order to remain undetected
- Skills and methods – The tools and techniques used throughout the event
- Actions – The precise actions of a threat or numerous threats
- Attack origination points – The number of points where the event originated
- Numbers involved in the attack – How many internal and external systems were involved in the event, and how many people's systems have different influence/importance weights
- Knowledge source – The ability to discern any information regarding any of the specific threats through online information gathering (you might be surprised by what you can find by being a little proactive)
How it works.
The seven steps of the cyber kill chain by Lockheed Martin
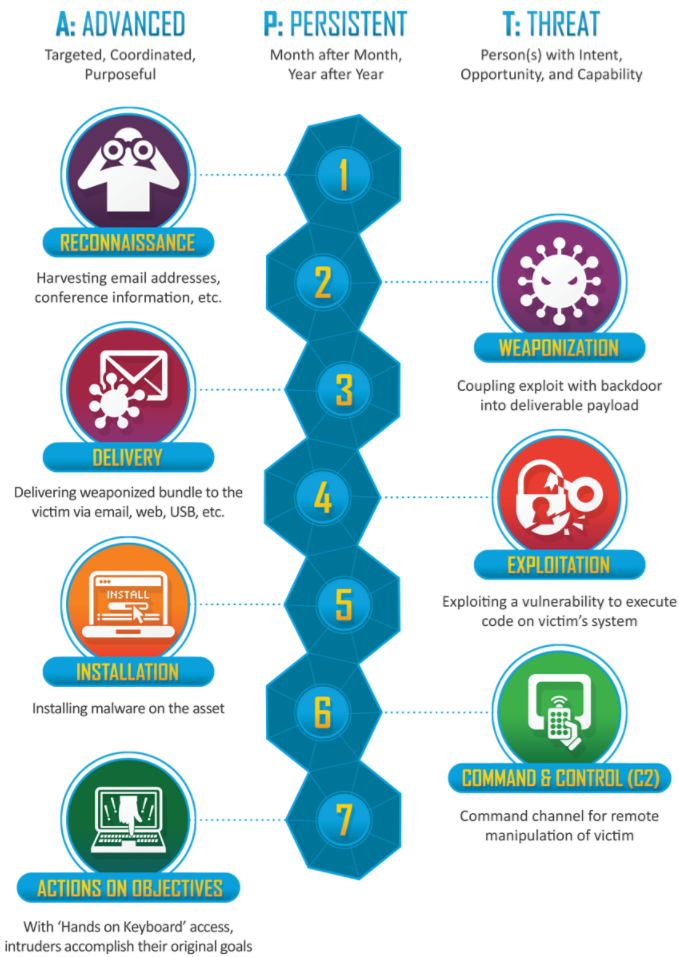
To improve your cyber security and successfully prevent, detect, and resolve advanced persistent threats, you need to understand how APTs work:
- Reconnaissance: The cyber criminal, is getting as much information possible about the target as possible. Either by public infrmation (WHOIS, DNS, etc.), using tools (TheHarvester, InSpy, Pastebin, Google hacks, Shodan, etc.) or by insider information he might get hold of using social engineering.
- Weaponization: From the targets and weaknesses discovered, the attacker chooses the best tools in his box to adopt it for it's specific use with the target.
- Delivery: The attacker uses the most proessing way of getting his above created weapon into the targets premessis. This usually includes social engineering (dropping usb sticks, sneeking, pigtailing, etc.), spear-fishing.
- Exploitation: Once the attackers have gained a foothold in the network through the malware they will try to expand their access to other parts of the network. The malware starts to monitor connections to servers in the network, gather information about installed programs and network users to identify server addresses, network structure and possibilities for expanding access. Unpatched programs or operating systems create possibilities for further expansion of the attackers access to network clients and servers. The attackers also perform active reconnaissance on the network themselves by connections through the malware clients. . The advanced malware probes for additional network access and vulnerabilities or communicates with command-and-control (CnC) servers to receive additional instructions and/or malicious code.
- Installation: Gathering and extracting information: After a while the attackers are successful and have found the wanted technical documentation and have access to the financial systems of the target. They slowly gather all the information on one of the clients they control and prepare the information for extraction. Finally they extract the information to a legitimate file storage application on the internet to make the extraction look as normal as possible. They also continue snooping around for other data they can sell and extract this as well.The malware typically establishes additional points of compromise to ensure that the cyber attack can continue if one point is closed.
- Command and Control: Once a threat actor determines that they have established reliable network access, they gather target data, such as account names and passwords. Even though passwords are often encrypted, encryption can be cracked. Once that happens, the threat actor can identify and access data. The attackers have continuously monitored progress through direct access through a backdoor created by the malware and by updates from the malware to servers on the internet
- Actions on objectives: The attackers now follow their original objectives on the target. At this point, the network is considered breached.
How common security is bypassed
Firewalls: Firewalls allow generic http Web traffic. Next-generation firewalls (NGFW) add layers of policy rules based on users and applications. NGFW consolidate traditional protections such as anti-virus and IPS but do not add dynamic protection that can detect next-generation threat content or behavior.
Try yourself at: http://http-evader.semantic-gap.de/ to evade you FW and IDS systems with the EICAR-test file.
IPS: Signatures, packet inspection, DNS analysis, and heuristics will not detect anything unusual in a zero-day exploit, especially if the code is heavily disguised or delivered in stages.
Anti-virus and Web malware filtering: Since the malware and the vulnerability it exploits are unknown (zero-day), and the website has a clean reputation, traditional anti-virus and Web filters will let it pass. The volume of vulnerabilities in browser plug-ins like Adobe and the exponential combinations of these browsers with operating systems make it hard for anti-virus vendors to keep up.
This only works if the source is “known bad” and you have additional tools installed that deal with such “reputational” information.
All AV need to store and scan the data for certain pattern. – Well this is how to evade such things. -> Run the malware only in memory and store no bit at the disk of your client.
Email spam filtering: Spoofed phishing sites use dynamic domains and URLs, so blacklisting lags behind criminal activities. It takes more than two days to shut down the average phishing site.
This is still the best route to success. – Humans are human. Think of the "Nigerian President"
Web filtering: Most outbound filtering blocks adult content or time-wasting entertainment sites. Less than a quarter of enterprises restrict social networking sites. In addition, dynamic URLs, hacks of legitimate websites, and addresses that are active for brief periods make static URL blacklisting obsolete.
Data loss prevention (DLP): DLP tools were primarily designed for personally identifiable information (PII)—strings like social security numbers, license numbers, or health data—and these tools are only as good as their rules. Most are too coarse-grained and cumbersome to detect exfiltration of credentials or intellectual property. Encryption of callback channels allows data to escape unseen. Their static approach does not match the dynamic nature of next-generation threats.
Countermeasures
"Keep vigilance and question everything"
The major APT's in detail from my subpages
Sources used within this writing:
![]()
A field guide to state-sponsored cyber attackers, who they target and how they operate
How to Protect Against the Next Generation of Cyber Attacks

CyberMonitor: APT & CyberCriminal Campaign Collection
![]()
Cyber Campaigns Central A list of over 125 (and growing!) cyber campaigns

MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™)

LISA'09 Michael K. Daly "The Advanced Persistent Threat"

CyberCriminals and their APT and AVT Techniques / February 23, 2015 By Pierluigi Paganini