BEAST
Browser Exploit Against SSL/TLS Attack (BEAST)
http://resources.infosecinstitute.com/ssl-attacks/
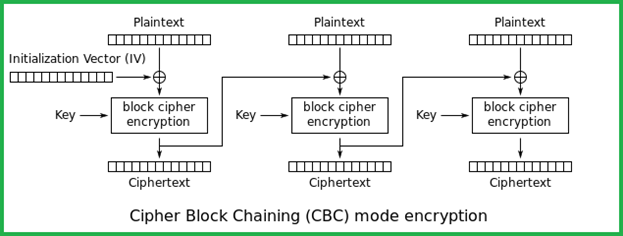
In CBC mode, to make each message unique, an initialization vector (IV) is used in the first block. An IV is a random string that is XORed with the plaintext message prior to encryption. Each block of plaintext is XORed with the previous cipher text block before being encrypted. In other words, each cipher text block depends on all plaintext blocks processed up to that point as shown in the figure below. It’s important to note that here IV is not a secret; it only adds randomness to the output. IV is sent along with the message in clear text format. With this background information, let us know focus on how the BEAST attack is accomplished.
Fix:
Use TLS >= 1.1 as this makes use of "explicit IV's"
-
Risk: low
- The attacker has to be in the same network and play a MITM attack.
- The attacker has to modify the traffic to see if the results match; as a result, multiple requests have to be sent in this process.
- The attacker can guess only one block at a time.
