While not having the amount of money to spend for sophisticated tools that are available I search for opensource tools to create my autopsy-useable forensic image.
Not having (very) great success yet, but still not having reached the end of the line. :-)
Hence everything here is still "work in progress"
Imaging using "adb backup"
ADB Cheat Sheet
https://www.automatetheplanet.com/adb-cheat-sheet/
C:\Users\Marcus\AppData\Local\Android\Sdk\platform-tools>adb backup -all -apk -shared -f N:\PIR\Tools\Jella.ab
WARNING: adb backup is deprecated and may be removed in a future release
Now unlock your device and confirm the backup operation…
Using this at a non-rooted device gives a .ab-file that needs to be converted to .tar, unpacked and can then be import as "Logicals files" in Autopsy.
Downside: This does not create a complete image while no right to access /data
Using this at a rooted device gives a .ab-file that needs to be converted to .tar, unpacked and can then be import as "Logicals files" in Autopsy.
Downside: You need to root the android first including the change of evidence.
Covert to .tar
Install JDK 7
https://www.oracle.com/java/technologies/javase/javase7-archive-downloads.html#license-lightbox
set JAVA_HOME=C:\Program Files\Java\jdk1.7.0_80
Install ABE
https://github.com/icepaule/android-backup-extractor
C:\Users\Marcus\AppData\Local\Android\Sdk\platform-tools\android-backup-extractor-master>gradlew.bat
Covert to .tar
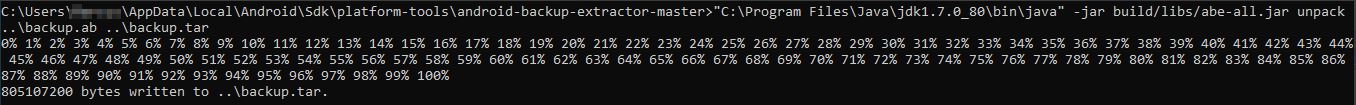
C:\Users\xxx\AppData\Local\Android\Sdk\platform-tools\android-backup-extractor-master>"C:\Program Files\Java\jdk1.7.0_80\bin\java" -jar build/libs/abe-all.jar unpack ..\backup.ab ..\backup.tar
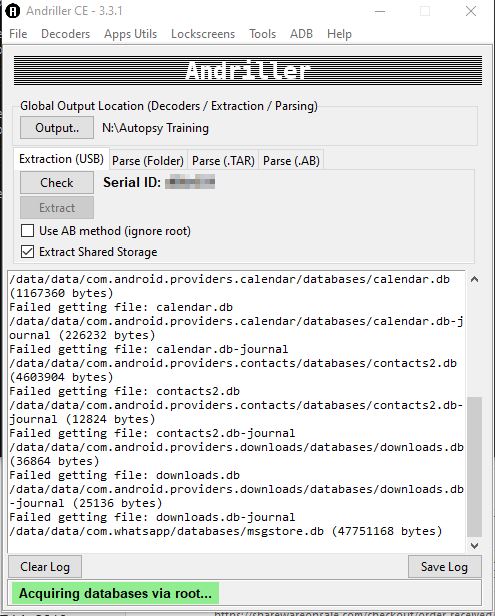
Imaging using "andriller"
Extract from a rooted device:
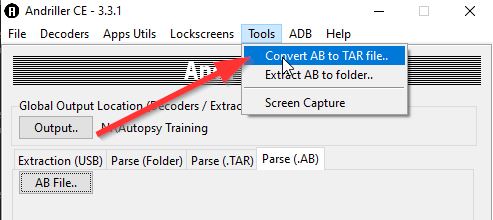
Convert into a tar-file:
Extract the tar file (with 7zip)
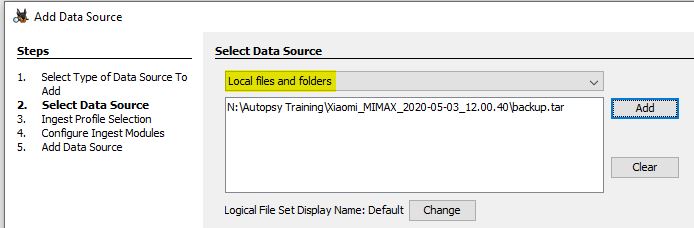
Now import as "logical file" into Autopsy:
Imaging a rooted android using busybox
At the target machine (having [target-IP])
nc -l [target-IP] -p 5555 > android_data.dd
at the source android (use "adb -d shell" and then "su -" to connect
dd if=/dev/block/bootdevice/by-name/userdata bs=1024k | busybox nc [target-IP] 5555
sources used:
- https://smarterforensics.com/wp-content/uploads/2014/06/android-memory-analysis-DI.pdf
- https://developer.android.com/studio/command-line/dumpsys
- https://hal.inria.fr/hal-01758679/document
- https://smarterforensics.com/wp-content/uploads/2014/06/Sushi-Smartphone-Forensics_Updated_20141025.pdf
- https://chethaka.wordpress.com/2013/05/02/run-adb-shell-and-get-instead-of/
- https://dfir.science/2017/04/Imaging-Android-with-root-netcat-and-dd.html
