The SIX STEPS of an Incident Response
"whack-a-mole" = unmögliches Spiel: Jumping from Identification straight to Eradication and tainting/missing out a lot of details.
First APT in 1998 "Moonlight Maze"
| No. | Name | Desciption | Actions | |||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Preparation | Preparation is as straightforward as making sure you have a trained incident response team, either employed, on retainer, or at least someone’s business card so you know who to call. | Create and test the response plan. | |||||||||||||||||||||
| 2 | Identification and Scoping | An incident is initially identified in any number of ways, leading you to start your response plan with only slight awareness of what the incident may be. The identification phase is meant to clear this part up. This phase also includes the investigation of the depth of the compromise, its source, and its success or failure. Identification is done through review of log files... lots and lots (and sometimes lots and lots and lots) of log files. | Consult your usecases from SIEM. | |||||||||||||||||||||
| 3 | Containment and Intelligence Development | Containment often happens concurrently with identification or immediately following. Damaged systems removed from production, devices are isolated, compromised accounts are locked down — the bleeding stops here. | avoid "whack-a-mole"
| |||||||||||||||||||||
| Intelligence-Driven Incident Response |
|
| ||||||||||||||||||||||
| 4 | Remediation Eradication | Eradication is exactly what it sounds like. Removing and remediating any damage discovered in the identification phase. This is normally done by restoring systems from backup and re-imaging workstation systems.
|
| |||||||||||||||||||||
| 5 | Recovery | Recovery is the testing of the fixes in the eradication phase and the transition back to normal operations. Vulnerabilities are remediated, compromised accounts have passwords changed or are removed altogether and replaced with other more secure methods of access. Functionality is tested and day to day business resumes. | Monitor LMS against occurance of gathered IOCs and TTPs | |||||||||||||||||||||
| 6 | Lessons learned / Threat intel consumption | The last phase is the one that many organizations skip, but it’s arguably the most important to prevent future incidents. Lessons Learned involves reviewing the steps that were taken during each phase and improving both your incident response capability and your security footprint are the important take-aways from this phase. | Publish IOC lists and TTPs via MISP and create usecases in SIEM |
Hunting team
| pce | Role | duty |
|---|---|---|
| 1 | Team lead | Nudge analyst on to the next artefact to look for to avoid him the impression of having missed something an search endless. |
| 1-2 | System und host forensicators | Have them the right and ability to access ALL sources/data within a company |
| 1-2 | Network forensicators | Have them the right and ability to access ALL sources/data within a company |
| 1 | Reverse Eng. | Analyse forensic samples and prove the valid IOC |
Cyber kill chain
| Step | Name | Action |
|---|---|---|
| 1 | Reconnaissance | Harvesting public available information. Finding vulnerabilities (scanning), email addresses, conference names, etc. |
| 2 | Weaponization | Building an exploit with backdoor into a deliverable payload |
| 3 | Delivery | Delivering the payload to the victim (via email, USB stick, drive-by, SQL-inject., etc.) |
| 4 | Exploitation | Exploiting a vulnerability to execute code on victims system i.e. phishing, ZeroDay use |
| 5 | Installation | Installing the malware on the asset |
| 6 | Command & Control | Establishing the command channel for remote manipulation of the victim |
| 7 | Actions on Objectives | "Hands on keyboard" access to accomplish their original goals |
ATT&CK
ATTA&CK focus on TTPs adversaries use to make decissions, expand access and execute their objectieves.
| Initial Access | Execution | Persistence | Privilege Escalation | Defense Evasion | Credential Access | Discovery | Lateral Movement | Collection | Command and Control | Exfiltration | Impact |
|---|
Hunt Evil - Know the "Normal"
| Image Path | system.exe |
|---|---|
| Parrent Proc. | None |
| Number of instances | One |
| User account | Local System |
| Start time | at boot |
| Description | run most kernel-module threats. Modules run under System (.sys files) but also several important DLLs as well as the ntoskrnl.exe |
| Image Path | %SystemRoot%\System32\smss.exe |
|---|---|
| Parrent Proc. | System |
| Number of instances | One master instance and other child instance per session. Children exit after creating theit session. |
| User account | Local System |
| Start time | seconds after boot for the master instance |
| Description | SessionManager creates new sessions. PID of smss.exe < csrss.exe |
| Image Path | %SystemRoot%\System32\wininit.exe |
|---|---|
| Parrent Proc. | smss.exe (but it exited after spawning, so looks like been called by a non-existent process |
| Number of instances | One |
| User account | Local System |
| Start time | seconds after boot for the master instance |
| Description | wininit.exe starts:
|
| Image Path | %SystemRoot%\System32\RuntimeBroker.exe |
|---|---|
| Parrent Proc. | svchost.exe |
| Number of instances | One or more |
| User account | logged on users |
| Start time | varies |
| Description | RuntimeBroker.exe is a proxy for UWP and Windows API. |
| Image Path | %SystemRoot%\System32\taskhostw.exe |
|---|---|
| Parrent Proc. | svchost.exe |
| Number of instances | One or more |
| User account | Local System and logged on user |
| Start time | varies |
| Description | Generic host process for windows tasks. It runs a continous loop and waits for trigger events. |
| Image Path | %SystemRoot%\System32\winlogon.exe |
|---|---|
| Parrent Proc. | smss.exe (but it exited after spawning, so looks like been called by a non-existent process |
| Number of instances | One or more |
| User account | Local System |
| Start time | seconds after boot for the first instance |
| Description | winlogon.exe handles interactive user logons and logoffs. It launches LogonUI.exe which passes credentials to lsass.exe for validation. One authenticated, winlogon loads the NTUSER.DAT into HKCU and start the user's shell (i.e. explorer.exe) via userinit.exe. |
| Image Path | %SystemRoot%\System32\csrss.exe |
|---|---|
| Parrent Proc. | smss.exe (but it exited after spawning, so looks like been called by a non-existent process |
| Number of instances | Two or more |
| User account | Local System |
| Start time | seconds after boot for the first two instance |
| Description | The Client/Server Run-Time Subsystem is the user-mode process for the Windows subsystem. Use of RDP and fast user swiitching creates each on new process of csrss.exe |
| Image Path | %SystemRoot%\System32\services.exe |
|---|---|
| Parrent Proc. | wininit.exe (but it exited after spawning, so looks like been called by a non-existent process |
| Number of instances | One ONLY |
| User account | Local System |
| Start time | seconds after boot |
| Description | Implements the unified background process manager (UBPM), which is responsible for background activities such as services and scheduled tasks. It implements also the SCM that loads services and device drivers marked for auto-start. |
| Image Path | %SystemRoot%\system32\svchost.exe |
|---|---|
| Parrent Proc. | services.exe (most often) |
| Number of instances | Many (generally at least 10) |
| User account | Local System, Network Service, Local Service. Win10 also logged-on user |
| Start time | seconds after boot |
| Description | Generic host process for Windows services. Used to run service DLLs. Uses the -k parameters for grouping similar services. >Win10 1703 >3,5GB RAM, expect more than 50 instances. |
| Image Path | %SystemRoot%\System32\lsaiso.exe |
|---|---|
| Parrent Proc. | wininit.exe |
| Number of instances | zero or one |
| User account | Local System |
| Start time | seconds after boot |
| Description | Runs only if Credential Guard is active. lsass.exe uses lsaiso.exe to rovide safe storing by running in a context that is isolated from other process through hardware virtualization technology. |
| Image Path | %SystemRoot%\explorer.exe |
|---|---|
| Parrent Proc. | userinit.exe (but it exited after spawning, so looks like been called by a non-existent process |
| Number of instances | One or more per interactively logged-on user |
| User account | logged-on user |
| Start time | First instance starts when the owner's interactive logon begins |
| Description | At its core, Explorer provides users access to files, but also to Desktop, Start Menu, Taskbar, control panel and application launching. |
Malware Persitence Mechanisms
AutoStart Persistence Locations (ASEPs)
Most popular registry_
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Runonce
Software\Microsoft\Windows\CurrentVersion\Runonce
Software\Microsoft\Windows\CurrentVersion\Run
Software\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit\
.. file
%AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Scheduled Tasks
at.exe runs as SYSTEM (depreciated but still present in WinXP and Windows7+
The use is recorded at at*.job files and Schdlgu.txt (XP)
schtasks.exe
C:\Windows\Tasks and C:\Windows\System32\Tasks
Both (at.exe and schtasks.exe) can be used on remote4 machines.
See: https://gladiator-antivirus.com/forum/index.php?showtopic=24610
Windows Services
New service creation (7045, 4688). Start value 0x02 will start at boot
IPRIP: RIP listener Service APT1
Service Replacement (GlasRAT) used the disabled "RasAuto" service
Service Failure Recorvery uses a service crash to recover with the implanted malware as recovery option. (!!!)
→ Kansa Get-SvcFail.ps1)
DLL Perstistance Attacks
Hijacks
While looking at the DLL search order, find a way to load the malicious dll before the legetime DLL.
Sample: Windows2000, explorer.exe (from \Windows) will load also the ntshuri.dll that an attacker had placed at \Windows instead of using the legetime DLL in \Windows\System32 that has restictions on writing at.
The common search order is:
- Side-ba-Side components
- KnownDLL list
- Application Directory
- C:\Windows\System32
- C:\Windows\system
- C:\Windows
- Applications registered App Paths directories
- System PATH
Phantom DLL hijacking
Use long forgotten DLLs that are still attempted to be loaded but are not existing anymore. Like fxsst.dll of the Fax service in the \Windows\System32 folder
DLL Side-Loading
Use the SxS function to present an "updated" version of the existing legetime DLL to the program. The presented version is the malicious code.
See the PlugX RAT or NetTraveler for the use of this technique.
WMI Event Consumer Backdoors
WMI came active with Windows2000
This technique requires three discrete steps (Managed Object Format MOF-Format: MOF)
- An event must be created describing a specific trigger to detect (i.e trigger every 20 sec.)
- An event consumer is added to the system with a script (or executable) to run
- The event and consumer are tied together via a binding and the persistence mechanism is loaded into the WMI repository.
Has been used by STUXNET MS10-016
Sysinternals autoruns and Kansa PowerShell framework helps to find such suspects
Hunting Accross the Enterprise
Using WMIC
i.e.:
Find Executables that do not reside in %Windows%-like folders aka find executables outside of trusted paths:
wmic /node:<remote-ip> /user:<username> PROCESS WHERE (NOT ExecutablePath LIKE "%Windows%") get name, executablepath, ParentProcessID
From: https://www.sans.org/blog/wmic-for-incident-response/
Examine Auto Start processes:
wmic /node:<remote-ip> /user:<username> startup list full
Find who is logged on to a computer's console:
wmic /node:<remote-ip> /user:<username> ComputerSystem Get UserName
Query local user accounts:
wmic /node:<remote-ip> /user:<username> useraccount list full
Find the path to a specific running executable and its parent process (for all, leave off ?where name='):
wmic /node:<remote-ip> /user:<username> process where get ExecutablePath,parentprocessid
Find command line invocation of a specific executable as well as the creation time for the process (for all, leave off ?where name='). Reference this Microsoft TechNet article for converting the time:
wmic /node:<remote-ip> /user:<username> process where get name,processid,commandline,creationdate
Find status of a specific service?note that 'caption' is needed in the where clause, but it is actually the 'displayname' (for all, leave off ?where caption='):
wmic /node:<remote-ip> /user:<username> service where caption="PsExec" get displayname,startname,state,status,startmode
Using PowerShell
(!!!) powershell.exe -ExecutionPolicy ByPass -file .\script.ps1 (!!!)
PS = Default in Win7/8/10 and Server 2008/2012/2017
See also: SANS Live Response Using PowerShell
List the running processes:
Get-WmiObject win32_process | select processname, ProcessId, CommandLine
List the creation date of the running processes:
Get-WmiObject win32_process | select
processname,@{NAME='CreationDate';EXPRESSION={$_.ConvertToDateTime($_.CreationDate)}},ProcessId,CommandLine |sort CreationDate -desc | format-table –auto -wrap
Save the successful logon events to a text file
$UserDirectory = (gi env:\userprofile).value Get-WinEvent -FilterHashtable @{Logname='security';ID=4624} | select TimeCreated,ID,Message | ft –auto -wrap | out-file $UserDirectory\desktop\Event-4624.txt
Check a cool PS1 script from Sajeev.Nair that I adopted: https://github.com/icepaule/defender/blob/master/tools/windows/liveresponsedesktop.ps1
PowerShell PSREMOTING
While you have created some PS for the local machine, use it in an enterprise wide scenario to collect you the required information to safe time and resources.
Prerequsit:
At the target machine, run: "Enable-PSRemoting -force"
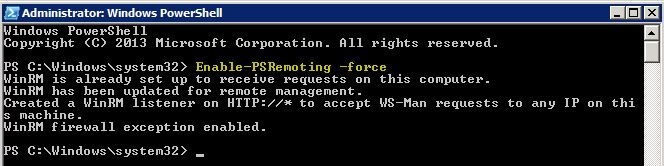
Or via remote command with psexec
psexec \[computer name]-u [admin account name]-p [admin account password]-h -d powershell.exe "enable-psremoting -force"
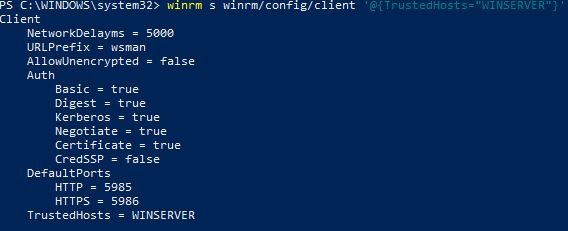
And add the destination to the trusted group:
winrm s winrm/config/client '@{TrustedHosts="WINSERVER"}'
Create a variable with your domain credentials. This way the credentials are not stored in plain text at the CLI.
$cred = get-credential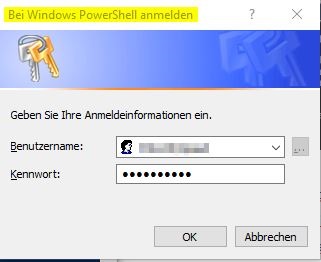
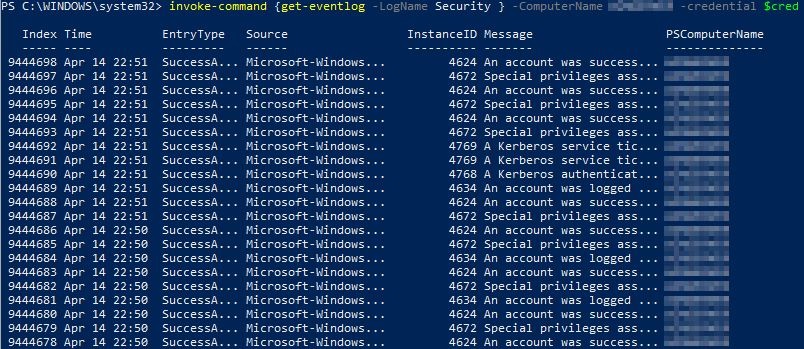
Now using the "invoke-command" to psremote the PS to the target machine:
invoke-command {get-eventlog -LogName Security } -ComputerName "the target"-credential $cred
The final action:
invoke-command { Get-WmiObject win32_process | select processname,@{NAME='CreationDate';EXPRESSION={$_.ConvertToDateTime($_.CreationDate)}},ProcessId,CommandLine | sort CreationDate -desc } -ComputerName WINSERVER -credential $cred
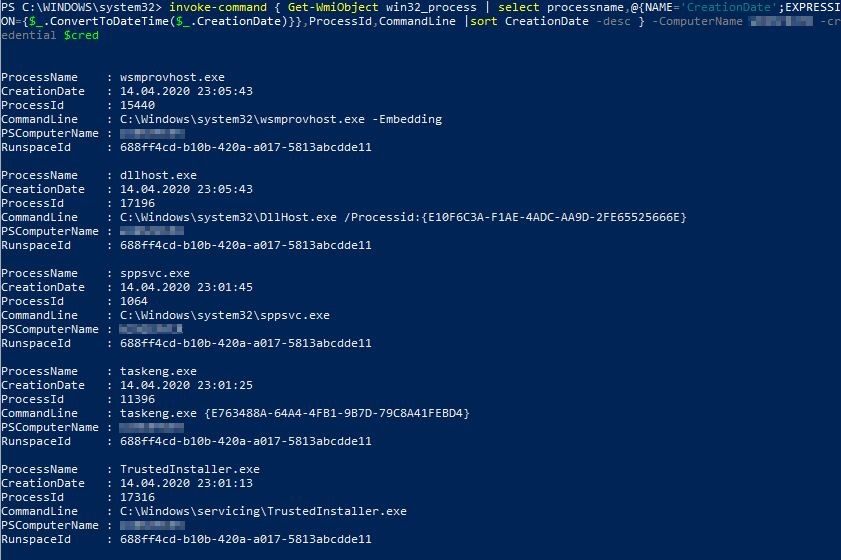
KANSA: The Swiss-Army-Knife for PowerShell
Prerequsit:
https://github.com/icepaule/Kansa
logparser.exe
Remote Server Adminstration Tools (or simply activate via "add internal features".
Create a variable with your domain credentials
$cred = get-credential
.\kansa.ps1 -TargetList .\hostlist -Pushbin -credential $cred
After that, you'll find the created files (.csv) in the unique output folder: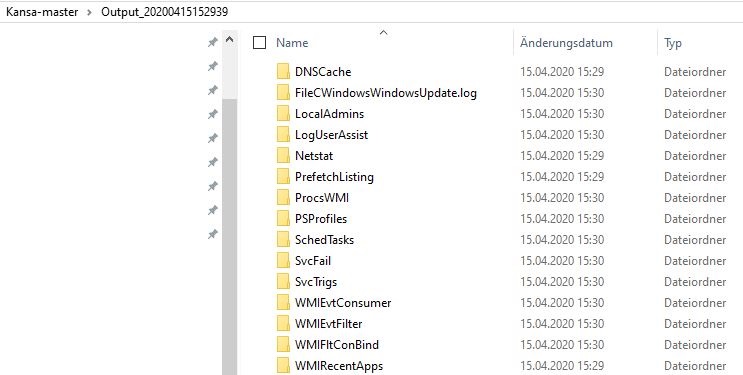
WMI Attacks
Reconnaisence:
- WMIC.exe process get CSName,description,ExecutablePath,ProcessId
- wmic useraccount list full
- wmic group list full
- wmic netuse list full
- wmic qfe get Caption,Description,HotFixID,Installed
- wmic startup get Caption,Command,Location,User
(!!!) add "/node:<remote-ip> /user:<username>" for remote actions (!!!)
Find unquoted autostart items NOT in %WINDOWS%:
WMIC.exe /node:10.1.1.111 /user:mpauli service get name,displayname,pathname,startmode | findstr /i "Auto" | findstr /i /v "C:\Windows\\" | findstr /i /v """
