Evading VM detection
Modern malware checks the environment it runs in to detect any virtual surrounding in the use of being quite to avoid sandboxes analysing.
To avoid this, one has to do some tricks, so the malware "thinks" it's on a real system and will start it's action, while you can analyse it's behaviour.
To check, if your virtual victim is affected by this detections, use some tools that give you a scope of virtual environment detections. A cool tool for that is "pafish". Just analyse the EXE with your cuckoo and check the detections.
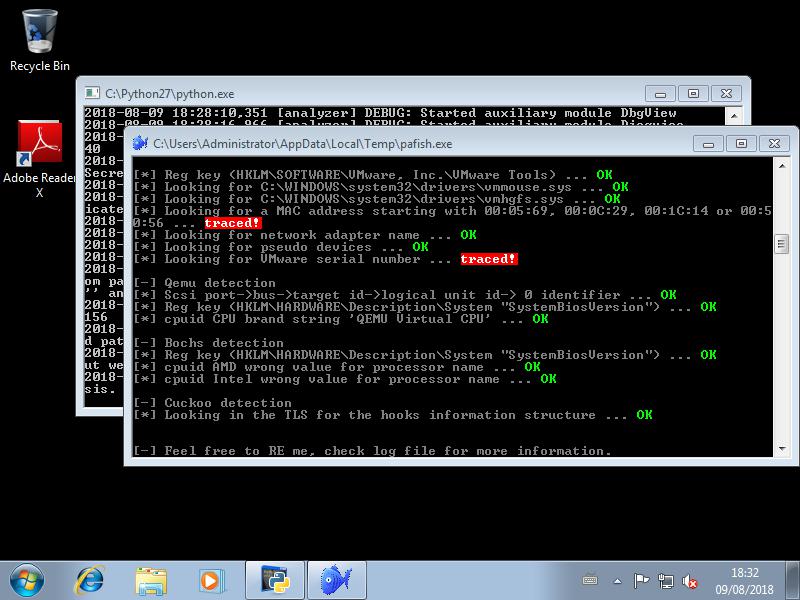
From the results given by pafish, you can go pretty straight forward to the setting and actions you have to implement to avoid the detection of your virt. environment.
Some good resources I found to accomplish that are:
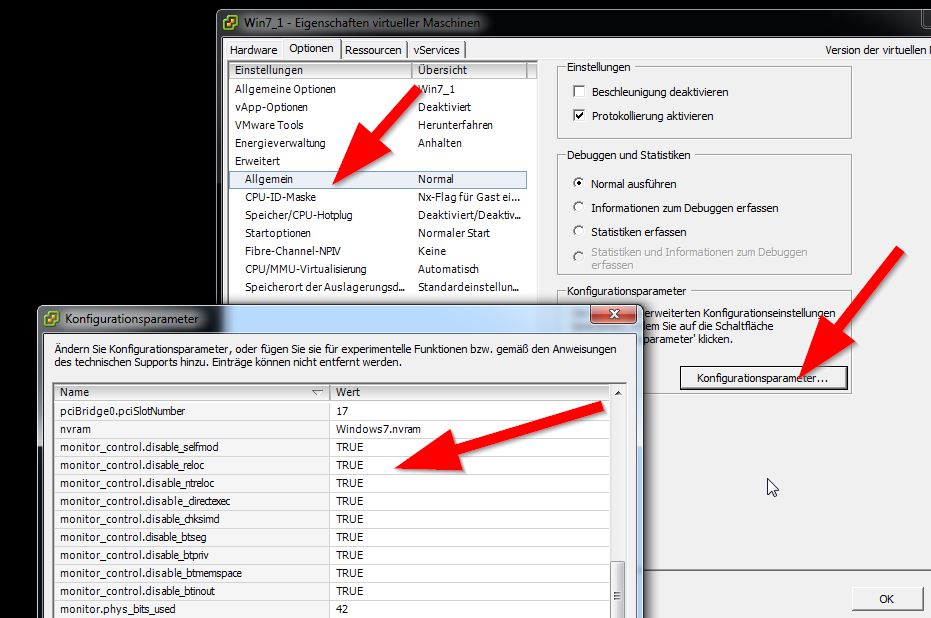
What helped me was adding below data to the .vmx file while powered off:
isolation.tools.getPtrLocation.disable = “TRUE”
isolation.tools.setPtrLocation.disable = “TRUE”
isolation.tools.setVersion.disable = “TRUE”
isolation.tools.getVersion.disable = “TRUE”
monitor_control.disable_directexec = “TRUE”
monitor_control.disable_chksimd = “TRUE”
monitor_control.disable_ntreloc = “TRUE”
monitor_control.disable_selfmod = “TRUE”
monitor_control.disable_reloc = “TRUE”
monitor_control.disable_btinout = “TRUE”
monitor_control.disable_btmemspace = “TRUE”
monitor_control.disable_btpriv = “TRUE”
monitor_control.disable_btseg = “TRUE”
Just change your victim machine as per below pic and add above config as new entrys.
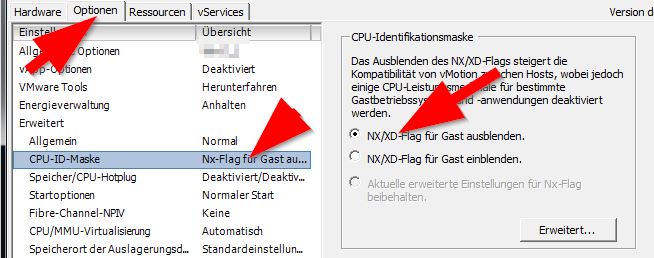
Deactivate the CPU ID:
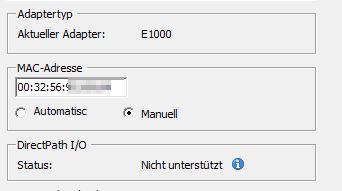
Change the MAC address to a non VMWARE class:
To see the outcome of these changes, reanalyse the pafish.exe ...
