Corona build of a honeypot
While Bavaria has limited social interactions due to Corona, we all are forced to stay at home where ever possible. So I was cleaning up my stuff right before I wanted to start with my yearly tax report. As this work is always a pain, I realized an old raspberry PI being a perfect excuse of doing something more fun.
So big thanks to cowrie@cowrie.org for his great work bringing cowrie to life.
So this is how you can build a little (very simple) honeypot (for telnet and ssh) and visualize the data in Splunk for fun.
Start with a fresh install of a raspberry pi and set it up to your personal needs.
Install cowrie
sudo apt-get install git python-virtualenv libssl-dev libffi-dev build-essential libpython3-dev python3-minimal authbind virtualenv
sudo adduser --disabled-password cowrie
sudo su - cowrie
git clone http://github.com/cowrie/cowrie
cd cowrie
virtualenv --python=python3 cowrie-env
source cowrie-env/bin/activate
pip install --upgrade pip
pip install --upgrade -r requirements.txt
cp etc/cowrie.cfg.dist etc/cowrie.cfg
I did some tweaks to my personal needs here but the mandatory part is to enable ssh and telnet.
[telnet] enabled = true
While my raspberry has a small LCD display, I wanted to have a little monitoring of the actual stuff that is going on. So I added below line to have a simple tail running after boot.
vi /etc/xdg/lxsession/LXDE-pi/autostart # (before screensaver line)
@lxterminal --command tail -f /home/cowrie/cowrie/var/log/cowrie/cowrie.log
The Splunk part of cowrie is quite easy:
[output_splunk]
enabled = true
url = https://[your splunk]:8088/services/collector/event
token = [the token from your input config]
index = cowrie
sourcetype = cowrie
source = cowrie
Splunk server config
In Splunk, enable the HTTP Event Collector (go to Settings->Add Data)
Do not enable Indexer Acknowledgment
Copy the authorization token for later use
Modify cowrie.cfg to enable the [splunk] section
Add URL to HTTP Event Collector and add the authorization token
Optionally enable sourcetype, source, host and index settings
After that use below probs.conf for the sourcetype
[cowrie]
DATETIME_CONFIG = CURRENT
INDEXED_EXTRACTIONS = json
KV_MODE = none
LINE_BREAKER = ([\r\n]+)
NO_BINARY_CHECK = true
category = Structured
description = cowrie honeyport sourcetype
disabled = false
pulldown_type = true
Splunk searches
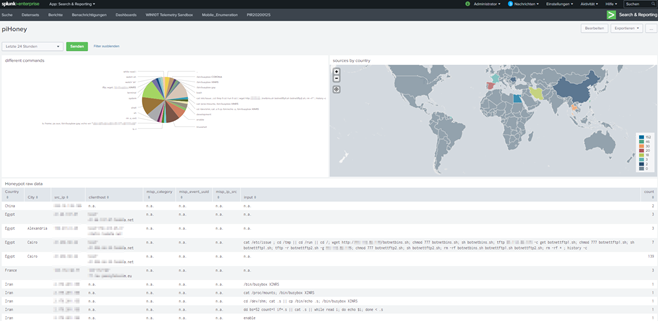
The above picture of my dashboard is made of the three below searches:
- index="cowrie" sourcetype="cowrie" | stats count by input
- index="cowrie" sourcetype="cowrie" | iplocation src_ip | stats count by Country| geom geo_countries allFeatures=True featureIdField=Country | sort - count
- index="cowrie" sourcetype="cowrie" | regex src_ip!="127.0.0.1" | lookup dnslookup clientip as src_ip | iplocation src_ip | fillnull value="n.a." | stats count by Country City src_ip clienthost misp_category misp_event_uuid misp_ip_src input