Simple *all traffic* interception of an Android app
The aim: Catch *all* traffic that is created by an Android app and capture it for analysis.
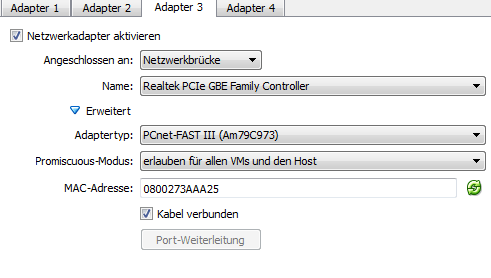
First create a new interface within Andy. (Now it's good to have a virtual box)
While the most used tool to redirect traffic in linux is "iptables", it's kind of complicated to identify the source of a traffic being a specific application.
The parameters for iptables I could find only allowed to tap traffic of:
- a specific user
- a specific source port
- a specific destination ip
- a specific destination port
Nothing from above list would let me (easily) identify *all* traffic that a certain programm creates.
BUT, there is a cool feature with android. - Every programm/app runs as it's own user, so the task is quite easy to achieve.
Install busybox on your android 
Install a shell o your android 
become root 
find the app/user your intrested in 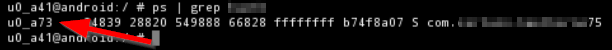
craft your iptables command
