Simple http/https traffic interception to test the security of a specific app
My main aim for this action was, to gather the risk of using a specific app.
Just install your app to analyse first. - Install it only, do not start it yet!
The actions of the access right the app has on the device itself shall not be part of this excersize. Although I checked it using the right section android itself brings with it.
Anyway, lets focus on how to get the data that this specific app sends around.
The tool that I found that could help me with achieving this goal was a smal (transparent) proxy, originally developed to get around some school-lan limitations.
 Available in the Google Play Store
Available in the Google Play Store
After installing it, it's pretty easy on how to use it.
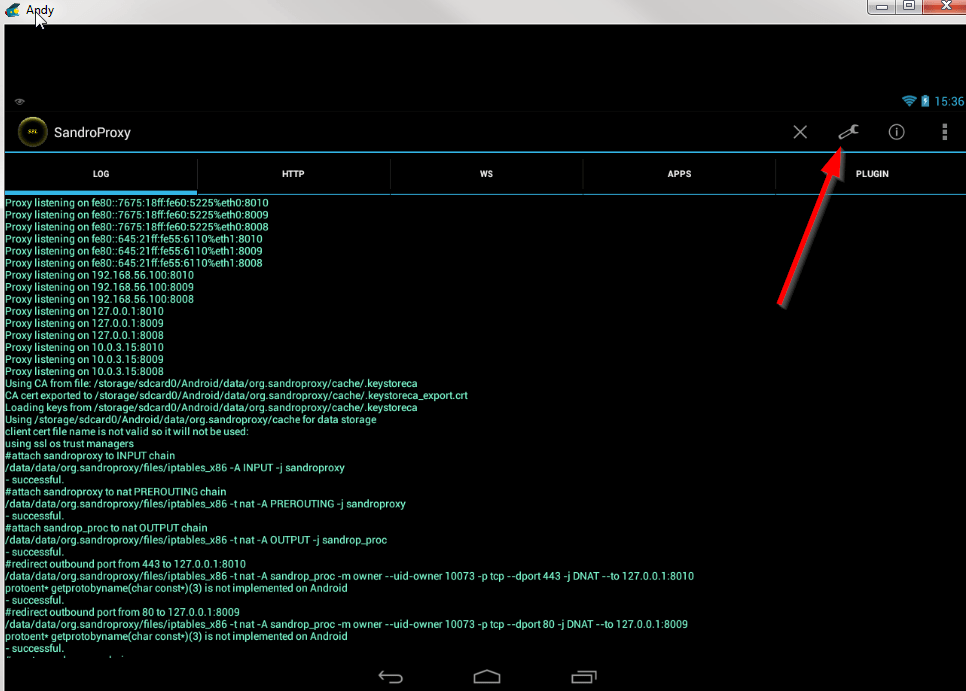
Use the developer mode:
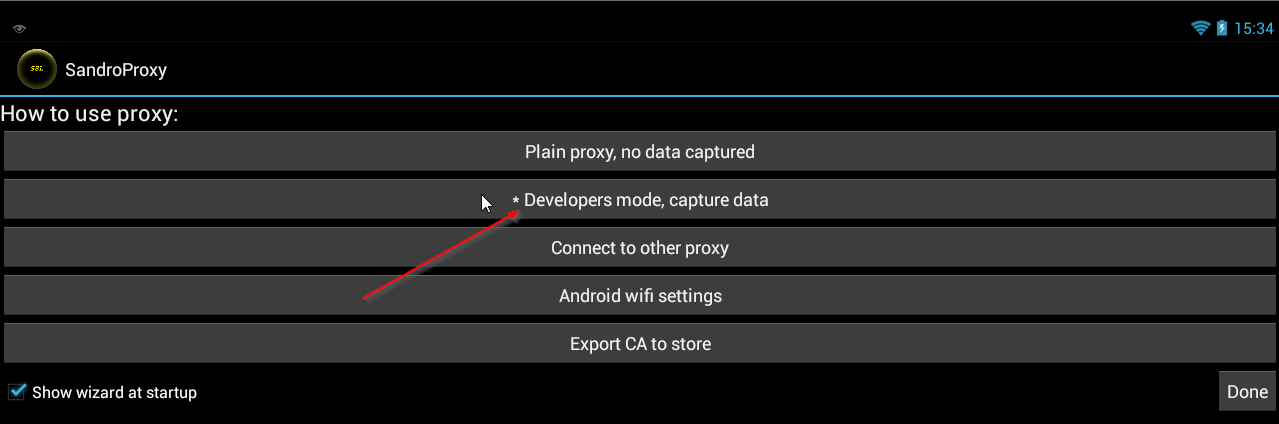
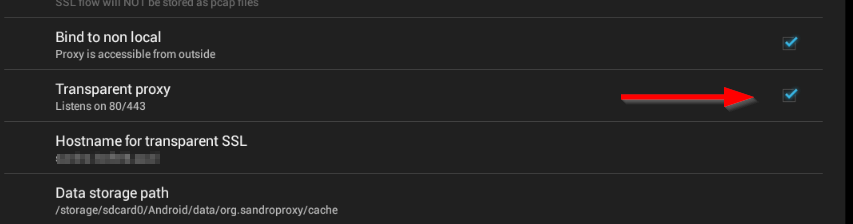
After activating the "Developers Mode" and clicking [OK], go to the settings and activate the transparrent proxy.
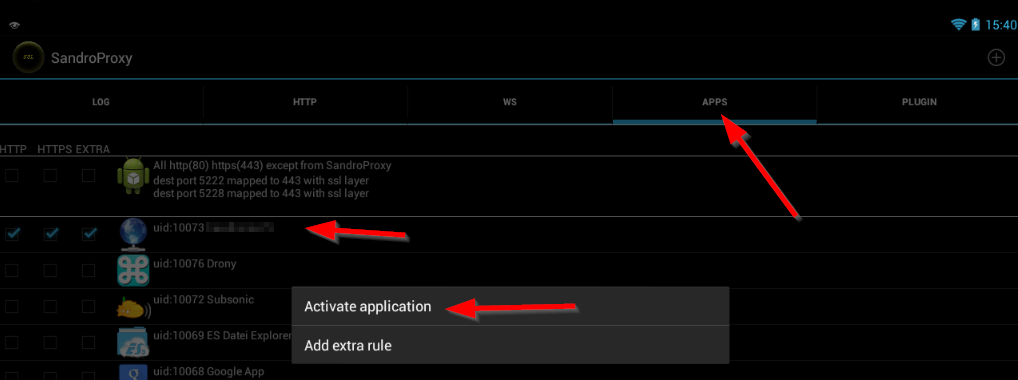
After accepting the settings, go to "Apps", find you app and activate all three ticks. Then long click it with you mouse and use "Activate Application".
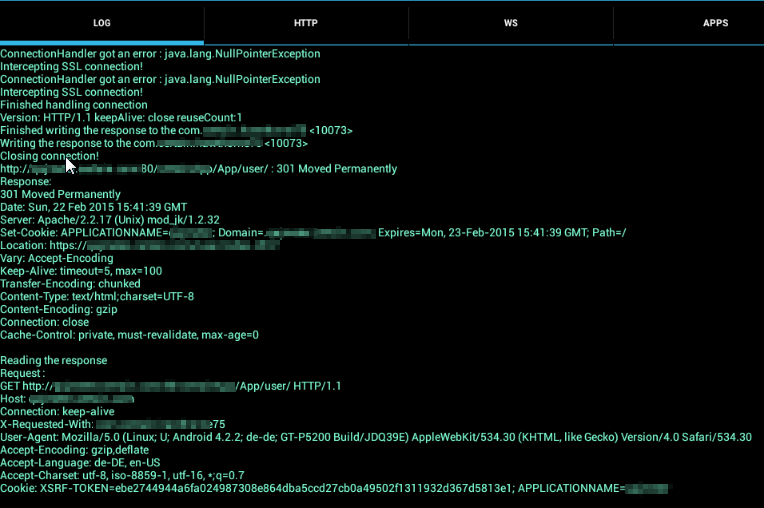
Your now been taken to your running application. (Please note that all specific information has been obvuscated)
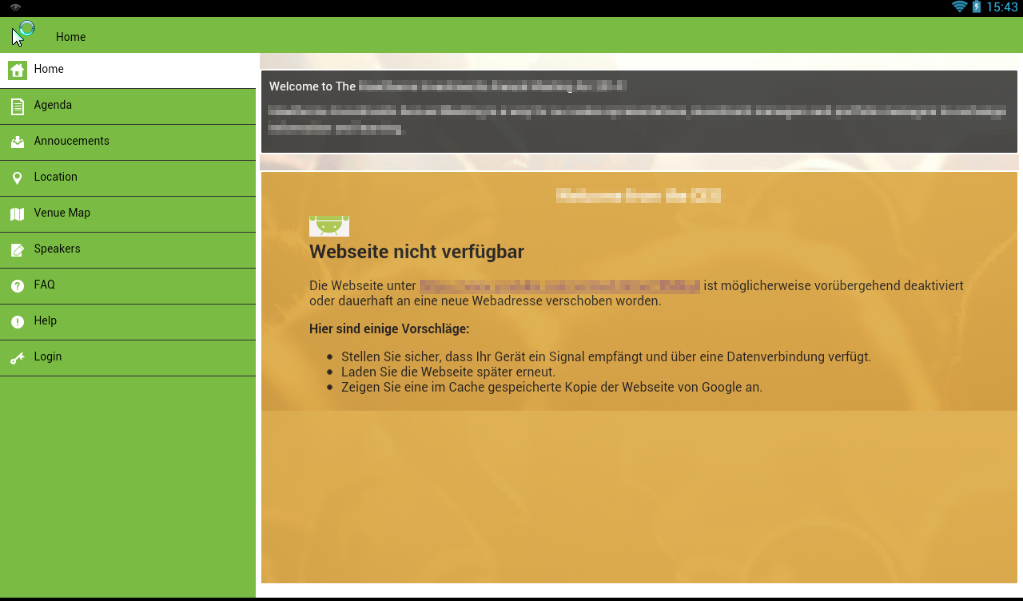
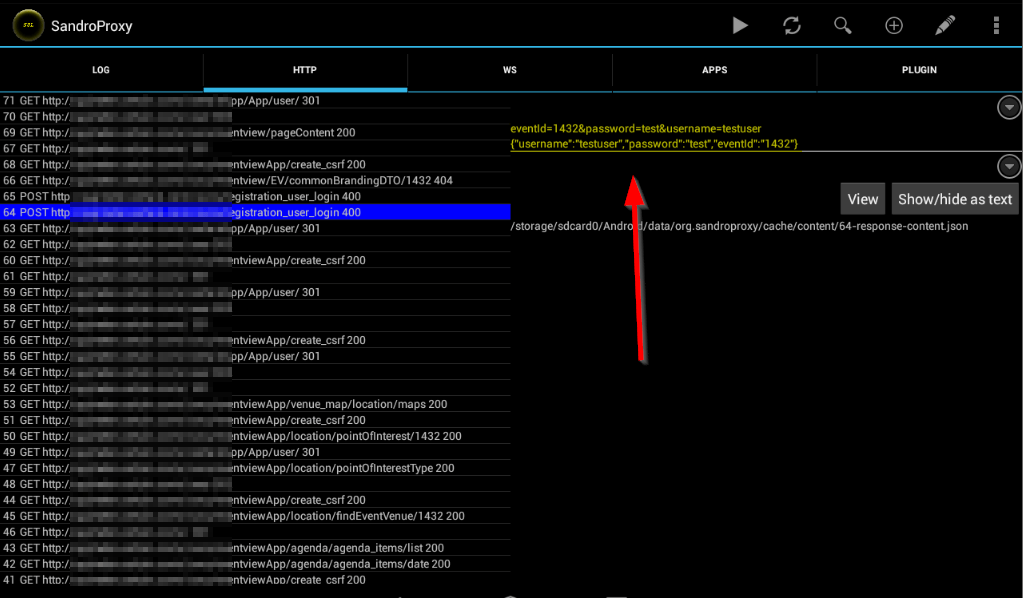
If your now going back to your Sandro Proxy app, you'll see what kind of communication the app uses.
While long clicking on the log area, you can mark the content and import it (i.e.) to gmail and send the output to our mail address for further investigation.
If going to the http part, you'll also see the clear text data that was transfered:
Just like my beloved xplico does.