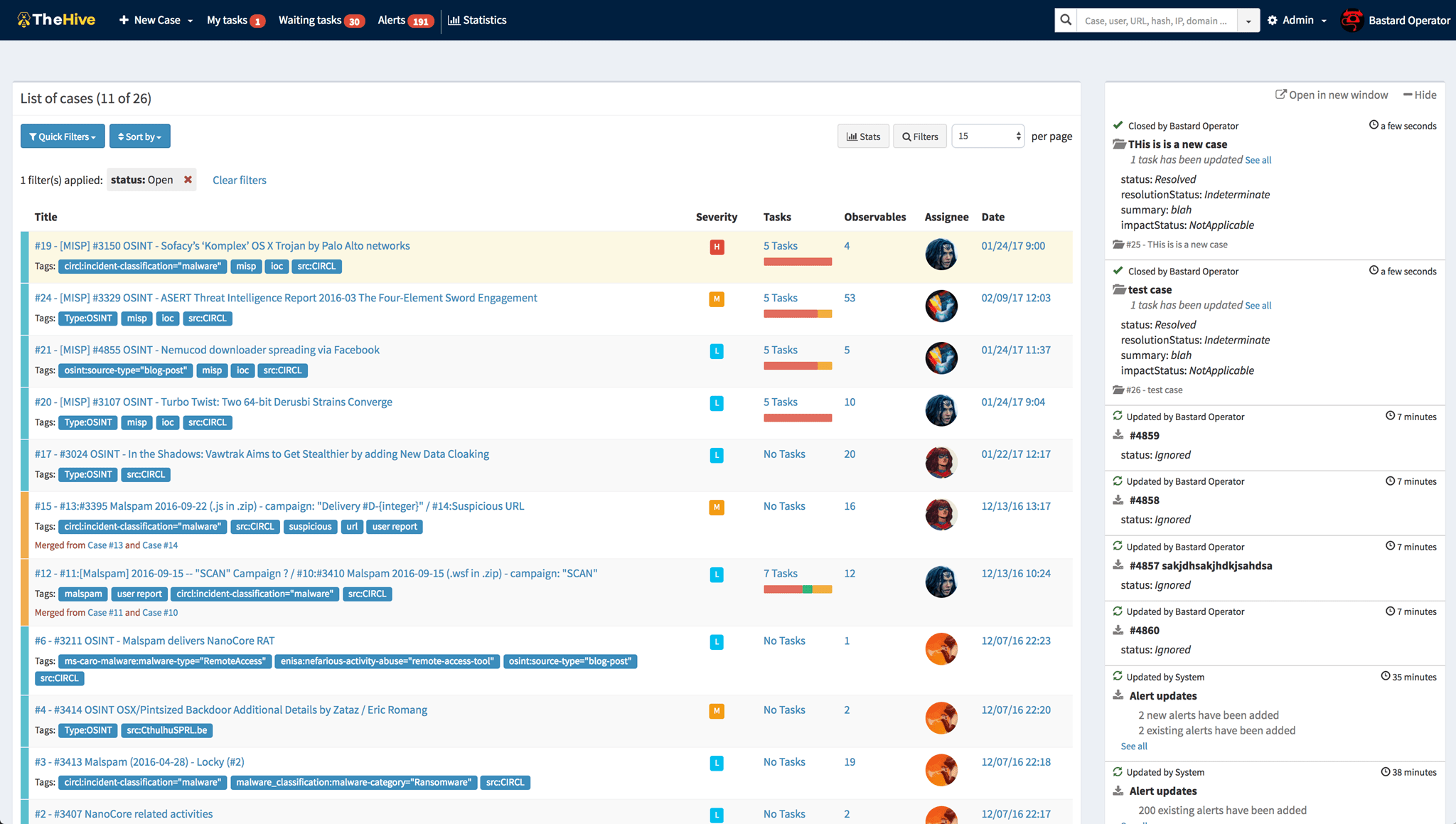
TheHive
A 3-IN-1 SECURITY INCIDENT RESPONSE PLATFORM
A scalable open source and free Security Incident Response Platform, tightly integrated with MISP (Malware Information Sharing Platform), designed to make life easier for SOCs, CSIRTs, CERTs and any information security practitioner dealing with security incidents that need to be investigated and acted upon swiftly.
From my recent experience within a live incidence response, this really saves you time as you can check the most important sources for matches of your gathered IOCs with just a view clicks.
Install a demo "to play with version" via an OVA the team has supplied.
When installed the OVA, login with thehive:thehive1234 and change the password.
Also, create certain log directorys:
sudo mkdir /var/log/thehive && sudo chown thehive:thehive /var/log/thehive && sudo service thehive restart
sudo mkdir /var/log/cortex && sudo chown cortex:cortex /var/log/cortex && sudo service cortex restart
Login to http://[your ip]:9000 for TheHive and http://[your ip]:9999 for Cortex
After the initial login to TheHive, you need to create yor initial dabatase
Analyzer and Associated Report Templates
To fully benefit from the analyzers, you should install the associated report templates:
- download the report template package
- log in TheHive using an administrator account
- go to Admin > Report templates menu
- click on Import templates button and select the downloaded package
Plug it with MISP
The test VM does not contain a MISP instance and none is configured in TheHive’s configuration file. To play with MISP, you may want to use the VM our good friends at CIRCL provide. Once you’ve downloaded it or if you have an existing instance, edit /etc/thehive/application.conf and follow the configuration guide.
in ../thehive-misp/conf edit reference.conf
| misp { | |
| #"MISP-SERVER-ID" { | |
| # # URL of MISP server | |
| # url = "[the URL to access your MISP]" | |
| # # authentication key | |
| # key = "[the API key of a misp user]" | |
| # #tags to be added to imported artifact | |
| # tags = ["misp"] | |
| #} |
Restart
After each modification of /etc/thehive/application.conf do not forget to restart the service:$ sudo service thehive restart
additions to TheHive
Add some feed-data to your hive
I've check the cortex docu and enabled as many of the free sources possible.
Some notes:
Integration with Digital Shadows
TheHive Project provides DigitalShadows2TH, a free, open source Digital Shadows alert feeder for TheHive. You can use it to import Digital Shadows incidents and intel-incidents as alerts in TheHive, where they can be previewed and transformed into new cases using pre-defined incident response templates or added into existing ones.
Integration with Zerofox
Zerofox2TH is a free, open source ZeroFOX alert feeder for TheHive, written by TheHive Project. You can use it to feed ZeroFOX alerts into TheHive, where they can be previewed and transformed into new cases using pre-defined incident response templates or added into existing ones.
hippocampe

Another great tool of the same team providing TheHive is the hippocampe.
Hippocampe regularly downloads and parses text-based threat feeds, public or private, from the Internet and stores them in Elasticsearch. Hassle-free. You can also supervise these operations and the data freshness.
As I had TheHive including the Cortex already installed, the remeining steps were just a view to get the hippocampe up and running
sudo apt-get install oracle-java8-installer
sudo pip install elasticsearch Configparser netaddr flask python-dateutil apscheduler requests
wget -qO- https://deb.nodesource.com/setup_4.x | sudo bash -
sudo apt-get install nodejs
sudo npm install -g bower
cd /opt
git clone https://github.com/CERT-BDF/Hippocampe.git
cd Hippocampe/core/static
bower install
mkdir core/logs
cd /opt/Hippocampe
nohup python core/app.py &
To check that it working, try:
curl -XGET localhost:5000/hippocampe/api/v1.0/shadowbook
And while you get the below (or simmilar ´) lines back, your good.
"job": {"AVSQjAYZGLawP2pF8zFV": "ongoing"}
To have the status of the retrievement use:
curl -GET http://localhost:5000/hippocampe/api/v1.0/jobs
For further readings check this tutorial.

