Turla
Also known as: EpicTurla, Waterbug, Whitebear, Venomous Bear, KRYPTON
Suspected attribution: Russia
Target sectors: government, embassies, military, education, research and pharmaceutical companies
Overview: A 2014 Guardian article described Turla as: 'Dubbed the Turla hackers, initial intelligence had indicated western powers were key targets, but it was later determined embassies for Eastern Bloc nations were of more interest. Embassies in Belgium, Ukraine, China, Jordan, Greece, Kazakhstan, Armenia, Poland, and Germany were all attacked, though researchers from Kaspersky Lab and Symantec could not confirm which countries were the true targets. In one case from May 2012, the office of the prime minister of a former Soviet Union member country was infected, leading to 60 further computers being affected, Symantec researchers said. There were some other victims, including the ministry for health of a Western European country, the ministry for education of a Central American country, a state electricity provider in the Middle East and a medical organisation in the US, according to Symantec. It is believed the group was also responsible for a much - documented 2008 attack on the US Central Command. The attackers - who continue to operate - have ostensibly sought to carry out surveillance on targets and pilfer data, though their use of encryption across their networks has made it difficult to ascertain exactly what the hackers took.Kaspersky Lab, however, picked up a number of the attackers searches through their victims emails, which included terms such as Nato and EU energy dialogue Though attribution is difficult to substantiate, Russia has previously been suspected of carrying out the attacks and Symantecs Gavin O’ Gorman told the Guardian a number of the hackers appeared to be using Russian names and language in their notes for their malicious code. Cyrillic was also seen in use.'
Associated malware: Uroburos, Epic, ComRAT, Gazer, Skipper, Snake, Uroburos
Attack vectors: Security researchers from ESET who have analyzed recent cyber espionage campaigns conducted by the dreaded Turla APT group reported that hackers leverage on malware downloaded from what appears to be legitimate Adobe URLs and IP addresses.
Turla is the name of a Russian cyber espionage APT group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using rootkit, Epic Turla (Wipbot and Tavdig) and Gloog Turla.
In a recent attacks, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
Attacks:
In a recent attack, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
The most recent attack known, was the federal ministry of internal affairs in march 2018:
Mail-C&C:
The way the Turla hackers took over Outlook has not yet been publicly described in this form. This is to exclude that other groups imitate this action of Turla hackers. One of the IT security researchers describes their approach as "elegant, because it is inconspicuous".
In the Foreign Office, a total of 17 computers were infected. Even a week after the announcement of the hacker attack on the federal network, the government is covered when it comes to publicly identify a culprit. The Federal Ministry of the Interior has not responded to any inquiries so far. The route of the data over Outlook would be a trace, which could be examined independently, for example if the malware finds itself on public web pages.
The hackers use the mail program to interact with their malware if it is already inside the attacked network.
So the Turla hackers send an e-mail to a computer that they have already infected with malware. Because after the infection, the attackers have to somehow get the data interesting for them from the completed networks. Hacker groups typically try to establish encrypted connections to a server over the Internet and send the data from the protected area directly to them. They use this infrastructure to communicate from the outside with their malicious software. In the networks of the Foreign Office, however, according to SZ information such connections are blocked. The only way out leads therefore via Mails. So also the control of the malicious software should have gone over mails.
The mail that the attackers send to the already infected machine contains an attachment. Such attachments are downloaded from Outlook without the user having to interact with them. In these documents - it is unclear which type it is, such as PDF or Doc - hidden information is included. These are commands like: "Hack the next computer, send a document!"
This means that the malware that is on the infected computer initially remains passive. She scans the mailbox and waits for instructions. A spokeswoman for Microsoft wanted to comment on the case on demand "at this time."
Instagram-C&C:
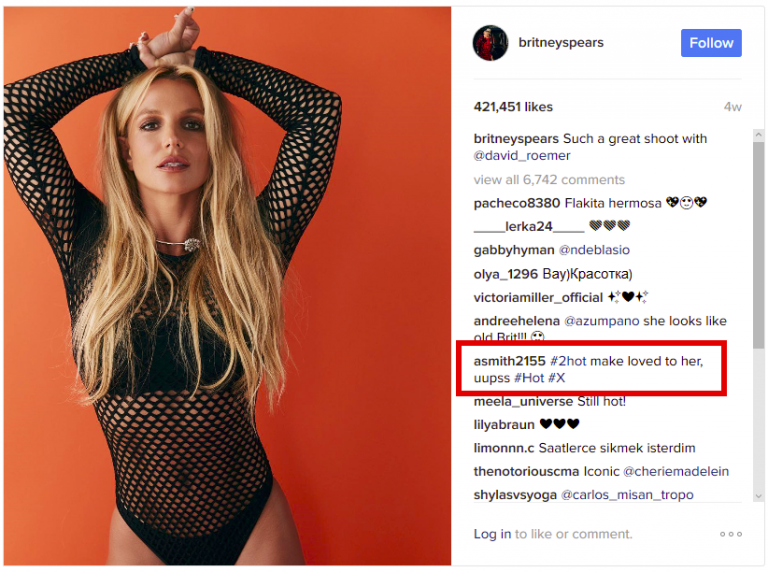
https://www.instagram.com/p/BO8gU41A45g/
The extension uses a bit.ly URL to reach Turla's C & C server. However, the URL path is nowhere to be found in the code of the extension. In fact, one gets the C & C path through comments posted under a particular Instagram post. The path used in our analyzed sample was an initially inconspicuous comment under a photograph of Britney Spears' official Instagram account.
The extension goes through all the photo comments and calculates one hash value each. If the hash matches 183, it will apply the following regular expression to the comment to get the path of the bit.ly URL:
? (: \\ u200d (?: # | @) (\\ w)
Of all the comments, there is only one candidate. This commentary was posted on February 6, while the original photo was released in early January. If you take the comment and execute it in RegEx, you get the following bit.ly URL:
http://bit.ly/2kdhuHX
If we look a bit more closely at the regular expression, we see that the script is either @ | # or the Unicode character \ 200d searches. This character is actually a non-printable character called 'Zero Width Joiner'. Usually it is used to separate emojis. Inserting the actual comment or looking at the source makes it clear that the non-printable character is used to show every single character of the bit.ly path:
smith2155 <200d> # 2hot ma <200d> ke lovei <200d> d to <200d> ago, <200d> uupss <200d> #Hot <200d> #X
The resolution of the shortened link leads to static.travelclothes.org/dolR_1ert.php, a Watering Hole C & C server used in the past.
Hiding Turlas source of action:
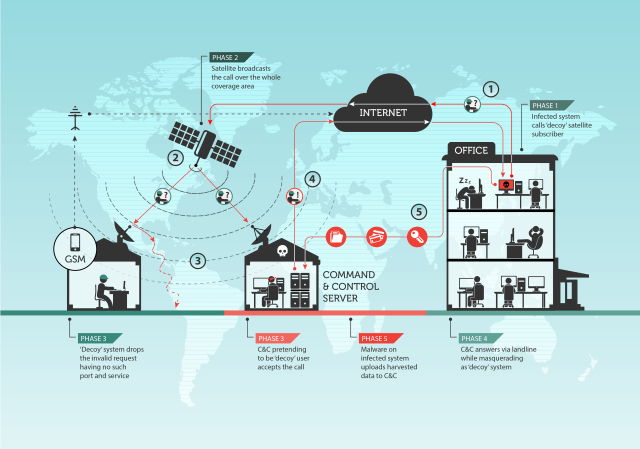
Although relatively rare, since 2007 several elite APT groups have been using — and abusing — satellite links to manage their operations — most often, their C&C infrastructure. Turla is one of them. Using this approach offers some advantages, such as making it hard to identify the operators behind the attack, but it also poses some risks to the attackers.
On the one hand, it’s valuable because the true location and hardware of the C&C server cannot be easily determined or physically seized. Satellite-based Internet receivers can be located anywhere within the area covered by a satellite, and this is generally quite large. The method used by the Turla group to hijack the downstream links is highly anonymous and does not require a valid satellite Internet subscription.
Unlike full duplex satellite-based Internet, the downstream-only Internet links are used to accelerate Internet downloads and are very cheap and easy to deploy. They are also inherently insecure and use no encryption to obfuscate the traffic. This creates the possibility for abuse.
Companies that provide downstream-only Internet access use teleport points to beam the traffic up to the satellite. The satellite broadcasts the traffic to larger areas on the ground, in the Ku band (12-18Ghz) by routing certain IP classes through the teleport points.
To attack satellite-based Internet connections, both the legitimate users of these links as well as the attackers’ own satellite dishes point to the specific satellite that is broadcasting the traffic. The attackers abuse the fact that the packets are unencrypted. Once an IP address that is routed through the satellite’s downstream link is identified, the attackers start listening for packets coming from the Internet to this specific IP. When such a packet is identified, for instance a TCP/IP SYN packet, they identify the source and spoof a reply packet (e.g. SYN ACK) back to the source using a conventional Internet line.
At the same time, the legitimate user of the link just ignores the packet as it goes to an otherwise unopened port, for instance, port 80 or 10080. There is an important observation to make here: normally, if a packet hits a closed port, a RST or FIN packet will be sent back to the source to indicate that there is nothing expecting the packet. However, for slow links, firewalls are recommended and used to simply DROP packets to closed ports. This creates an opportunity for abuse.
Conclusions
The regular usage of satellite-based Internet links by the Turla group represents an interesting aspect of their operation. The links are generally up for several months, but never for too long. It is unknown if this is due to operational security limitations self-imposed by the group or because of shutdown by other parties due to malicious behavior.
The technical method used to implement these Internet circuits relies on hijacking downstream bandwidth from various ISPs and packet-spoofing. This is a method that is technically easy to implement and provides a much higher degree of anonymity than possibly any other conventional method such as renting a VPS or hacking a legitimate server.
To implement this attack methodology, the initial investment is less than $1000. Regular maintenance should be less than $1000 per year. Considering how easy and cheap this method is, it is surprising that we have not seen more APT groups using it. Even though this method provides an unmatched level of anonymfor logistical reasons it is more straightforward to rely on bullet-proof hosting, multiple proxy levels or hacked websites. In truth, the Turla group has been known to use all of these techniques, making it a very versatile, dynamic and flexible cyber-espionage operation.
Lastly, it should be noted that Turla is not the only APT group that has used satellite-based Internet links. HackingTeam C&Cs were seen on satellite IPs before, as well as C&Cs from the Xumuxu group and, more recently the Rocket Kitten APT group.
If this method becomes widespread between APT groups or worse, cyber-criminal groups, this will pose a serious problem for the IT security and counter-intelligence communities.
Further reading:
How highly advanced hackers (ab)used satellites to stay under the radar
Satellite Turla: APT Command and Control in the Sky
The Epic Turla Operation
Introducing WhiteBear
Gazing at Gazer
https://www.welivesecurity.com/deutsch/2017/06/07/turla-watering-hole-firefox-erweiterung-missbraucht-instagram/
Turla in action:
Download IOC’s:
From the GitHUB here.
