Webtraffic interception
Capturing the web traffic of clients/devices is very important while you have an attack ongoing.
But please Keep in mind, that capturing private data is/might be illegal in your country.
"Man in the middle" setup with Ettercap
setup xplico as described in my forensic section.
Be sure to activate Routing on your box: echo 1 > /proc/sys/net/ipv4/ip_forward
Run:
ettercap -G
Goto sniff, unified sniffing, eth0 (or what ever your active interface is called)
After that, goto Hosts, scan for Hosts. Click Hosts list
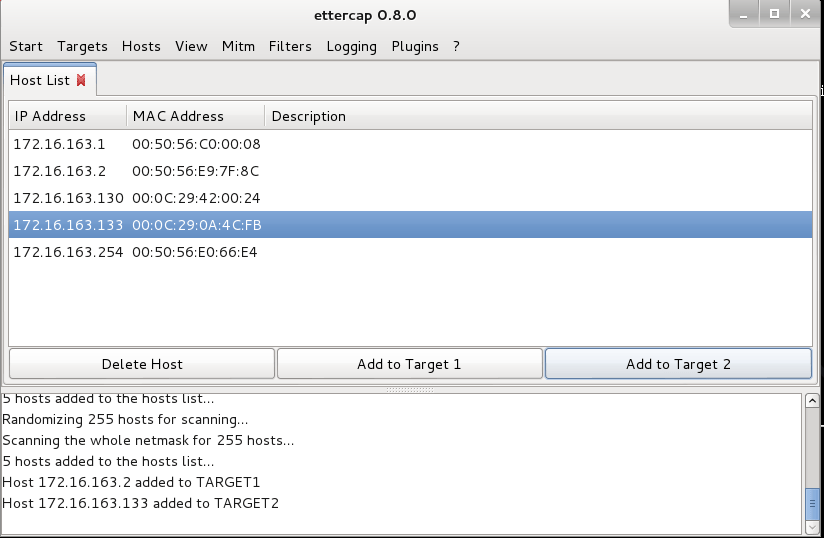
Add your default gateway and the target to "Target 1" and "Target 2"
check your actual arp table: "arp -a"
Go back to ettercap and click: Mitm, ????
Compare the arp table again. - Recognize something? :-)
Now use a browser on the attacked machine and watch the data traveling into xplico.
