UserAssist
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
GUI-based programs launched from the desktop are tracked in the launcher on a Windows System.
Location
NTUSER.DAT HIVE: NTUSER.DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist\ {GUID}\Count
Interpretation
All values are ROT-13 Encoded
>>> s = "HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\haxabja\Ohernh\argjbex-gnfxznantre.rkr"
>>> s.decode("rot13")
u'UEME_RUNPATH:C:\\Documents and Settings\\unknown\\Bureau\x07etwork-taskmanager.exe'
• GUID for XP
- 75048700 Active Desktop
• GUID for Win7/8/10
- CEBFF5CD Executable File Execution
- F4E57C4B Shortcut File Execution
Use volatility:
python vol.py -f ~/memdump/infected.img userassist
Further readings:
Windows 10 Timeline
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Win10 records recently used applications and files in a “timeline” accessible via the “WIN+TAB” key. The data is recorded in a SQLite database and (only) stored for the past 30 days of activity.
Location
C:\Users\\AppData\Local\ConnectedDevices Platform\L.\ActivitiesCache.db
The catalog Users\%profile name%\AppData\Local\ConnectedDevicesPlatform\ contains a CDP file with information about the last Windows 10 Timeline synchronization with the cloud (CNCNotificationUriLastSynced) and about the user ID
Interpretation
• Application execution • Focus count per application
ActivitiesCache.db contains the following tables: Activity, Activity_PackageId, ActivityAssetCache, ActivityOperation, AppSettings, ManualSequence, and Metadata. The ones that hold the most interest for investigators are Activity_PackageId and Activity.
The records in the Activity_PackageId table are stored for 30 days and can contain information about executable files or documents that are no longer present on the hard drive.
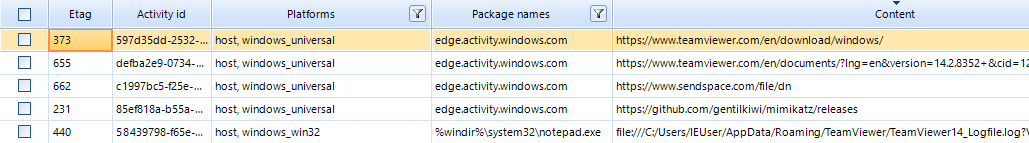
Sample:
As can be seen in the screenshot, the attackers installed TeamViewer (a file from a file sharing website called sendspace.com) and Mimikatz on the victim's computer. An analysis of the events stored in Windows 10 Timeline indicates that the attackers opened TeamViewer logs (TeamViewer14_Logfile.log) via Notepad (notepad.exe). They may have done this to delete or modify the file information.
Further readings:
Windows 10 RecentApps
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
GUI Program execution launched on the Win10 system is tracked in the RecentApps key
Location
NTUSER.DAT\Software\Microsoft\Windows\Current Version\Search\RecentApps
Interpretation
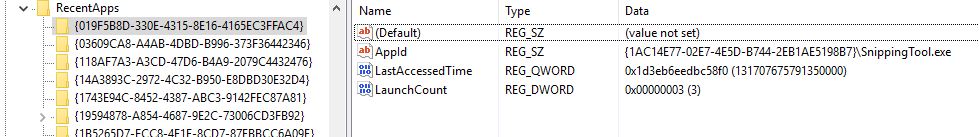
Each GUID key points to a recent application.
AppID = Name of Application
LastAccessTime = Last execution time in UTC
LaunchCount = Number of times executed
Sample:
Further readings:
Shimcache
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Windows Application Compatibility Database is used by Windows to identify possible application compatibility challenges with executables.
It tracks the executables file name, file size, last modified time, and in Windows XP the last update time .
From reading Andrew Davis' whitepaper "Leveraging the Application Compatibility Cache in Forensic Investigations", we know each time an application with unique metadata is executed, a corresponding Shimcache entry will be created. In other words, new entries are created when an existing file’s metadata has changed and is re-executed.
Location
XP: SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatibility
Win7/8/10: SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache
Interpretation
Any executable run on the Windows system could be found in this key. You can use this key to identify systems that specific malware was executed on. In addition, based on the interpretation of the time-based data you might be able to determine the last time of execution or activity on the system.
Windows XP contains at most 96 entries
LastUpdateTime is updated when the files are executed
Windows 7 contains at most 1,024 entries
LastUpdateTime does not exist on Win7 systems
Further readings:
Jump List
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
The Windows 7 task bar (Jump List) is engineered to allow users to “jump” or access items they have frequently or recently used quickly and easily. This functionality cannot only include recent media files; it must also include recent tasks.
The data stored in the AutomaticDestinations folder will each have a unique file prepended with the AppID of the associated application.
The AutomaticDestinations files are the OLE files, so you can analyze them with oledump.
Location
Win7/8/10: C:\%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
Interpretation
First time of execution of application.
- Creation Time = First time item added to the AppID file.
Last time of execution of application w/file open.
- Modification Time = Last time item added to the AppID file.
List of Jump List IDs -> http://www.forensicswiki.org/wiki/List_of_Jump_List_IDs
Further readings:
Amcache.hve
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
ProgramDataUpdater (a task associated with the Application Experience Service) uses the registry file Amcache.hve to store data during process creation
Location
Win7/8/10: C:\Windows\AppCompat\Programs\Amcache.hve
Interpretation
Amcache.hve – Keys = Amcache.hve\Root\File\{Volume GUID}\#######
Entry for every executable run, full path information, File’s $StandardInfo Last Modification Time, and Disk volume the executable was run from
First Run Time = Last Modification Time of Key
SHA1 hash of executable also contained in the key
Frequency Analysis Review: Amcache
Here is a summary of the steps so far using the DFIR host:
- Gather up amcache hives
- Run RegRipper on all amcache hives. Make sure to use the modified version of the plugin.
Windows:find {directory with amcache hives} -print -exec rip.exe -r {} -p amcache_tln ; > appcache{datetime}.txt
*NIX:
find {directory with amcache hives} -print -exec rip.pl -r {} -p amcache_tln \; > appcache{datetime}.txt
- Cut out the SHA1 hashes and run them against the NSRL/MSDN/Review/Whitelist databases to remove known good hashes.
-
cut -f8 -d\| amcache{datetime}.txt | sort | uniq | grep -v amcache | sed '/^[[:space:]]*$/d' | grep -v -i "plugins" > amcache{datetime}.sha
-
./ir_distill_v0.3.py --nsrl ./nsrl.db --reviewlist ./whitelist.db ./msdn.db --file ./amcache{datetime}.sha --out amcache{datetime}_shareview —ignorecase
-
cut -d\| -f6 amcache{datetime}_shareview _match.csv | sort | uniq -c
-
- Cut out the directory path and filename, sort them, and unique them for frequency analysis<\li>
grep -f amcache{datetime}.shareview_nomatch.txt| cut -f7 -d\| | sort | uniq -c | sed -e 's/^[ \t]*//' | sort -t" " -k2 > amache{datetime}_freq.txt
- Reduce output with IR Distill
./ir_distill_v0.3.py -f ./os.sqlite --showallmatches --ignorecase -i amache{datetime}_freq.txt -o amcache_{datetime}_distill2
- Review "amcache_{datetime}_distil_nomatch.txt" file
- Review the binaries
- Pull binaries from source machines
- Run hashes through VT
- Malware analysis of binaries
Further readings:
SRUM - System Resource Usage Monitor
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Records 30 to 60 days of historical system performance. Applications run, user account responsible for each, and application and bytes sent/received per application per hour.
Location
SOFTWARE\Microsoft\WindowsNT\CurrentVersion\SRUM\Extensions {d10ca2fe-6fcf4f6d-848e-b2e99266fa89} = Application Resource Usage Provider C:\Windows\ System32\SRU\
Interpretation
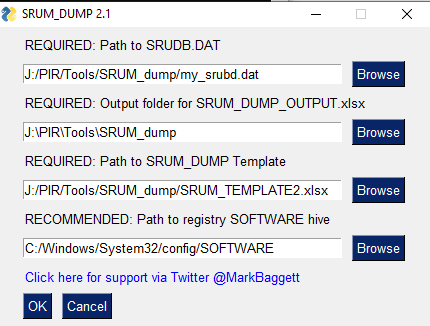
Use tool such as srum_dump.exe to cross correlate the data between the registry keys and the SRUM ESE Database.
Further readings:
SRUM - System Resource Usage Monitor
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Windows 10 Background Activity Moderator (BAM)
Location
Win10: SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID} SYSTEM\CurrentControlSet\Services\dam\UserSettings\{SID}
Interpretation
Provides full path of the executable file that was run on the system and last execution date/time
Further readings:
Startup Type
| Windows 10 version | Home | Pro | Education | Enterprise |
|---|---|---|---|---|
| 1507 | not exists | not exists | not exists | not exists |
| 1511 | not exists | not exists | not exists | not exists |
| 1607 | not exists | not exists | not exists | not exists |
| 1703 | not exists | not exists | not exists | not exists |
| 1709 | System | System | System | System |
| 1803 | System | System | System | System |
| 1809 | System | System | System | System |
| 1903 | System | System | System | System |
| 1909 | System | System | System | System |
MRU - Last visited or MostRecentlyUsed
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Tracks the specific executable used by an application to open the files documented in the OpenSaveMRU key. In addition, each value also tracks the directory location for the last file that was accessed by that application. Example: Notepad.exe was last run using the C:\%USERPROFILE%\ Desktop folder
Location
XP:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRU
Win7/8/10:
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
Interpretation
Tracks the application executables used to open files in OpenSaveMRU and the last file path used.
RunMRU: Any program launched from Start>Run command can also be used to see what programs the user has launched via this route. These entries get logged under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU, and there will be a list of all the programs launched from Run.It will also contain an MRULISt which will show the order of these with the first entry being the most recent.
Further readings:
Prefetch
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download
Description
Increases performance of a system by pre-loading code pages of commonly used applications. Cache Manager monitors all files and directories referenced for each application or process and maps them into a .pf file.
Utilized to know an application was executed on a system.
Limited to 128 files on XP and Win7
Limited to 1024 files on Win8
(exename)-(hash).pf
Location
WinXP/7/8/10: C:\Windows\Prefetch
Interpretation
Each .pf will include last time of execution, number of times run, and device and file handles used by the program.
Plesae keep in mind that although each parameter will create a new PF-entry, the actual parameter will not be retrievable.
Date/Time file by that name and path was first executed
Creation Date of .pf file (-10 seconds)
Date/Time file by that name and path was last executed
Embedded last execution time of .pf file
Last modification date of .pf file (-10 seconds)
Win8-10 will contain last 8 times of execution
Further readings: