Defense & countermeasures
Now that we know, how an attack works and what kind of tools might be used, it's time to talk about how to defend these actions.

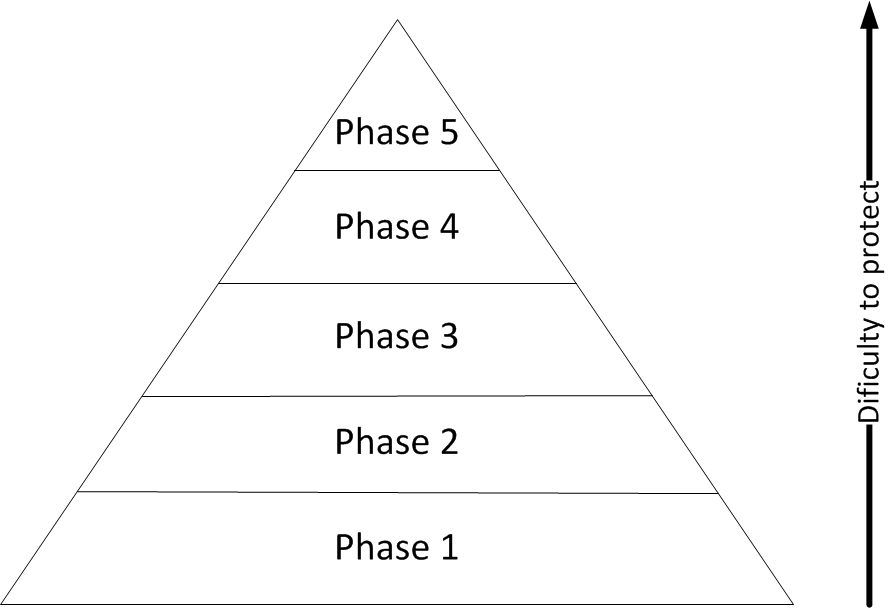
Now that we know, how an attack works and what kind of tools might be used, it's time to talk about how to defend these actions.

