CyCON 2019
I had the honor, pleasure and joy to participate at the CyCON 2019 of the @ccdcoe 28.05. - 31.05.2019 in Tallinn/Estonia.
Below are my notes of the conference to manifest the facts for my personal memory.
The big question that was heavily discussed throughout the days "What situation legalizes countermeasures in an cyber attack"
As there have been politics, military, tecky's and law sciences, this was a more the thrilling and fascinating discussion.
28.05.19 09:00 - 12:00: Cyber War Game: State-sponsored cyber-attack on a critical infrastructure
Cyber risks have increased enormously in recent years, and organisations – from governments to large and small businesses – need to understand that, without a robust and structured approach to cyber security, cyber criminals, terrorists, states and totalitarian regimes will continue to abuse today’s increased digitisation to fulfil their goals.
This Cyber War Game simulates a cyber attack on a critical infrastructure. The scenario includes escalating ripple effects, which are designed to raise crucial questions with regard to cyber risks for states and enterprises.
Participants are encouraged to approach a complex problem in a structured manner, in order to assess the problem of a cyber attack and to find appropriate technical and organisational solutions.
The aim of the exercise is to assess the overall threat situation and to answer the question of how well an organisation is prepared to deal with a cyber attack.
Moderators: Dr. Stefanie Frey and Michael Bartsch
This was an excellent tabletop excercice, especially as I have done and organized this kind of event myself in the past. From the knowledge of my role as an incident response manager and technical incident responder in commercial situations, I was finding the implications of beein in the role of a nation state was completly new and thrilling to me. I really learned what it means to defend, react and manage a nation state attack and the differences to "only" a company being in the focus of the bad guys.
Big thanks to Dr. Stefania Frey and Michael Bartsch but especially the team members of my table that made this event such a great success for me personally.
28.05.19 - 13:30 - 15:00: Official launch of the International Cyber Law: Interactive Toolkit
The Cyber Law Toolkit is a dynamic interactive web-based resource for legal professionals who work with matters at the intersection of international law and cyber operations. During the launch, the Toolkit functionalities and its history and future will be introduced to the audience.
At its heart, the Toolkit consists of 13 (and counting) hypothetical scenarios, each of which contains a description of cyber incidents inspired by real-world examples accompanied by detailed legal analysis. The Toolkit may also be explored by looking for legal concepts you’re interested in or by reading about individual real-world examples that had inspired the scenarios. The individual scenarios and the Toolkit as such have been reviewed by a team of over 20 peer reviewers.
The project is supported through the UK ESRC IAA Project Co-Creation scheme. Partner institutions include the University of Exeter, United Kingdom; NATO Co-operative Cyber Defence Centre of Excellence (CCD COE) in Tallinn, Estonia; and the Czech National Cyber and Information Security Agency (NCISA) in Brno, Czechia. The project team is composed of Dr Kubo Mačák (Exeter); Mr Tomáš Minárik (CCD COE); and Ms Taťána Jančárková (NCISA). The Toolkit is expected to be continuously updated and expanded.
As I am a so called "nerd", the part of legally insuring my actions at a customer site could always be handled with paperwork between Airbus and the customer. Finding myself in the role of applying international law to any action was and is still a great mystery to me. The Interactive Toolkit will help finding the way through the rules by giving sample scenarios and showing pretty simply what implications apply. Even understandable for a "nerd" like me.
28.05.19 19:00 - 22:00: CyCon Icebreaker in the Tallinn Creative Hub
The CyCon icebreaker serves as a social kick-off for the conference, where the participants, speakers and organisers can meet each other again (or for the first time) and get into the CyCon spirit in a relaxed and informal atmosphere accompanied by good food and good music.
This year we welcome you to the Tallinn Creative Hub, a creative centre and venue for cultural events located in the heart of Tallinn. Until 1979, it was the Tallinn City Central Power Station; with the founding of this power station in 1913, the use of electric power became common in Estonia. Completed in 1934 and now completely renovated, this building with limestone walls and high ceilings is now used by art-minded, creative people.
This was the final start of the great benefit of CyCON 2019. Chatting and discussing with all sort of people to hear and reflect their background and thought of international cyber conflicts. I learned so much from 1:1 talks. Actually this was also the first moment that I was told (and realized) that there is no agile regulation/process to defend a non-state towards a non-state cyber attack while the partys are not within the same country.
29.05.19 09:00 - 09:10: Opening Remarks

Col Jaak Tarien, Director, NATO CCD COE
Mr. Tarien, that I later had the joy of meeting personally, gave us a great opening speech as the Director of the CCDCOE.


International law DOES apply in #cyber.
All else stems from that – rights and obligations, attribution issues, and also countermeasures, if necessary.
Madam President, Kersti Kaljulaid, of Estonia held a fascinating and poignant speech about the evolving cyber world and gave a fantastic insight of Estonias way of dealing with the technology from a state perspective. It was an absolute Honor to listen to her words and statements that were clear, demanding and full of knowledge. I which that more politicians (especially my own ones) would take her words, understanding and pragmatism into every days life. Her clear statements about the international law that has to be taken into account and needs to be extended in a way to deal with todays situations just put into words what everybody in the room was thinking and feeling.
Europe and the whole world has the chance of becoming a good and safe place with Madam President Kaljulaid.
29.05.19 10:50 - 11:50: Cyber Commanders Panel
Speakers:
LtG Ludwig Leinhos, Chief of the German Cyber and Information Domain Service
BGen Francesco Vestito, Commander of Joint Operational Cyber Command of Italy
BGen Maria A. Biank, Director, J-6, Cyber/C4, U.S. European Command
Moderator:
Adm (ret.) Michael Rogers, Former Commander of U.S. Cyber Command and Director of National Security Agency
29:05.19 13:30 - 15:00: Law in Action: Defending a Nation in Cyberspace
In the past decade, silent cyber operations conducted or controlled by states have become the most serious threat to cyber security; moreover, the increased reliance of societies on cyberspace has made them more vulnerable to cyber threats. This session will look at the legal qualification of specific subversive cyber operations, but also at the role of law in choosing the right strategy to defend the interests of a state in cyberspace.
Ms. Kadri Kaska, Researcher, Law branch, NATO Cooperative Cyber Defence Centre of Excellence
Prof. Jeff Kosseff, Assistant Professor, U.S. Naval Academy Cyber Science Department
Mr.Kenneth Kraszewski, LLD Candidate, University of Helsinki
Moderator: Mr. Tomáš Minárik, Researcher, Law branch, NATO Cooperative Cyber Defence Centre of Excellence
Speakers:
Ms. Kadri Kaska, Legal researcher, NATO CCDCOE
Prof. Jeff Kosseff, Assistant Professor, U.S. Naval Academy Cyber Science Department
Mr. Kenneth Kraszewski, LLD Candidate, University of Helsinki

29.05.19 15:30 - 17:00: Law and Policy of Attributing Cyber Operations
Attribution is a major element in establishing the responsibility of States under international law. States are no longer silent when it comes to attributing major cyber operations, as can be seen in the examples of NotPetya or WannaCry. Apart from discussing the application of existing rules of attribution to cyber operations, this session will also cover current State practice and policies in attributing recent cyber operations and will try to point out possible developments in the interpretation of existing rules.
Mr. Robert E. Barnsby, Cyber Law Fellow, Army Cyber Institute, United States Military Academy at West Point
Ms. Manon Le Blanc, Cyber Policy Sector, European External Action Service
Ms. Liis Vihul, Chief Executive Officer, Cyber Law International
Mr. Robert E. Barnsby, Cyber Law Fellow, Army Cyber Institute, United States Military Academy at West Point
Moderator: Prof. Sean Watts, Creighton University Law School, United States Military Academy at West Point
Speakers:
Prof. Robert E. Barnsby, Cyber Law Fellow, Army Cyber Institute, United States Military Academy at West Point
Ms. Manon Le Blanc, Security & Defense Policy, Cyber Policy Sector, European External Action Service
Ms. Liis Vihul, Chief Executive Officer, Cyber Law International
-> For nation state: The (last) source IP might be good enough to claim "due diligence" from sourcing state
29.05.19 19:00 - 21:00: Tallinn City Tour "come to Tallinn and hugh a tree"
30.05.19 09:00 - 10:15: Keynotes of Day 2
Speakers:
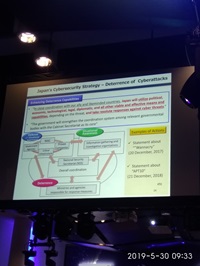
H.E. Mr. Kentaro Sonoura, Special Advisor to Prime Minister, Japan
VAdm Arnaud Coustillière, Director General of the General Directorate for Digital Communication and Information Systems (DGNUM), Ministry for the Armed Forces, France
Mr. B. Edwin Wilson, Deputy Assistant Secretary of Defense for Cyber Policy, United States
30.05.19 11:00 - 12:30: Monitoring and detection in support of discovering silent malicious activities in cyberspace
There is a lot happening in cyberspace that we do not know about. Admitting this is the first step towards improving the situation. However, detecting these covert activities is of utmost importance. Real-time monitoring and analysis are essential for defending against various threats such as cyber attacks, malware, user exploitation and theft of information. This panel presents the latest research efforts in the areas of monitoring the Dark Web, detecting malicious communication channels, data analytics and machine learning.
Mr. Pierre Dumont, Department of Information Technology and Electrical Engineering ETH, Zürich
Dr. Vincent Lenders, head of newly created Swiss Cyber-Defence Campus and of the C4I group, armasuisse Science and Technology
Dr. Csaba Krasznay, National University of Public Service, Program Director of Cybersecurity Academy, Hungary
Moderator: Prof. Bruce W. Watson, Chief Scientist, IP Blox and Stellenbosch University
Speakers:
Dr. Csaba Krasznay, Program Director of Cybersecurity Academy
Dr. Vincent Lenders, Head of Cyber-defence Campus and C4I Group, armasuisse Science and Technology
Mr. Pierre Dumont, Cybersecurity Engineer, Kudelski Security (Switzerland)


30.05.19 13:0 - 15:00: Information Warfare: defining and analyzing
The defence community is nearing a stage where it can precisely define information warfare but is yet to reach a consensus on how best to analyse it. The panel will assess some of the emerging methodologies that researchers have been using to identify and analyse digital information operations, with a special focus on the applicability of Social Network Analysis (SNA) in the cyber arena.
Ms. Renee DiResta, Mozilla Fellow, Media Misinformation and Trust
Ms. Alicia Marie Bargar, Research Engineer, Johns Hopkins Applied Physics Laboratory
Major Geoff Nicholls, Officer, The British Army
Moderator: Ms. Donara Barojan, DFR Lab / NATO StratCom COE
Speakers:
Ms. Renee DiResta, Mozilla Fellow, Media Misinformation and Trust
Ms. Alicia Marie Bargar, Research Engineer, Johns Hopkins Applied Physics Laboratory
Maj Geoff Nicholls, Officer Commanding Digital Operations, The British Army, 77th Brigade
Bilder (4)
30.05.19 15:30 - 17:00: Strategic Vulnerabilities: Time for a New Approach?
Despite several cyber-physical incidents with disruptive and destructive capabilities, such as Stuxnet (2010) and Triton (2017) which exploited known vulnerabilities throughout the attack life-cycle, information sharing on industrial control systems (ICS) vulnerability remains a global challenge. For instance, the ICS community lacks specialised mechanisms for knowledge sharing. Concurrently, the proliferation of commercial off-the-shelf hardware and software with short product life-cycles poses another challenge for service providers, which already struggle to keep up with the pace of vulnerabilities to sustain the resiliency of their systems. Strategically it remains essential for the potentially affected parties to adopt an overall more proactive posture towards attacks in and through cyberspace. Could the employment of a more military-style Indications & Warning system be a game-changer? What are the Ends, Ways and Means that help us achieve cyber effects?
Ms. Bilyana Lilly, Pardee Fellow, RAND Corporation in Los Angeles, California
Sen. Capt Erwin Orye, Strategy Researcher NATO Cooperative Cyber Defence Centre of Excelence
Cpt(N) Baris Egemen Özkan, Cyberspace Operations Centre, Plans Branch Head, SHAPE
Mr. Daniel Kapellmann Zafra, Senior Cyber Threat Intelligence Analyst, FireEye cyber-physical team
Speakers:
Ms. Bilyana Lilly, Pardee Fellow, RAND Corporation in Los Angeles, California
Sen. Capt Erwin Orye, Strategy Researcher, NATO CCD COE
Cpt(N) Baris Egemen Özkan, Cyberspace Operations Centre, Plans Branch Head, SHAPE
Mr. Daniel Kapellmann Zafra, Senior Cyber Threat Intelligence Analyst, FireEye cyber-physical team
Moderator:
Lt Ihsan Tolga, Researcher, NATO CCD COE

30.05.19 19:00 - 22:00: "The beachparty"
o shoes, no suits, no worries!
Did you know that the weather in Tallinn in the end of May can be just about anything? It can be warm and sunny, it can rain cats and dogs and in the worst case it can snow. We do not want to risk it and therefore we are taking you to an indoor beach – Teras Beach – to enjoy the CyCon Beach Party, with good food, music and the great company of your old and new fellows on the white sand and in a real beach atmosphere. There will be sand under your feet, a roof above your head and a temperature of +26C even if it snows outside.
Dress code: summer clothes and bare feet

30.05.19 22:00 - 02:00: The after-beach-party
Meet the CyCON party people in an estonian habitat. :-)
"to the cycon, down with all controlers"

31.05.19 09:00 - 10:30: Cyber and Space
Activities of states in the outer space domain have an increasingly important cyber element, which might, on alarmingly numerous occasions, become a major vulnerability. Activities in other domains rely heavily on space and/or cyber technologies. It has therefore been argued that, for instance, satellite systems that form the basis of many recognised critical infrastructures are often left without special protection and should be better regulated. Space systems are also characterised by particular difficulties in introducing updates and repairing the underlying hardware. The interdependence of space technologies and networked ICT systems also poses new challenges to the traditional international space law and LOAC. This panel aims to open up a series of discussions on the domain-specific problems of cyber security, addressing first the one that is at once the most distant, the most romanticised and the most technologically complicated.
Mr. Robert Traussnig, Head of Product Security Space Systems, Airbus Defence & Space
Mr. James Pavur, DPhil Student, Oxford University
Lt Col Henry Heren, NATO Space & Cyberspace Strategist, Joint Air Power Competence Centre
Moderator: Dr. Katrin Nyman Metcalf, Adjunct Professor, Tallinn University of Technology
Speakers:
Mr. Robert Traussnig, Head of Product Security Space Systems, Airbus Defence & Space
Mr. James Pavur, DPhil Student, Oxford University
Lt Col Henry Heren, Space & Cyberspace Strategist, NATO Joint Air Power Competence Centre
31.05.19 11:15 - 12:30: Keynotes of Day 3
Speakers:
Mr. Luc Dandurand, Head of Cyber Operations, Guardtime
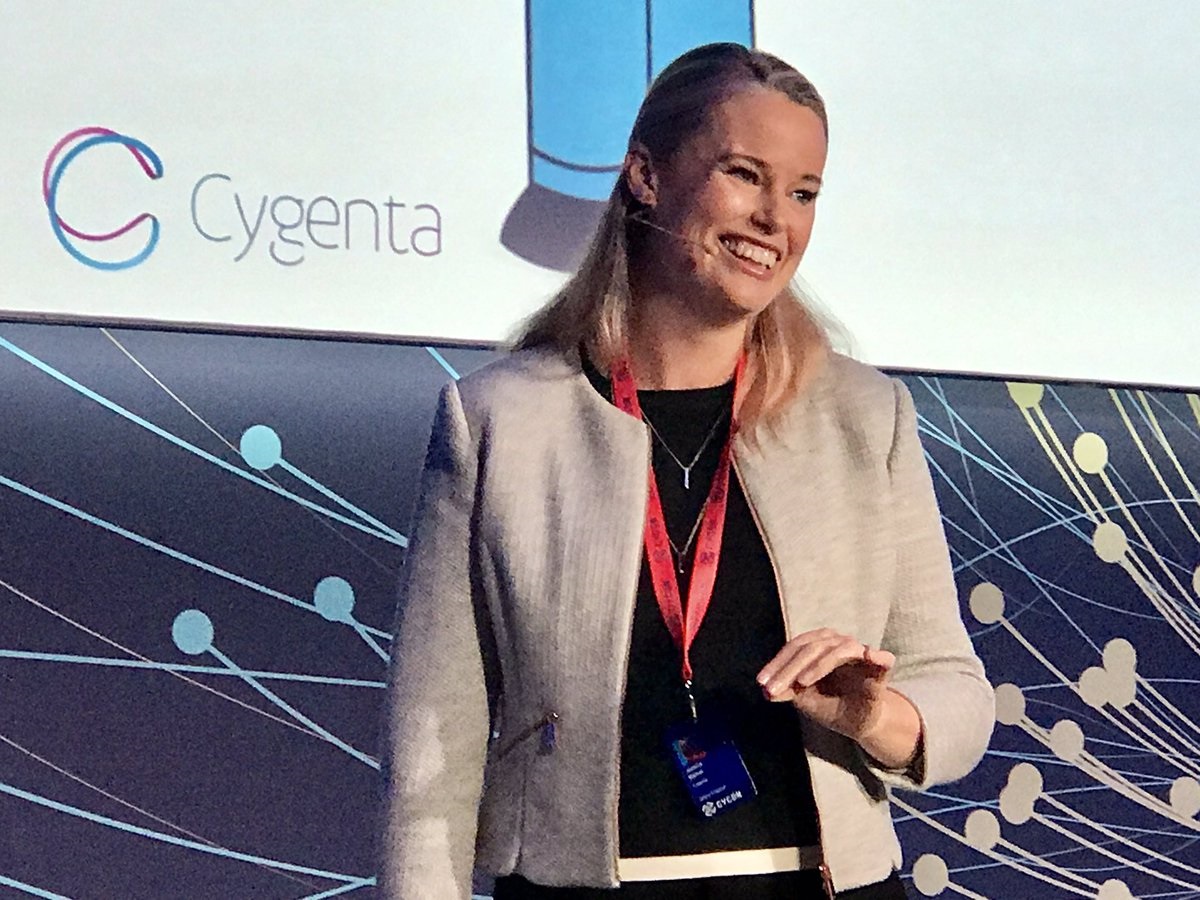
Dr. Jessica Barker, Co-Founder and co-CEO, Cygenta
Mr. Taavi Kotka, Entrepreneur and former Estonian Government CIO