CIF / CTI
As per the famous SANS institute, ("Maturing and Specializing: Incident Response Capabilities Needed, by Alissa Torres, August 2015"), it was proven, that the fast majority of us uses reputational IP information to triage the daily security events.
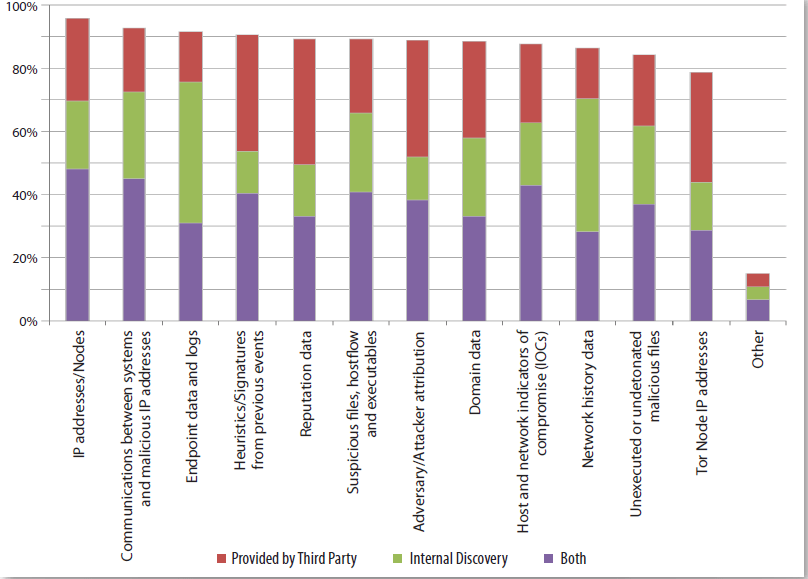
- 96% tie intelligence to IP addresses. This was the most commonly implemented type of CTI data when including internal and third-party sources. • 93% tie traffic to known suspicious IPs.
- 91% track endpoint security data and logs.
- 91% incorporate signatures and heuristics from previous events.
The "(Cyber) Collective Intelligence Framework" as part of my "Cyber Threat Intelligence" work or
Get your own IP reputation server up and running.
The Intelligence Layer
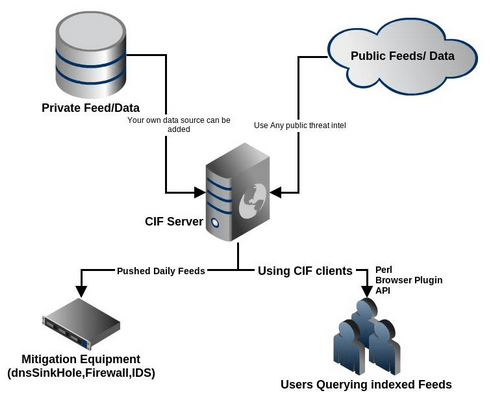
CIF is a cyber threat intelligence management system. CIF allows you to combine known malicious threat information from many sources and use that information for identification (incident response), detection (IDS) and mitigation (null route). The most common types of threat intelligence warehoused in CIF are IP addresses, domains and urls that are observed to be related to malicious activity.
More can be found by continuing on to What is CIF? and some history
This framework pulls in various data-observations from any source; create a series of messages "over time" (eg: reputation). When you query for the data, you'll get back a series of messages chronologically and make decisions much as you would look at an email thread, a series of observations about a particular bad-actor.
CIF helps you to parse, normalize, store, post process, query, share and produce data sets of threat intelligence.
The original idea came from from:
http://bret.appspot.com/entry/how-friendfeed-uses-mysql