phishing
COOL: Hackers Using Zero-Width Spaces to Bypass MS Office 365 Protection
Swati Yoav Nathaniel is writing about a new way to evade URL-detaction with the Office365.
His idea is to put Zero-Width statements into the URL to trick the MS ATP-detection algorythm.
So, it's about to enhance our own detection filters with the below list to stay on top of detections.
- ​ (Zero-Width Space)
- ‌ (Zero-Width Non-Joiner)
- ‍ (Zero-Width Joiner)
-  (Zero-Width No-Break Space)
- 0 (Full-Width Digit Zero)
His poc was.
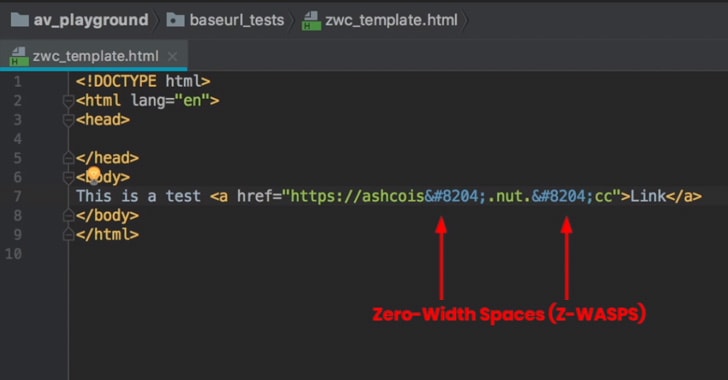
In a Z-WASP phishing attack, the Zero-Width Non-Joiner (‌) is added to the middle of a malicious URL within the RAW HTML of an email.
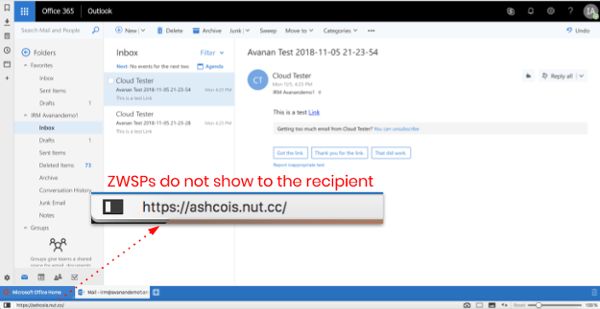
Microsoft email processing did not recognize this URL as a legitimate URL, and neither applied URL reputation checking nor converted it with Safe Links for post-click checking. The email was delivered to the intended recipient; but in their inbox, users did not see the ZWSPs in the URL.
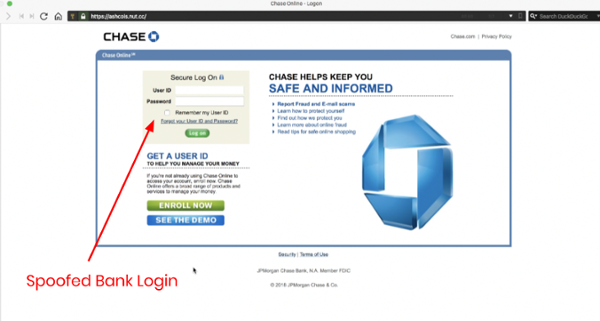
When the end-users clicked on the link in the email, they were taken to a credential harvesting phishing site. In the example below, Chase Bank was spoofed.