ids_enhance
OK, this ones not one of my first macros, but one of my bigger ones, surely.
The macro looks up several values from csv files to enhance the source data with the values provided.
The aim is to have a filter description and some more data about the triggert snort rule and add some reputational information from public available sources, to repriotize the risk of the alert depending on the sourced or targeted public IP.
triagecomments.csv
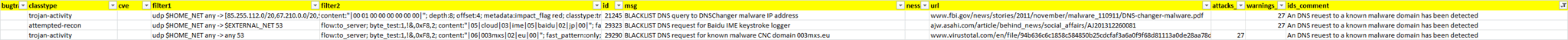
ids_enhance
rename sid AS id |lookup rule.csv id |rename bugtraq AS m1_bugtraq |rename classtype AS m1_classtype |rename cve AS m1_cve |rename filter1 AS m1_filter1 |rename filter2 AS m1_filter2 |rename msg AS m1_msg |rename nessus AS m1_nessus |rename url AS m1_url |rename attacks_id AS m1_attacks_id |rename warnings_Id AS m1_warnings_id |rename ids_comment AS m1_comment|lookup ids-comments id |rename bugtraq AS m2_bugtraq |rename classtype AS m2_classtype |rename cve AS m2_cve |rename filter1 AS m2_filter1 |rename filter2 AS m2_filter2 |rename msg AS m2_msg |rename nessus AS m2_nessus |rename url AS m2_url |rename attacks_id AS m2_attacks_id |rename warnings_Id AS m2_warnings_id |rename ids_comment AS m2_comment|rename id AS sid |eval at_bugtraq=coalesce(m1_bugtraq,m2_bugtraq) |eval at_classtype=coalesce(m1_classtype,m2_classtype) |eval cve=coalesce(m1_cve,m2_cve) |eval at_filter1=coalesce(m1_filter1,m2_filter1) |eval at_filter2=coalesce(m1_filter2,m2_filter2) |eval at_msg=coalesce(m1_msg,m2_msg) |eval at_nessus=coalesce(m1_nessus,m2_nessus) |eval at_url=coalesce(m1_url,m2_url) |eval at_attacks_id=coalesce(m1_attacks_Id,m2_attacks_Id) |eval at_warnings=coalesce(m1_warnings,m2_warnings) |eval ids_comment=coalesce(m1_comment,m2_comment) |fillnull value=undefined at_classtype,cve | rename srcip AS ip |lookup reputation ip | fillnull reputation value=neutral |rename reputation AS at_reputation |rename location AS at_location |rename ip AS srcip |rename url AS at_url |fillnull value="medium" host_priority |eval priority = case(at_reputation != "neutral", priority*5, at_reputation == "neutral", priority) |eval adjusted_priority = case((NOT cidrmatch("10.0.0.0/8",srcip) OR NOT cidrmatch("10.0.0.0/8",dstip)), priority*6,host_priority == "critical", priority*5,host_priority == "high", priority*4,host_priority == "medium", priority*3,host_priority == "Warning", priority*2,host_priority == "low", priority)| eval adjusted_priority = case(at_classtype == "trojan-activity", adjusted_priority+priority*4,at_classtype == "successful-admin", adjusted_priority+priority*4,at_classtype == "successful-user", adjusted_priority+priority*4,at_classtype == "denial-of-service", adjusted_priority+priority*4,at_classtype == "shellcode-detect", adjusted_priority+priority*4,at_classtype == "attempted-user", adjusted_priority+priority*3,at_classtype == "attempted-admin", adjusted_priority+priority*3,at_classtype == "attempted-dos", adjusted_priority+priority*3,at_classtype == "web-application-attack", adjusted_priority+priority*3,at_classtype == "string-detect", adjusted_priority+priority*3,at_classtype == "suspicious-login", adjusted_priority+priority*3,at_classtype == "protocol-command-decode", adjusted_priority+priority*3,at_classtype == "misc-attack", adjusted_priority+priority*3,at_classtype == "misc_activity", adjusted_priority+priority*2,at_classtype == "bad-unknown", adjusted_priority+priority*2,at_classtype == "not-suspicious", adjusted_priority+priority*1,at_classtype == "network-scan", adjusted_priority+priority*1,at_classtype == "undefined", adjusted_priority,at_classtype != "undefined", adjusted_priority) |eval highest_tag = mvindex('tag::eventtype', 0) |rex field=highest_tag "(?<at_priority>.*)__(?<at_action>.*)__(?<at_ticket>.*)__(?<at_title>.*)" |fillnull at_action value=Triage
