Nice coloring rules
Using custmized coloring rules in Wireshark is a perfect aproach of getting a clue of all the data running over your screen.
Just go to View/Coloring Rules/
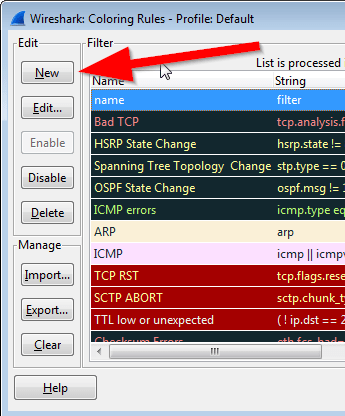
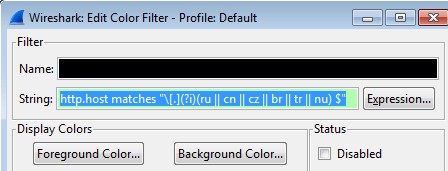
And add the below samples of filters into the "string" field.
| Description | string |
|---|---|
| Detect the presence of suspicious file downloads | frame matches “\.(?i)tar” or frame matches”MZ” or frame matches “\.(?i)exe” or frame matches “\.(?i)vbs” |
| Detect the presence of IRC or Bot Command and Control traffic | irc or frame matches “(?i) join” |
| Detect the presence of possible Bot Command and Control traffic based on unusual DNS traffic: | dns.count.answers > 10 |
| Detect the presence of a possible Man-in-the-Middle Attack | (arp.opcode == 1) && !(eth.dst == ff:ff:ff:ff:ff:ff) |
| Detect the presence of suspicious IP Header Options | ip.hdr_len > 20 &&! igmp |
| Detect the presence of obsolete ICMPv4 Types: | icmp.type >12 |
| Detect the presence of the Low Orbit Ion Cannon Bot Software | frame matches “(?i)probando” |
| Detect the presence of the Nessus Scanning Software | frame matches”(?i)nessus” or frame matches”(?i)qualys” |
| Detect the presence of the Retina / Ettercap Scanning Software | ip.id==0xe77e |
| Detect the presence of suspicious DNS Country Code extensions | http.host matches “\[.](?i) (ru || cn || cz || br || tr || nu) $” |
More coloring samples can be found at the Wireshark wiki.
