Tools'n links
Thanks to the contribution of several guys, this is a good compilation of sources.
Thanks to Fresh01
Information Gathering and Analysis
Google dorks – Using advanced operators in the Google search engine to locate specific strings of text within search results.
Maltego – An interactive data mining tool that renders directed graphs for link analysis.
FOCA – A tool used to find metadata and hidden information in the documents its scans.
http://checkusernames.com/ – Check the use of a brand or username on 160 social networks.
https://haveibeenpwned.com/ – Check if an account has been compromised in a data breach.
https://www.beenverified.com/ – Search people & public records.
Shodan – Search engine for Internet-connected devices.
Censys – A search engine that allows computer scientists to ask questions about the devices and networks that compose the internet.
Gephi – Visualisation and exploration software for all kinds of graphs and networks.
Fierce – A DNS reconnaissance tool for finding target IPs associated with a domain.
BuiltWith – Find out what websites are built with.
Wappalyzer – A cross-platform utility that uncovers the technologies used on websites.
https://aw-snap.info/ – Tools for owners of hacked websites to help find malware and recover their site.
http://themecheck.org/ – A quick service that lets you verify WordPress themes for security and code quality.
theHarvester – Gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers, and SHODAN.
Cymon.io – Tracker of malware, phishing, botnets, spam, and more.
Mnemonic – A passive DNS database.
Vulnerability Scanning and Penetration Testing
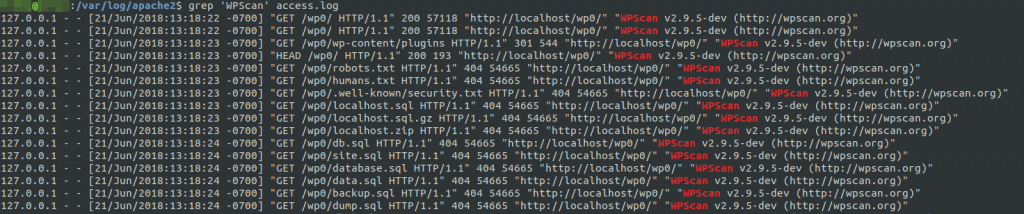
WPScan – A black box WordPress vulnerability scanner.
Sqlmap – An open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over database servers.
BeEF – A penetration testing tool that focuses on the web browser.
Firefox Hackbar – A simple security audit/penetration test tool.
Burp Suite – Software for web security testing.
OpenVAS – An open source vulnerability scanner and manager.
Fiddler – A free web debugging proxy.
Joomscan – Detect Joomla CMS vulnerabilities and analyse them.
Kum0nga – A simple Joomla scan.
Arachni – A feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of modern web applications.
Forensics and Log Analysis
Lnav – An advanced log file viewer.
Mandiant Highlighter – A free log file analysis tool.
Wp-file-analyser – Find modified, missing and extra files in a WordPress directory.
Auditd – Access monitoring and accounting for Linux.
Araxis Merge – Advanced 2 and 3-way file comparison (diff), merging and folder synchronisation.
WinMerge – An Open Source differencing and merging tool for Windows.
DiffNow – Compare files online.
Code and Malware Analysis
CyberChef – the Cyber Swiss Army Knife
UnPHP – A free service for analysing obfuscated and malicious PHP code.
UnPacker – JavaScript unpacker.
Jsunpack – A generic JavaScript unpacker.
JSBeautifier – An online JavaScript beautifier.
https://www.base64decode.org/ – Base64 Decode and Encode
https://www.urldecoder.org/ – URL Decode and Encode
http://lombokcyber.com/en/detools/decode-sourcecop – Decode SourceCop v3.x
Other Tools
regex101 – Develop and test regular expressions.
regexpal – Another site to develop and test regular expressions.
HashKiller – Online hash cracking service. Useful to reverse engineer hashes into passwords.
Noscript – Noscript is a Firefox extension that allows Javascript, Java and Flash to only be executed by websites that you define and trust.
Other Lists of Tools
Awesome Forensics – A curated list of awesome free (mostly open source) forensic analysis tools and resources.
awesome-incident-response – A curated list of tools and resources for security incident response, aimed to help security analysts and DFIR teams.
OSINT Framework – OSINT is short for ‘open source intelligence’. This site provides a graphical directory of OSINT resources.
Kali Linux
Kali Linux is a linux distribution that is the favourite of penetration testers and security analysts worldwide. It is a linux distribution that comes packed with security analysis tools. If you want to learn about cyber security, Kali should be one of your starting points.
sqlmap
SQL injection vulnerabilities can be devastating if exploited, and for better or worse, sqlmap is really good at finding them. It features a bevy of tests against a variety of DBMS backends from MySQL to Oracle, and can be used to automate much of the process of identifying and attacking injectable points on a site.
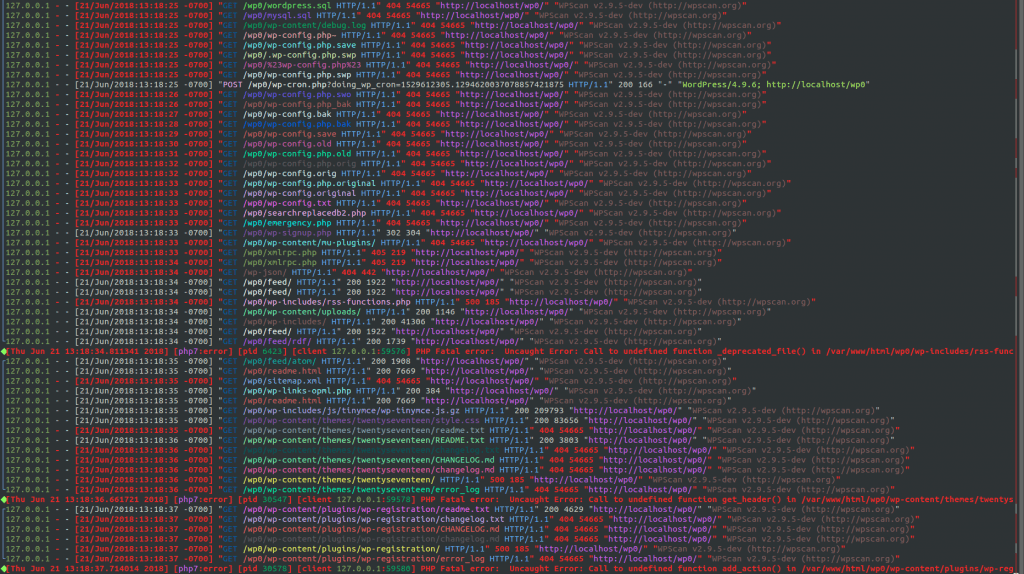
WPScan
With WordPress pulling in a respectable 59.9% of the CMS market share, it was inevitable that a highly specialized vulnerability scanner like WPScan would be developed for it. Launching WPScan is a common first step in black box audits of WordPress sites, due to its ability to divulge a great deal of information about a typical installation.
Thanks to Mikey Veenstra:
Forensics & Log AnalysisHighlighter
FireEye’s Highlighter is a graphically-focused log analysis utility which can be of great use to administrators and incident response personnel in the wake of an attack.
Viewing a histogram of log activity over time can provide a unique perspective on the timeline of a breach, and the ability to pinpoint keywords and whitelist known good items from your dataset can streamline the analysis process. Unfortunately, Highlighter hasn’t seen a new release since 2011 and thus only officially supports Windows 7 and below, but it certainly holds loyalty from those who started using it a few years ago.
lnav
For the Linux and Mac log reviewers, you can’t beat lnav. It presents itself as a small-scale log viewer, more suitable for quick review of specific data on a single host than tools like Splunk, which are firmly enterprise-scale and often require their own infrastructure.
Cool features like SQL query implementations and easy-to-read syntax highlighting make lnav a no-brainer to implement in log review processes, especially in cases where you’re performing a postmortem review for a third party and no formal log aggregation was in place before you got involved.
The Command Line
This one might be a bit of a cheat, but we couldn’t pass it up with all the write-ins for grep, awk, and the like on our team survey. Regardless of your workflow or your technology stack, it’s crucial to know your way around the utilities commonly built into the systems with which you interact.
In most cases, it’s also important to leave your comfort zone and familiarize yourself with operating systems you encounter less frequently. For instance, Linux-using researchers may find themselves wishing they knew more PowerShell when encountering a Windows system in an engagement. To help you brush up, the SANS Institute has published a number of easily digestible reference materials, including the Linux Shell Survival Guideand the PowerShell Cheat Sheet.
Malware AnalysisUnPHP
Web-based malware is commonly masked by one or more layers of obfuscation, where the code is deliberately made to be difficult or impossible for humans to read. UnPHP is a solid first-run choice for analysts who encounter obfuscated PHP scripts without the time or experience to deobfuscate them manually.
UnPHP isn’t a panacea, and there are a number of evasions used in malware obfuscation which it can’t quite crunch at this time, but it handles many common techniques with ease. Of particular note is its recursive deobfuscation, as UnPHP can identify when a decoded output is itself obfuscated and automatically process the new layer. Even though it may not solve everything you throw at it, it’s still a valuable time-saver for anyone who comes across obfuscated PHP.
CyberChef
Where clean interface design and an “automate the boring stuff” mindset collide, we get CyberChef. CyberChef is an easy-to-use web application built to accommodate a number of data manipulation tasks, from simple encoding and decoding to encryption and compression, in a repeatable format.
To this end, CyberChef allows the user to create and save “recipes” out of a series of operations. Instruction sets like “Gunzip, then ROT13, then Base64 decode, then ROT13 again” can be stored and reloaded to “bake” new inputs repeatedly. These operations can scale up to complete a number of tasks, especially with built-in functions to extract useful strings like IP addresses and emails from the decoded input.
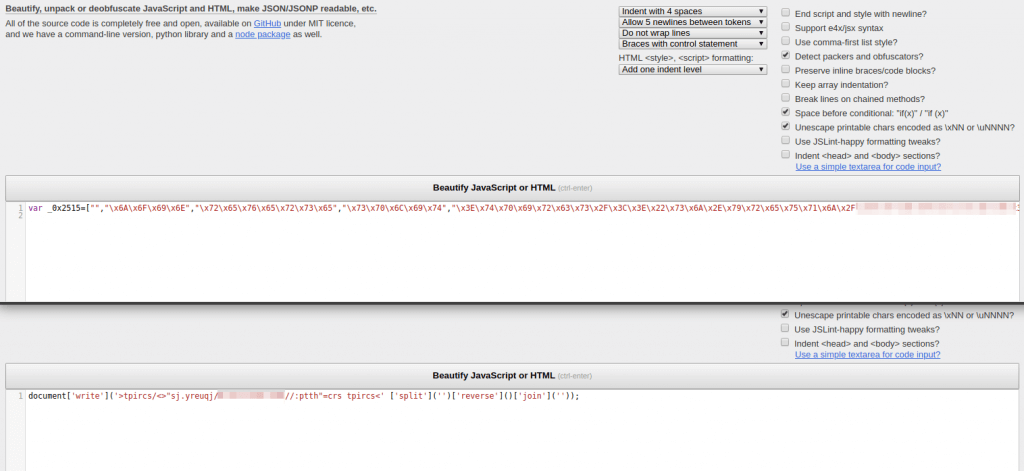
JS Beautifier
JavaScript minification is a standard process for just about every front-end web developer in the market, and malware developers are no stranger to this. JS Beautifier is a simple online tool used to automate the formatting of minified and obfuscated JavaScript into a human-readable document.
For the purposes of malware deobfuscation in particular, JS Beautifier can detect and reverse common obfuscation methods (notably packer, by Dean Edwards) as well as handling various character encodings like hexadecimal. Like UnPHP above, JS Beautifier isn’t a silver bullet that will take all of the work out of JS malware analysis, but it’s an excellent first step in almost every case.
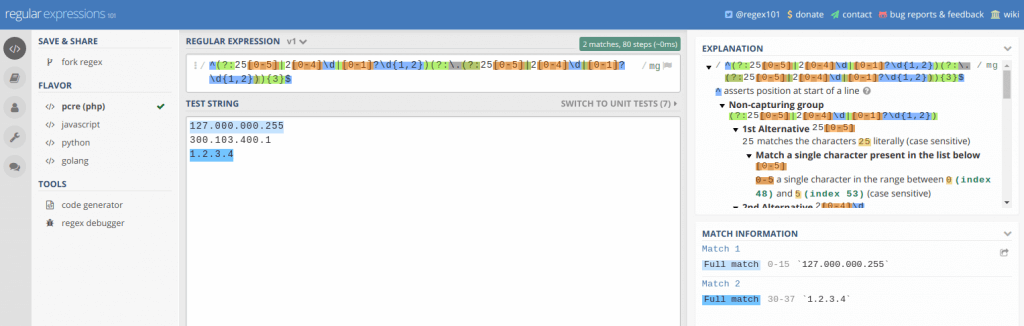
OtherRegex101
Whether writing a regular expression is a daily task or an occasional solution to a problem, Regex101 is sure to be of use. Users inexperienced with regex will quickly appreciate the availability of quick reference materials and a powerful Explanation view, which provides you with a breakdown of why your expression behaves the way it does.
Experienced users can make great use of Regex101 as well. The built-in debugger allows developers to observe their regex as it runs step-by-step, which helps to identify performance improvements. Even simply watching Regex101 follow along as you write an expression, highlighting matching content in your test string as you go, can be of great assistance in preventing simple issues in complex regular expressions that may have been considerably more difficult to debug if written unassisted.
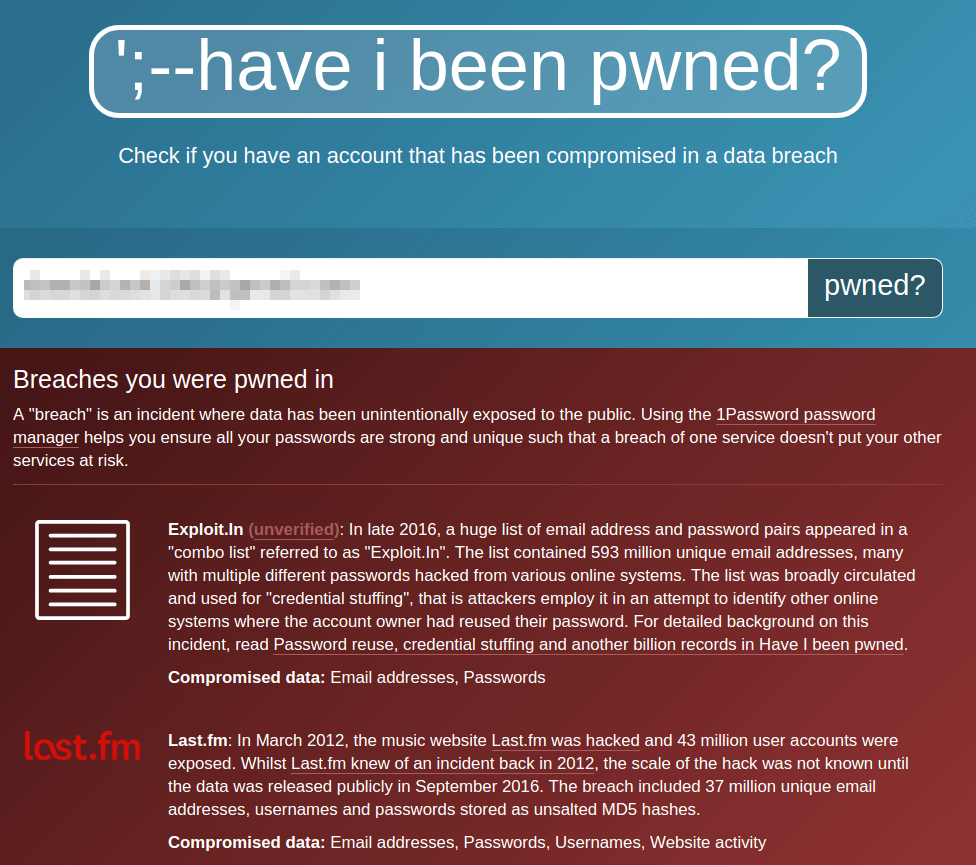
Have I Been Pwned?
Troy Hunt’s massive breach data aggregation project Have I Been Pwned? is a staple in information security awareness efforts. HIBP gives anyone on the internet the chance to know whether their personal data was associated with a publicly-known security breach. It provides a user-friendly breakdown of what particular data may have been stolen, as well as the source of each breach, if known. There’s also a separate API to check whether a given password has appeared in a breach, which we’ve built into Wordfence in an effort to prevent WordPress users from using compromised passwords.
While HIBP is of some use as a research tool, it excels at helping the layperson grasp the importance of security best practices. After all, there’s really no better way to convince your relatives that password reuse is dangerous than by showing them their data has probably already been breached.
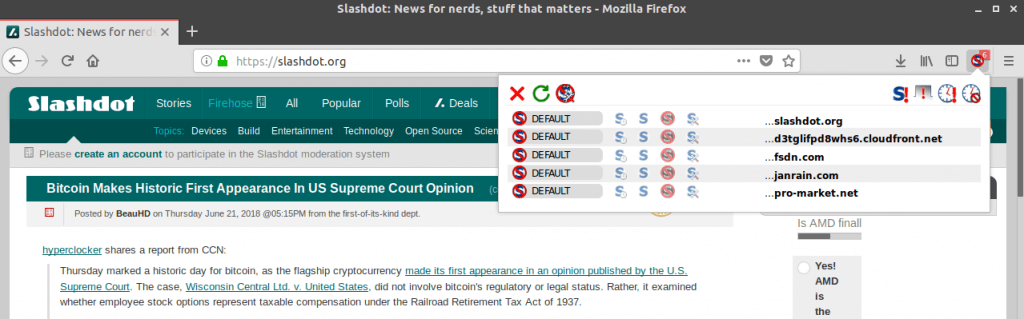
Noscript / uMatrix
Spending any amount of time interacting with infected websites has the potential to be unsafe, or at the very least annoying. Malicious scripts on the sites in question will be attempting a number of behaviors, like browser redirects and cryptomining, so having a readily-configurable browser extension to protect yourself from these scripts is important.
NoScript has been the giant in this market since the mid-2000s, providing users with the ability to automatically block all scripts from executing until whitelisted by domain or on a per-script basis. However, it’s currently only compatible with Firefox and other Mozilla software, which can be a limiting factor for many users.
The browser gap is largely filled by uMatrix, a browser firewall developed by the creator of the popular ad blocker uBlock Origin. uMatrix is compatible with Firefox, Chrome, and Opera, and offers similar functionality to NoScript in terms of unwanted script filtering. While it offers a bit more to the power-user, uMatrix is definitely less user-friendly than NoScript, and you’ll find “For Advanced Users” warnings across its entries in browser addon repositories and its GitHub project alike.