tor Proxy setup
While Cuckoo contacts the outer world with it's own source IP address and gives the destination a clue of which malware was found at your site, you need some privacy to avoid this traceback.
The below shows how to setup a tor proxy to obfuscate your requests.
Find this sources that helped me to write this article:
Following the torproject.org site for defining the apt sources for debian helps a lot finding the right apt settings you need.
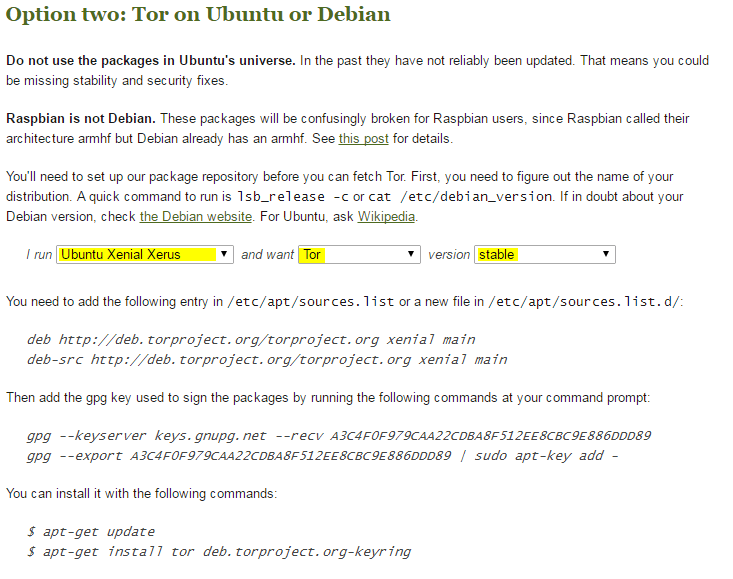
For Ubuntu 16.10 server I've used:
deb http://deb.torproject.org/torproject.org xenial main deb-src http://deb.torproject.org/torproject.org xenial main
gpg --keyserver keys.gnupg.net --recv A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
apt-get update apt-get install tor deb.torproject.org-keyring
For security reasons, I don't like the idea of having a tor socks proxy available for access within the network. Thus, I use privoxy as a frontend instead.
tor config
/etc/tor/torrc
SOCKSPolicy accept 127.0.0.1/32
SOCKSPolicy reject *
Privoxy config
sudo apt-get install privoxy
vi /etc/privoxy/config
and add (at least) those two lines:
forward-socks5 / 127.0.0.1:9050 .
In my case I also added the below lines:
listen-address 0.0.0.0:3128
listen-address 0.0.0.0:8080
forward 192.168.*.*/ .
forward 172.16.*.*/ .
forward 10.*.*.*/ .
forward 127.*.*.*/ .forward localhost/ .
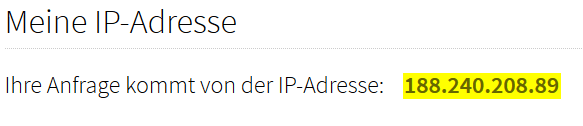
Now add [privoxy-ip]:8080 as proxy to your prevered browser and checkout your ip at heise.de
Below mentioned IP should not be the one you are comming from while surfing out your "un-tored" internet connection.