DeAuth-Attack detector using an ESP8266
Found a very interesting PoC at mobile hacker showing how to detect and alter DeAuth attacks using a tiny Wemos D1 mini.
Following the HowTo and installed all at the Wemos D1 mini board.
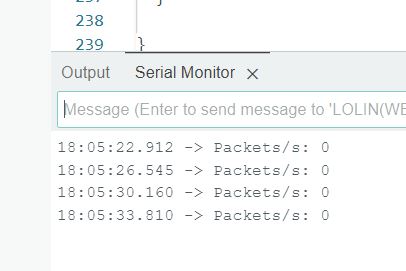
And see the result of an (not) ongoing DeAuth-Attack,
Now let's prove it realy does detect an attack.
While using another project for the ESP8266 to DeAuth-Attack my own WiFi, the detector shows an ongoing attack. !!!
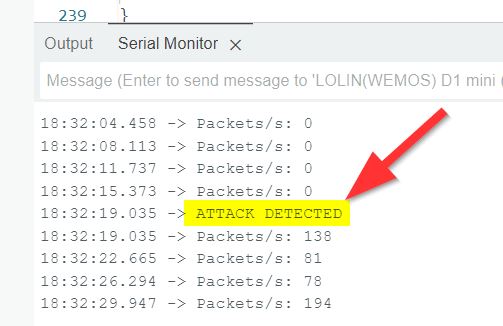
Next topic will be to add MQTT connectivity to have an ongoing attack also visible within the ioBroker.
Neue TLD .zip bietet gutes Phishing
Google bietet seit kurzem die Möglichkeit sie Domains mit der Endung .zip zu registrieren.
Das wird nicht nur von legitimen Akteuren genutzt. Wie bei solchen Toplevel Domains üblich gibt es auch jede Menge Schattengestalten die dies für ihre Geschäfte (meist Phising) nutzen.
Einen kleinen Einblick bietet dieser Link der einen Auszug aus den aktuell registrierten TLDs zeigt.
Neue TLD .zip bietet gutes Phishing
Google bietet seit kurzem die Möglichkeit sie Domains mit der Endung .zip zu registrieren.
Das wird nicht nur von legitimen Akteuren genutzt. Wie bei solchen Toplevel Domains üblich gibt es auch jede Menge Schattengestalten die dies für ihre Geschäfte (meist Phising) nutzen.
Einen kleinen Einblick bietet dieser Link der einen Auszug aus den aktuell registrierten TLDs zeigt.
MS Sharepoint scant PW-gesicherte Archive
Wie aus einem Blog von Andrew Brandt zu erfahren war, scant MS Sharepoint wohl ebenfalls kennwortgesicherte Archive auf Malware.
Im weiteren Threat ist zu lesen, dass MS sich wohl einer Passwortliste und in Mails übermittelte Kennwörter bedient, um den Inhalt der Archive zu scannen.
HP LaserJet CVE-2023-27971 CVSS 8.8 privilege elevation
wie hp schreibt, gibt es bei (wenigstens) der nachfolgenden Modellen ein größeres Problem wodurch Rechte auf dem Gerät ausgeweitet werden können. Als Fix bleibt wohl nur ein Update der Firmware.
Ein adHoc-Prüfung gab keinerlei Findings bei FI-TS.
| Product Name | Model Number | Updated Firmware Version |
HP Color LaserJet MFP M478-M479 series | W1A75A, W1A76A, W1A77A, W1A81A, W1A82A, W1A79A, W1A80A, W1A78A | 002_2310A or higher |
HP Color LaserJet Pro M453-M454 series | W1Y40A, W1Y41A, W1Y46A, W1Y47A, W1Y44A, W1Y45A, W1Y43A | 002_2310A or higher |
HP LaserJet Pro M304-M305 Printer series | W1A66A, W1A46A, W1A47A, W1A48A | 002_2310A or higher |
HP LaserJet Pro M404-M405 Printer series | W1A51A, W1A53A, W1A56A, W1A63A, W1A52A, 93M22A, W1A58A, W1A59A, W1A60A, W1A57A | 002_2310A or higher |
HP LaserJet Pro MFP M428-M429 f series | W1A29A, W1A32A, W1A30A, W1A38A, W1A34A, W1A35A | 002_2310A or higher |
HP LaserJet Pro MFP M428-M429 series | W1A28A, W1A31A, W1A33A | 002_2310A or higher |
Quelle: HP Support Seite
Heute "World Password Day"
Jeden ersten Donnerstag im May ist der "Welt Passwort Tag", so wie heute am 04.05.23 auch.
Auch wenn heute schon Techniken existieren die klassischen Passworte abzulösen, haben wir noch immer mit jeder Menge davon zu tun.
Durch Nutzung von Password-Safes etc. hat sich die Lage sicherlich verbessert jedoch sehe ich in meinem privaten Umfeld noch immer die Nutzung von sehr unsicheren Kennwörtern.
Da stellt sich natürlich die Frage, wie ein sicheres Kennwort aussieht und wie man sich das merken soll? Nun, schon vor Jahren habe ich dazu Gedanken publiziert (Quelle).
Letztendlich zeichnet sich ein gutes Password durch seine Länge aus. Nutzen Sie einen (möglichst) unlogischen Satz als Kennwort.
Beispielsweise "MeineWebseitehat4arme##"
- Lang (>12 Zeichen), damit ein Bruteforce-Angriff möglichst lange dauert.
- Unlogisch, damit eine Dictionary-Attacke keinen Erfolg hat
Natürlich ist das kein Garant für ein unknackbares Kennwort aber es erhöht doch den Aufwand für einen Angreifer enorm es maschinell zu "knacken."
PentestGPT - AI supported pentesting
 Ein "early stage" PoC von GreyDGL zeigt wie mittels ChatGPT-Unterstützung ein Pentest unterstützt werden kann. Also die Interpretationen der jeweiligen Ergebnisse von der AI erledigt werden.
Ein "early stage" PoC von GreyDGL zeigt wie mittels ChatGPT-Unterstützung ein Pentest unterstützt werden kann. Also die Interpretationen der jeweiligen Ergebnisse von der AI erledigt werden.
Wer also kein Problem damit hat seine Daten an openAI zu senden, kann sich hiermit viel Zeit sparen.
Intel schmilzt noch immer
Wie Marc Stöckel von Tarnkappe schreibt, ist es einer Forschergruppe gelungen einen weiteren Seitenkanalangriff auf Intel-CPUs aufzudecken. Da ja das "Meltdown-Problem" in Hardware "gegossen" ist, werden uns derartige Veröffentlichungen noch eine ganze Weile begleiten. Das Positive an der aktuellen Entdeckung ist jedoch, dass sich der Angriff alles andere als einfach gestaltet.
“Dieser Timing-Angriff stützt sich auf andere transiente Ausführungsangriffe, um einen realen Angriff aufzubauen, und er kann leicht durch Rauschen gestört werden. Dennoch handelt es sich um einen neuen Seitenkanalangriff, der eine weitere Erforschung wert ist. Dieser Angriff kann Einblicke in neue Angriffe auf die Mikroarchitektur geben und einen neuen Weg zur Entwicklung von Seitenkanalangriffen in Cache-Seitenkanal-resistenten CPUs eröffnen.”
ForschungsberichtGoogle Cloud europe-west9-a Zone
Auch die Cloud hat ihre Schwächen.
Google schreibt auf seiner Service Health Seite, dass das Pariser Rechenzentrum wegen "water intrusion" nicht (oder nur teilweise) erreichbar ist.
Bitmarck - IT-Dienstleister der Krankenkassen (wieder) gehackt
Wie Bitmarck auf seinen temporären Website schreibt, hat man dort eine Cyberattacke identifiziert und daraufhin die Systeme vom Netz genommen.
Was ist passiert?
BITMARCK hat eine Cyberattacke identifiziert und über unsere Frühwarnsysteme einen Angriff auf BITMARCK-interne Systeme gemeldet. Im Rahmen unserer Sicherheitsprotokolls hat BITMARCK seine Kunden- und interne Systeme im Anschluss kontrolliert vom Netz genommen. Die zuständigen Behörden wurden über den Vorfall informiert. Unsere Analysen, die wir mit externen Experten vornehmen, konnten bisher keine Datenabflüsse festzustellen. Die Abschaltung, Analyse und Wiederinbetriebnahme erfolgen entsprechend der allseits abgestimmten Sicherheitsrichtlinien von BITMARCK.
Sind Kunden- oder Versicherten-Daten abgeflossen?
Nein, es hat nach aktuellem Kenntnisstand keinen Abfluss von Daten gegeben, weder bei BITMARCK noch bei Kunden oder Versicherten. Die Sicherheit unserer Kunden- und Versichertendaten hatte und hat sowohl bei der Abwehr des Angriffs als auch bei der Wiederinbetriebnahme unserer Systeme höchste Priorität.
Inwiefern sind die Daten der elektronischen Patientenakte (ePA) betroffen?
Die in der ePA hinterlegten Daten waren und sind durch den Angriff zu keiner Zeit gefährdet. BITMARCK hat gemäß gematik-Spezifikationen keinen Zugriff auf sich in der ePA befindliche Daten.
Wie wirken sich die Sicherheitsmaßnahmen aus?
Gesetzliche Krankenversicherungen, die ihre IT bei BITMARCK betreiben lassen, sind von den Präventivmaßnahmen in unterschiedlicher Weise betroffen. Im Zuge dieser Maßnahmen kommt es bei den Kunden, insbesondere gesetzlichen Krankenversicherungen sowie bei BITMARCK selbst allerdings zu erheblichen technischen Störungen und zu großen Einschränkungen im Tagesgeschäft. Speziell die Betreuung der Versicherten ist in punkto Erreichbarkeit, Beratung und Service stark eingeschränkt – davon ist auch der Datenaustausch betroffen.
Nordrhein-Westfalen und das Abitur
Wie sicherlich aus der Presse schon erfahren, hatten überlastete Server wohl eine gravierende Panne beim Abitur ausgelöst. Letztendlich mussten die Klausuren in Biologie, Chemie, Ernährungslehre, Informatik, Physik sowie Technik (Grund- und Leistungskurs) verschoben werden.
 Was aber weniger "laut" in der Presse zu vernehmen war, ist die Tatsache dass das komplette AD offen verfügbar war. (Wie Lilith Wittman auf Twitter schreibt.
Was aber weniger "laut" in der Presse zu vernehmen war, ist die Tatsache dass das komplette AD offen verfügbar war. (Wie Lilith Wittman auf Twitter schreibt.
"Das waren mehr als 500 - nämlich euer ganzes Active Directory - >16000 User mit Namen, E-Mails und Jobs - und das hat einige andere interessante Sicherheitslücken eröffnet. zB Account-Takeovers von E-Mail-Adressen, bei denen Domains nicht mehr existierten."
Ransomware Angriff auf NCR
Wie NCR auf seiner Status-Seite schreibt, wurde die Firma am 13.4.23 Opfer einer Ransom-Attacke was zu einem kompletten Ausfall eines Datacenters geführt hat.
"On April 13, NCR determined that a single data center outage that is impacting some functionality for a subset of its commerce customers was caused by a cyber ransomware incident. Upon such determination, NCR immediately started contacting customers, enacted its cybersecurity protocol and engaged outside experts to contain the incident and begin the recovery process. The investigation into the incident includes NCR experts, external forensic cybersecurity experts and federal law enforcement."
BSI Warnung ntp 4.2.8p15
Das BSI hat am Mittwoch (12.4.23) eine Warnung bzgl. einer ntp-Version ausgesprochen.
Im weiteren Verlauf und Analysen durch die Community wurde jedoch klar, dass sich die Gefahr weitaus geringer darstellt. Kurz und knapp, nur beim Einsatz eines "Trimble Palisade GPS-Empfängers" kommt es zu einem "kleinen" Treiberproblem. Wie heise.de schön zusammenfasst.
Ungeachtet haben wir natürlich bereits die Betroffenheit unserer Systeme geprüft und adäquate Maßnahmen ergriffen.
Analyse des VulkanFiles Leaks
SEKOIA.IO hat in einem ausführlichen Blog-Artikel die sog. VulkanFiles analysiert. Diese Dateien sind aus einem der letzten Leaks und beschreiben ein offensives Cyber Project des Russischen Verteidigungs-Ministerium aus den Jahren 2016-2019.
"Conclusion
Exfiltrated Vulkan documents provided insights into two different information systems supposedly designed for Russian military intelligence services. If Scan-AS, a tool used to map and prepare operations on advisory networks, is relatively common and expected, Amezit particularly caught SEKOIA.IO analysts’ attention.
Amezit global system gathers infrastructure control features – communications interception, analysis and modification – and information level control features – internet monitoring and automated content creation. In this sense, Amezit is an illustration of the Russian information warfare doctrine, a concept which looks for strategic gains through the combination of offensive cyber operations, electronic warfare, psychological operations, and information operations."
3CX VoIP-Client kompromittiert
Das BSI warnt vor einer kompromittierten Version des beliebten VoIP-Clients.
"Am 29. März 2023 berichteten verschiedene Quellen darüber, dass sich eine kompromittierte Fassung des Voice over IP (VOIP)-Clients 3CX Desktop App im Umlauf befinde. Die Software ist zwar durch den Hersteller signiert, enthält jedoch schadhafte Elemente, die der Funktion eines Trojaners entsprechen. Grund dafür ist eine manipulierte DLL-Datei."
GPT4ALL - ein lokales chatGPT
Welche Möglichkeiten sich durch ein lokales, selbst gehostetes chatGPT Klone ergeben, ist sicherlich nur der persönlichen Phantasie geschuldet. Jedoch zeigt nomic-ai in seinem Repository wie eine lokale Instanz zu betreiben wäre. - Definitiv ein Tag "Play-Time" wert, dies als PoC aufzusetzen.
Azure Active Directory ermöglichte Datenklau bei Office365-Kunden
heise.de Berichtet über eine Publikation der Sicherheitsfirma Wiz, wonach es möglich war durch eine SEO-Manipulation Zugriff auf interne Administrationswerkzeuge der Bing-Suchmaschine zu gelangen.
"Über manipulierte Suchergebnisse in Microsofts Suchmaschine Bing konnte ein Sicherheitsforscher eigene Ergebnisse ganz oben in der Liste platzieren und mit Schadcode versehen. Der hätte dann zum Beispiel Zugangscookies von angemeldeten Office365-Kunden stehlen können.
Microsoft bietet das Azure Active Directory als Cloud-Dienst für Kunden an, nutzt das System jedoch auch für interne Dienste zum Identitätsmanagement. Der Forscher erlangte mit seinem Azure-AD-Nutzer durch eine Fehlkonfiguration Zugriff auf interne Administrationswerkzeuge für die Bing-Suchmaschine und konnte dort dann weitgehend frei schalten und walten."
GCHQ: CyberChef Ver. 10 released
 Der britische Geheimdienst (GCHQ) hat eine neue Version 10 des CyberChef Tools veröffentlicht die verschiedene Konstelationen vereinfachen.
Der britische Geheimdienst (GCHQ) hat eine neue Version 10 des CyberChef Tools veröffentlicht die verschiedene Konstelationen vereinfachen.
CyberChef v10 führt eine Reihe neuer Funktionen in den Eingabe- und Ausgabefenstern ein:
- Statusleisten, die Statistiken und Optionen in Bezug auf die Daten anzeigen Auswahl der Zeichenkodierung, um explizit festzulegen, wie Eingabedaten kodiert und Ausgabedaten dekodiert werden sollen
- Auswahl des Trennzeichens für das Zeilenende zur Verbesserung der Datenintegrität
- Darstellung von nicht druckbaren Zeichen, um sicherzustellen, dass Sie immer genau wissen, womit Sie arbeiten
- Verbessertes Laden von Dateien, so dass Sie jede Datei, die Sie in das Tool laden, bearbeiten können
- Eine Reihe von modernen Editor-Funktionen wie rechteckige Auswahlen, Klammerabgleich und Auswahlabgleich
Darüber hinaus wurde eine neue kontextbezogene Hilfefunktion hinzugefügt, die durch Drücken von F1 aktiviert wird, während Sie den Mauszeiger über eine Funktion bewegen, über die Sie mehr erfahren möchten.
CISA: MS Cloud Secuity "untitled goose"
Die CISA veröffentlich ein Tool (Untitled Goose) auf GitHUB um maliziöse Aktivitäten in der MS Cloud zu erkennen. - Ein definitives "must try" als Erweiterung der bestehenden Could Monitoring Plattform.
"Untitled Goose Tool is a robust and flexible hunt and incident response tool that adds novel authentication and data gathering methods in order to run a full investigation against a customer’s Azure Active Directory (AzureAD), Azure, and M365 environments. Untitled Goose Tool gathers additional telemetry from Microsoft Defender for Endpoint (MDE) and Defender for Internet of Things (IoT) (D4IoT)."
Mastodon: Datenleck
Wie Mastodon.social am 16.3.23 schreibt, hat man am 24.2.23 dort festegestellt, das ein fehlerhaft konfigurierter S3-Bucket zu einer möglichen Datenabwanderung führte, wenn User vorher Datenexporte durch Dritte beauftragt haben.
Die Konfiguration wurden innerhalb von nur 30 Minuten korrigiert, jedoch soll die Fehlkonfiguration seit dem 2.2.23 existiert haben.