Video: Android malware analysis - fake Sagawa malware

Lukas provides us a cool video showing his androis malware analysis of a sms worm that spies on victims.
Myself in the news ...
Myself a little proud of geting in the news. #weareairbus
Read the linkedIN article here.
Naked Security: How Chrome and Firefox could ruin your online business this month
Sophos Naked Security is giving us a cool news about Forefox and Chrome to block certificates signed by Symantec.
Most people who use Google’s popular browser will receive the update, and either won’t realise or won’t especially care about the changes it contains.
Next Tuesday, Firefox 63 will be released, and much the same thing will happen for users of Mozilla’s browser.
But one of the changes common to both those products, which have a huge majority of the market share amongst laptop users, may matter very much to a small but significant minority of website operators.
Chrome 70 and Firefox 63 will both be disowning any web
certificates signed by Symantec.
From this month, anyone
with Chrome or Firefox who browses to a web page “secured” with a Symantec
certificate will see an unequivocal warning insisting that the site is
insecure:
continue Paul Ducklins article here.
Known issues updating to Windows 10, version 1809 (2.Oct.2018)
See your personal data leaving to heaven ... :-)
Doublecheck the
rollout of the latest MS patch carefully.
We have paused the rollout of the Windows 10 October 2018 Update (version
1809)* for all users as we investigate isolated reports of users missing
some files after updating.
For the latest information on this issue please
see John Cable's
blog.
ICANN changes DNSSEC Keys *TODAY* 11.Oct.18
While the majority of DNS resolvements are transfered via DNSSEC, the root DNS servers need to renew their DNSSEC kyes from time to time.
As the new keys have been setup a while a go already, it's just the question if your own (or the one of your provider) DNS server has already established these new keys. - If not, DNS resolvements will fail from today on.
See this list of DNS servers known, that have failed installing the new keys. This is just the minimum servers, there will be much more.
WhatsApp: Heap Corruption in RTP processing
Googles ProjectZero team found a major security issue in WhatsApp.
To
solve this issue and not loose your phone by simply receiving a WhatApp video
call, just update to the latest version.
Greenbone VA: Check for Ver. 4.2.21
If you are about to update for GOS version 4.2.21, rather check with the Greenbone support for some "feature" you might not expect... ;-)

Bloomberg: The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies
Bloomberg is writing about a very scary situtaion (here).
Although I personally remember a situation of the US planting a special IOS into Cisco equipment as well, it's scarry that even the Chinese have been cought in doing things like that. So rather doublecheck your Supermicro mainboard....
During the ensuing top-secret probe, which remains open more than three years later, investigators determined that the chips allowed the attackers to create a stealth doorway into any network that included the altered machines. Multiple people familiar with the matter say investigators found that the chips had been inserted at factories run by manufacturing subcontractors in China.
70+ different types of home routers(all together 100,000+) are being hijacked by GhostDNS
Thanks to Erik who found a GhostDNS implementation reported by yegenshen.
Statistics of Infected Routers
Based on the logs of GhostDNS from 09-21 to 09-27, we have observed 100k+ infected router IP addresses (87.8% located in Brazil), involving 70+ router/firmwares. Due to the dynamic updates of router IP address, the actual number of infected devices should be slightly different.

read the full articel here for background and a lot of IOCs.
Hybrid Analysis with new YARA capabilities from Falcon MalQuery
Use the famous HybridAnalysis with YARA matchings from Crowdstrike Falcon MalQuery.
Sometimes dreams come true. ;) Today, we are announcing a
revoluationary new search capability to our Hybrid Analysis community platform,
which has been implemented as part of a powerful new YARA hunt and binary
pattern search capability. Including custom search filters (e.g. date ranges)
and efficacy evaluation over petabytes of data. In order to facilitate this type
of research by the security community, CrowdStrike has donated Falcon
MalQuery, its rapid malware search engine technology, to the
community.
Thunderbird / Enigmail does not encrypt while saying it does
Please be aware, that the PGP addon for Thunderbird and Outlook does not encrypt mails while telling you it does (If used in the default "Junior" settings)
The way to mitigate this, is to change the default setting to force (either S7MIME or pep) as:
Preparing for a "Lunch&Learn" - OSINT
See my work in progress while I prepare myself for the upcoming Lunch&Learn of OSINT
Great help for reconnaissance
A amazing job for reconnaissance can be achieved by using the tool of hdm. It will download and normalize all mayor (and free) sources that you would need to search truogh while doing reconnaissance anyway.
I've already started my PoC, so stay tuned...
Internet Data Download
Download and normalize internet data from various sources. This package is normally run on a daily basis (after 10:00am CST).
Data Sources
| Name | Description | Price |
|---|---|---|
| Sonar | FDNS, RDNS, UDP, TCP, TLS, HTTP, HTTPS scan data | FREE |
| Censys.io | TCP, TLS, HTTP, HTTPS scan data | FREE (non-commercial) |
| CT | TLS | FREE |
| CZDS | DNS zone files for "new" global TLDs | FREE |
| ARIN | American IP registry information (ASN, Org, Net, Poc) | FREE |
| CAIDA PFX2AS IPv4 | Daily snapshots of ASN to IPv4 mappings | FREE |
| CAIDA PFX2AS IPv6 | Daily snapshots of ASN to IPv6 mappings | FREE |
| US Gov | US government domain names | FREE |
| UK Gov | UK government domain names | FREE |
| RIR Delegations | Regional IP allocations | FREE |
| PremiumDrops | DNS zone files for com/net/info/org/biz/xxx/sk/us TLDs | $24.95/mo |
| WhoisXMLAPI.com | New domain whois data | $109/mo |
APT38: Details on New North Korean Regime-Backed Threat Group
FireEye gives us some background on APT38

Meet Black Rose Lucy, the Latest Russian MaaS Botnet
Checkpoint did a brilliant research on the "Malware as a Service" (MaaS) of Black Rose that was discovered. - Brilliant for the less techy criminal, or those that would like to enter that market.
Research By: Feixiang He, Bogdan Melnykov, Andrey Polkovnichenko
An organization needs to have a collaborative hiring process, advised Steve Jobs. Always a group to follow mainstream trends closely, in recent years we’ve seen cyber criminals take greater heed of this advice by increasingly hiring cyber mercenaries and Malware-as-a-Service (MaaS) providers as a way to carry out their malicious activities.
Instead of gathering an all-around team that possesses the required skillset necessary for initiating an attack completely from scratch, many threat actors prefer hiring smaller groups with a much more specialized skill set. Indeed, such threat actors buy malware services from MaaS providers in a similar way as legitimate organizations purchase cloud services, for example.
Recently, with the help of David Montenegro, the Check Point Research intercepted a new MaaS product, Black Rose Lucy, developed by a Russian speaking team whom we have dubbed ‘The Lucy Gang’.
At the time of writing, we believe the Lucy Gang has already conducted various demos to potential malicious clients and while it may well still be in its early stages, given time it could easily become a new cyber swiss army knife that enables worldwide hacker groups to orchestrate a wide range of attacks. Our analysis of this product below reveals the latest trends in the underground MaaS market. continue here...
Hackers Target Port of Barcelona, Maritime Operations Not Affected
Do you rememeber the nopetya breakout at MAERSK? Now, this is at least the same attempt in Barcelona...
https://twitter.com/portofbarcelona/status/1042701903270961152
As per electiq
Summary
Reportedly, on September 20, 2018 the Port of Barcelona has fallen a victim of a cyber-attack that affected some of its servers and systems, forcing the organization to launch the contingency plan designed specifically for these incidents.
Key Findings:
· The port of Barcelona is yet to determine the scale of damage caused by the cyber-attack. Currently is only known that the attackers hit several servers at the infrastructure.
· Maritime operations were not affected. Land operations, such as reception and delivery of goods, also remained unaffected by the attack.
Analysis
The Port of Barcelona said that it has already informed law enforcement agencies about the incident and simultaneously has initiated legal actions against the attack.
CVE-2018-8392 | Microsoft JET Database Engine Remote Code Execution Vulnerability
Security Vulnerability (Keep the fingers off the JET Database Engine)
Published: 09/11/2018
MITRE
CVE-2018-8392
A buffer overflow vulnerability exists in the Microsoft JET Database Engine that could allow remote code execution on an affected system. An attacker who successfully exploited this vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
To exploit the vulnerability, a user must open a specially crafted Excel file while using an affected version of Microsoft Windows. In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted Excel file to the user, and then convincing the user to open the file.
The security update addresses the vulnerability by modifying how the Microsoft JET Database Engine handles objects in memory.
Wired: THE MIRAI BOTNET ARCHITECTS ARE NOW FIGHTING CRIME WITH THE FBI
Wired is telling us about the "bad guys" now become the "good guys"...
THE THREE COLLEGE-AGE defendants behind the the Mirai botnet—an online tool that wreaked destruction across the internet in the fall of 2016 with powerful distributed denial of service attacks—will stand in an Alaska courtroom Tuesday and ask for a novel ruling from a federal judge: They hope to be sentenced to work for the FBI. continue ...
Avira: XBash – the all-in-one botnet
Avira is giving us news about a new "evil at the sky" that has been discovered by Palo Alto Networks, infecting Windows and Linux servers.
It is specialized in taking over Hadoop, Redis, and Active MQ servers and tries to brute-force into services like web servers (HTTP), VNC, MariaDB, MySQL, PostgreSQL, Redis, MongoDB, Oracle DB, CouchDB, ElasticSearch, Memcached, FTP, Telnet, RDP, UPnP/SSDP, NTP, DNS, SNMP, LDAP, Rexec, Rlogin, Rsh, and Rsync.
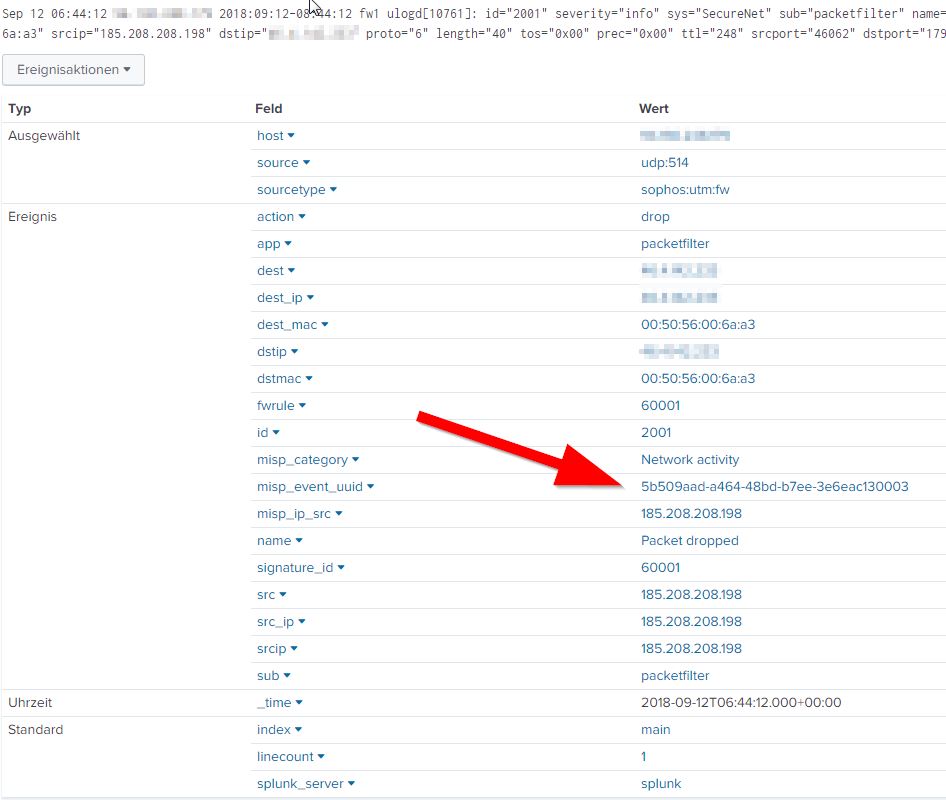
Splunk MISP feed integration
FX GANZER relesed a Splunk app to integrate your MISP data into Splunk and automatically match it on the most important fields of your log data.
EXCELLENT WORK .... ! ! !
I've installed it within my dev environment and had fantastic results already out-of-the box. Afetr a bit of tuning, PERFECT.
It comes with a complete dashboard:

An the correlation is done automatically to give you the correct MISP UUID to search for in your MISP.