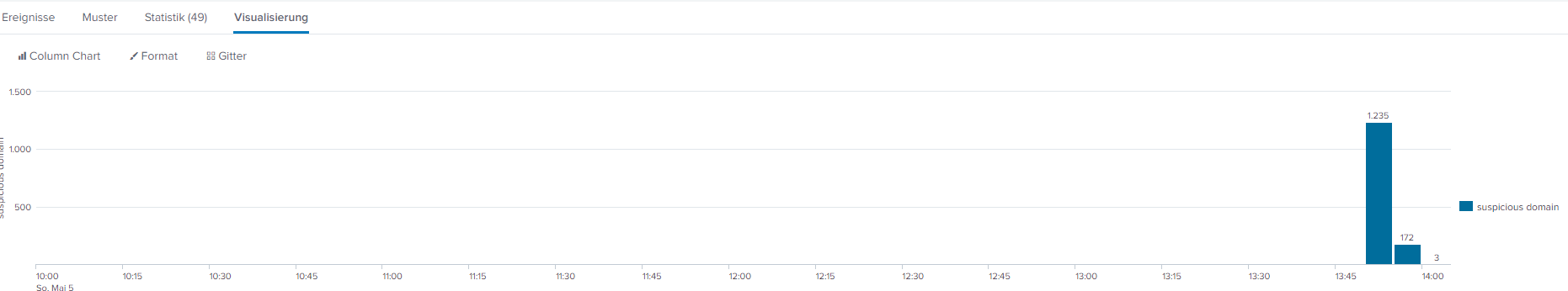Find suspicious phshing domains
This add-on for Splunk can be used to monitor certificate transparency logs.
For example to watch certificates issued for your domains or malicious look-a-likes.
It outputs the certificate logs as CIM compliant events in Splunk. This allows you to create an alert in Splunk or Splunk Enterprise Security that fires when a certificate gets issued for your-domain-suspicious-fishing-domain dot tld.
So you can create a wildcard watchlist for your personally owned domains to see if some registration of SSL certificates of equal domains are seen by Google.
But....
In addition, I found x0rz/phishing_catcher at GITHUB who does even a bit more in terms of finding *all* suspicious domains google sees.
It outputs a suspicious_domains.log that can be imported and correlated directly into Splunk.
Taking this and inputlookup it against your e.g. proxylogs gives you even more in terms of identifying potential fraud going on.
inputs.conf
[monitor:///opt/phishing_catcher/suspicious_domains.log]
disabled = false
sourcetype = phishing_domain
probs.conf
[phishing_domain]
DATETIME_CONFIG = CURRENT
LINE_BREAKER = ([\r\n]+)
NO_BINARY_CHECK = true
SHOULD_LINEMERGE = false
category = Application
disabled = false
pulldown_type = true
REPORT-domain = REPORT-domain
transforms.conf
[REPORT-domain]
DELIMS = "$"
FIELDS = "domain"
sourcetype=phishing_domain | timechart count(domain) AS "suspicious domain" span=5m