Windows Programm Execution Artefacts
- Prefetch
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Increases performance of a system by pre-loading code pages of commonly us...
mehr... - MRU - Last visited or MostRecentlyUsed
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Tracks the specific executable used by an application to open the files ...
mehr... - SRUM - System Resource Usage Monitor
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Windows 10 Background Activity Moderator (BAM) Location Win10: SYSTEM\...
mehr... - SRUM - System Resource Usage Monitor
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Records 30 to 60 days of historical system performance. Applications run, ...
mehr... - Amcache.hve
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description ProgramDataUpdater (a task associated with the Application Experience Se...
mehr... - Jump List
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description The Windows 7 task bar (Jump List) is engineered to allow users to “jump” ...
mehr... - Shimcache
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Windows Application Compatibility Database is used by Windows to identify ...
mehr... - Windows 10 RecentApps
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description GUI Program execution launched on the Win10 system is tracked in the Rec...
mehr... - Windows 10 Timeline
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description Win10 records recently used applications and files in a “timeline” accessi...
mehr... - UserAssist
inspired and sourced by https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download Description GUI-based programs launched from the desktop are tracked in the launcher...
mehr...
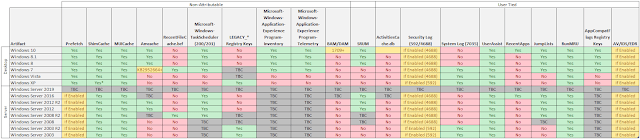
Windows: Available Artefacts - Evidence of Execution

Adam Harrison hast done a great article including the below table of where to look first while forensically examining a windows machine.
The table below details some of the artifacts which evidence program execution and whether they are available for different versions of the Windows Operating System
Summary of Artifacts
What follows below is brief details on the availability of these artifacts, some useful resources for additional information and tools for parsing them. It is not my intention to go into detail as to the functioning of the artifacts as this is generally already well covered within the references.
PrefetchPrefetch has historically been the go to indication of process execution. If enabled, it can provide a wealth of useful data in an investigation or incident response. However, since Windows 7, systems with an SSD installed as the OS volume have had prefetch disabled by default during installation. With that said, I have seen plenty of systems with SSDs which have still had prefetch enabled (particularaly in businesses which push a standard image) so it is always worth checking for. Windows Server installations also have Prefetch disabled by default, but the same applies.
The following registry key can be used to determine if it is enabled:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\PrefetchParameters\EnablePrefetcher
0 = Disabled
1 = Only Application launch prefetching enabled
2 = Only Boot prefetching enabled
3 = Both Application launch and Boot prefetching enabled
References/Tools:
https://www.forensicmag.com/article/2010/12/decoding-prefetch-files-forensic-purposes-part-1
https://github.com/EricZimmerman/Prefetch
ShimCacheIt should be noted that the presence of an entry for an executable within the ShimCache doesn't always mean it was executed as merely navigating to it can cause it to be listed. Additionally Windows XP ShimCache is limited to 96 entries all versions since then retain up to 1024 entries.
ShimCache has one further notable drawback. The information is retained in memory and is only written to the registry when the system is shutdown. Data can be retrieved from a memory image if available.
References/Tools:
https://www.fireeye.com/blog/threat-research/2015/06/caching_out_the_val.html
https://www.andreafortuna.org/cybersecurity/amcache-and-shimcache-in-forensic-analysis/
https://github.com/EricZimmerman/AppCompatCacheParser
MUICachePrograms executed via Explorer result in MUICache entries being created within the NTUSER.DAT of the user responsible.
References/Tools:
http://windowsir.blogspot.com/2005/12/mystery-of-muicachesolved.html
http://what-when-how.com/windows-forensic-analysis/registry-analysis-windows-forensic-analysis-part-8/
Amcache / RecentFileCache.bcfAmcache.hve within Windows 8+ and RecentFileCache.bcf within Windows 7 are two distinct artifacts which are used by the same mechanism in Windows to track application compatibility issues with different executables. As such it can be used to determine when executables were first run.
References/Tools:
https://www.andreafortuna.org/cybersecurity/amcache-and-shimcache-in-forensic-analysis/
http://www.swiftforensics.com/2013/12/amcachehve-in-windows-8-goldmine-for.html
http://digitalforensicsurvivalpodcast.com/2016/07/05/dfsp-020-amcache-forensics-find-evidence-of-app-execution/
https://www.dfir.training/windows/amcache/207-lifars-amcache-and-shimcache-forensics/file
Microsoft-Windows-TaskScheduler (200/201)The Microsoft-Windows-TaskScheduler log file (specifically events 200 and 201), can evidence the starting and stopping of and executable which is being run as a scheduled task.
References/Tools:
https://www.fireeye.com/blog/threat-research/2013/08/execute.html
LEGACY_* Registry KeysApplicable to Windows XP/Server 2003 only, this artifact is located in the System Registry Hive, these keys can evidence the running of executables which are installed as a service.
References/Tools:
http://windowsir.blogspot.com/2013/07/howto-determine-program-execution.html
http://journeyintoir.blogspot.com/2014/01/it-is-all-about-program-execution.html
Microsoft-Windows-Application-Experience Program-Inventory / TelemetryBoth of these system logs are related to the Application Experience and Compatibility features implemented in modern versions of Windows.
At the time of testing I find none of my desktop systems have the Inventory log populated, while the Telemetry log seems to contain useful information. I have however seen various discussion online indicating that the Inventory log is populated in Windows 10. It is likely that my disabling of all tracking and reporting functions on my personal systems and VMs may be the cause... more testing required.
References/Tools:
http://journeyintoir.blogspot.com/2014/03/exploring-program-inventory-event-log.html
Background Activity Monitor (BAM)The Background Activity Monitor (BAM) and (DAM) registry keys within the SYSTEM registry hive, however as it records them under the SID of the associated user it is user attributable. The key details the path of executable files that have been executed and last execution date/time
It was introduced to Windows 10 in 1709 (Fall Creators update).
References/Tools:
https://www.andreafortuna.org/dfir/forensic-artifacts-evidences-of-program-execution-on-windows-systems/
https://www.linkedin.com/pulse/alternative-prefetch-bam-costas-katsavounidis/
System Resource Usage Monitor (SRUM)Introduced in Windows 8, this Windows features maintains a record of all sorts of interesting information concerning applications and can be used to determine when applications were running.
References/Tools:
https://www.sans.org/summit-archives/file/summit-archive-1492184583.pdf
http://cyberforensicator.com/2017/08/06/windows-srum-forensics/
https://github.com/MarkBaggett/srum-dump
ActivitiesCache.db In Windows 10 1803 (April 2018) Update, Microsoft introduced the Timeline feature, and all forensicators did rejoice. This artifact is a goldmine for user activity analysis and the associated data is stored within an ActivitiesCache.db located within each users profile.
References/Tools:
https://cclgroupltd.com/windows-10-timeline-forensic-artefacts/
https://binaryforay.blogspot.com/2018/05/introducing-wxtcmd.html
Security Log (592/4688) Event IDs 592 (Windows XP/2003) and 4688 (everything since) are recorded within the Security log on process creation, but only if Audit Process Creation is enabled.
References/Tools:
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=592
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4688
https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/audit-process-creation
System Log (7035) Event ID 7035 within the System event log is recorded by the Service Control Manager when a Service starts or stops. As such it can be an indication of execution if the associated process is registered as a service.
References/Tools:
http://www.eventid.net/display-eventid-7035-source-Service%20Control%20Manager-eventno-1530-phase-1.htm
UserAssistWithin each users NTUSER.DAT the UserAssist key tracks execution of GUI applications.
References/Tools:
https://www.4n6k.com/2013/05/userassist-forensics-timelines.html
https://blog.didierstevens.com/programs/userassist/
https://www.nirsoft.net/utils/userassist_view.html
RecentAppsThe RecentApps key is located in the NTUSER.DAT associated with each user and contains a record of their... Recent Applications. The presence of keys associated with a particular executable evidence the fact that this user ran the executable.
References/Tools:
https://df-stream.com/2017/10/recentapps/
JumpListsImplemented in Windows 7, Jumplists are a mechanism by which Windows records and presents recent documents and applications to users. Located within individual users profiles the presence of references to executable(s) within the 'Recent\AutomaticDestinations' can be used to evidence the fact that they were run by the user.
References/Tools:
https://articles.forensicfocus.com/2012/10/30/forensic-analysis-of-windows-7-jump-lists/
https://www.blackbagtech.com/blog/2017/01/12/windows-10-jump-list-forensics/
https://ericzimmerman.github.io/#!index.md
RunMRUThe RunMRU is a list of all commands typed into the Run box on the Start menu and is recorded within the NTUSER.DAT associated with each user. Commands referencing executables can be used to determine if, how and when the executable was run and which user account was associated with running it.
References/Tools:
http://www.forensicfocus.com/a-forensic-analysis-of-the-windows-registry
http://what-when-how.com/windows-forensic-analysis/registry-analysis-windows-forensic-analysis-part-8/
AppCompatFlags Registry KeysReferences/Tools:
https://journeyintoir.blogspot.com/2013/12/revealing-program-compatibility.html
CCM_RecentlyUsedAppsReferences/Tools:
https://www.fireeye.com/blog/threat-research/2016/12/do_you_see_what_icc.html
Application Experience Program TelemetryReferences/Tools:
https://www.hecfblog.com/2018/09/daily-blog-474-application-experience.html
https://threatvector.cylance.com/en_us/home/Uncommon-Event-Log-Analysis-for-Incident-Response-and-Forensic-Investigations.html
IconCache.dbReferences/Tools:
https://www.researchgate.net/publication/263093655_Structure_and_application_of_IconCachedb_files_for_digital_forensics
Windows Error Reporting (WER)References/Tools:
https://journeyintoir.blogspot.com/2014/02/exploring-windows-error-reporting.html
Syscache.hveReferences/Tools:
https://dfir.ru/2018/12/02/the-cit-database-and-the-syscache-hive/
https://dfir.ru/2019/01/04/what-writes-to-the-syscache-hive/
https://www.hecfblog.com/search?q=syscache&max-results=20&by-date=true
AV/IDS/EDR
Various Anti-Virus, Intrusion Detection and Endpoint Detection and Response (EDR) solutions may provide evidence of program execution. It is recommended to identify and analyse any associated logs and note that some logging may be centralised.
Repeating the appeal earlier in this post, feedback, suggested additions and corrections are very welcome!Posted by Adam Harrison