Chinese hackers poke the Bayer, but German giant says it withstood attack
![]()
Pharmaceutical brand says no data lost in Winnti
outbreak
By Shaun
Nichols in San Francisco 4 Apr 2019 at 22:12
German pharmaceuticals giant Bayer says it has been hit by malware, possibly from China, but that none of its intellectual property has been accessed.
On Thursday the aspirin-flingers issued a statement confirming a report from Reuters that the Winnti malware, a spyware tool associated with Chinese hacking groups, had been detected on some of its machines.
The malware was spotted on Bayer PCs in early 2018, with the company silently monitoring its behavior for more than a year before finally pulling the plug on the operation last month and notifying authorities.
continue here
Thunderclap flaws impact how Windows, Mac, Linux handle Thunderbolt peripherals

By Catalin
Cimpanu for Zero Day | February 26, 2019 --
23:46 GMT (23:46 GMT) | Topic: Security
Windows, Mac, Linux, and FreeBSD systems are all impacted by a new vulnerability that was disclosed this week at the NDSS 2019 security conference.
The vulnerability --named Thunderclap-- affects the way Thunderbolt-based peripherals are allowed to connect and interact with these operating systems, allowing a malicious device to steal data directly from the operating system's memory, including highly sensitive information.
The research team behind this vulnerability says that "all Apple laptops and desktops produced since 2011 are vulnerable, with the exception of the 12-inch MacBook."
Similarly, "many laptops, and some desktops, designed to run Windows or Linux produced since 2016 are also affected," as long as they support Thunderbolt interfacing.
WHAT IS THUNDERBOLT?
Thunderbolt is the name of a hardware interface designed by Apple and Intel to allow the connection of external peripherals (keyboards, chargers, video projectors, network cards, etc.) to a computer.
These interfaces became wildly popular because they combined different technologies into one single cable, such as the ability to transmit DC power (for charging purposes), serial data (via PCI Express), and video output (via DisplayPort).
The technology was initially available for Apple devices but was later made available for all hardware vendors, becoming ubiquitous nowadays, especially thanks to the standard's latest version, Thunderbolt 3.
But according to the research team, all Thunderbolt versions are affected by Thunderclap. This means Thunderbolt 1 and 2 (the interface versions that use a Mini DisplayPort [MDP] connector) and Thunderbolt 3 (the one that works via USB-C ports).
Continue reading here.
The original finding was done by 
BibTeX record
@TechReport{UCAM-CL-TR-934,
author =
{Rothwell, Colin L.},
title = {{Exploitation from malicious PCI
Express peripherals}},
year = 2019,
month = feb,
url = {https://www.cl.cam.ac.uk/techreports/UCAM-CL-TR-934.pdf},
institution = {University of Cambridge, Computer Laboratory},
number = {UCAM-CL-TR-934}
}
Find the PoC on GitHUB done by carma
Windows Commands Abused by Attackers and their mitigation
Shusei Tomonaga from the JPCERT is providing us with some cool statistics of commonly used windows internal commands by attackers and shows a cool way of mitigation.
Hello again, this is Shusei Tomonaga from the Analysis Center.
In Windows OS, various commands (hereafter “Windows commands”) are installed by default. However, what is actually used by general users is just a small part of it. On the other hand, JPCERT/CC has observed that attackers intruding into a network also use Windows commands in order to collect information and/or to spread malware infection within the network. What is worth noting here is the gap between those Window commands used by general users and by attackers. If there is a huge difference, it would be possible to detect or limit the attackers’ behaviour by monitoring/controlling the Windows command execution.
Continue here.
Metasploit Framework User Agents
Florian Roth is referencing a list of known metasploit useragantes to enhance your SIEM qaccordingly.
Need to escalate privileges without fancy tools?
Just for the little fun you have on foreign systems ...
Paul Seekamp (@nullenc0de)
twitterte um 9:53 nachm. on Mo., Feb. 25, 2019:
Need to escalate privileges
without fancy tools?
open CMD
findstr /si password *.txt
findstr /si password *.xml
dir
/s pass == cred == vnc == .config
findstr
/spin "password" .
reg query HKLM /f password /t REG_SZ /s
reg
query HKCU /f password /t REG_SZ /s
(https://twitter.com/nullenc0de/status/1100136763157291009?s=09)
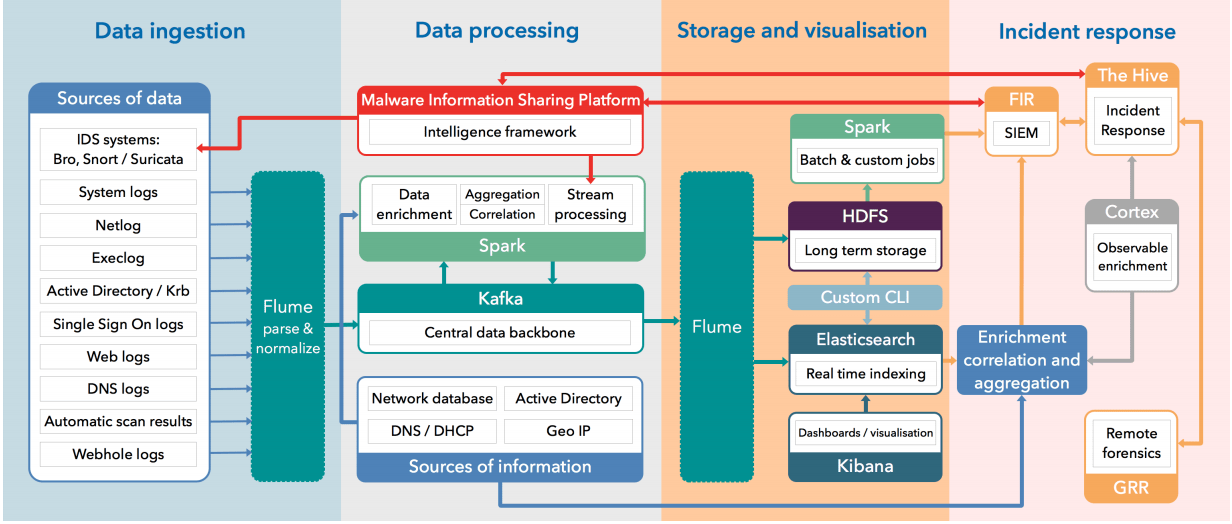
Building a large scale Intrusion Detection System
The Swiss CERN is providing us with an exellent article on how to build a large scale IDS. This is really worth reading (and building) as it does not use expensive commercial LMS.
Thanks to:
Pablo Panero
CERN, Switzerland
E-mail: pablo.panero@cern.ch
Liviu Valsan
CERN, Switzerland
E-mail: liviu.valsan@cern.ch
Vincent Brillault
CERN, Switzerland
E-mail: vincent.brillault@cern.ch
Ioan Cristian Schuszter
CERN, Switzerland
E-mail: cristian.schuszter@cern.ch
In this paper the implementation of an Intrusion Detection System (IDS) both at the Network (NIDS) and Host (HIDS) level, used at CERN, is presented. The system is currently processing in real time approximately one TB of data per day, with the final goal of coping with at least 5 TB / day. In order to accomplish this goal at first an infrastructure to collect data from sources such as system logs, web server logs and the NIDS logs has been developed making use of technologies such as Apache Flume and Apache Kafka. Once the data is collected it needs to be processed in search of malicious activity: the data is consumed by Apache Spark jobs which compare in real time this data with known signatures of malicious activities. These are known as Indicators of Compromise (IoC). They are published by many security experts and centralized in a local Malware Information Sharing Platform (MISP) instance. Nonetheless, detecting an intrusion is not enough. There is a need to understand what happened and why. In order to gain knowledge on the context of the detected intrusion the data is also enriched in real time when it is passing through the pipeline. For example, DNS resolution and IP geolocation are applied to it. A system generic enough to process any kind of data in JSON format is enriching the data in order to get additional context of what is happening and finally looking for indicators of compromise to detect possible intrusions, making use of the latest technologies in the Big Data ecosystem.
Here comes the Sun (and TheHive 3.3-RC5)
New version of TheHive has been released.
On February 10, 2019, we released TheHive 3.3-RC2. It contained new features such as bulk alert merging, alert sorting, observable tag autocompletion, exporting case tags to MISP & more. Since then your favourite French code Chefs have been beesy refining TheHive 3.3 through new release candidates while getting Cortex 3 ready for prime time.
Over the weekend, Nabil decided he was not working enough already during the week. So he drained his batteries to the very last drop to release TheHive 3.3-RC5 before he crashed headfirst into his bed for a long, reparative sleep. Cumulatively since RC2, we added several features and squashed 10 bugs as described below.
Note that release candidates are beta software. You can get TheHive 3.3-RC5 from the pre-release, beta repositories. As usual, we encourage you to test it and report any bugs or issues you spot so we can address them before the final release.
Check TheHive Installation guide for further details.
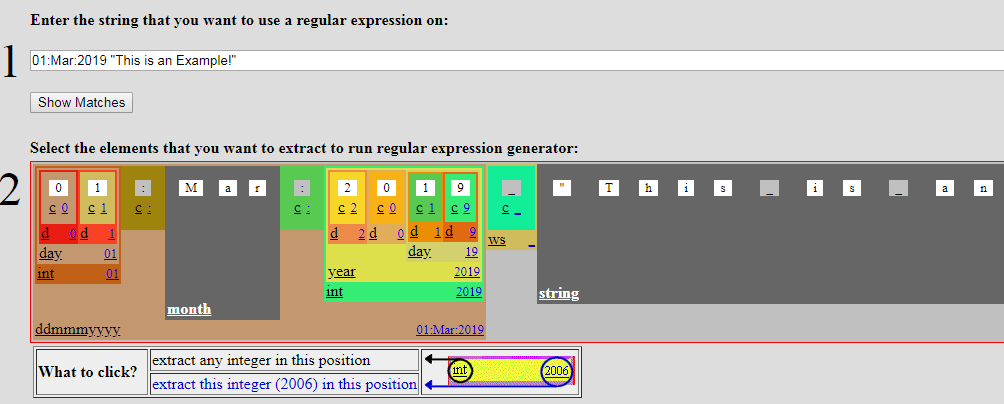
Florian Roth is giving us some cool sigme detection for acount tampering detections.
Check it out here.
| Status: | |
| - '0xC0000072' # User logon to account disabled by administrator | |
| - '0xC000006F' # User logon outside authorized hours | |
| - '0xC0000070' # User logon from unauthorized workstation | |
| - '0xC0000413' # Logon Failure: The machine you are logging onto is protected by an authentication firewall. The specified account is not allowed to authenticate to the machine | |
| - '0xC000018C' # The logon request failed because the trust relationship between the primary domain and the trusted domain failed | |
| - '0xC000015B' # The user has not been granted the requested logon type (aka logon right) at this machine |
Technical Analysis: Pacha Group Deploying Undetected Cryptojacking Campaigns on Linux Servers
Introduction
Cryptomining malware, also known as cryptojacking or cryptocurrency mining malware, refers to software developed to take over a computer’s resources and use them for cryptocurrency mining without a user’s explicit permission.
There are several reports documenting this newer malware breed and how it has become more popular in the last few years.
Antd is a miner found in the wild on September 18, 2018. Recently we discovered that the authors from Antd are actively delivering newer campaigns deploying a broad number of components, most of them completely undetected and operating within compromised third party Linux servers. Furthermore, we have observed that some of the techniques implemented by this group are unconventional, and there is an element of sophistication to them. We believe the authors behind this malware are from Chinese origin. We have labeled the undetected Linux.Antd variants, Linux.GreedyAntd and classified the threat actor as Pacha Group.
Read the intire article here.
COM XSL Transformation: Bypassing Microsoft Application Control Solutions (CVE-2018-8492)
Introduction
Greetings, Everyone! It has been several months since I’ve blogged, so it seems fitting to start the New Year off with a post about two topics that I thoroughly enjoy exploring: Application Control/Application Whitelisting (AWL) and the Component Object Model (COM). As the title suggests, I stumbled upon a technique for bypassing Microsoft Application Control solutions using COM. In a particular case, the technique executes unsigned code to bypass Windows Defender Application Control (WDAC)/Device Guard, including PowerShell Constrained Language Mode (CLM) with an Extensible Stylesheet Transformation (XSLT). In this post, we will discuss the following:
- Brief Overview of Microsoft AWL Solutions
- Brief Overview of PowerShell With Constrained Language Mode
- Walkthrough of CVE-2018-8492 (WDAC Bypass via COM XSLT)
- Defensive Considerations
Read the entire article here.
while doing some forensics ...
... using Autopsy I found out, that analysing multiple data images is not suported by the program. After a while of thinking, I found the reason lyaing in the simple-sql being used with the tool that creates a deadlock when using it in analysing multiple images.
So the solution was to setup a "multi user environment" using postgres in the background.
So I started with first setting up a central repository as this wil provide the postgresql needed for the multi user as well.
See my article of setting up a central repository here.
China: Order of the Ministry of Public Security
Did you know, that China has changed it's security law to do "security supervision" even onsite?
Chapter III Supervision and Inspection Procedures
Article XIII carry out public security organs Internet security supervision and inspection, supervision and examination can be taken on-site or remote detection manner.
Article XIV of the public security organs when conducting Internet security site supervision and inspection, the People's Police shall not be less than two, and should show people's police supervision and inspection certificate and notice above the county level people's government issued by the public security organs.
Article XV of public security organs to carry out on-site supervision and inspection of Internet security may need to take the following measures:
(1) Entering business premises, computer rooms, and workplaces;
(2) requiring the person in charge of the supervision and inspection or the network security management personnel to explain the supervision and inspection items;
(3) consulting and copying information related to Internet safety supervision and inspection items;
(4) Check the operation of technical measures for network and information security protection.
Read the complete (translated) law paper here.
Hackers KO Malta's Bank of Valletta in attempt to nick €13m

by:
By Gareth
Corfield 13 Feb 2019 at 17:38
In a statement reported by various local outlets, Maltese prime minister Joseph Muscat told parliament that the attack was detected shortly after the start of business today – and involved assailants, said to be from "overseas", trying to transfer €13m to a variety of banks spread across the UK, US, Czech Republic and Hong Kong.
The bank's website, BOV.com, is inaccessible at the time of writing. Even the domain's nameservers appear to have been wiped, judging from the results of multiple domain lookups attempted by The Register.
And some people still ask me why we need expensive (cyber)
security at all ...
I guess the amount the damage costs would have rectified
some security on the forehand.
[M.Pauli]
Distributed Denial of Secrets
Very good collection of leaks and classified
documents/information.
Tor-only connection
The Collective
We are a small group, but our reach expands far beyond just our members, not all of who are listed or ever acknowledged by their own preference. We have informally worked together for many years and have developed deep connections in the field of data gathering, research, journalism, activism and technology. In 2018, we decided to pool together our expertise and time to create a unified project representing our shared goals, and provide a platform for others to know and trust.
The modern state of “leaking” organizations has detoriorated rapidly for many years, poisoned by their own egos and interests. Our view is that data is a resource and a record - this data can never tell the whole story. We trust the public to be responsible with data, and open it to them for the rigorous examination of it. In time, the truth can always emerge.
The Team
Emma Best - @NatSecGeek
Emma is an independent journalist who has spent more years filling out FOIA’s than most people have spent reading the news. Known for her tenacity in always finding the next lead and penetrating the bureaucratic walls of government, she has a keen eye for the details in every document and is a ruthless advocate for the truth even when all others dare not dig deeper.
“Vexsome” - Federal Bureau of Investigation, 2016
“The Architect”
A pseudonym for our technical behemoth who wishes to remain anonymous. He is no stranger to controversy and has been involved in privacy and technology activism for at least 10 years. The Architect is primarily responsible for advising on the operational security of the collective and maintains web and technical operations for the group.
The Firebog: The Big Blocklist Collection
While doing some work on my PiHole project, I found a enxellent collection of block lists to choose from at TheFirebog.
Have a look yourself and choose lists that best fit your needs.
Sophos KB: Resolving outbreaks of Emotet and TrickBot malware
Sophos released a good writing about EMOTET.
The basic avoidence of EMOTET infections come to:
- Secure all of your machines
- Patch early, patch often
- Block PowerShell by default
Overview
This article is designed to help Sophos customers who have detections for the Emotet or TrickBot malware. While these two malware families are different, often networks infected with one will also have the other as well. This is primarily due to Emotet spreading across a network and additionally downloading TrickBot as it goes. These two threats are very advanced and fast moving, they also use different techniques to achieve their goals and removing both of these involves taking the same actions. In this article, we cover the basic points worth knowing about these threats, how to remove them and how to improve your security to help prevent getting infected again in the future.
The following sections are covered:
MISP OSINT Feeds
MISP includes a set of public OSINT feeds in its default configuration. The feeds can be used as a source of correlations for all of your events and attributes without the need to import them directly into your system. The MISP feed system allows for fast correlation but also a for quick comparisons of the feeds against one another.
How to have my feed published in the default MISP OSINT feed
- Fork the MISP project on GitHub.
- Update the default MISP feed to add your feed(s).
- Make a pull-request with the updated JSON file.
Paul Seekamp: Secure your printers !
Paul Seekamp is giving a quick win if your printers are configured to use ldap/AD authentication to register itself within you domain.
- Log into printer.
- Look for LDAP configured.
- Point the destination to your PC.
- netcat -l -vv -p 444
- Initiate an LDAP query.
Wait for creds!
Florian Roth: Very good SIGMA rule collection
Check out Florians SIGMA rules
collection at GitHUB of Neo23x0.
Again,
Florian is doing an exellent task in contributing to the community. Thx a
lot..!!!