ENISA: Excellent training material

Find some excellent technical training resources at the
page of the European
Union Agancy for Network and Information Security.
- Building artifact handling and analysis environment
- Processing and storing artifacts
- Artefact analysis fundamentals
- Advanced artefact handling
- Introduction to advanced artefact analysis
- Dynamic analysis of artefacts
- Static analysis of artefacts
- Forensic analysis: Local incident response
- Forensic analysis: Network incident response
- Forensic analysis: Webserver analysis
- Developing Countermeasures
- Common framework for artefact analysis
- Using indicators to enhance defence capabilities
- Identification and handling of electronic evidence
- Digital forensics
- Mobile threats incident handling
- Mobile threats incident handling (Part II)
- Proactive incident detection
- Automation in incident handling
- Introduction to network forensics New
- Honeypots
- Vulnerability handling
- Presenting, correlating and filtering various feeds
2.2 billion passwords have been leaked and published
Check HIBP to see if you are a victim. He provides checks against 6,474,028,664 pwned account including the Collection #1 sources.
Looking forward to see the new rockyou.txt "best password dictionary"
Or get you a copy of the source "Collection #1" and search offline if you
have been pwned.
"Collection #2 - #5" are already available as well, but
you'd have to dig a bit deeper.
https://pastebin.com/RyWJgaED
magnet:?xt=urn:btih:B39C603C7E18DB8262067C5926E7D5EA5D20E12E&dn=Collection%201&tr=udp%3a%2f%2ftracker.coppersurfer.tk%3a6969%2fannounce&tr=udp%3a%2f%2ftracker.leechers-paradise.org%3a6969%2fannounce&tr=http%3a%2f%2ft.nyaatracker.com%3a80%2fannounce&tr=http%3a%2f%2fopentracker.xyz%3a80%2fannounce
magnet:?xt=urn:btih:D136B1ADDE531F38311FBF43FB96FC26DF1A34CD&dn=Collection%20%232-%235%20%26%20Antipublic&tr=udp%3a%2f%2ftracker.coppersurfer.tk%3a6969%2fannounce&tr=udp%3a%2f%2ftracker.leechers-paradise.org%3a6969%2fannounce&tr=http%3a%2f%2ft.nyaatracker.com%3a80%2fannounce&tr=http%3a%2f%2fopentracker.xyz%3a80%2fannounce
tor: Transparency, Openness, and Our 2016 and 2017 Financials
The tor network was able to reduce the US government funding dramatically.
28th Januarry: European Data Protection Day
Even those who have "nothing to hide" should protect their privacy
January 28, 2019
They talk to a friend in a café. Suddenly, the waiter
asks what your phone numbers are, who your friends are and what you are talking
about. Do you provide information? Would you post the information if, in return,
you did not have to pay the bill? Do you have something to hide if you do not
respond to this trade?
Internet users who voluntarily disclose their privacy to free online services often do so, citing that they have "nothing to hide". However, this point of view is untenable. Having nothing to hide may be a desirable state of affairs, but it is fundamentally different from giving up your privacy.
Not informing the waiter does not mean that you have something to hide but that you want to preserve the privacy you deserve. You may be talking about something banal, but you simply do not think the matter concerns the waiter. In addition, you do not know what the waiter could do with the information or where his interest comes from.
Those who do not unknowingly disclose personal information to unknown persons in everyday life should certainly not do that towards online services. Combining different data sources makes it easy to draw a detailed picture of the users, which may reveal much more about them than they would like.
Today is the European Data Protection Day. Protect your privacy, e.g. With
France will engage in offensive cyber warfare
I guess this will start a controverse discussion about this way of "fighting fire with fire" philosophy....
France will engage in offensive cyber warfare
French defence secretary Florence Parly announced that France will engage in a policy of using “cyber arms as all other traditional weapons… to respond and attack" (The Register).
It's a significant statement in an area that governments have often been leery of admitting to and is likely to prompt a shift in international discussion and rhetoric on cyber warfare. Meanwhile, French diplomat Jean Heilbronn has suggested that online espionage should be treated as business as usual by international governments, much as its physical equivalent currently is.
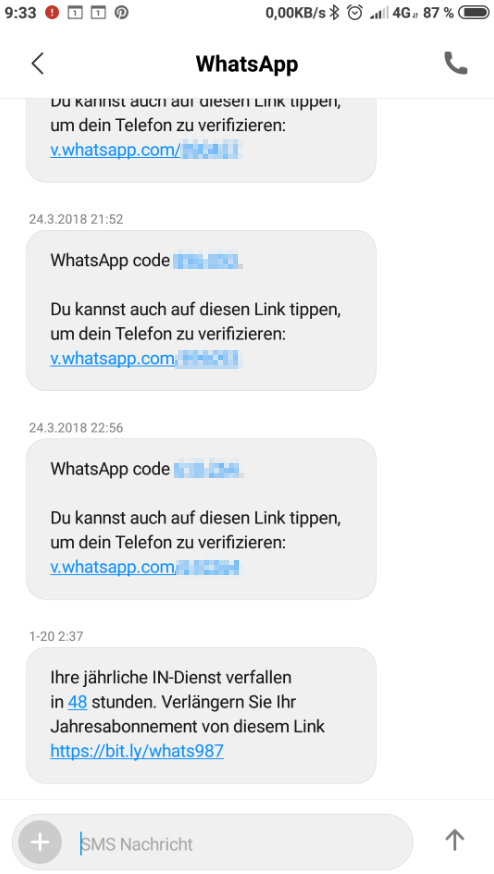
WhatApp phishing attempt from original SMS-source
A wide phishing attempt is active since the last view days. - Well this would not be worth a news, but the phishing came from the original WhatApp SMS verification number and by that looks really good.
But keep in mind, WhatApp is free and known german gramar.
BYOB (Build Your Own Botnet)
This goes to Hugo and his investigative searching for news...
malwaredllc is giving us a complete botnet client-server setup for educational purpose. So build you own botnet and find detections and mitigations in your own lab setup.
Despite of the educational aspect of such doing, sadly the bad guys abuse this action already in the wild. Everything can be used in good and bad ways. I think A. Einstein mentioned something like that.
But as the actual source is available, it will be an excellent example for security analysts to analyse the bot and create mature detectors to alert of such activity found in your network.
So thanks malwaredllc for the contribution...!!!
BAMF (Backdoor Access Machine Farmer)
If you ever wanted to use shodan like a pro and find and use exploitable routers for education, this tool of malwaredllc is your choice.
BAMF is an open-source tool designed to leverage Shodan (a search engine for the Internet of Things) to discover vulnerable routers, then utilize detected backdoors/vulnerabilities to remotely access the router administration panel and modify the DNS server settings.
Hack and Track People's Device Constantly Using TRAPE
Install:
git clone https://github.com/jofpin/trape.git
cd trape
python2 trape.py -hUse:
To see an example of what and how you could work with it now, have a read at Justins post at null-byte.
"If you want to hack the victim's device perfectly, you can make a website and make the victim redirect to your website, you can just let the victim download a payload made by Metasploit and take control completely!(There is a button for these)"
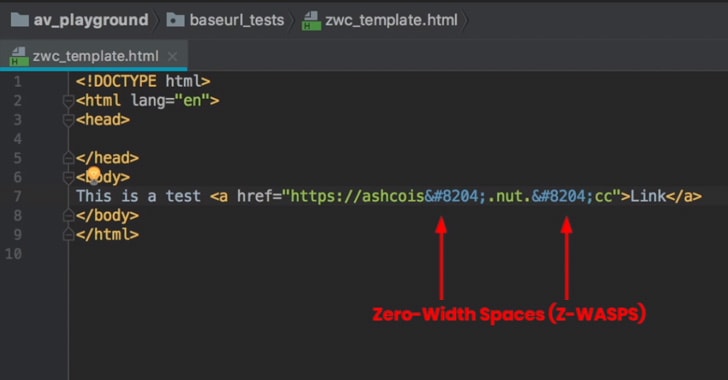
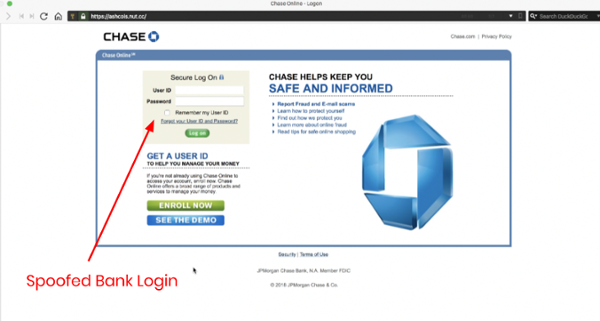
COOL: Hackers Using Zero-Width Spaces to Bypass MS Office 365 Protection
Swati Yoav Nathaniel is writing about a new way to evade URL-detaction with the Office365.
His idea is to put Zero-Width statements into the URL to trick the MS ATP-detection algorythm.
So, it's about to enhance our own detection filters with the below list to stay on top of detections.
- ​ (Zero-Width Space)
- ‌ (Zero-Width Non-Joiner)
- ‍ (Zero-Width Joiner)
-  (Zero-Width No-Break Space)
- 0 (Full-Width Digit Zero)
His poc was.
In a Z-WASP phishing attack, the Zero-Width Non-Joiner (‌) is added to the middle of a malicious URL within the RAW HTML of an email.
Microsoft email processing did not recognize this URL as a legitimate URL, and neither applied URL reputation checking nor converted it with Safe Links for post-click checking. The email was delivered to the intended recipient; but in their inbox, users did not see the ZWSPs in the URL.
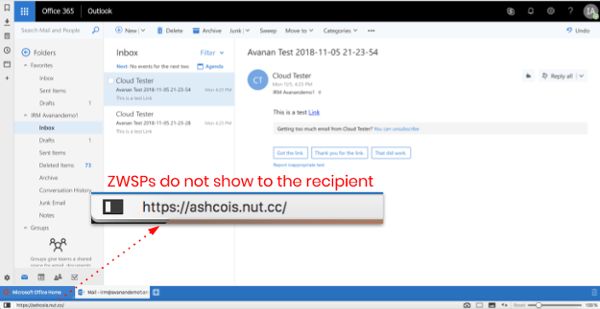
When the end-users clicked on the link in the email, they were taken to a credential harvesting phishing site. In the example below, Chase Bank was spoofed.
msoffcrypto-crack.py to decrypt MSWORD documents
Check out the new version of Didier Stevens new version of msoffcrypto-crack.py
Didier StevensMonday 31
December 2018New Tool: msoffcrypto-crack.pyFiled under: Encryption,maldoc,My Software — Didier Stevens @ 0:00
This is a new tool to recover the password of encrypted MS Office documents. I quickly put together this script to help with the analysis of encrypted, malicious documents.
This tool relies completely on Python module msoffcrypto to decrypt MS Office documents.
Since this is a Python tool based on a Python library, don’t except fast password recovery. This is more a convenience program.
It can recover passwords using a build-in password list, or you can provide your own list via option -p.
The tool can also decrypt the encrypted MS Office document if the password is recovered: used option -o to achieve this. Otherwise, the tool just displays the recovered password.
Like many of my tools, it can take its input from stdin and provide the decrypted document via stdout.
It’s developed with Python 2, and also tested on Python 3.
Read the man page for all the details: option -m.

msoffcrypto-crack_V0_0_1.zip (https)
MD5: F67060E0DE62727A1A69D0FD6F39013A
SHA256:
1466B94B56595BA0B91F0A2606F699E1D737E964F3F1A4DFDF7EAA47843DD063
Passport pictures with the help of google search
If you'd need some idea of how a foreign passport looks like, just ask Dr. Google:
intitle: "Index of /" Passport
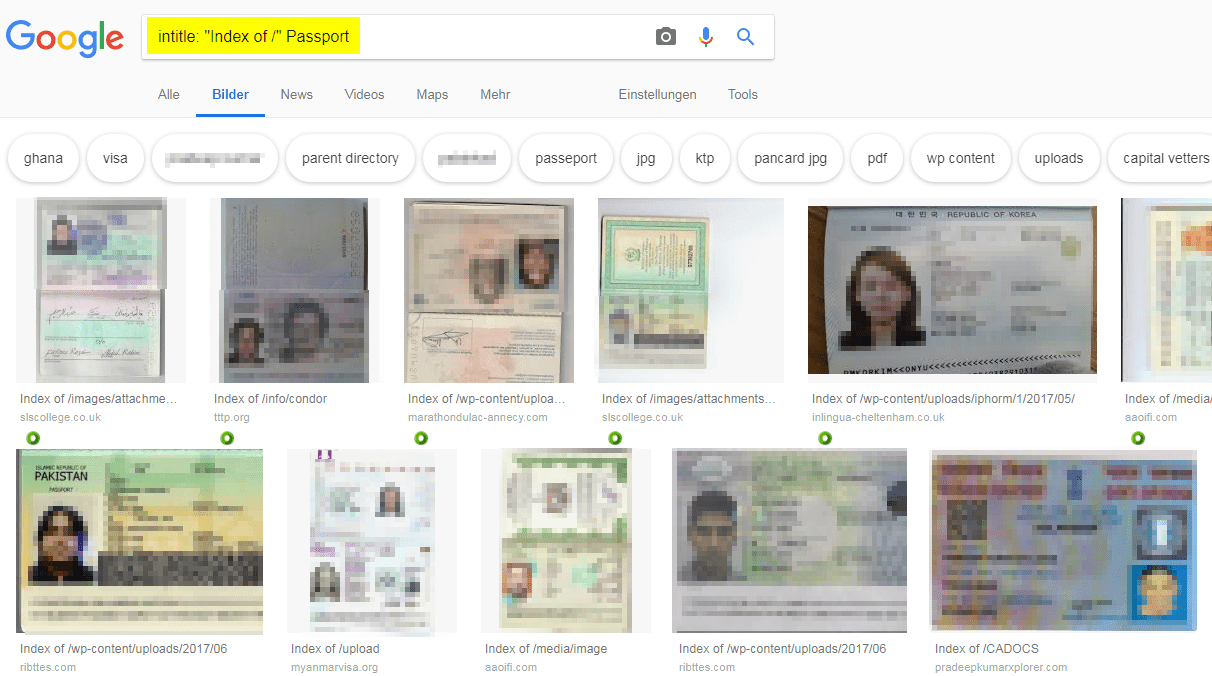
And this is not to build yourself another identitiy, this is to compare a foreign passport that is sown to you if it looks "good" or not. :-)
Metasploit Framework 5.0 Released!
![]() announced the new release of Metasploit 5.0 with
some cool additions.
announced the new release of Metasploit 5.0 with
some cool additions.
The following is a high-level overview of Metasploit 5.0’s features and capabilities.
-
Metasploit users can now run the PostgreSQL database by itself as a RESTful service, which allows for multiple Metasploit consoles and external tools to interact with it.
-
Parallel processing of the database and regular
msfconsoleoperations improves performance by offloading some bulk operations to the database service. -
A JSON-RPC API enables users to integrate Metasploit with additional tools and languages.
-
This release adds a common web service framework to expose both the database and the automation APIs; this framework supports advanced authentication and concurrent operations. Read more about how to set up and run these new services here.
-
Adds
evasionmodule type and libraries to let users generate evasive payloads without having to install external tools. Read the research underpinning evasion modules here. Rapid7’s first evasion modules are here. -
The
metashellfeature allows users to run background sessions and interact with shell sessions without needing to upgrade to a Meterpreter session. -
External modules add Metasploit support for Python and Go in addition to Ruby.
-
Any module can target multiple hosts by setting RHOSTS to a range of IPs, or by referencing a hosts file with the
file://option. Metasploit now treats RHOST and RHOSTS as identical options. -
An updated search mechanism improves Framework start time and removes database dependency.
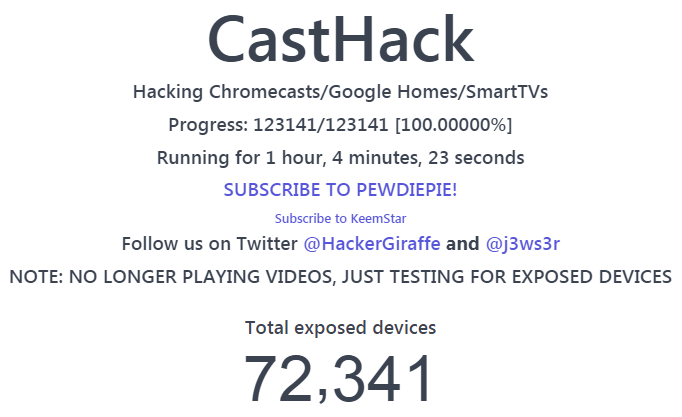
Hacking Chromecasts/Google Homes/SmartTVs
Good hacker have showed the world that Googles Chromecast is often available via the Internet due to badly configured routers allowing UPnP, by playing a youtube video at 123141 devices.
CastHack gives a cool overview of how far they are:
The increased use of powershell in attacks
Having found a very good document writen by Symantec I created a summary of the (in my opinion) most important topics on a extra page of my site here.
Some OSINT hints for #btleaks
To see how I did a "quick catch" on the BTLEAK files, have a look at my documentation of how I found the data and links although the major information was hidden and blocked.
Twitter leak or #BTLEAK
During the end of 2018, just bevore christmas, the germany partys have got a fancy gift from santa via some tweets, promissing valuable information of several prominent politicians of the german parliament.
Although twitter, google and other bigger institutions tried their best to hide the actual information, but the network is designed to overcome an atomic desaster, so hiding is hard within an environment that never forgets.
By the time of writing, I was still able to use some caches and crawler to get me the actual information and follow the several URL's (669) within the head documents.
I'm still busy with reading and evaluating the information so far, but from the first and second sight, it looks not like the very, very finest information. But, it shows how unprofessional and childish polititians use their data.
Never the less of the quality of the information itself, it is an fantastic source of information for trust relationsships that can be used in phishing and are excellent for social engineering. I*m sure further attacks from turla etc. will use it as a valuable tool.
ALEXA: Bit**, stop sharing my intimities
Amazon reveals private Alexa voice data files
Heise News is reporting (upon others) about a data leak at Amazon while they
shared intime recordings to a foreign user. Upon that, it's a prove that Alexa
is recording what every "she" get to hear.
Well, we all knew it already that
this is just a eavesdropping bug, but now it's proven by Amazon itself.
But read the original articel of heise News here.
[Update of heise News]
Today, Amazon sent us an upgraded statement on the case. The company stressed that it was an "isolated incident" and that contact had been established with the relevant authorities, quote: “This was an unfortunate case of human error and an isolated incident. We have resolved the issue with the two customers involved and have taken steps to further improve our processes. We were also in touch on a precautionary basis with the relevant regulatory authorities.”
Read the full article with all the details (English, PDF, 644 KByte)
0xffff0800: Excellent malware sample repository
@0xffff0800 was so kind to provide the community with a comprehensive collection of malware samples for analysis and sandboxing fun. I personally use many of them as a test for my Cuckoo.
If you'd like taking things apart, choose any of the samples and try your best. But be aware of the danger that "playing with fire" has. :-)
Fürstenfeldbruck: Malware completely paralyzes hospital IT
Heise
News is reporting, that the very large hospital in Fürstenfeldburck (close
to Munich) had to work without any IT for at least a week.
From my
personal experience I know, that even other hospitals suffer from being more or
less completly blank on cyber security as the clinical administration sees no
revenue in investing into the cyber security. - Well, let the bad guys hit them
to make the administration aware, that spending small money to prevent is much
better then spending a massive amount to fix.
Translation of the original article from heise by Martin Holland:
The clinical center Fürstenfeldbruck in Bavaria has been without a computer for a week, apparently after a received by mail Trojan infected the IT systems. The reports the Munich Mercury, citing the person in charge of the hospital in the county seat west of Munich. Almost all of the existing 450 computers are still under review and the affairs of the house are largely done without IT support. Only in the coming days should all devices work again.
Ambulance diverted
According to the report, the hospital's first
computer failed last Thursday, presumably "after an e-mail attachment was opened
with malware hidden". After that, more and more departments reported problems
and more and more computers were no longer functional. The hospital was then
deregistered by the Integrated Rescue Center, so that emergency patients would
now be brought to other hospitals.
Patients were never at risk, it is said. Life-threatening cases, for example, would continue to be treated, stressed the head of the clinic. Anyone who appears in person in the clinic will also be treated. Other patients would be taken to hospitals in Munich, Dachau, Starnberg and Landsberg am Lech.
After external experts were called in last weekend, they are currently believed to have become victims of a variant of the rampant malware Emotet. The software, which specializes in password theft and online banking scams, is currently being distributed in deceptively real-looking invoices via e-mail. Attached is a doc file that tries to infect the system with malware. For this reason, the Fürstenfeldbruck Clinic has had all bank accounts blocked in order to curb financial damage. The central office Cybercrime Bavaria has started investigating the malware.