René Feingruber "Pentesters Windows NTFS tricks collection
SEC Consult is publishing an excelent blog article on how to do some NTFS tricks to gain your goals.
TRICK 1: CREATE FOLDERS WITHOUT PERMISSIONS (CVE-2018-1036/NTFS
EOP)
TRICK 2: BYPASS PATH RESTRICTIONS WITH ALTERNATE DATA
STREAMS
TRICK 3: CREATE FILES WHICH CAN’T BE FOUND BY USING
THE “…” FOLDER
TRICK 4: “HIDE” THE DESTINATION OF A
DIRECTORY JUNCTION
TRICK 5: HIDE ALTERNATE DATA
STREAMS
TRICK 6: HIDING THE PROCESS
BINARY
REFERENCES:
German Secret Service should also be allowed to search online in domestic Germany

Golem.de
(Moritz Tremmel) is reporting about a new law proposal that shall allow the
german secret service (BND) to be allowed to monitor and "hack" within
Germany.
As the german law had only foreseen the BNDs activity on outside of
Germany to protect the country of outside threats, changing this to inside the
contrys activitys as well is a major change to my point of view. Especially as
Germany had some historical reasons of limiting the secret service activity. -
We should all remember what happend during the 2nd world war times and during
the german democratic replic by germans spying on germans.
Although I
have great trust in the germans legislative to create controls on such new
duties of the BND, it still makes me think ...
The Social Democratic Party (SPD) already stated out that she will NOT support such action. - So vote wise
New Max Planck Institute for Cybersecurity and Privacy in Bochum
Translated from the German article:
Another decisive step has been taken in founding the Max Planck Institute for Cybersecurity and Privacy in North Rhine-Westphalia: The Joint Science Conference today (3 May 2019) approved the plans to set up the institute in Bochum.
Minister President Armin Laschet: "The decision in favor of Bochum is another award for the excellent research landscape in North Rhine-Westphalia: with the Horst Görtz Institute, the Universities of Bochum and Dortmund, a large number of innovative companies in the IT industry and a high-quality startup Scene, the region has become a renowned hotspot for IT security. The planned new institute will benefit from this with its research on key issues of the future. Bochum and the Ruhr Metropolis provide the ideal environment to explore the key cybersecurity technologies. We want to further expand and network innovative cutting-edge research 'Made in North Rhine-Westphalia'. "
"The scientific expertise available at the Bochum site creates excellent cooperation opportunities for cutting-edge research at this new Max Planck Institute," said Isabel Pfeiffer-Poensgen, Minister for Culture and Science. "The state government is committed to creating the best possible starting conditions for the new institute. The aim is to establish a center of excellence for basic research and training of young scientists in the field of cyber security and privacy. "
The focus of the new Max Planck Institute (MPI) will be on top-level, state-of-the-art research on cyber security, cryptography, IT system security and on legal, economic and social aspects of security and privacy. It aims to cover the entire spectrum from theory to data-driven to empirical research, and to network closely with external researchers in the fields of computer science, physics, mathematics, social sciences, economics and law.
As early as November 2018, the Senate of the Max Planck Society had called for the founding of a new Max Planck Institute for Cybersecurity and Privacy at the Bochum location. The next step towards founding is the special financing of a new building.
The Max Planck Society decided on the location of the new institute in Bochum in a location finding process encompassing several possible locations. The institute will eventually have six departments and twelve Max Planck research groups and an annual operating budget of around 20 million euros.
souvereign Runet
 (www.rbc.ru) of the Russian Federation and the end:
what risks does the project on sovereign Runet bear
(www.rbc.ru) of the Russian Federation and the end:
what risks does the project on sovereign Runet bear
Rusia will have it's "own" Internet for Russia-internal internet communication. Not to control traffic or content of the rusians, but to ensure their internal communication works even in case of global Internet outages and stay safe of outside threat.

The State Duma submitted a bill aimed at
strengthening the sovereignty of the Runet. Why the document can reduce the
quality of Internet access in Russia and lead to a restriction of the freedoms
of users, understood RBC
The main
provisions of the bill
Internet providers will have to “ensure installation” in their networks
of technical means for countering threats. These funds (which are not explained
in the document) should be provided to them by Roskomnadzor free of charge. In
cases of threats to the integrity, stability and security of the functioning of
the Internet of general use, the service may exercise centralized network
management in a manner determined by the government. As specified by RBC
Klishas, the procedure, terms and technical conditions for the installation of
technical equipment, as well as the requirements for communication networks when
using such technical equipment will be established in a sub-legal act of
Roskomnadzor.
Even if there is no threat to the Runet, Roskomnadzor will
block resources prohibited in Russia through the installed equipment. Now
providers are doing it themselves.
The system of organizing the exchange
of traffic on the territory of the country is changing completely - it must pass
only through exchange points entered in a special register (the principle of its
formation is not specified) and according to certain rules of Roskomnadzor
(which is not specified).
Introduces the ability to deny service
providers and organizers of information dissemination on the Internet (ORI,
these include instant messengers, social networks, e-mail services, etc.) to
connect to traffic exchange points. The refusal will follow if the operators do
not comply with the requirements of Roskomnadzor or law enforcement officers
(which ones - not specified).
Owners of communication lines that connect
Russia with other countries; telecom operators; Individuals with an autonomous
system number (combines groups of IP addresses so that the service provider can
build a route for traffic); owners of traffic exchange points will be required
to participate in the exercise. The position of the exercise will be set by the
Russian government.
It is proposed to create a national system for
obtaining information on domain names and network addresses, a registry that
will duplicate the list of domain names and autonomous system numbers delegated
to Russian users.
(translated via Google from
rusian)
https://www.rbc.ru/technology_and_media/15/12/2018/5c13ccfc9a7947693d157b5e
Find suspicious phshing domains
This add-on for Splunk can be used to monitor certificate transparency
logs.
For example to watch certificates issued for your domains or malicious
look-a-likes.
It outputs the certificate logs as CIM compliant events in
Splunk. This allows you to create an alert in Splunk or Splunk Enterprise
Security that fires when a certificate gets issued for
your-domain-suspicious-fishing-domain dot tld.
So you can create a wildcard
watchlist for your personally owned domains to see if some registration of SSL
certificates of equal domains are seen by Google.
But....
In addition, I found x0rz/phishing_catcher at GITHUB
who does even a bit more in terms of finding *all* suspicious domains google
sees.
It outputs a suspicious_domains.log that can be
imported and correlated directly into Splunk.
Taking this and inputlookup it against your e.g. proxylogs gives you even more in terms of identifying potential fraud going on.
inputs.conf
[monitor:///opt/phishing_catcher/suspicious_domains.log]
disabled
= false
sourcetype = phishing_domain
probs.conf
[phishing_domain]
DATETIME_CONFIG =
CURRENT
LINE_BREAKER = ([\r\n]+)
NO_BINARY_CHECK =
true
SHOULD_LINEMERGE = false
category = Application
disabled =
false
pulldown_type = true
REPORT-domain = REPORT-domain
transforms.conf
[REPORT-domain]
DELIMS = "$"
FIELDS
= "domain"
sourcetype=phishing_domain | timechart count(domain) AS "suspicious domain"
span=5m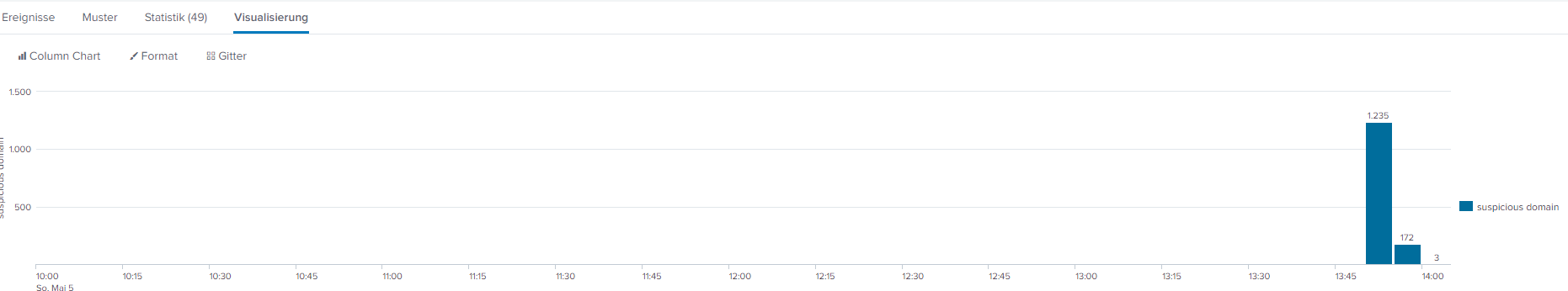
DSA-2019-051: Dell SupportAssist Client Multiple Vulnerabilities
Dells "SupportAssist" client not only helps DELL but also the bad guys..!!!
Affected products:
Dell SupportAssist Client versions prior to 3.2.0.90.
Summary:
Dell SupportAssist Client has been updated to address multiple vulnerabilities which may be potentially exploited to compromise the system.
Details:
Improper Origin Validation (CVE-2019-3718)
Dell SupportAssist Client versions prior to 3.2.0.90 contain an improper origin validation vulnerability. An unauthenticated remote attacker could potentially exploit this vulnerability to attempt CSRF attacks on users of the impacted systems.
CVSSv3 Base Score: 7.6 (AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:H)
Remote Code Execution Vulnerability (CVE-2019-3719)
Dell SupportAssist Client versions prior to 3.2.0.90 contain a remote code execution vulnerability. An unauthenticated attacker, sharing the network access layer with the vulnerable system, can compromise the vulnerable system by tricking a victim user into downloading and executing arbitrary executables via SupportAssist client from attacker hosted sites.
CVSSv3 Base Score: 7.1 (AV:A/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H)
Resolution:
The following Dell SupportAssist Client release contains resolutions to these vulnerabilities:
- Dell SupportAssist Client version 3.2.0.90 and later.
Dell recommends all customers upgrade at the earliest opportunity.
Link to remedies:
Customers can download software from https://downloads.dell.com/serviceability/Catalog/SupportAssistInstaller.exe.
Credit:
Dell would like to thank John C. Hennessy-ReCar for reporting CVE-2019-3718 and Bill Demirkapi for reporting CVE-2019-3719.
New Exploits for Unsecure SAP Systems
Alert (AA19-122A)
New Exploits
for Unsecure SAP Systems
Original release date: May 02,
2019 | Last revised: May 03, 2019
Although SAP systems should never ever been exposed directly to the internet as they host a massive amount of sensible data, there have been now defined a lot of vulnerabilities due to false configurations. Thanks to OPCDE (Dmitry Chastuhin and Mathieu Geli and their gatherings. When ever you are doing a SAP-pentest, you MUST this first.
Summary
The Cybersecurity and Infrastructure Security Agency (CISA) is issuing this activity alert in response to recently disclosed exploits that target unsecure configurations of SAP components. [1]
Risk
Vulnerable SAP applications can be compromised by a remote unauthenticated attacker having only network access to the system (without the need for a valid SAP user ID and password). Attackers can obtain unrestricted access to SAP systems, enabling them to compromise the platform along with all of its information, modify or extract this information or shut the system down. Order-to-Cash, Procure-to-Pay, Inventory Management, Treasury, Tax, HR & Payroll, and any other business process handled by SAP can be controlled, affecting the integrity of business information used to build the financial statements.
A person abusing this vulnerability would be able to perform critical business transactions including but not limited to:
- Creating fake vendors
- Creating fake employees
- Creating/modifying purchase orders
- Changing bank accounts
- Paying any vendor or employee
- Releasing shipments
- Changing inventory data
- Generating corrupted management reports
- Bypassing automatic business controls
A person performing any kind of fraud would be able to delete any traces or records that prove his or her actions and an action of this kind may not be detected.
A presentation at the April 2019 Operation for Community Development and Empowerment (OPCDE) cybersecurity conference describes SAP systems with unsecure configurations exposed to the internet. Typically, SAP systems are not intended to be exposed to the internet as it is an untrusted network. Malicious cyber actors can attack and compromise these unsecure systems with publicly available exploit tools, termed “10KBLAZE.” The presentation details the new exploit tools and reports on systems exposed to the internet.
SAP Gateway ACL
The SAP Gateway allows non-SAP applications to communicate with SAP applications. If SAP Gateway access control lists (ACLs) are not configured properly (e.g., gw/acl_mode = 0), anonymous users can run operating system (OS) commands.[2] According to the OPCDE presentation, about 900 U.S. internet-facing systems were detected in this vulnerable condition.
SAP Router secinfo
The SAP router is a program that helps connect SAP systems with external
networks. The default secinfo configuration for a SAP
Gateway allows any internal host to run OS commands anonymously. If an attacker
can access a misconfigured SAP router, the router can act as an internal host
and proxy the attacker’s requests, which may result in remote code
execution.
According to the OPCDE presentation, 1,181 SAP routers were exposed to the internet. It is unclear if the exposed systems were confirmed to be vulnerable or were simply running the SAP router service.
SAP Message Server
SAP Message Servers act as brokers between Application Servers (AS). By default, Message Servers listen on a port 39XX and have no authentication. If an attacker can access a Message Server, they can redirect and/or execute legitimate man-in-the-middle (MITM) requests, thereby gaining credentials. Those credentials can be used to execute code or operations on AS servers (assuming the attacker can reach them). According to the OPCDE presentation, there are 693 Message Servers exposed to the internet in the United States. The Message Server ACL must be protected by the customer in all releases.
Signature
CISA worked with security researchers from Onapsis Inc.[3] to develop the following Snort signature that can be used to detect the exploits:
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"10KBLAZE SAP Exploit execute attempt"; flow:established,to_server; content:"|06 cb 03|"; offset:4; depth:3; content:"SAPXPG_START_XPG"; nocase; distance:0; fast_pattern; content:"37D581E3889AF16DA00A000C290099D0001"; nocase; distance:0; content:"extprog"; nocase; distance:0; sid:1; rev:1;)
CISA recommends administrators of SAP systems implement the following to mitigate the vulnerabilities included in the OPCDE presentation:
- Ensure a secure configuration of their SAP landscape.
- Restrict access to SAP Message Server.
- Review SAP Notes 1408081 and 821875. Restrict authorized hosts via ACL
files on Gateways
(
gw/acl_modeandsecinfo) and Message Servers (ms/acl_info).[4], [5] - Review SAP Note 1421005. Split MS
internal/public:
rdisp/msserv=0 rdisp/msserv_internal=39NN. [6] - Restrict access to Message Server internal port (
tcp/39NN) to clients or the internet. - Enable Secure Network Communications (SNC) for clients.
- Review SAP Notes 1408081 and 821875. Restrict authorized hosts via ACL
files on Gateways
(
- Scan for exposed SAP components.
- Ensure that SAP components are not exposed to the internet.
- Remove or secure any exposed SAP components.
- [1] Comae Technologies: Operation for Community Development and Empowerment (OPCDE) Cybersecurity Conference Materials
- [2] SAP: Gateway Access Control Lists
- [3] Onapsis Inc. website
- [4] SAP Note 1408081
- [5] SAP Note 821875
- [6] SAP Note 1421005
- The onapsis Threat Report
- May 2, 2019: Initial version
Enhance Autopsy with ClamAV MD5s

I
had some quick win for doing forensics with Autopsy 4.0 and thought to write it
down.
Work on eliminating MS Telemetry services
Although the "deadly man-flu" keeps me off my desk, I could not resist to do at least some fevered work on this hot topic.
VirusTotal for investigators workshop
During the Kaspersky SAS 2019, VT had a workshop entitled "Virus Total for Investigators". For all those who could not attend personally, the slides are available for download.
The slides will amphasise the reader on:
- How to use VirusTotal Graph to visualize malware campaigns.
- How to use VirusTotal Intelligence to identify interesting malware metadata.
- How to use Yara for proactive and retroactive visibility.
trimstray: Search engines for Hackers:
Some of you guys might already know, some might be new….
Search engines for Hackers:
https://censys.io/
https://www.shodan.io/
https://viz.greynoise.io/table
https://www.zoomeye.org/
https://wigle.net/
https://publicwww.com/
https://hunter.io/
https://haveibeenpwned.com/
https://pipl.com/
https://osintframework.com/
And some more I found:
http://fofa.so
http://app.binaryedge.io
http://onyphe.io
http://hackle.dev
http://nerdydata.com
http://thingful.net
http://reposify.com
http://netdb.io
http://weleakinfo.com
Pastbein:
https://www.threatcrowd.org/
https://fofa.so/
https://hackle.dev/
https://tineye.com/
https://nerdydata.com/
https://searchcode.com/
https://searchisback.com/
https://crt.sh/
https://censys.io/
https://www.shodan.io/
https://viz.greynoise.io/table
https://www.zoomeye.org/
https://wigle.net/
https://publicwww.com/
https://hunter.io/
https://haveibeenpwned.com/
https://searx.me/
https://pipl.com/
https://osintframework.com/
https://buckets.grayhatwarfare.com/
https://cxsecurity.com/
https://leakedsource.ru/
https://ghostproject.fr/m
https://www.onyphe.io/
http://urlquery.net/
http://protoxin.net/s3/
http://fotoforensics.com/
http://www.errorlevelanalysis.com/
http://www.insecam.org/
https://totalhash.cymru.com
https://hosts-file.net
http://vurldissect.co.uk/
https://networking.ringofsaturn.com/
https://www.networktotal.com/search.html
https://www.packettotal.com/
https://www.exploit-db.com/
https://psbdmp.ws/
https://paper.seebug.org/
http://code.woboq.org/
https://metacpan.org/
https://totalhash.cymru.com/
http://cybercrime-tracker.net/
http://malc0de.com/database/
https://sploitus.com/
http://atm.cybercrime-tracker.net/
https://www.maltiverse.com/search
https://urlscan.io/
https://www.wolfram.com/
https://www.inteltechniques.com/menu.html
https://search.weleakinfo.com/
http://databases.today/search.php
https://findsubdomains.com/
https://dns.coffee/
https://dnsdumpster.com/
http://intelx.io
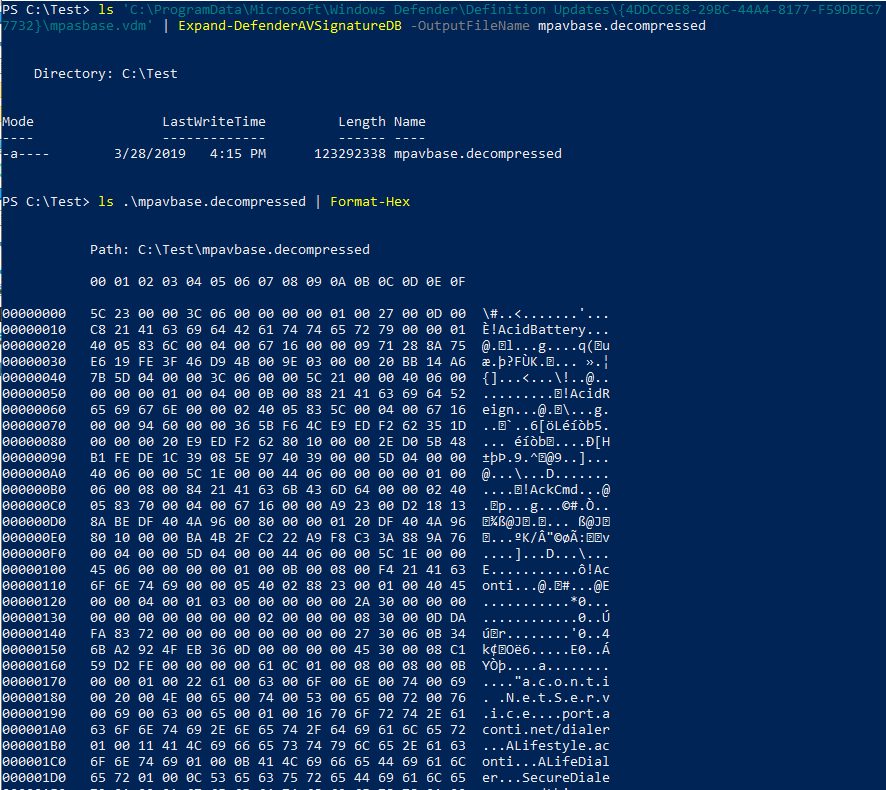
Matt Graeber: decompress WDAV .vdm files
Ever wanted to better understand how Windows Defender implements its
signatures? Here's a first step. I wrote a thing to decompress WDAV .vdm files.
https://gist.github.com/mattifestation
Emad Shanab: Red Team, tips,tools,methods,and more:
Red Team, tips,tools,methods,and more:
https://t.co/rwMhVbtBAi
https://t.co/AugskePbOh
https://t.co/kBZsy9uwg4
https://t.co/2cA2r3WbVz
https://t.co/O0mfRu3Myh
https://t.co/M7f3GfOyYh
https://t.co/8mGmRDtCTt
https://t.co/VZPjBOpnG5
https://t.co/Dt5rjPKrDo
https://t.co/5nfJu6MoGIhttps://t.co/YuPSvASXGL
Complete Mandiant Offensive VM, the first full Windows-based penetration testing virtual machine distribution
For penetration testers looking for a stable and supported Linux testing platform, the industry agrees that Kali is the go-to platform. However, if you’d prefer to use Windows as an operating system, you may have noticed that a worthy platform didn’t exist. As security researchers, every one of us has probably spent hours customizing a Windows working environment at least once and we all use the same tools, utilities, and techniques during customer engagements. Therefore, maintaining a custom environment while keeping all our tool sets up-to-date can be a monotonous chore for all. Recognizing that, we have created a Windows distribution focused on supporting penetration testers and red teamers.
Born from our popular FLARE VM that focuses on reverse engineering and malware analysis, the Complete Mandiant Offensive VM (“Commando VM”) comes with automated scripts to help each of you build your own penetration testing environment and ease the process of VM provisioning and deployment. This blog post aims to discuss the features of Commando VM, installation instructions, and an example use case of the platform. Head over to the Github to find Commando VM.
Radare 3.4.0 - Codename: "hufflepuff" released
radare released this 9 days ago · 70 commits to master since this release
Release Notes
Version: 3.4.0
From: 3.3.0
To: 3.4.0
Commits: 349
Contributors:
47
Striker - Offensive Information And Vulnerability Scanner
Striker is an offensive information and vulnerability scanner.
Features
Just supply a domain name to Striker and it will
automatically do the following for you:
- Check and Bypass Cloudflare
- Retrieve Server and Powered by Headers
- Fingerprint the operating system of Web Server
- Detect CMS (197+ CMSs are supported)
- Launch WPScan if target is using Wordpress
- Retrieve robots.txt
- Check if the target is a honeypot
- Port Scan with banner grabbing
- Dumps all kind of DNS records
- Generate a map for visualizing the attack surface
- Gather Emails related to the target
- Find websites hosted on the same web server
- Find hosts using google
- Crawl the website for URLs having parameters
- SQLi scan using online implemention of SQLMap (takes < 3 min.)
- Basic XSS scanning
VOOKI - Web Application Vulnerability Scanner
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities. Vooki includes Web Application Scanner, Rest API Scanner, and reporting section.
Vooki – Web Application Scanner can help you to find the following attacks
- Sql Injection
- Command Injection
- Header Injection
- Cross site scripting – reflected,
- Cross site scripting – stored
- Cross site scripting – dom based
- Missing security headers
- Malicious JS script execution
- Using components with known vulnerabilities
- Jquery Vulnerabilites
- Angularjs Vulnerabilites
- Bootstrap Vulnerabilities
- Sensitive Information disclosure in response headers
- Sensitive Information disclosure in error messages
- Missing Server Side Validation
- Javascript Dyanamic Code Execution
- Sensitive Data Exposure
Osmedeus - Fully Automated Offensive Security Tool For Reconnaissance And
Osmedeus allow you automated run the collection of awesome tools to reconnaissance and vulnerability scanning against the target.
Features
Subdomain Scan.
- Subdomain TakeOver Scan.
- Screenshot the target.
- Basic recon like Whois, Dig info.
- IP Discovery.
- CORS Scan.
- SSL Scan.
- Headers Scan.
- Port Scan.
- Vulnerable Scan.
- Seperate workspaces to store all scan output and details logging.
- REST API.
- SPA Web UI.
- Slack notifications.
Installation
git clone https://github.com/j3ssie/Osmedeus
cd Osmedeus
./install.sh
DDoS Added Syrian Censorship logs to
2019/04/04- Added Syrian Censorship logs to MENA
- Added Popov alleged-Ukraine General Prosecutor offices release to State Sponsored
- Added Popov alleged-CEIEC release to State Sponsored
- Added Popov files to Researchers
- Added Pfeiffer Nuclear Weapon and National Security Archive to Researchers
- Added Identity Evropa Discord logs to to North America/United States of America