First-ever malware strain spotted abusing new DoH (DNS over HTTPS) protocol
Tat is the cool thing about a job within the cyber security. One hole is closed, another one opens up…. :-)
Read the complete article by Catalin Cimpanu for Zero Day published at ZDNet about the abusing "Godlua", a Linux DDos bot that uses DoH to hide its activity within the DNS traffic.
heisec Emailcheck
![]() is providing some simple dummy emotet mailchecks
to be send to your mailaccount for testing your security equipment from there
servers.
is providing some simple dummy emotet mailchecks
to be send to your mailaccount for testing your security equipment from there
servers.
In view of the existential threat of Emotet & Co., more and more companies regulate the reception of office files via e-mail. Some lock their reception completely; often, at a minimum, Office documents that contain macros are quarantined as a precaution, or at least marked as "potentially dangerous" to warn employees. Emotet reloads additional modules via such macro functions, which infect the computer sustainably and then drive its mischief through the entire network. With the email check from heise Security you can now send harmless test emails to test your own filters.
Upgrade Confluence NOW
As per Atlassians advisory, you should upgrade your onprem installation of confluence rather today than tomorrow.
As per Alert
Logic:
Exploit code for a new vulnerability in Confluence (CVE-2019-3396) has been rapidly deployed by attackers and successfully used to breach hosts. We have observed attempts by these campaigns to execute Gandcrab ransomware on the victim hosts via PowerShell and usage of standard toolsets to avoid detection. Readers are encouraged to assess and patch their environments for this vulnerability as soon as possible.
Proof of concept code for the vulnerability was made available in the public domain on the April 10 and by the next day we were observing the first weaponized attack attempts using this new vector. This emphasizes yet again the critical nature of patching as a core component of your security protection. Don’t wait until exploit code appears in the public domain, or you are reading this blog, to react. By then it might well be too late.
Fidelis - Deception Training
I've attended a training at Fidelis in Prague to get on top of their deception solution.
Really cool stuf I'm looking forward in deploying at some customers.
- Lure attackers with breadcrumbs on real assets to decoys and services to divert and defend
- Invoke fake users within Active Directory showing activity on decoys within deception layers
- Detect external attacks and insiders to expose reconnaissance and lateral movement
- Learn details of attack paths, resource interests and initial compromised foothold systems
CyCON 2019
I had the honor, pleasure and joy to participate at the CyCON 2019 of the @ccdcoe 28.05. - 31.05.2019 in
Tallinn/Estonia.
Below are my notes of the conference to manifest the facts
for my personal memory.
The big question that was heavily discussed throughout the days "What
situation legalizes countermeasures in an cyber attack"
As there have been
politics, military, tecky's and law sciences, this was a more the thrilling and
fascinating discussion.
French gas stations robbed after forgetting to change gas pump PINs

By Catalin
Cimpanu for Zero Day | March 27, 2019
French authorities have arrested five men who stole over 120,000 litres (26,400 gallons) of fuel from gas stations around Paris by unlocking gas pumps using a special remote.
The five-man team operated with the help of a special remote they bought online and which could unlock a particular brand of gas pumps installed at Total gas stations.
The hack was possible because some gas station managers didn't change the gas pump's default lock code from the standard 0000. Hackers would use this simple PIN code to reset fuel prices and remove any fill-up limits.
Crooks would operate in small teams of two to three individuals who visited gas stations at night using two vehicles.
A man in a first car would use the remote to unlock the gas station, and then a second car, usually a van, would come along seconds later to fill a giant tanker installed in the back of the vehicle with as much as 2,000 or 3,000 litres in one go.
The group advertised the fuel they stole on social media, providing a time and place where customers could come and refuel their vehicles or pick up orders for gasoline and diesel at smaller prices.
Their scheme was uncovered in April 2018, when police arrested a suspect in Sagy, a Paris suburb. The suspect was in the possession of a remote at the time of his arrest. Five men, part of the same gang, were arrested on Monday, according to Le Parisien, who first reported the scheme last November.
Win back some privacy with a cone of silence for your smart speaker

A cool HACKDAY
post by Dan Maloney after
my collegue brought up an related posting doing the same with Arduino.
:-)
To quote the greatest philosopher of the 20th century: “The future ain’t what it used to be.” Take personal assistants such as Amazon Echo and Google Home. When first predicted by sci-fi writers, the idea of instant access to the sum total of human knowledge with a few utterances seemed like a no-brainer; who wouldn’t want that? But now that such things are a reality, having something listening to you all the time and potentially reporting everything it hears back to some faceless corporate monolith is unnerving, to say the least.
There’s a fix for that, though, with this cone of silence for your smart speaker. Dubbed “Project Alias” by [BjørnKarmann], the device consists of a Raspberry Pi with a couple of microphones and speakers inside a 3D-printed case. The Pi is programmed to emit white noise from its speakers directly into the microphones of the Echo or Home over which it sits, masking out the sounds in the room while simultaneously listening for a hot-word. It then mutes the white noise, plays a clip of either “Hey Google” or “Alexa” to wake the device up, and then business proceeds as usual. The bonus here is that the hot-word is customizable, so that in addition to winning back a measure of privacy, all the [Alexas] in your life can get their names back too. The video below shows people interacting with devices named [Doris], [Marvin], [Petey], and for some reason, [Milkshake].
We really like this idea, and the fact that no modifications are needed to the smart speaker is pretty slick, as is the fact that with a few simple changes to the code and the print files it can be used with any smart speaker. And some degree of privacy from the AI that we know is always listening through these things is no small comfort either.
Posted in Raspberry Pi, Security Hacks
Malicious applications in circulation! (GanCrab 5.2)

by Hannah Kreyenberg | May 8,
2019 | Security Informationen
Original post in German translatet via google translate and put in
italcs
Disguised as a professionally designed application mail with an encrypted attachment, an unidentified virus is spreading. This is reported by the Hornetsecurity Security Lab.
Look for emails with the subject "Apply for your job advertisement" or "Apply for the current job advertisement" and an attachment that is encrypted. To open the document, a password will be included in the cover letter of the e-mail. Through the encrypted .pdf, .doc or zip file, cyber criminals try to circumvent local virus scanners because the contained malicious code is thereby "hidden". However, decoding the attachment unloads the virus and infects the computer system.
In order to raise trust with the recipient of this e-mail, a good quality candidate image is often added and referred to the company's website where the alleged candidate has found the vacancy.
As the security researchers from the Hornetsecurity Security Lab now discovered, the spreading malware is a new Gandcrab campaign. Already in January this year and autumn 2018 security experts observed an increased occurrence of this type of malware. The perfidious thing about the spam wave, however, is the encrypted document that downloads the GandCrab Ransomware. The encryption leverages classic checks from the macro code, since a static analysis of the document is not possible. So the encrypted file could not be recognized by any classic anti-virus program.
As soon as the recipient opens and decrypts the attached document, the user is prompted to click the "Enable editing" and "Activate content" buttons. If you do this, the macro in the Office document starts a hidden terminal and runs PowerShell commands to download and run the GandCrab Ransomware from the Internet.
Subsequently, the GandCrab Ransomware encrypts all data on the infected machine and replaces the desktop background with a claim message.
Summary of the key data of the defective
e-mail:
Cover letter is written in good German, with
professional-looking details of the "applicant"
-The attachment contains an
encrypted document in .pdf, .doc or zip format
-The password for decrypting
the attachment is also sent in the same e-mail
-The linguistic idiom varies
with the sample mail below
IoCs –
SHA256:
d17646f0eb60e8844959480ef9a57eb38efc8cd55775d5585510d4df4cde29b7
(application/msword)
93e5705c467d4b92a2a1dde1c1216472e127787b58feb45804b83087b68125ad
(application/msword)
Hannah did an excellent post explaining GandCrab in more detail. Below IOCs are taken from that post.
machustonecadunfe.info
316532969.doc (CDFV2 Encrypted)
SHA256
2addae338445a427cf2dfb7e486d130f6fe863506ba7a715af9e87cbf83b0978
word1.tmp (PE32 executable (GUI) Intel 80386, for MS Windows)
SHA256
9b7229403e4729d9347d2d66a4dc6a75fd87a646cbb1027d2857b066a3bbb354
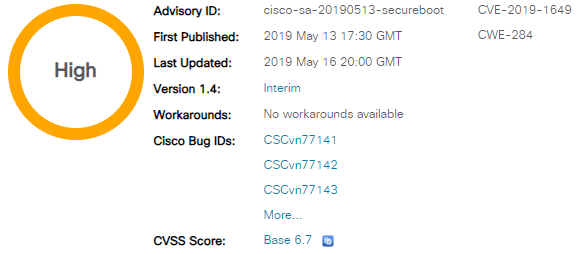
Thrangrycat 0Day: Cisco Secure Boot Hardware Tampering Vulnerability
Details
-
An attacker will need to fulfil all the following conditions to attempt to exploit this vulnerability:
- Have privileged administrative access to the device.
- Be able to access the underlying operating system running on the device; this can be achieved either by using a supported, documented mechanism or by exploiting another vulnerability that would provide an attacker with such access.
- Develop or have access to a platform-specific exploit. An attacker attempting to exploit this vulnerability across multiple affected platforms would need to research each one of those platforms and then develop a platform-specific exploit. Although the research process could be reused across different platforms, an exploit developed for a given hardware platform is unlikely to work on a different hardware platform.
Affected products: See this link
Workarounds
-
There are no workarounds that address this vulnerability.
China Chopper Malware affecting SharePoint Servers

Number: AL19-006
Date:
23 April 2019
Assessment
The Cyber Centre is aware of a campaign that is currently compromising several versions of Microsoft SharePoint Server in order to deploy the China Chopper web shell. Trusted researchers have identified compromised systems belonging to the academic, utility, heavy industry, manufacturing and technology sectors. The following versions of Microsoft SharePoint are known to be affected:
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Foundation 2013 SP1
- Microsoft SharePoint Server 2010 SP2
- Microsoft SharePoint Server 2019
It is likely that the current campaign is leveraging CVE-2019-0604 in order to deploy the web shell. Microsoft released security updates addressing this vulnerability in February and March 2019; however, many systems remain outdated.
Suggested action
- All Microsoft SharePoint Server installations should be patched with the latest security update, dated 12 March 2019, using Microsoft Update, the Microsoft Update Catalog or the Microsoft Download Center.
- If a SharePoint instance serves strictly as an on-premises solution, ensure that the server has no exposure to the Internet.
Indicators of compromise HASH Values
MD5 Hash: b814532d73c7e5ffd1a2533adc6cfcf8
SHA1 Hash:
dc8e7b7de41cac9ded920c41b272c885e1aec279
SHA256 Hash:
05108ac3c3d708977f2d679bfa6d2eaf63b371e66428018a68efce4b6a45b4b4
Filename:
pay.aspx
MD5 Hash: 708544104809ef2776ddc56e04d27ab1
SHA1 Hash:
f0fb0f7553390f203669e53abc16b15e729e5c6f
SHA256 Hash:
b560c3b9b672f42a005bdeae79eb91dfb0dec8dc04bea51f38731692bc995688
MD5 Hash: 0eebeef32a8f676a1717f134f114c8bd
SHA1 Hash:
4c3b262b4134366ad0a67b1a2d6378da428d712b
SHA256 Hash:
7d6812947e7eafa8a4cce84b531f8077f7434dbed4ccdaca64225d1b6a0e8604
Filename:
stylecss.aspx
IP Address
114.25.219.100
References
Microsoft advisory: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0604
ZDI article: https://www.zerodayinitiative.com/blog/2019/3/13/cve-2019-0604-details-of-a-microsoft-sharepoint-rce-vulnerability
Chine Chopper information: https://cyber.gc.ca/en/guidance/web-shells-china-chopper
CVE-2018-12130 ZombieLoad-Attack
Another side channel attack has been discovered
ZDNet has done a post among many others.
And Intel has done an official post about their impacts.
Under certain conditions, data in microarchitectural structures that the currently-running software does not have permission to access may be speculatively accessed by faulting or assisting load or store operations. This does not result in incorrect program execution because these operations never complete, and their results are never returned to software. However, software may be able to forward this speculative-only data to a side channel disclosure gadget in a way that potentially allows malicious actors to infer the data.
Mitigation
Some current processors and future processors will have microarchitectural data sampling methods mitigated in the hardware. For processors that are affected, the mitigation for microarchitectural data sampling issues includes overwriting store buffers, fill buffers, and load ports before transitioning to possibly less-privileged code.
There are two methods to clear microarchitectural structures
affected by MDS: MD_CLEARfunctionality1 and software
sequences. On processors that enumerate MD_CLEAR2, developers
can use the VERW instruction
or L1D_FLUSH command3 to cause the processor to
overwrite buffer values that are affected by MDS, as these instructions are
preferred to the software sequences.
Panama Citizens Massive Data Breach

SECURITY DISCOVERY POSTED BY: BOB
DIACHENKO MAY 13, 2019 is writing a post
of:
On May 10th I identified a massive bulk of data sitting in an unprotected and publicly available Elasticsearch cluster (hence visible in any browser).

This database contained 3,427,396 records with detailed information on Panamanian citizens (labeled as ‘patients‘), plus 468,086 records with records labeled as ‘test-patient‘ (although, this data also appeared to be valid and not purely test data).
Each record contained the following info:
- full name
- date of birth
- national ID number (cedula)
- medical insurance number
- phone
- address
- other info
With Panama’s total population number at 4,1M, the exposed number of 3,4-4,8M records would correspond to almost 90% of the country’s citizens.
I have immediately sent a notification alert to CERT Panama, and within 48 hours the database has been secured.
According to Shodan historical data, the IP in question has been indexed since April 24th, 2019 and it is unknown whether anyone else has accessed the data.
The danger of having an exposed Elasticsearch or similar NoSql databases is huge. I have previously reported that the lack of authentication allowed the installation of malware or ransomware on the MongoDB servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
Google: A global hub for privacy engineering, in the heart of Europe
Sundar Pichai CEO of Google in Munich:
Last week at I/O, our annual developer conference in California, I shared how we’re working to build a more helpful Google for everyone. Keeping people safe online, and their information private and secure, is a big part of how we do this. We believe that privacy and safety must be equally available to everyone in the world, and we bring that to life with products that empower everyone with clear and meaningful choices around their data.
To build on that commitment, this week, we’re officially opening the Google Safety Engineering Center (GSEC) in Munich, Germany. We’re growing our operations and doubling the number of privacy engineers in Munich to more than 200 by the end of 2019, making Germany a global hub for Google’s cross-product privacy engineering efforts. The team will work hand-in-hand with privacy specialists in Google offices across Europe and globally, and the products built there will be used around the world.
It’s no accident that we’re building our privacy hub in the heart of Europe, and in a country that in many ways reflects how Europeans think about online safety, privacy and security. Many of our privacy products have been built in Munich, including Google Account, a central place where you can control your privacy when you use Google products. Today, more than 20 million people visit Google Account every day to review their settings, using tools like Privacy Checkup, which provides a quick and easy walk-through of your privacy settings.
Continue reading here.
TheGuardian: WhatsApp hack
As recently reported by the Guardian and many others, there is another vulnerability facing the VoIP-stack of WhatsUp. So your in danger of someone taking over your phone by just giving you a whatsup call.
But cure is available already. Just update to the most recent version and you're save. - Well, until they discover a new vuln - as usual. :-)
Read the original Guardian post here.
citycomp leak
http://snatchvwddns6zto.darknet.to/targets/citycomp.de/
http://snatchvwddns6zto.onion/targets/citycomp.de/packed/
Be careful, some of the files have been reported to have malware embedded..!!!
See my main page here.
Win10 Telemetry tweaks
https://www.mpauli.de/disable-data-logging-in-windows-10.html
#
Win 10 / Server 2016 / Server 2019 Initial Setup Script - Tweak library
#
Author: Disassembler <disassembler@dasm.cz>
# Version: v3.6,
2019-01-28
# Source: Disassembler0/Win10-Initial-Setup-Script
Description
This is a PowerShell script for automation of routine tasks done after fresh installations of Windows 10 and Windows Server 2016 / 2019. This is by no means any complete set of all existing Windows tweaks and neither is it another "antispying" type of script. It's simply a setting which I like to use and which in my opinion make the system less obtrusive.
Usage
If you just want to run the script with the default preset, download and unpack the latest release and then simply double-click on the Default.cmd file and confirm User Account Control prompt. Make sure your account is a member of Administrators group as the script attempts to run with elevated privileges.
The script supports command line options and parameters which can help you customize the tweak selection or even add your own custom tweaks, however these features require some basic knowledge of command line usage and PowerShell scripting. Refer to Advanced usage section for more details.
powershell.exe -NoProfile -ExecutionPolicy Bypass -File Win10.ps1 [-include
filename] [-preset filename] [[!]tweakname]
-include filename load module
with user-defined tweaks
-preset filename load preset with tweak names to
apply tweakname apply tweak with this particular name
!tweakname remove
tweak with this particular name from selection
My output while installing the defaulting script:
C:\Users\xxxx\Downloads\Win10-Initial-Setup-Script-master\Win10-Initial-Setup-Script-master>.\Default.cmd
Disabling Telemetry...
Disabling Wi-Fi Sense...
Disabling Bing
Search in Start Menu...
Disabling Application suggestions...
Disabling
Activity History...
Disabling Background application access...
Disabling
Location Tracking...
Disabling automatic Maps updates...
Disabling
Feedback...
Disabling Tailored Experiences...
Disabling Advertising
ID...
Disabling Website Access to Language List...
Disabling
Cortana...
Disabling Error reporting...
Stopping and disabling Diagnostics
Tracking Service...
Stopping and disabling WAP Push Service...
Disabling
implicit administrative shares...
Setting current network profile to
private...
Hiding Account Protection warning...
Disabling Windows Script
Host...
Enabling .NET strong cryptography...
Enabling F8 boot menu
options...
Setting Data Execution Prevention (DEP) policy to
OptOut...
Disabling Windows Update automatic restart...
Disabling Shared
Experiences...
Disabling Remote Assistance...
Enabling Remote Desktop w/o
Network Level Authentication...
Disabling Autoplay...
Disabling Autorun
for all drives...
Disabling Action Center (Notification
Center)...
Disabling Lock screen...
Hiding network options from Lock
Screen...
Hiding shutdown options from Lock Screen...
Disabling Sticky
keys prompt...
Showing task manager details...
Showing file operations
details...
Hiding Taskbar Search icon / box...
Hiding Task View
button…
Hiding Pictures icon from This PC...
Hiding Videos icon from This
PC...
Hiding 3D Objects icon from This PC...
Disabling creation of
thumbnail cache files...
Disabling creation of Thumbs.db on network
folders...
Disabling OneDrive...
Uninstalling OneDrive...
Uninstalling
default Microsoft applications...
Uninstalling default third party
applications...
Disabling Xbox features...
Disabling built-in Adobe Flash
in IE and Edge...
Disabling Edge preload...
Disabling Edge shortcut
creation...
Disabling Internet Explorer first run wizard...
Setting Photo
Viewer association for bmp, gif, jpg, png and tif...
Adding Photo Viewer to
'Open with...'
Uninstalling Microsoft XPS Document Writer...
Removing
Default Fax Printer...
Press any key to continue...
Block suspicious (phishing) domains with a piHole
https://www.mpauli.de/dnssec-on-a-raspberry-pi-in-5-minutes.html
In the consequence of an article I did on detecting bad domains from the Google transparency service, I thought of using the outcome on my piHole to block the findings right away.
Install it the usual way:
git clone
https://github.com/x0rz/phishing_catcher.git
phishing_catcher/
pip install
-r requirements.txt
./catch_phishing.py
And add the logfile to the piHole config
![]()
Click [save & update]

Done …. and you're a bit more secured now :-)
Solutions for the GOOGLE CTF 2018 Hacking contest
Read the summary done by SEC Consult on an article originally written by Pichaya Morimoto (Security Consultant, SEC Consult Thailand) to give you an insight to last year’s Google Capture the Flag contest took place in June 2018.
WHAT IS GOOGLE CTF?
Google CTF is a hacking competition in the style of Capture-the-Flag, which has been going on for many years. Many of the questions have to do with Google’s technologies such as Android, Firebase, Angular, GCP and others. There are 5 categories of questions to solve: Crypto, Misc, Pwn, Re and Web. This article will focus about Web, which is a lot of fun.
Continue reading the whole blog here.