Exploring the MQTT Protocol with ESP8266
Using an RPi as the MQTT broker. We'll explore two-node communication as well as LWT messages (last will).
Story
In any IoT project we have a number of unique requirements and restrictions. The communication strategy to connect devices and send data between them is critically important.
In this guide we will explore a powerful, simple and lightweight messaging protocol over the wire: MQTT
Main Features
- Data agnostic: you can use it to send sensor data, images or even OTA (over the air) updates
- Lightweight and bandwidth efficient: smallest frame is only 2 bytes long
- Per-queue QoS levels
- Runs on top of the TCP/IP stack, so you can use it to encrypt the data with TLS/SSL and to have a secure connection between clients
- Simple to develop: clients exist for all operating systems and programming languages
- Central broker: different devices can communicate with each other without having to worry about compatibility
- Session awareness: provides an identity-based approach for subscriptions
- Flexible subscription topics using single-level and multi-level wildcards
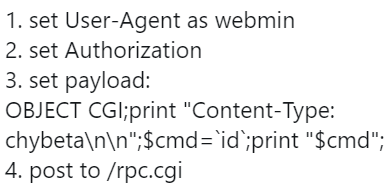
CVE-2019-15642 another Webmin Remote Code Execution (authenticated)
 has
done a tweet about a poc of CVE-2019-15642.
has
done a tweet about a poc of CVE-2019-15642.
This will provide RCE capabilities on a Webmin instance.
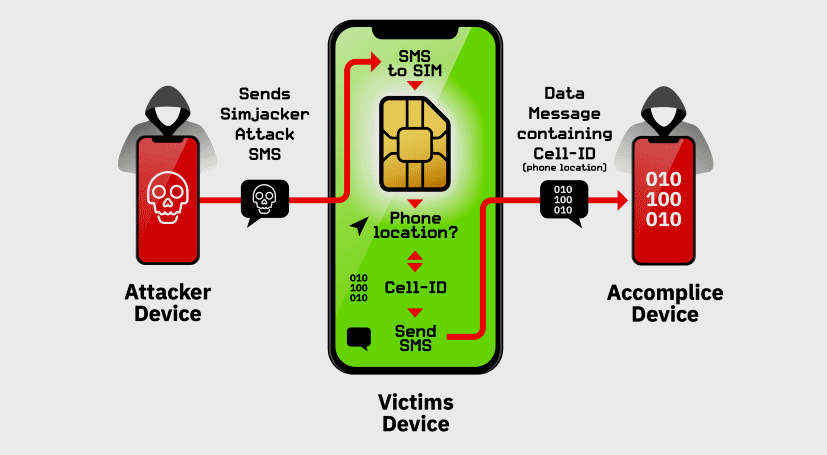
ZDNet: Simjacker attack exploited in the wild to track users for at least two years
Catalin Cimpanu for Zero Day wrote a cool article about SIMJacker being used for the last two years.
The reader that might not have heard about this vulnerability of millions of cell phones, may be interested in below description taken from a very detailed report coming from AdaptiveMobile Systems:
The main attack observed involves two stages:
1) Attack Stage: An SMS ‘Attack Message’ is sent from an attacker to a victim phone number
The Attack Message executable primarily instructs the SIM Card to request Location Information – the current serving Cell-ID of the handset and the IMEI from the Handset, and send the Location and IMEI from the Handset in a 2nd SMS. These instructions are in the form of a series of SIM Toolkit (STK) instructions, which the SIM Card will run to obtain the relevant information.
2) Exfiltration Stage: An SMS ‘Data Message’ is sent from the Victim Handset to a Recipient Phone Number – i.e. the Exfiltration Address.
This activity is not noticeable by the Victim – there is no indication on the handset
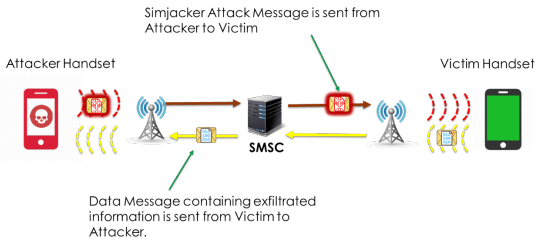
Note: This diagram is for illustration. Often the Attackers send the Data Message to a different Recipient Phone Number than that which originated the actual attack.
My personal conclusion:
Despite the information disclosure and GPS
tracking ability an attacker has on the victims device, he can use the S@T browser to download/install (in combination of other
vulns) any stuff he likes on the device. But think of the "low hanging fruites"
of:
- Fraud Applications
- Advanced Location Tracking
- Assistance in Malware Deployment
- Denial of Service
- Information Retrieval
- Misinformation
By the nature of the technology, everything is done with zero-security.
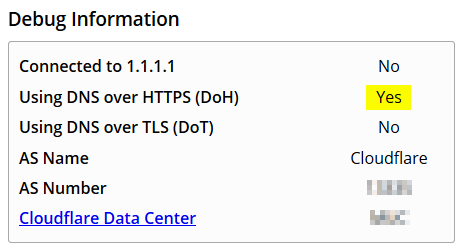
DNS over httos (DoH) on pihole
How to use the cloudflare DoH service via your pihole.
Here we are downloading the precompiled binary and copying it to
the /usr/local/bin/ directory to allow execution by the
cloudflared user. Proceed to run the binary with
the -v flag to check it is all working.
wget https://bin.equinox.io/c/VdrWdbjqyF/cloudflared-stable-linux-arm.tgz tar -xvzf cloudflared-stable-linux-arm.tgz sudo cp ./cloudflared /usr/local/bin sudo chmod +x /usr/local/bin/cloudflared cloudflared -v
Configuring cloudflared to run on startup¶
Create a cloudflared user to run the daemon.
sudo useradd -s /usr/sbin/nologin -r -M cloudflared
Proceed to create a configuration file
for cloudflared by copying the following in
to /etc/default/cloudflared. This file contains the
command-line options that get passed to cloudflared on startup.
# Commandline args for cloudflared CLOUDFLARED_OPTS=--port 5053 --upstream https://1.1.1.1/dns-query --upstream https://1.0.0.1/dns-query
Update the permissions for the configuration file
and cloudflared binary to allow access for the
cloudflared user
sudo chown cloudflared:cloudflared /etc/default/cloudflared sudo chown cloudflared:cloudflared /usr/local/bin/cloudflared
Then create the systemd script by copying the
following in to /lib/systemd/system/cloudflared.service. This
will control the running of the service and allow it to run on startup.
[Unit] Description=cloudflared DNS over HTTPS proxy After=syslog.target network-online.target [Service] Type=simple User=cloudflared EnvironmentFile=/etc/default/cloudflared ExecStart=/usr/local/bin/cloudflared proxy-dns $CLOUDFLARED_OPTS Restart=on-failure RestartSec=10 KillMode=process [Install] WantedBy=multi-user.target
Enable the systemd service to run on startup, then
start the service and check its status.
sudo systemctl enable cloudflared sudo systemctl start cloudflared sudo systemctl status cloudflared
Now test that it is working! Run the
following dig command, a response should be returned
similar to the one below
dig @127.0.0.1 -p 5053 google.com ; <<>> DiG 9.10.3-P4-Ubuntu <<>> @127.0.0.1 -p 5053 google.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 65181 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1536 ;; QUESTION SECTION: ;google.com. IN A ;; ANSWER SECTION: google.com. 299 IN A 243.65.127.221 ;; Query time: 3 msec ;; SERVER: 127.0.0.1#5053(127.0.0.1) ;; MSG SIZE rcvd: 65
Configuring Pi-hole¶
Finally, configure Pi-hole to use the
local cloudflared service as the upstream DNS server:
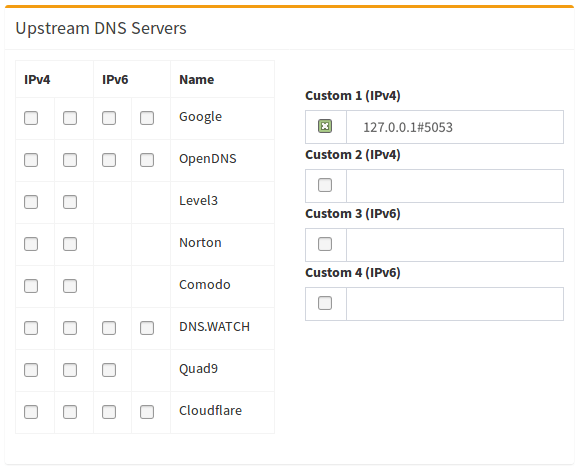
You can test the setup at https://1.1.1.1/help
Portable ATM skimmer card detector
Cameron Coward has written an article about a portable skimmer card detector for ATMs.
So if you were ever unsure if everything is alreight with the ATM your using, use this little 35$ device to see if your card data is being copied away. (watch the legal situation of your country)
Checkout hackster.io not only for this cool gadget.
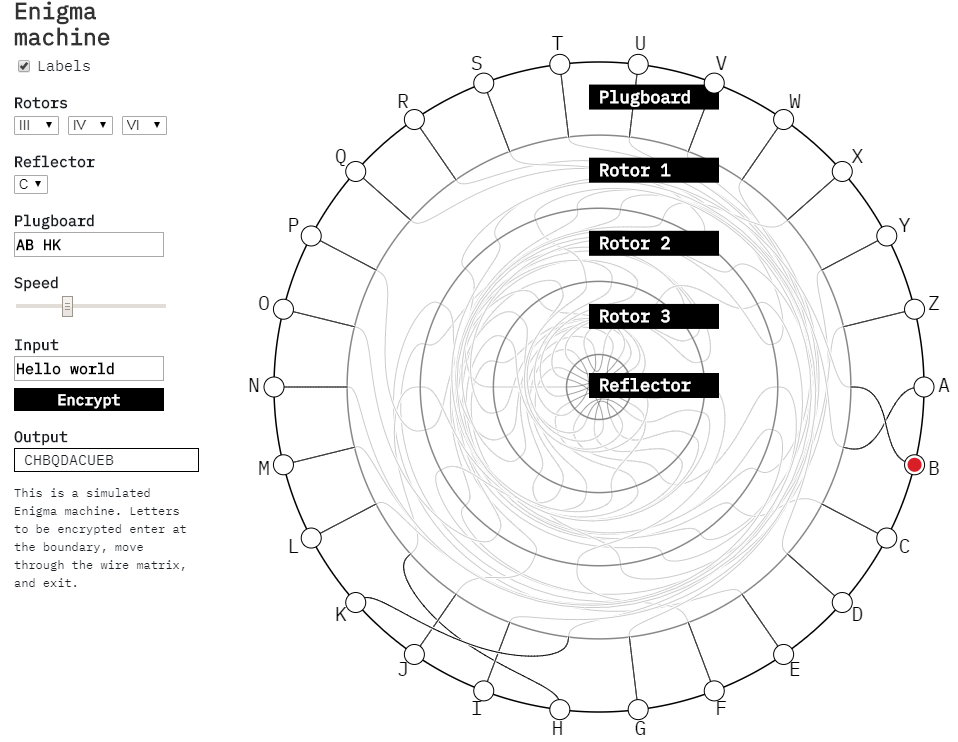
Animated workflow of the Enigma machine
Tom MacWright is showing the animation of how the Enigma works. This is a "must see" of an excellent work.
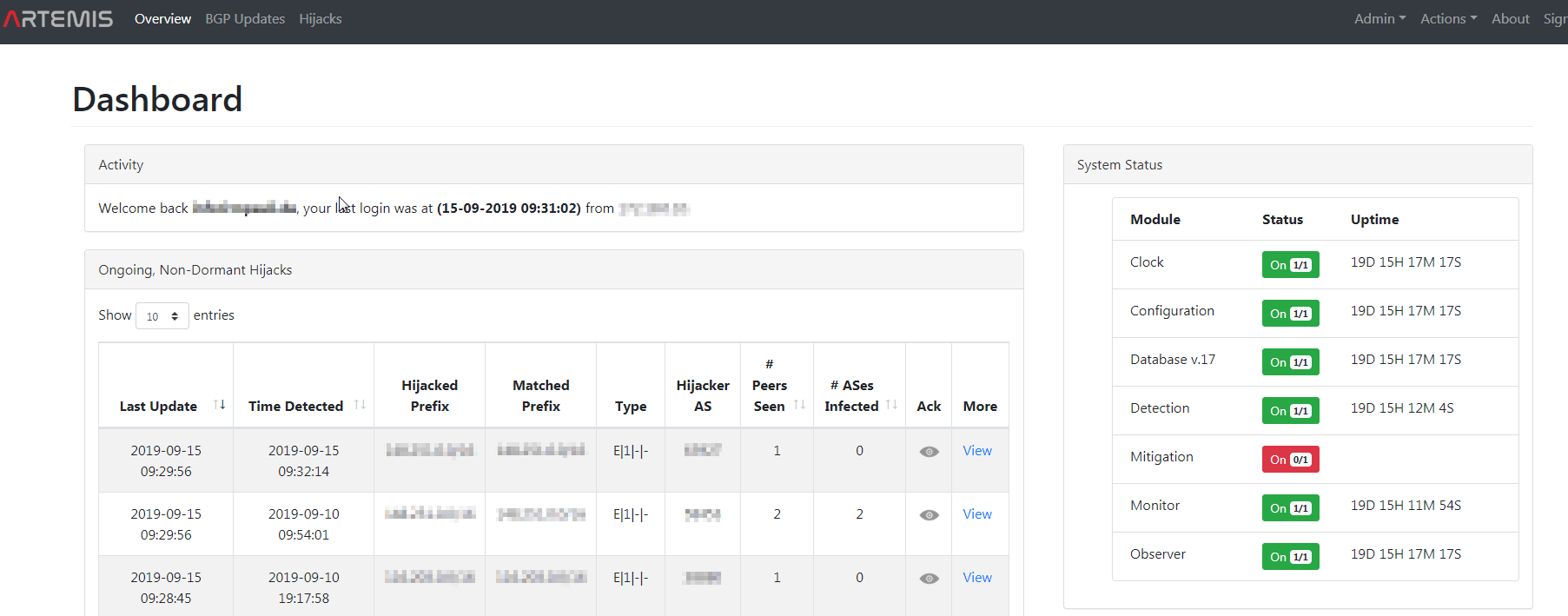
Artemis: BGP-Hijack monitor
![]()
FORTH-ICS-INSPIRE from
Greek is providing the community with a personally long awaitet tool to monitor
BGP-Hijack attempts of configurable networks.
Features:
- Real-time monitoring of the changes in the BGP routes of the prefixes originated by the AS running ARTEMIS.
- Real-time detection and notifications of BGP prefix hijacking
attacks/events of the following types (please refer to the attack taxonomy in
our ARTEMIS ToN paper):
- exact-prefix, type 0/1, any data plane manipulation
- sub-prefix, any type (0/1/-), any data plane manipulation
- squatting attacks, type 0 (others are N/A), any data plane manipulation
- policy violations (route leaks) due to long paths towards no-export prefixes
- Automatic/custom tagging of detected BGP hijack events (ongoing, resolved, ignored, under mitigation, withdrawn, outdated and dormant).
- Manual or manually controlled mitigation of BGP prefix hijacking attacks.
- Comprehensive web-based User Interface (UI).
- Configuration file editable by the operator (directly or via the UI), containing information about: prefixes, ASNs, monitors and ARTEMIS rules ("ASX originates prefix P and advertises it to ASY").
- Support for both IPv4 and IPv6 prefixes.
- Support for both mobile and desktop environments (UI): sample screenshots.
- Support for docker-compose (local deployment) and Kubernetes (helm charts).
- Support for multiple modes of operation (passive monitor/detector, active mitigator, etc.).
- Modularity/extensibility by design.
- CI/CD.
I created a PoC on my environment to monitor my providers AS. Looks pretty amazing.
"Heartbleed" @ Marcus
![]()
Sorry for being so silent the last view weeks, but I had
an heart attack and still need some time to recover. - But cyber time does not
stand still so I still have collected some news worth knowing.
#postponed# My first own MeetUp: Save the date 12.09.2019
Unfortunetly this had to be postponed to December as of my heard attack. :-/
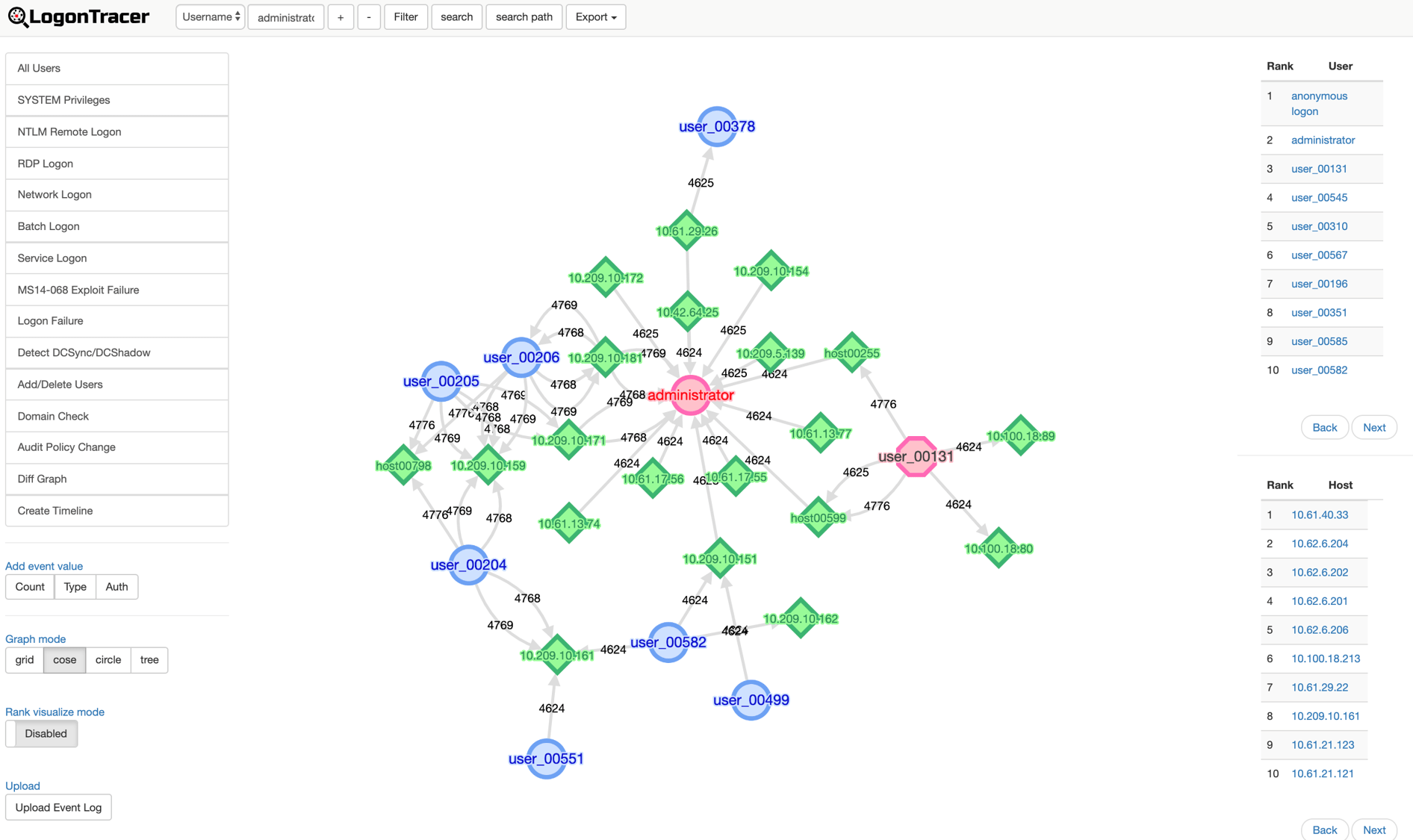
Visualize windows eventlogs with LOGONTRACE
Thx to JPCERTCC/LogonTracer
While I was busy doing windows event log anaysis the past days, I came across a very cool tool to visualize the different WinEvents with LogonTracer of the JPCERT.
LogonTracer is a tool to investigate malicious
logon by visualizing and analyzing Windows Active Directory event logs. This
tool associates a host name (or an IP address) and account name found in
logon-related events and displays it as a graph. This way, it is possible to see
in which account login attempt occurs and which host is used.
This tool can
visualize the following event id related to Windows logon based on this research.
- 4624: Successful logon
- 4625: Logon failure
- 4768: Kerberos Authentication (TGT Request)
- 4769: Kerberos Service Ticket (ST Request)
- 4776: NTLM Authentication
- 4672: Assign special privileges
While using a docker image, the installation is very easy, so is the use. - Give it a try.
$ docker run \ --detach \ --publish=7474:7474 --publish=7687:7687 --publish=8080:8080 \ -e LTHOSTNAME=[IP_Address] \ jpcertcc/docker-logontracer
SYSMON Test of your SIEM
Are you using sysmon in your environment and detect unwanted behaviour from within your SIEM with it? Then have a check at sbousseaden/EVTX-ATTACK-SAMPLES and test your SIEM capabilities or create new usecases with the 120 available samples of various attack samples.
A big thanks to sbousseaden for this great contribution.
Opensource intruder detection with tokens in your documents and network

While having a little obsession for birds (Cuckoo) I just was made aware of another
species "Canary" from
StationX.
Wouldn’t it be cool if you could setup security tripwires to tell you if someone or something was trying to poke around in our files, on our laptop, phone, in our email and on our online accounts? Well now you can.
You can either use the cloud service of StationX or setup your own system to get an alert when ever someone if accessing a "trap" (token) you embedded within an email, file, directory, pdf or word document.
To get you an idea of what sort of tokens you could create to be alerted on access or use, StationX is providing some good samples:

Or just embed the created token within an email you send to your account with below data to make is very useful for an attacker to "follow" the link. - Apart from clicking the embedded "phishy" link, an alert can already be generated by only opening the mail due to an hidden code being in place.
|
MY PASSWORDS AND STUFF • DOB = 10 - August 1922 |
Another "Lunch & Learn"
We had an excellent event within our "Lunch & Learn" this time
with speakers from the German Aerospace (DLR) about the attempts they make
in securing our ridiculously insecure flight communication.
A thrilling and
eye opening event that created a lot of interest within the audience of my cyber
colleges and me. I hope we all can make it for the "open
doors" day on 21st July 2019 at the DLR.
Thank you very much for this event and the participation.
See it on LinkedIn
Google Home Silently Captures Recordings of Domestic Violence and More
 Author
Lindsay O'Donnell
is writing an article at Threatpost
about the same thing as of Alexa now was made public for Google's "Home".
Author
Lindsay O'Donnell
is writing an article at Threatpost
about the same thing as of Alexa now was made public for Google's "Home".
In a Wednesday report, Dutch news outlet VRT NWS said it obtained more than one thousand recordings from a Dutch subcontractor who was hired as a “language reviewer” to transcribe recorded audio collected by Google Home and Google Assistant, and help Google better understand the accents used in the language. Out of those one thousand recordings, 153 of the conversations should never have been recorded, as the wake-up command “OK Google” was clearly not given, the report said.
“VRT NWS was able to listen to more than a thousand excerpts recorded via Google Assistant,” according to the report. “In these recordings we could clearly hear addresses and other sensitive information. This made it easy for us to find the people involved and confront them with the audio recordings.”Google for its part on Thursday acknowledged that VRT NWS had obtained authentic recordings, but argued that its language experts only review around 0.2 percent of all audio snippets.
“As part of our work to develop speech technology for more languages, we partner with language experts around the world who understand the nuances and accents of a specific language,” according to David Monsees, product manager at Google Search. “These language experts review and transcribe a small set of queries to help us better understand those languages. This is a critical part of the process of building speech technology, and is necessary to creating products like the Google Assistant.”
Google did acknowledge that some audio may be recorded by Google Home or Google Assistant without the wake-up word being said, due to error.
As of my earlier writing, the "Project Alias" by BjørnKarmann had already thought of this security issue and developed a excellent device made around a Raspy PI, that plays white noise to Alexa or Home while not having heard the "wakeup word". This way, if someone is eavesdroping, he only hears garbage. Still, be deactivating the "garbage" when ever the self definable "wakeup word" was heard, the white noise is turned off and the original function is been established.
A very cool and pragmatic solution…!!! Credits and respects to Bjoern.
Logitech keyboards and mice vulnerable to extensive cyber attacks
heise Security has a brilliant article about several devices of Logitech being vulnerable of MouseJack (CVE-2019-13055)
So checkout your devices for the orange asterisk. *
The vulnerabilities allow an attacker to eavesdrop on keystrokes from wireless keyboards. Everything an affected user types, from e-mails to passwords, is readily available to the adversary. But it gets worse: An attacker can send any command to the victim's computer if a vulnerable Logitech-device is installed. And that makes it easy to infect the computer with malicious code without the rightful owner taking notice.
These products are affected
Any Logitech device that uses the so-called Unifying radio technology is affected. Logitech has been shipping the vulnerable Unifying USB receivers with wireless keyboards and mice since 2009. Unifying is used across Logitech's product range, from inexpensive entry level devices to current high-end models. The vulnerable USB receivers are recognized by a small orange star logo.
In addition, wireless gaming products of the Lightspeed series and the Wireless Presenters R500 and Spotlight are also affected. They use related radio technology. The Presenter R400, R700 and R800, however, are not affected by the vulnerabilities described in this article.
OpenCTI
A new star at the CTI sky… (Credits to Hugo)
Check out opencti and correlate all your CTI sources at one tool to give you a fine overview.
Knowledge graph
The whole platform relies on a knowledge hypergraph allowing the usage of hyper-entities and hyper-relationships including nested relationships.
Unified and consistent data model
From operational to strategic level, all information are linked through a unifed and consistent data model based on the STIX2 standards.
By-design sourcing of data origin
Every relationships between entities have time-based and space-based attributes and must by sourced by a report with a specific confidence level.
Exploration and correlation
The whole dataset could be explored with analytics and correlation engines including many visualization plugins, MapReduce and Pregel computations.
Automated reasoning
The database engine performs logical inference through deductive reasoning, in order to derive implicit facts and associations in real-time.
Data access management
Full control of data access management using groups with permissions based on granular markings on both entities and relationships.
Have a look at the open demo:
Installation is fairly simple by the use of docker:
$ mkdir /path/to/your/app && cd /path/to/your/app
$ git clone https://github.com/OpenCTI-Platform/opencti.git
$ cd opencti/opencti-docker
vi docker-compose.yml and change the value of APP__SECRET to a random
string
$ sysctl -w vm.max_map_count=262144 to adjust elasticsearch
$
docker-compose up
Browse to: http://localhost:8080 and log in with
username admin@opencti.io and
password admin
Finding and Testing MisConfigured S3 Buckets
Rohan Chavan has a cool writing on how to establish above task at medium.com.
Finding Buckets :-
These can be done manually or by using some automated scripts such as :-
bucket_finder
Download: https://github.com/FishermansEnemy/bucket_finder
S3Scanner
Download: https://github.com/sa7mon/S3Scanner
s3-inspector
Download: https://github.com/kromtech/s3-inspector
Malware sample repository
@0xffff0800 is sharing his malware repository with the community. This is an excellent source to test the capabilities of your new cuckoo and/or do some reversing on the stuff.
tor only: http://iec56w4ibovnb4wc.onion/Library/
heading only:
sudo apt-get install torsocks
torsocks wget -mkEpnp http://iec56w4ibovnb4wc.onion/Library/
Secure your Microsoft Office software

The German Cyber Alliance has done a great job by publishing several documents on how to secure your MS Office applications. Coll if you know how to read German, but if not just use the translator of your choice. The documents themselves have the English translation of the setting inside anyway.
Exploiting Android Through ADB With PhoneSploit
Your Android is M I N E ! ! !
Use shodan and search for port:5555 product:"Android Debug Bridge". By the time of this writing, I got 13220 results. Manly from Asia where the providers seem to open this service and port to the Internet per default.
Now get PhoneSploit and do any of the below:
- Access Shell on a phone
- Install an apk on a phone
- Screen record a phone
- Screen Show a picture on a phone
- Pull folders from phone to pc
- Turn the device off
- Uninstall an app
- Show real time log of device
- Dump system Info
- List all apps on a phone
- Run an app
Please bear in mind, that any such action would probably be illegal according to the lawset of the country you start the action in.